
The “off-by-one” vulnerability is an old concept. Here is a description from Wikipedia:
An off-by-one error (OBOE) is a logical error involving the discrete equivalent of a boundary condition. It often occurs in computer programming when an iterative loop iterates one time too many or too few. Usually this problem arises when a programmer fails to take into account that a sequence starts at zero rather than one (as with array indices in many languages), or makes mistakes such as using “is less than or equal to” where “is less than” should have been used in a comparison.
Such an error can lead to DOS or even, in some cases, code execution. There are many resources online describing the exploitation of “off-by-one heap overflow”.
Now, why “Off-by-one 2.0”?
While reading my Twitter feed, I noticed something really interesting. A tweet from an official business account included a shortened URL (bit.ly) that led to a site providing a Potentially Unwanted Application.
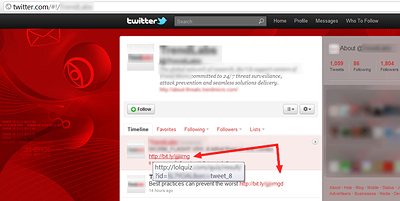
If you look closely on the screenshot, you will see two similar bit.ly links. One of them is missing the letter “d”, hence the “Off-by-one 2.0”.
Because of a simple copy-and-paste error, the new URL leads to a totally different site. I was rather cautious and checked the website with http://web-sniffer.net.
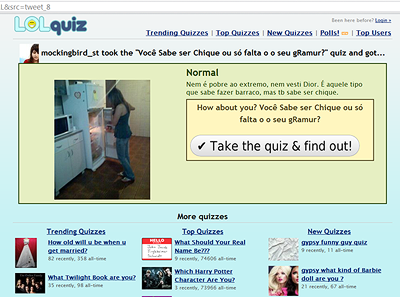
Here is the website you get when following the original tweet:
As the domain name implies, it is a quiz site, but it does look fishy. I have seen many sites similar to this one in the past doing malicious things.
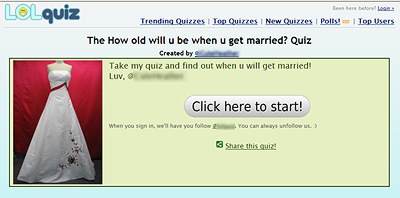
I therefore decided to investigate and I clicked on a random quiz:
Using a test machine and a test Twitter account, I accepted the prompt to start the quiz. They clearly say that if you sign in, you are going to follow their Twitter account.
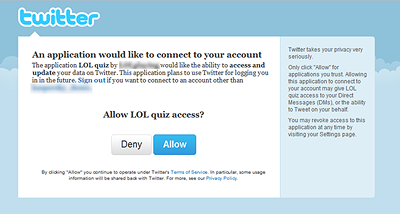
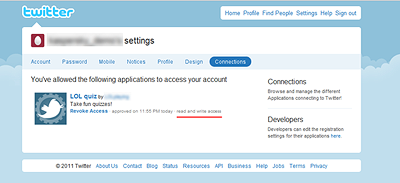
Surprisingly, I ended up on Twitter again, and was asked to authorize an application to access my Twitter account as you can see below:
Using my test account, I authorized the application and was redirected to the quiz that was originally offered:
What did the application do?
By allowing that application to install, I granted read and write access to my Twitter account as you can see below:
As soon as the application was granted access, it automatically followed the “lolquiz” Twitter account. This behavior was announced on the website, in a sentence with very small print, that I missed first time round.
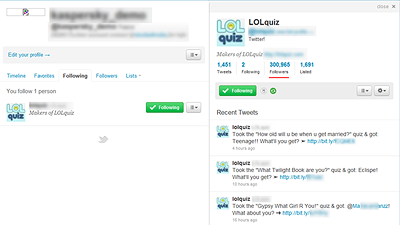
My test account is now following the authors of this potentially unwanted application.
If you look at the number of followers, more than 300,000(!) users have granted access to the application. I am confident that most of them didn’t read the small print about the auto-follow feature of the application:
It hadn’t tweeted anything as of yet. So I decided to take the quiz and see if something would happen after that:
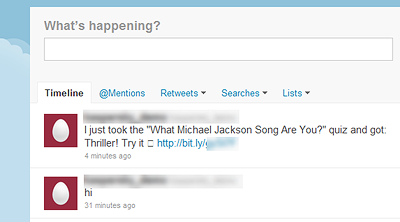
As soon as you take a quiz from their website, the application tweets the result of your quiz. If others want to try the quiz themselves, they will have to grant access to their Twitter account, and will automatically follow “lolquiz” and post on their Twitter feed, thus spreading virally.
It’s interesting to note that the author of that application is following two other similar twitter accounts.
Doing a simple search on Twitter reveals a lot of similar posts by users:
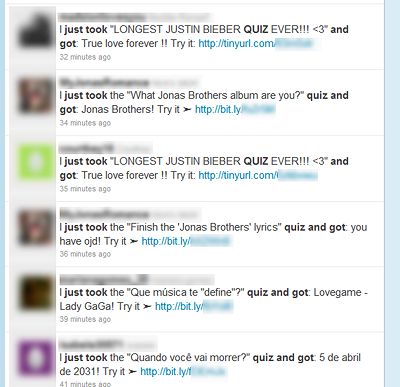
It’s not clear what the real intention of this application is. It is not malicious (so far) but potentially unwanted.
They say that you can un-follow them, but they don’t mention that the installed application still has read and write access to your Twitter feed even if you stop following them. They offer a DM opt-out option, which does not remove the application or stop the auto-tweeting feature.
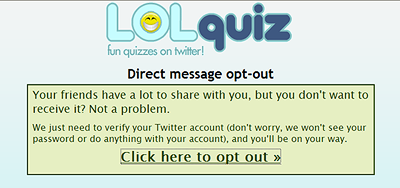
These quiz applications are very common on Facebook, and they now seem to have invaded Twitter as well. This quiz may have been around since 2009.
If the authors of this application change their website to something more dangerous (or if they were to be compromised with malicious links), it could lead to a more serious problem where hundreds of thousands of users could be affected. They have the ability to tweet anything from your account.
My past blog about Rogue AV being spread on Twitter is a good example of what could happen.
I think this proves how dangerous URL shortening services can be, as a simple copy paste mistake can lead to totally different websites, whereas in most cases, on a normal URL, you would end up on a “404 – Page not found”.






















Off-by-one 2.0