
During the past two years we’ve written many times about programs which pretend to be something that they are not. The most notorious are rogue antivirus solutions – programs which display messages saying the victim machine is infected, even though it is not. These programs neither scan nor clean computers, and they are actually designed to persuade users that their computers are at risk and scare them into buying the “antivirus” product. Such programs are often referred to as “scareware”: Kaspersky Lab classifies them as FraudTool, a subset of the RiskWare class.
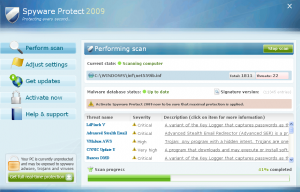
FraudTool.Win32.SpywareProtect2009: the main window
Such programs are extremely widespread and are increasingly used by cybercriminals. Whereas Kaspersky Lab detected about 3,000 rogue antivirus programs in the first half of 2008, more than 20,000 samples were identified in the first half of 2009.
Common distribution techniques
First of all, how do rogue antivirus programs end up on victim machines? They are spread using the same methods use to distribute other malware: for instance, a Trojan-Downloader can secretly download such programs, or vulnerabilities in compromised/ infected sites can be exploited to perform a drive-by download.
More often than not, though, such programs are downloaded by users themselves – cybercriminals use dedicated (Hoax) programs or adverts to trick users into doing this.
Hoax programs are another type of fraudware; they are designed to persuade users that they need to download a “wonder-working” antivirus solution, and will install the rogue solution on the victim machine even if the user declines the offer.
Hoax programs get downloaded to victim machines either by using a backdoor or by exploiting a vulnerability on a website. Once such a program is installed, an alert appears which says the system contains multiple errors, the registry is damaged or that confidential data is being stolen.
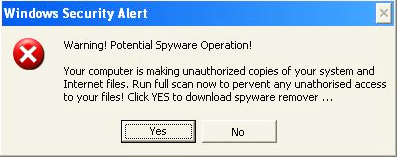
Message displayed by Hoax.Win32.Fera
The screenshot above is a fake warning message that suggests the computer is infected with spyware. It also prompts the user to install a “spyware remover”. An attempt will be made to download and install the rogue program even if the user clicks “No”.
Cybercriminals also use Internet advertising to distribute rogue antivirus solutions. Lots of sites currently host banners informing users of a new “wonder” product which will solve all types of malware problem. These flashing banners or irritating flash adverts for “new antivirus solutions” can even be found on legitimate resources. When browsing the Web, a user may also find pop-ups appearing in the browser window offering a free antivirus download. The screenshot below shows an example of this type of pop-up.
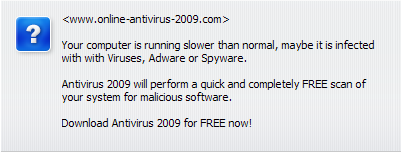
A pop-up window in Opera
Usually, such pop-ups give the user no choice because there is only one button – either “OK” or “YES”. Even if there is a button marked “NO” or “Cancel”, a rogue antivirus program will still be downloaded regardless of which button is clicked.
Kaspersky Lab has recently identified a technique used for the dynamic download of rogue antivirus programs. Here’s an example: a script on ********.net/online-j49/yornt.html generated a redirect address, http://******.mainsfile.com.com/index.html?Ref=’+encodeURIComponent (document.referrer). The address generated depended on how the user arrived at the page containing the script (done with the help of document.referrer), or, in other words, which site the user had previously viewed. In this case the redirect led to http://easyincomeprotection.cn/installer_90001.exe, a page hosting a new rogue antivirus program, FraudTool.Win32.AntivirusPlus.kv.
Dynamic distribution allows cybercriminals to hide the IP address of the page from which malware downloads. This makes it more difficult for antivirus companies to obtain the files for analysis and detection. This distribution method is also used by many common worms and viruses.
For example, Net-Worm.Win32.Kido.js (used to create botnets) employs DDNS technology, and also downloads and installs a rogue antivirus program called FraudTool.Win32.SpywareProtect2009.s. This demonstrates that one and the same group of malware writers is probably responsible for both the network worms and the rogue antivirus, and use the former to smoothly install the latter.
Scaring users into action
It should now be clear how rogue antivirus solutions get onto a system. Let’s see what they do once they are there.
The first step is the system scan. When scanning, rogue antivirus programs display a carefully though-out sequence of messages: for example, notification of a Windows error, followed by a message saying malware has been detected, followed by a message offering the opportunity to install an antivirus program. Sometimes, to make all this seem even more convincing, a file will be installed on the computer together with the rogue antivirus; this file will later be “detected” during the “scanning” process.
