
Pre-holiday spam
Easy money
In the run-up to Christmas and New Year, scam е-mails mentioning easy pickings, lottery winnings, and other cash surprises are especially popular. All the more so given how simple it is to adapt existing schemes simply by mentioning the holiday in the subject line.
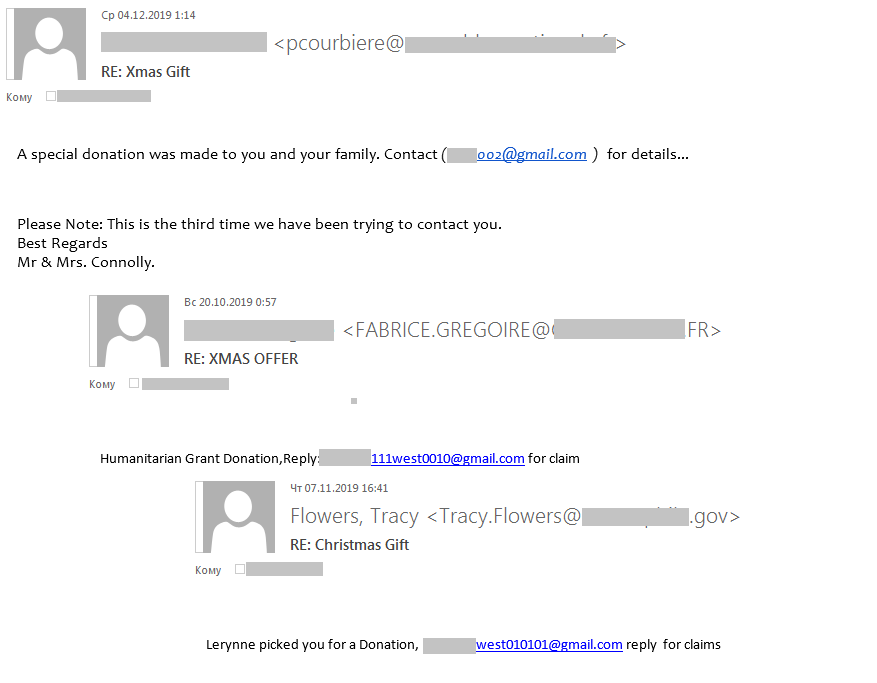
For example, one scam е-mail with the subject line “Xsmas gift” or “Xmas offer” talks about a “special donation” and provides a contact е-mail address for more information. Recipients who respond are lured into parting with a sum of money through social engineering.
Scammers offering “Xmas gifts” are very persistent
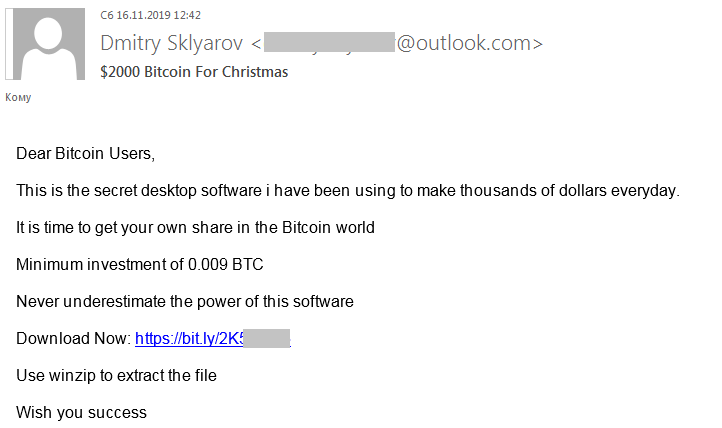
Another Christmas-related scheme aims to steal cryptocurrency. Scammers offer the chance to earn some bitcoins before the holiday period using “secret” software that can be downloaded via a link:
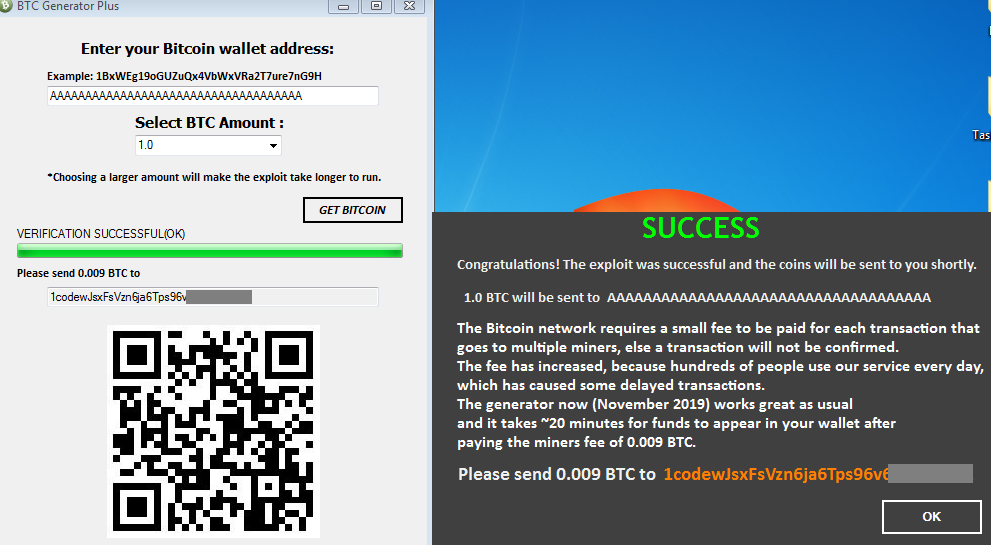
After downloading and running the program (the malware Hoax.Win32.Agent.gen.), the user is prompted to enter their cryptowallet credentials and wait until the request is executed.
