
The adware PBot (PythonBot) got its name because its core modules are written in Python. It was more than a year ago that we detected the first member of this family. Since then, we have encountered several modifications of the program, one of which went beyond adware by installing and running a hidden miner on victim computers:
Two other versions of PBot we detected were restricted to the goal of placing unwanted advertising on web pages visited by the victim. In both versions, the adware initially attempts to inject a malicious DLL into the browser. The first version uses it to run JS scripts to display ads on web pages, the second — to install ad extensions in the browser. The latter is the more interesting of the two: developers are constantly releasing new versions of this modification, each of which complicates the script obfuscation. Another distinctive feature of this Pbot variation is the presence of a module that updates scripts and downloads fresh browser extensions.
Throughout April, we registered more than 50,000 attempts to install PBot on computers of users of Kaspersky Lab products. The following month this number increased, indicating that this adware is on the rise. PBot’s target audience is mainly in Russia, Ukraine, and Kazakhstan.
Distribution methods
PBot is generally distributed through partner sites whose pages implement scripts to redirect users to sponsored links.
Here is the standard PBot propagation scheme:
- The user visits the partner site.
- When any point on the page is clicked, a new browser window pops up that opens an intermediate link.
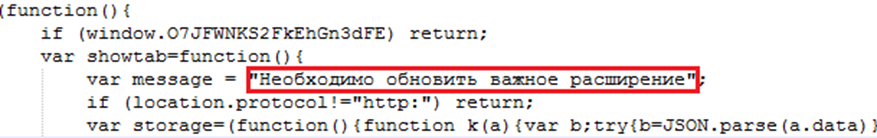
- The intermediate link redirects the user to the PBot download page, which is tasked with downloading and running the adware on the victim computer by hook or by crook. The following is a section of code from one such page:
- An HTA file is downloaded. On startup this file downloads the PBot installer.
Operating logic
PBot consists of several Python scripts executed in sequence. In the latest versions of the program, they are obfuscated using Pyminifier.
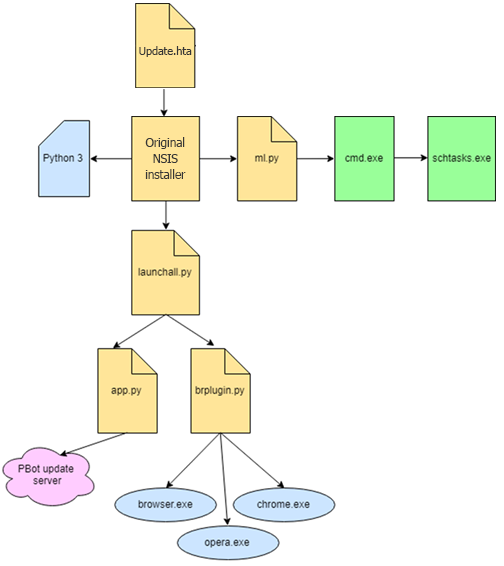
In the new versions of PBot, modules are executed according to the following scheme:
- The source file *.hta downloads an executable file, which is the NSIS installer of PBot, to %AppData%.
- The installer drops a folder with the Python 3 interpreter, Python scripts, and a browser extension into %AppData%.
- Using the subprocess library, the ml.py script adds two tasks to Windows Task Scheduler. The first is tasked with executing ml.py when the user signs into the system, while the second runs app.py daily at 5:00. In addition, the winreg library is used to write the app.py script to the autoloader.
- The launchall.py script runs app.py, which handles the update of PBot scripts and the download of new browser extensions.
- Next, launchall.py checks whether the following processes are active:
- browser.exe
- chrome.exe
- opera.exe
- If the processes are found, the DLL-generating script brplugin.py is started. The resulting DLL is injected into the launched browser and installs the ad extension.

The browser extension installed by PBot typically adds various banners to the page, and redirects the user to advertising sites.
Conclusion
In pursuit of profit, adware owners often resort to installing their products on the sly, and PBot developers are no exception. They release new versions (and update them on user computers), complicating their obfuscation to bypass protection systems.
Kaspersky Lab solutions detect PBot with the following verdicts:
AdWare.Win32.PBot
AdWare.NSIS.PBot
AdWare.HTML.PBot
AdWare.Python.PBot
IoCs:
3cd47c91d8d8ce44e50a1785455c8f7c
1aaedcf1f1ea274c7ca5f517145cb9b5
bb2fbb72ef683e648d5b2ceca0d08a93
23e7cd8ca8226fa17e72df2ce8c43586
ad03c82b952cc352b5e6d4b20075d7e1
0cb5a3d428c5db610a4565c17e3dc05e
3a6ad75eb3b8fe07c6aca8ae724a9416
184e16789caf0822cd4d63f9879a6c81
























Pbot: evolving adware