
We regularly see Trojans being sent via IM. There’s a whole range of approaches used, from standard messages saying ‘Hey, take a look at my photos’ or links which purportedly lead to useful utilities, to social engineering which plays on people’s fears:
![]()
[Translation: Look what’s been written about you here]
Of course, the pages linked to are stuffed with exploits which are used to turn the victim machine into a malware menagerie.
There’s nothing new in these mailings. But today we got another example of a mailing that’s been going on for the last three weeks or so – every day, millions of ICQ users are being sent the following message:
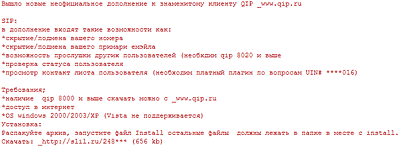
SIP:
The add-on includes options such as:
*hide/ fake your number
*hide/ fake your primary email
*eavesdrop on other users (requires qip 8020 or higher)
*check user status
*view user’s contact list (requires paid plug-in enquiries to UIN# ****016)
Requirements:
*qip 8000 or higher can be downloaded from _www.qip.ru
*Internet access
*Windows 2000/2003/XP (Vista not supported)
Installation:
Unpack the archive, launch the Install file remaining files should be located
in the folder together with install.
Download: _http://slil.ru/248### (656 kb)
Although the link does change, sometimes the same link gets sent twice in one day – it depends how quickly antivirus companies react to the latest malware that’s placed on the link. If the user is incautious or uninformed enough to click on the link, his or her machine ends up infected with a variant of the ever popular Trojan-PSW.Win32.LdPinch.
We took a look at all the different variants that have been downloaded, and discovered that:
- An old version of Pinch is being used, and this version is freely available – for each wave of mailings, the malware simply gets packed with different packers.
- To start with, Pinch sent its log files off using public SMTP servers, but then moved to using a script gate on a free hosting site.
- The recipient’s email is the same in all cases.
Pinch is a true omnivore – it grabs just about everything it can from the victim machine: the Windows license number, system information, a list of programs installed, as well as ICQ, email and FTP passwords, and passwords saved to Windows Protected Storage.
On the most productive days, the person behind the mass mailings managed to collect up to a hundred logs. And his e-store has a whole bunch of ICQ numbers for sale, presumably stolen from victim machines. He’s clearly out to make money – given that malware writers have made the shift from simple disruption to clearly criminal activity, that’s no surprise. However, what he maybe doesn’t realize is that a careful analysis of Pinch leads to a wealth of information about the author – name, date of birth, town, mobile number and various other personal data.
Good news for those fighting cyber crime, but not so great for those involved in illegal activity.




















Pinch pinched