
Recently, there have been discussions around the topic that if our product is installed, ExPetr malware won’t write the special malicious code which encrypts the MFT to MBR. Some have even speculated that some kind of conspiracy might be ongoing. Others have pointed out it’s plain and simple nonsense. As usual, Vesselin Bontchev, a legend in IT security, who’s become famous for usually getting things right, said it best:
So, what is going on here? As a wise man once said, “the code doesn’t lie,” so let’s analyze the ExPetr MBR disk infection/wiping code in details.
In a nutshell, the malware does these actions:
- Checks administrator privileges
- Enumerates running processes
- Depending on the processes found, initialize a special runtime config
- Depending on this runtime config, malware execution branches are chosen
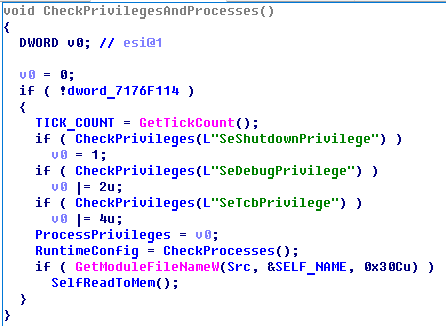 The “check privileges” function
The “check privileges” function
An interesting fact is that malware tries to find several running processes (it calculates a hash from running process names and compares it with several hard-coded values).
The most interesting part that happens here is:
After this condition two malicious functions could be executed:
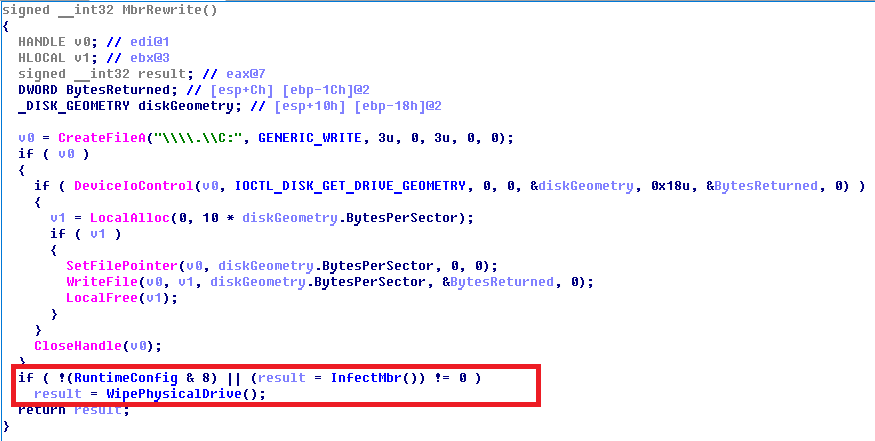
- InfectMbr This routine will write the malicious GoldenEye encryptor code to the MBR. After reboot, this code will encrypt MFT and 1024 bytes of each file.
- WipePhysicalDrive This routine will overwrite the first 10 sectors of the disk with random trash.
Let’s describe this condition in detail:
- The WipePhysicalDrive function will be initiated if:
- the special bit in runtime config is not set (that happens when malware finds the avp.exe running process).
- the InfectMbr function fails.
This is what happens after an initial infection:

Graphic illustration of condition
Very important additions:
- WipePhysicalDrive could be initiated regardless of whether the avp.exe process is running or not. This function will be called when the malware could not write the malicious code to MBR. For example, it could be caused by the activity of other security solutions blocking this write.
- Regardless of whether MBR was infected with malicious code or was overwritten with random trash, malware will still try to encrypt the victim’s files using the AES and RSA ciphers and the attacker’s public key.
Overall, it appears that the group behind ExPetr have built what is usually called a stone soup. This is a mix of old code, new code, dirty hacks, test checks and parts of unusual code. For instance, there is a special condition block in which the AES file encryption doesn’t run at all, however, this condition is always false. It very much looks like something that was rushed out the door before it was polished and ready, from many points of view.
Why the rush, you may wonder? We do not know, but there could be several explanations. One of them could be they tried really hard to catch the EternalBlue/EternalRomance “train”. After WannaCry, a lot of organizations started patching their Windows installations to close these vulnerabilities, effectively shrinking the window of opportunity. It’s possible the authors of ExPetr wanted to infect as many targets as possible before these exploits were widely patched.
Despite the rush, the attackers were obviously aware of our technologies (and other companies’ technologies, obviously), notably System Watcher, which is extremely effective at fighting ransomware. System Watcher works by collecting information about the suspicious actions of running programs and builds a score. For instance, when a program reads a full file in memory, it then writes another file of similar size yet different format, then deletes the original, and the score increases. Other similar known bad behavior is used to increase the score and good behavior to decrease it. If multiple malicious actions happen several times, over and over, the score can reach a threshold where it’s pretty obvious that something is wrong. In that case, System Watcher warns the user and offers to terminate the offending process and restore the data.
To fight against this technology, the ExPetr authors have included multiple “counter measures.” One of them is to avoid writing the GoldenEye encryptor code to the MBR if our product is running. This is done in order to prevent raising the suspicion score and getting terminated too early. It actually seems that they put significant energy into trying to bypass our products and target our users, meaning they were pretty worried about being stopped. Nevertheless, these didn’t work too well, reinforcing the theory of a big pile of hacks, put together in a rush. The System Watcher component fires anyway and stops the file encryption, terminating the process and undoing the changes.
To conclude, our users have been protected despite the measures built into ExPetr to target them.
So why we are writing this longer explanation? With complex malware code and retro measures built to bypass antivirus products, it is complicated to understand all the functionality of today’s malware. It is easy to get tricked and believe certain code checks give a free pass to Kaspersky users. In reality, they were intended as a means of trying to pass under the System Watcher’s radar. In the end, it didn’t work. Our users do not need a free pass from ExPetr, since they have an universal “free pass” from our products and System Watcher.
No Free Pass for ExPetr






















Woat
I noticed a “CheckPrivilegesAndInitConfig()” function being called but not “CheckPrivilegesAndProcesses()”. Where exactly is the “CheckPrivilegesAndProcesses()” function called?