Next, the user is informed that the cryptocurrency will be credited to their account immediately after they pay a transfer fee. The result is predictable — the user earns no bitcoins, and the “fee” goes to the scammers.
Extortion
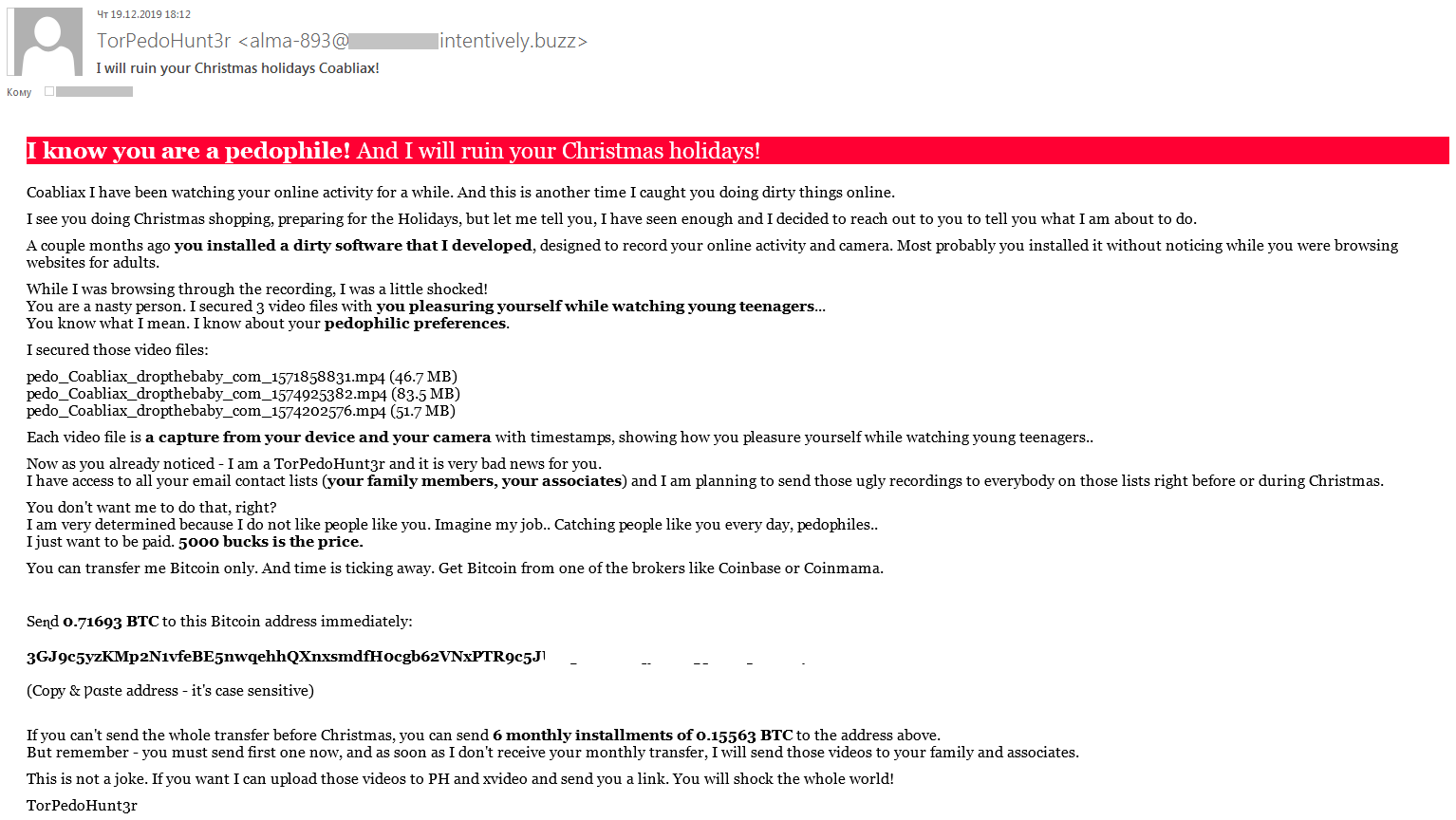
Standard extortion schemes are also adapted for the festive period. For instance, the authors of this е-mail threaten to spoil the victim’s Christmas by smearing them as a pedophile. To prevent this, the recipient needs to transfer the equivalent of $5,000 in bitcoin to the extorters:
Malicious mailings and the corporate sector
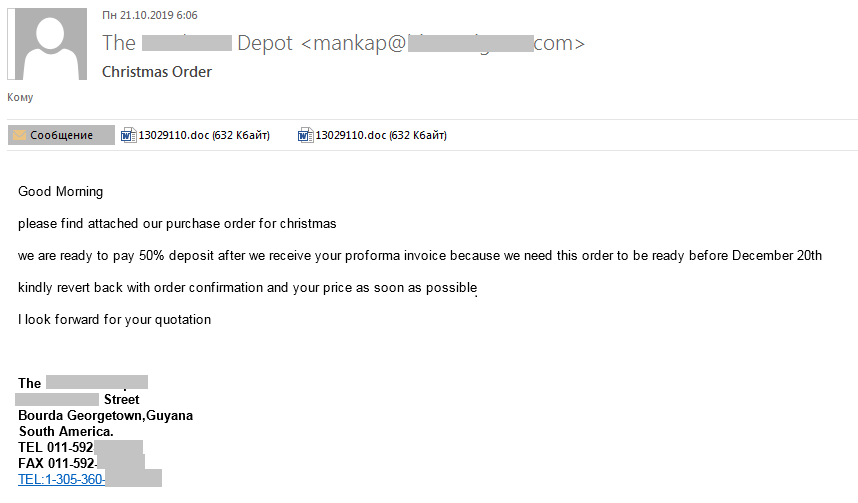
Corporate е-mail addresses are also on the cybercriminal radar. To extract confidential information from recipients, or install malware, scammers mask malicious е-mails as business correspondence. In the pre-holiday period, when sales are on