
In February this year, a curious backdoor passed across our virtual desk. The analysis showed the malware to have a few quite unpleasant features. It can spread itself over a local network via an exploit, provide access to the attacked network, and install miners and other malicious software on victim computers. What’s more, the backdoor is modular, which means that its functionality can be expanded with the aid of plugins, as required. Post-analysis, the malware was named Backdoor.Win32.Plurox.
Key features
Plurox is written in C and complied with Mingw GCC, and judging by the presence of debug lines, the malware was at the testing stage when detected.
The backdoor uses the TCP protocol to communicate with the C&C server; plugins are loaded and directly interfaced via two different ports, which are stitched into the body of Plurox; the C&C addresses are also hardcoded into the bot. When monitoring the malware’s activity, we detected two “subnets.” In one, Plurox receives only miners (auto_proc, auto_cuda, auto_gpu_nvidia modules) from the C&C center, while in the other, besides miners (auto_opencl_amd, auto_miner), it is passed several plugins, which will be discussed later.
The Plurox family has virtually no encryption, only a few 4-byte keys are applied for the regular XOR cipher. The packet for calling the C&C server looks as follows:
The buffer contains an XORed string with the key at the start of the packet. The response from the C&C center contains the command to be executed, plus data for its execution, which is encrypted using XOR. When the plugin is loaded, the bot itself selects the required bitness and requests both auto_proc and auto_proc64. In response there arrives a packet with an encrypted plugin, the usual MZ-PE.
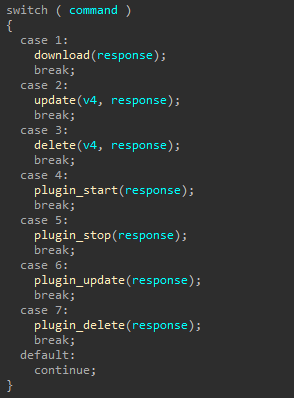
Supported commands
The Plurox version we found supports a total of seven commands:
- Download and run files using WinAPI CreateProcess
- Update bot
- Delete and stop (delete own service, remove from autoload, delete files, remove artifacts from registry)
- Download and run plugin
- Stop plugin
- Update plugin (stop process and delete file of old version, load and start new one)
- Stop and delete plugin
Plugins
During the monitoring, we managed to detect several Plurox plugins and study them all.
Plugin miners
The malware can install on the victim computer one of several cryptocurrency miners, depending on the particular system configuration. The bot sends the package with the system configuration to the C&C server, and in response it receives information about which plugin to download. We counted eight mining modules in total, whose features can be guessed from their names:
- auto_proc
- auto_cuda
- auto_miner
- auto_opencl_amd
- auto_gpu_intel
- auto_gpu_nvidia
- auto_gpu_cuda
- auto_gpu_amd
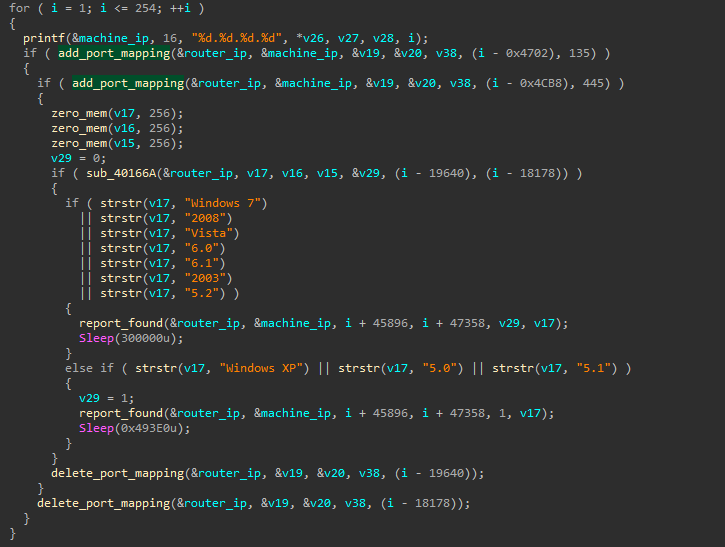
UPnP plugin
The module receives from the C&C a subnet with mask /24, retrieves all IP addresses from it, and attempts to forward ports 135 (MS-RPC) and 445 (SMB) for the currently selected IP address on the router using the UPnP protocol. If successful, it reports the result to the C&C center, waits for 300 seconds (5 minutes), and then deletes the forwarded ports. We assume that this plugin can be used to attack a local network. It would take an attacker just five minutes to sort through all existing exploits for services running on these ports. If the administrators notice the attack on the host, they will see the attack coming directly from the router, not from a local machine. A successful attack will help the cybercriminals gain a foothold in the network.