Messages displayed by rogue antivirus programs offer the opportunity to correct system errors and clean the system; however, this service is not free. Of course, the more legitimate the software appears, the more chance the cybercriminals have of receiving money in return for their fake solutions.
Here are two examples of rogue antivirus: FraudTool.Win32.DoctorAntivirus and FraudTool.Win32.SmartAntivirus2009. As the screenshots below show, both programs “detect” nonexistent problems on a machine running Windows XP Professional Service Pack 2 and then display messages saying payment must be made to activate the product and clean the infection. DoctorAntivirus detected 40 backdoors, Trojans and spyware programs and displayed a warning message that this could lead to various types of system failure. SmartAntivirus2009 detected a larger number of issues and also warned that they posed a threat to the system.
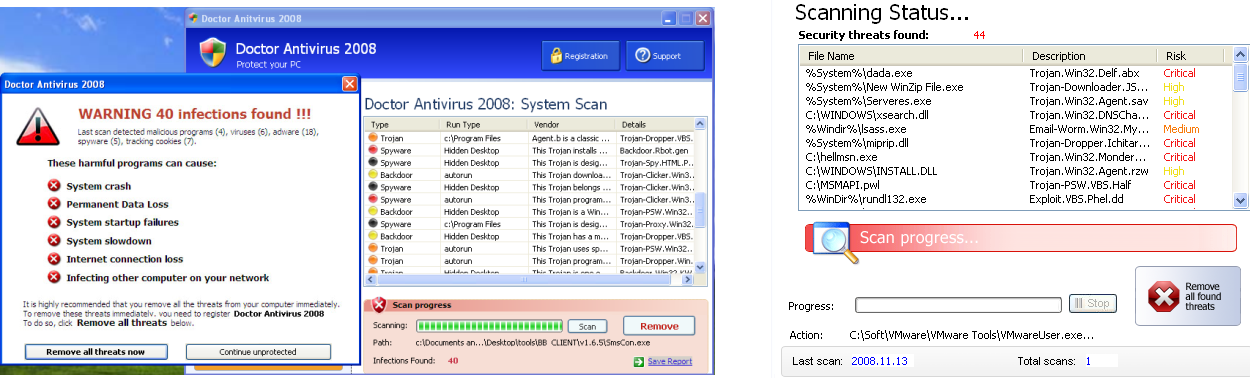
Results of system “scan” performed by DoctorAntivirus
2008 (left) and Smart Antivirus 2009 (right)
After clicking the “Remove” button in both cases, a window appears asking the user to purchase the fake product. If the user agrees, several methods of payment are suggested – PayPal, American Express, etc. After payment has been made, the user receives a registration code. Both these rogue antivirus programs used code verification procedures to ensure that randomly entered characters do not work. This technique is used to help make the programs appear more legitimate. However, the authentication codes which are sent rarely work, and some fake antivirus programs even automatically state that the code is incorrect in the hope that a user will pay a second time.
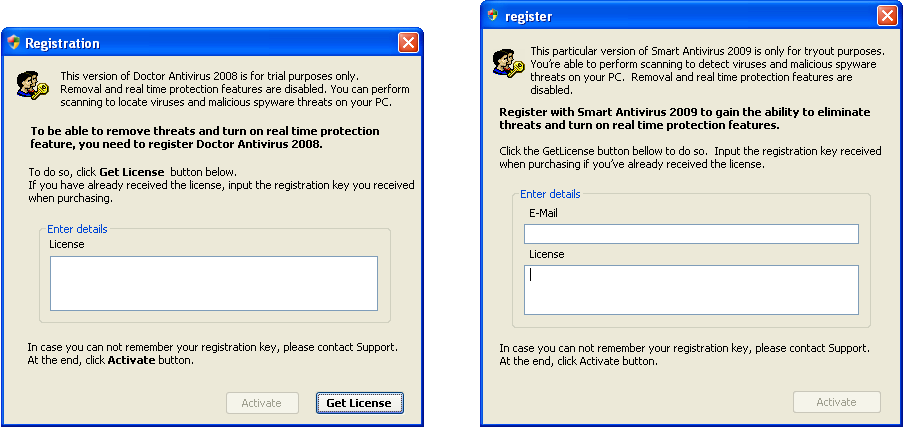
Activating FraudTool.Win32.DoctorAntivirus (left)
and FraudTool.Win32.SmartAntivirus 2009 (right)
The DoctorAntivirus and SmartAntivirus2009 activation windows are almost identical. It looks as if the developers of these programs used a code generator which makes only minor modifications to the text/ appearance of the message while leaving the rest unchanged.