the rise, retail finds itself in a special risk zone. E-mails with malicious attachments (DOC or XLS) are sent under the guise of messages related to orders for goods.
For example, hidden in the attachment to this е-mail is Trojan-Downloader.MSOffice.SLoad.sb, which in turn downloads other malware to the victim’s computer:
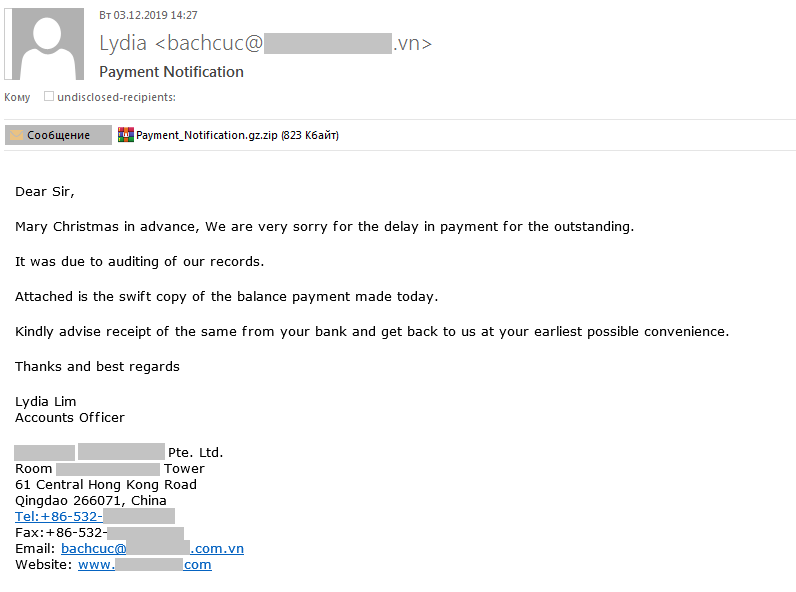
Malicious attachments can also be disguised as invoices and payment notices. The archive attached to this е-mail actually contains the Trojan-PSW.MSIL.Agensla.hdt stealer, which harvests logins and passwords, and then sends them to the cybercriminals:
Statistics
The share of spam as a percentage of world email traffic gradually increased throughout the entire Q4 2019 and in December amounted to 57.26%. Thus it almost reached the maximum value for the second half of the year — 57.78% (which we recorded in August).
