
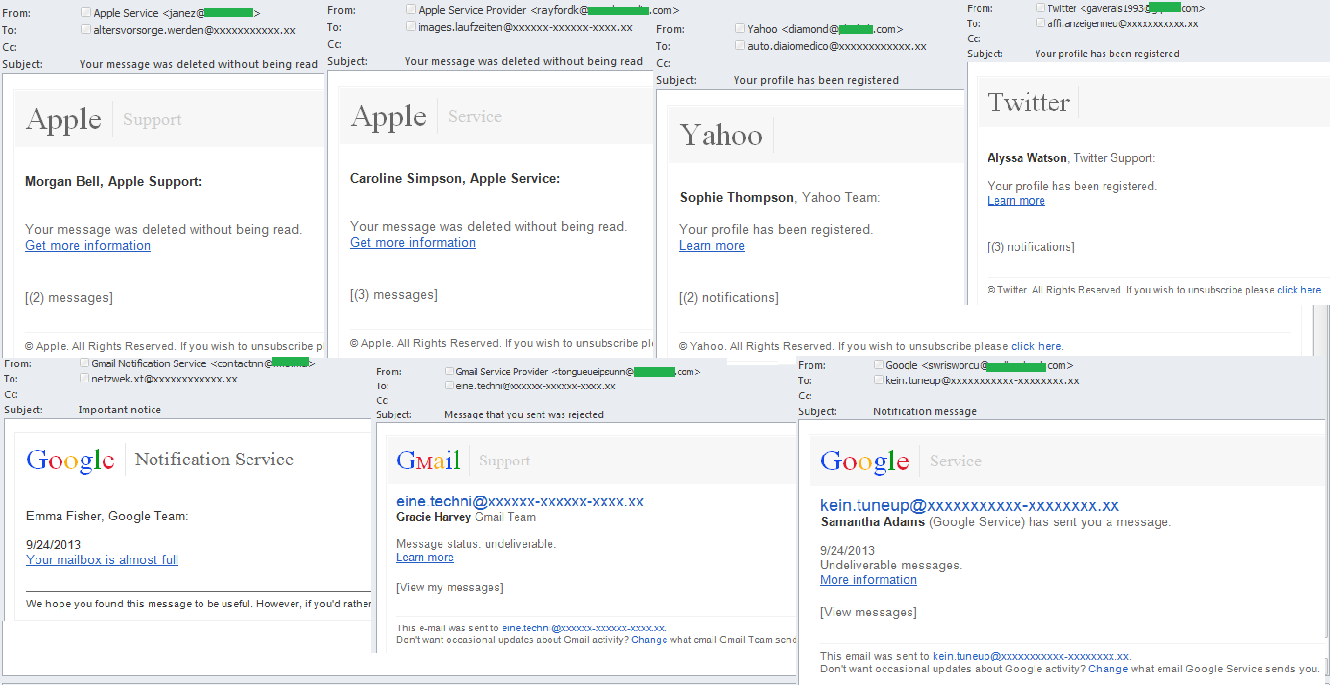
Adverts for medication to improve male sex drive are a staple of spam mailings. Like any other unsolicited messages, emails of this nature have evolved with time and today’s versions no longer merely contain promises of enahnced potency and a link to a site selling pills. In August and September we noted a series of mailings that used the names of well-known companies, that looked just like typical phishing messages. However, instead of a phishing site the links they contained led to an advert for “male medication”.
All the messages in the mailings were made to look as though they had come from FedEx, Google, Twitter, Yahoo and other popular companies and services. One of those names was usually used in the ‘From’ field of the messages. The text body in the messages imitated official letters from the companies, including logos and signatures from ficticious employees. It was all meant to convince recipients that the emails were genuine. But an attentive user would easily notice from the sender’s address that it was anything but genuine, and was most probably generated automatically. There were several variants of message within a mass mailing.
The spammers used a number of pretexts to get users to click the links. For example, some emails imitated legitimate messages about undelivered emails, profile registration, deleting of unread emails, etc. The messages were intentionally very short, prompting the recipient to click the link in order to find out more information. But the link actually redirected to an advertising site for pharmaceutical spam.
Other variants included reminders about a new message or notifications. The received date was shown in the body of the message while the field ‘View messages’ contained a hidden link that led to an advert for male pills.
In some mailings the spammers also used different color designs – bright colors for the links and the company names. The subjects of the emails were pretty standard phrases about receiving a message, the need to activate an account and so on.
At the beginning of August we detected another mass mailing similar to those described above, but of a much higher standard. The message was written on behalf of Google, or to be more precise made to look like an automated notification from a service called Google Message Center. The sender’s address is supposedly located in the google.com domain, and most users could easily be forgiven for thinking it was a genuine address associated with Google. The message from the malicious sender notified the recipient about a new email that had supposedly sent to his/her address, and provided a link. In a bid to outwit spam filters the spammers changed the encoding of a few letters in the links to ASCII. For example, the letter ‘s’ became the number 73. The spammers also used the Google Translate service to disguise the real link – it’s a popular trick that, together with the subject of the message and other ‘noise’, can be quite effective. However, the recipient needs only place the cursor over the link for its true nature to be revealed.
The URL sent out in this mailing also leads to a site advertising pharmaceutical goods. By using noise the spammers can make the same link unique for every message, because each time different letters are encoded using ASCII.
It looks like the majority of users now don’t bother opening messages with traditional pharmaceutical spam themes, so the spammers have turned to the sort of tricks associated with phishers. While the obfuscated links used by the spammers may be seen as less harmful than the criminal actions of phishers who lure users to fraudulent sites or malicious files, we still recommend being very wary about opening any official-looking emails and don’t click any links inside these messages.
























Pharmaceutical ‘Phishing’