Usually, once a free trial version that allegedly detects (but does not delete) malware has been downloaded, a message is displayed saying the full version should be activated (in return for payment. Such messages often promise a high performance product as well as technical support once the product has been activated.
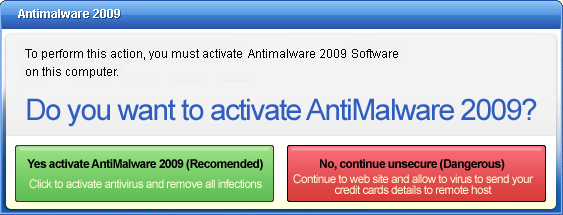
Activation message displayed by FraudTool.Win32.AntiMalware2009
The next screenshot shows the activation window of Smart-Anti-Spyware, a rogue antivirus which is clearly of Russian origin. In order to activate the product, an SMS has to be sent to a short number: this method is commonly used in extortion scams on the Russian Internet.
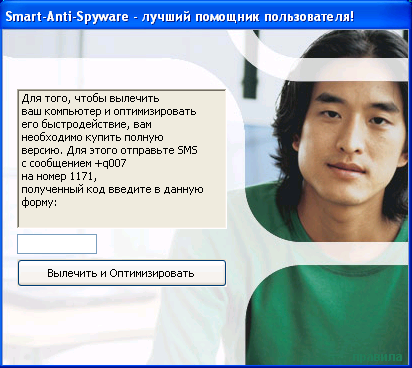
Smart-Anti-Spyware activation window
Treat and optimize]
Production line malware
As mentioned above, some of the messages displayed by different rogue antivirus programs are very similar, if not identical, and it is highly likely that the authors of these programs use the same code generator to create them.
Rogue antivirus programs often the same mechanisms as polymorphic worms and viruses to combat antivirus solutions: the main body of the program is encrypted to conceal strings and links. To ensure the program runs correctly, dynamic code within the file decrypts the body of the malware prior to the payload being delivered.
FraudTool.Win32.MSAntivirus.cg and FraudTool.Win32.MSAntispyware2009.a are typical rogue antivirus programs which implement the approach above. Although the programs come from different families, both are protected by the same polymorphic decrypters. The screenshots below show code fragments from both rogue programs containing the decrypters. The file structure is identical.

FraudTool.Win32.MSAntivirus.cg: polymorphic decrypter fragment
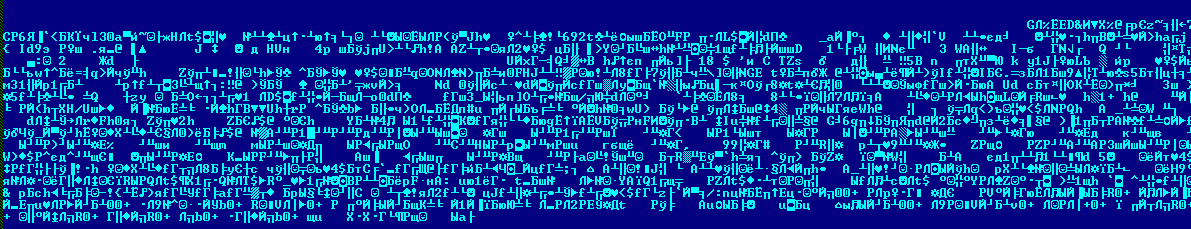
FraudTool.Win32.MSAntispyware2009.a: polymorphic decrypter fragment
The use of off-the-shelf solutions means that lots of similar programs can be created very quickly, and also helps bypass classic signature antivirus solutions. There is now a production line creating rogue antivirus programs; additionally, these programs are evolving, with the body of the programs becoming increasingly sophisticated in order to prevent them from being detected by antivirus signatures.
Additionally, it’s very difficult to detect rogue antivirus programs using heuristic signatures based on behavioural analysis. This is because it’s hard to differentiate between a rogue program which has opened in a separate window from a legitimate application. Consequently, if the rogue program is not packed with a non-legitimate packer, its malicious status can only be determined with manual analysis, making the task of detecting new rogue antivirus programs considerably more difficult.
The statistics speak for themselves
The graph below shows the rise of rogue antivirus solutions since 2007.
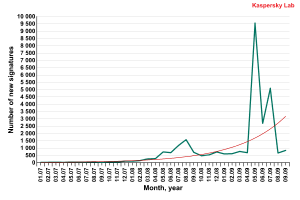
Number of new signatures that detect rogue antivirus
programs (month, 2007-2009)
The graph shows the number of signatures for rogue antivirus programs increased in the first half of 2008, though by the end of the year the increase had slowed. However, in May 2009 there was another upswing in the number of new signatures.