A similar picture was observed in Russia. However, in the fall the growth was less pronounced:
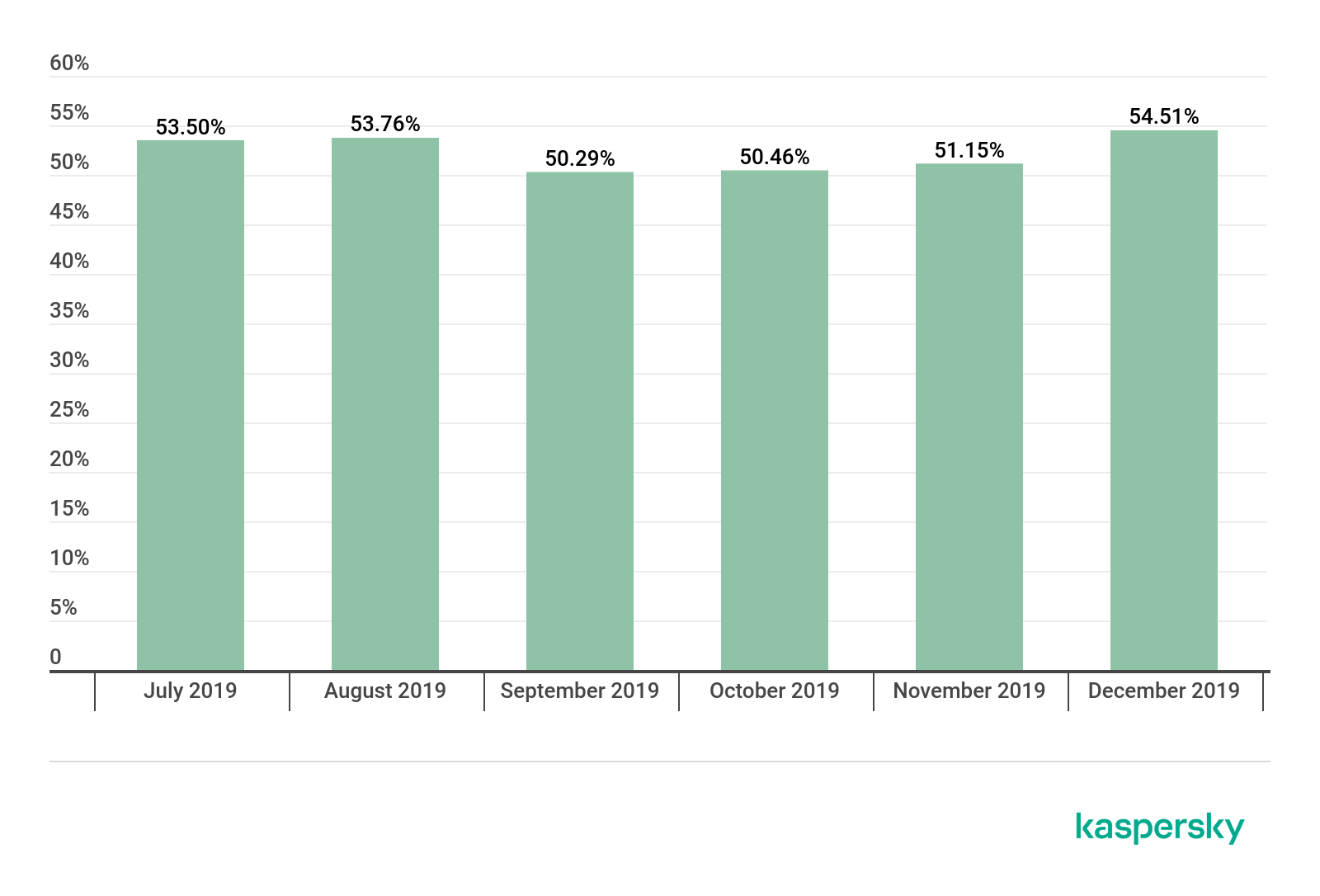
From September to November the amount of spam traffic grew by a total of 0.86 percentage points (compared to a growth rate of 1.14 percentage points for the entire world) to reach 51.15% of total email volume. However, during the last month of the year, the share of spam jumped dramatically by 3.36 p.p. (compared to only 1.44% for the entire world) and exceeded even the summer indicators (54.51% in December as opposed to 53.5 % in July and 53.76% in August). Most likely, such a sharp rise can be attributed to the traditional uptick in holiday season activity by spammers.