According to its description, the plugin is very similar to EternalSilence, except that port 135 is forwarded instead of 139. See this Akamai article for details of EternalSilence:
{"NewProtocol": "TCP", "NewInternalPort": "445", "NewInternalClient": "192.168.10.165",
"NewPortMappingDescription": "galleta silenciosa", "NewExternalPort": "47622"}
And here’s the Plurox plugin template:
<NewInternalPort>%d</NewInternalPort>
<NewInternalClient>%s</NewInternalClient>
<NewEnabled>1</NewEnabled>
<NewPortMappingDescription>galleta silenciosa</NewPortMappingDescription>
In the two examples, a matching line is highlighted — a description of port forwarding.
SMB plugin
This module is responsible for spreading malware over the network using the EternalBlue exploit. It is identical to the wormDll32 module from Trojan.Win32.Trickster, but with no debug lines in the code, plus the payload in the exploit is loaded using sockets.
As can be seen in these samples, not only is the injected code similar, but also the code for standard procedures. Based on this, we can assume that the analyzed samples were taken from the same source code (commented lines in the Trickster plugin are missing in the Plurox plugin), which means the respective creators of Plurox and Trickster may be linked.
Kaspersky security solutions detect the bot and its plugins with the verdicts Backdoor.Win32.Plurox and HEUR:Trojan.Win32.Generic.
IoC
C&C servers
- 178.21[.]11.90
- 185.146[.]157.143
- 37.140[.]199.65
- 194.58[.]92.63
- obuhov2k[.]beget[.]tech
- webdynamicname[.]com
- 37.46[.]131.250
- 188.93[.]210.42
MD5
- Main body
- 59523DD8F5CE128B68EA44ED2EDD5FCA
- C4A74D79030336A0C3CF60DE2CFAE9E9
- CECFD6BCFDD56B5CC1C129740EA2C524
- BE591AA0E48E496B781004D0E833E261
- Trickster Worm module
- f233dd609821c896a4cb342cf0afe7b2
- auto_proc32
- 2e55ae88c67b1d871049af022cc22aac
- auto_proc64
- b2d76d715a81862db84f216112fb6930
- auto_opencl_amd32
- a24fd434ffc7d3157272189753118fbf
- auto_opencl_amd64
- 117f978f07a658bce0b5751617e9d465
- auto_miner32
- 768857d6792ee7be1e1c5b60636501e5
- auto_miner64
- e8aed94c43c8c6f8218e0f2e9b57f083
- upnp32
- 8cf5c72217c1bb48902da2c83c9ccd4e
- upnp64
- b2824d2007c5a1077856ae6d8192f523
- smb32
- 6915dd5186c65891503f90e91d8716c6
- smb64
- cd68adc0fbd78117521b7995570333b2
Plurox: Modular backdoor


























stuart
Thanks for the research. Few questions – how is it being spread – phishing emails? Who was it being sent to (industry vertical, geographic region?) How many infections, or was this just a test run you saw? How many AV vendors are picking it up?
Technical research is all well and go, it’s the ‘how’ of the malware. But as cyber security teams, we also need to know the who, where, what, why. The malware might be the most vicious ever found, but if it’s only being sent to email addresses in the Middle East (say), I’m going to be less concerned than if it were being sent to organisations in my industry and country.
No
Links to tradingbot.zip in youtube scam video descriptions. They also order 100s of bot accounts to like and comment so it looks real.