The main reasons for the huge increase in the number of rogue antivirus programs over the last year are that these programs are very easy to create; the distribution system is very effective; cybercriminals can make large profits in a short period of time.
There are currently 318 different families of rogue antivirus programs in the Kaspersky Lab collection. The table below lists the top twenty most common rogue antivirus families; these have had the most signatures created to detect them since 2007. The first five families account for 51.69% of all signatures which detect malware classified as FraudTool, and the names include the names of the antivirus programs which these rogue programs imitate.
| Family | Number of signatures |
| not-a-virus:FraudTool.Win32.SpywareGuard2008 | 4652 |
| not-a-virus:FraudTool.Win32.XPAntivirus | 4519 |
| not-a-virus:FraudTool.Win32.SystemSecurity | 2090 |
| not-a-virus:FraudTool.Win32.XpPoliceAntivirus | 1950 |
| not-a-virus:FraudTool.Win32.AwolaAntiSpyware | 1370 |
| not-a-virus:FraudTool.Win32.PC-AntiSpy | 1356 |
| not-a-virus:FraudTool.Win32.VirusIsolator | 1134 |
| not-a-virus:FraudTool.Win32.WinSpywareProtect | 855 |
| not-a-virus:FraudTool.Win32.SpyNoMore | 758 |
| not-a-virus:FraudTool.Win32.Agent | 575 |
| not-a-virus:FraudTool.Win32.AntivirusXPPro | 434 |
| not-a-virus:FraudTool.Win32.AntiVirusPro | 374 |
| not-a-virus:FraudTool.Win32.AntiSpyware | 344 |
| not-a-virus:FraudTool.Win32.AntivirusPlus | 338 |
| not-a-virus:FraudTool.Win32.SpywareStop | 312 |
| not-a-virus:FraudTool.Win32.WinAntiVirus | 278 |
| not-a-virus:FraudTool.Win32.Antivirus2009 | 227 |
| not-a-virus:FraudTool.Win32.BachKhoa | 224 |
| not-a-virus:FraudTool.Win32.AdvancedAntivirus | 223 |
| not-a-virus:FraudTool.Win32.BestSeller | 214 |
| not-a-virus:FraudTool.Win32.AntiSpywareBot | 206 |
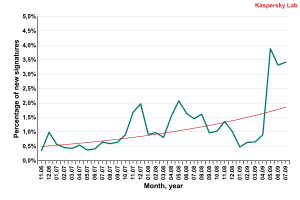
Percentage of new signatures for Hoax and FraudTool
programs in total signatures (month, 2007-2009)
The graph above shows that the signature databases for programs designed to deceive users are growing in size mainly due to the increase in the number of rogue antivirus programs rather than a general increase in the total number of programs detected.
New rogue antivirus programs have become common: Kaspersky Lab detects between 10 and 20 new Hoax or FraudTool programs every day. This would have seemed incredible two or three years ago when a new malicious program of this type only appeared once every two days.
Protection methods
A rogue antivirus infection will not damage the victim machine, but cybercriminals use these programs to extort money from inexperienced users. A convincing interface, a few worrying messages about infection and prompts to buy a “product” can easily persuade someone to part with their money. Remembering a few simple rules should ensure you don’t end up paying for a fake program.
If you find an unknown antivirus program on your computer, check whether the vendor has an official site and technical support. If it doesn’t, it is definitely a rogue antivirus.
Legitimate programs designed to combat malware will never first scan a computer and then demand money for activation. You should never pay for a product which does this: install a genuine antivirus solution developed by a well-known antivirus company and use this to scan and clean your computer.
You should only click on messages from a legitimate antivirus solution installed on the computer. Ignore any messages warning you of infection that appear randomly while you’re browsing the Internet. Don’t click on pop-up windows even if they aren’t blocked by the browser security or other security solutions. If you follow these simple rules, in 99% of cases a rogue antivirus solution will not be able to penetrate your computer.
Conclusion
Unfortunately, programs designed to extort money from users are becoming more and more common. Instead of the occasional rogue antivirus programs, there is now a steady flow of this type of malware being generated. Cybercriminals are actively developing these malicious programs, modifying everything from the scale and methods of distribution to the techniques used to evade antivirus detection.
It’s likely that the continue evolution of these programs will focus on the technologies used to bypass antivirus detection. The number of programs will probably continue to rise, as will the number of users who fall for them.
The growing popularity of rogue antivirus solutions among cybercriminals suggests that this is a very profitable business. The scare tactics used increase the likelihood of success. Once again, we recommend installing a legitimate antivirus solution. This way you can be sure your computer has reliable protection and you haven’t just thrown your money away.






















Rogue antivirus: a growing problem