
Earlier this week, we published our report on “Red October”, a high-level cyber-espionage campaign that during the past five years has successfully infiltrated computer networks at diplomatic, governmental and scientific research organizations.
In part one, we covered the most important parts of the campaign: the anatomy of the attack, a timeline of the attacker’s operation, the geographical distribution of the victims, sinkhole information and presented a high level overview of the C&C infrastructure.
Today we are publishing part two of our research, which comprises over 140 pages of technical analysis of the modules used in the operation.
When analyzing targeted attacks, sometimes researchers focus on the superficial system infection and how that occurred. Sometimes, that is sufficient, but in the case of Kaspersky Lab, we have higher standards. This is why our philosophy is that it’s important to analyze not just the infection, but to answer three very important questions:
- What happens to the victim after they’re infected?
- What information is being stolen?
- Why is “Red October” such a big deal compared to other campaigns like Aurora or Night Dragon?
According to our knowledge, never before in the history of ITSec has an cyber-espionage operation been analyzed in such deep detail, with a focus on the modules used for attack and data exfiltration. In most cases, the analysis is compromised by the lack of access to the victim’s data; the researchers see only some of the modules and do not understand the full purpose of the attack or what was stolen.
To get around these hiccups, we set up several fake victims around the world and monitored how the attackers handled them over the course of several months. This allowed us to collect hundreds of attack modules and tools. In addition to these, we identified many other modules used in other attacks, which allowed us to gain a unique insight into the attack.
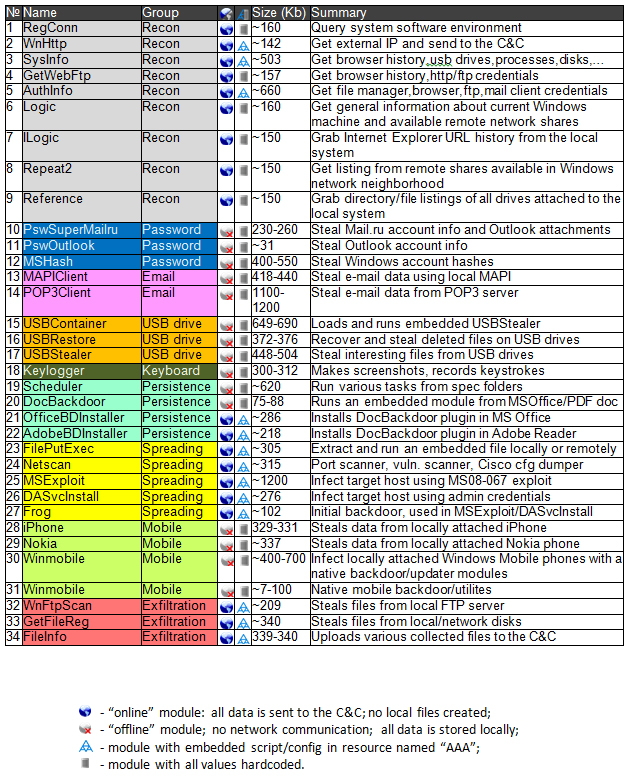
The research that we are publishing today is perhaps the biggest malware research paper ever. It is certainly the most complex malware research effort in the history of our company and we hope that it sets new standards for what anti-virus and anti-malware research means today.
Because of its size, we’ve split “part 2” in several pieces, to make reading easier:





















“Red October” – Part Two, the Modules