In the Asia-Pacific region as a whole, we also observed an increase in the amount of spam in email traffic from September (50.19%) to December (52.62%). As you can see from the diagram, the increase is quite gradual. At the same time, the volume of junk messages reached a peak in January, when their share made 55.48%. This is most likely due to the lunar new year, which is celebrated in most of the countries of the region and which this year fell on January 25.
Christmas/New Year phishing
Fake websites
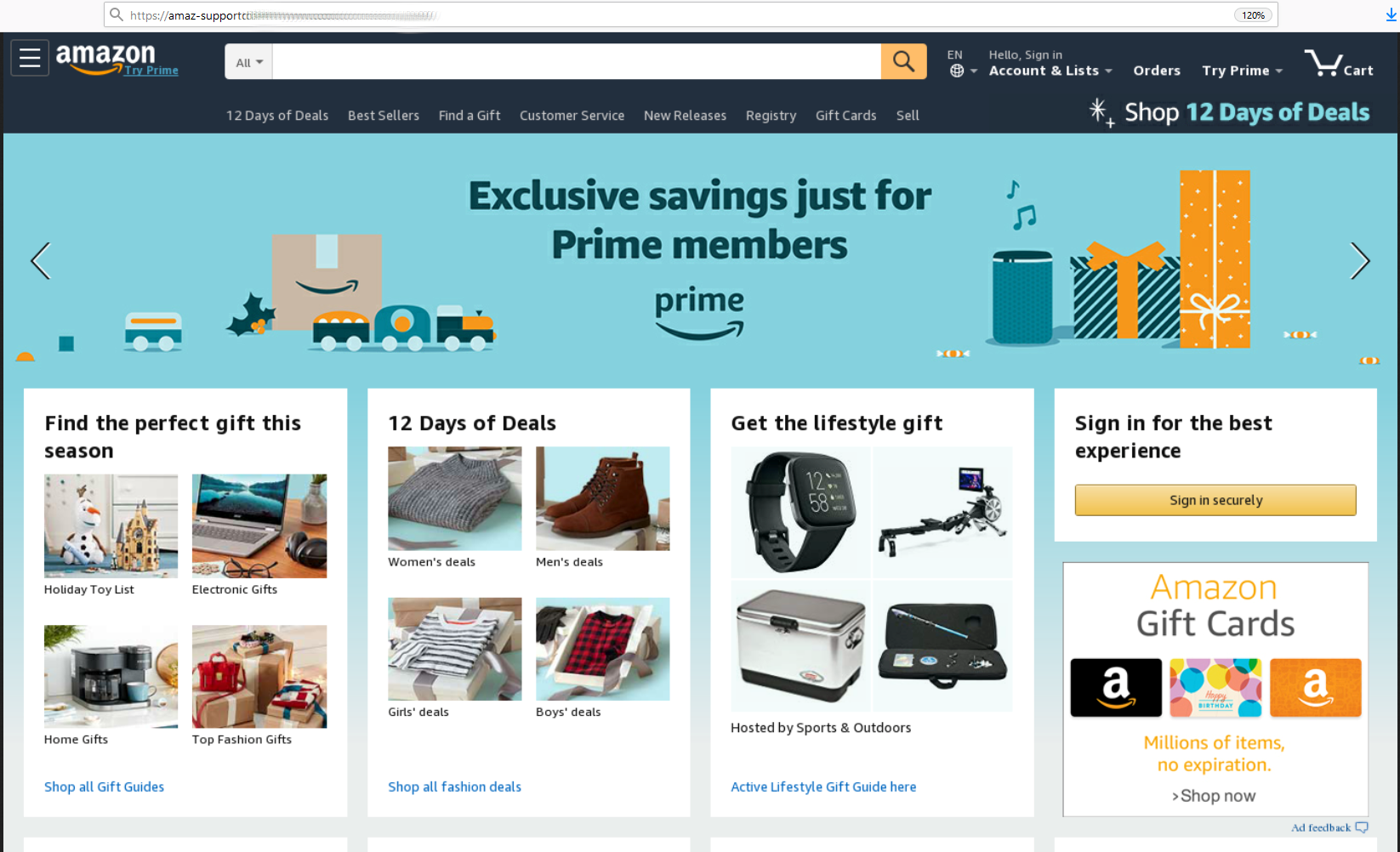
Phishers lured users onto fake pages with the promise of favorable T&Cs, discounts, gifts. For example, they tried to gain access to Amazon Prime accounts by offering Christmas promotions supposedly on behalf of the service; to take part, users were asked to enter their account credentials.
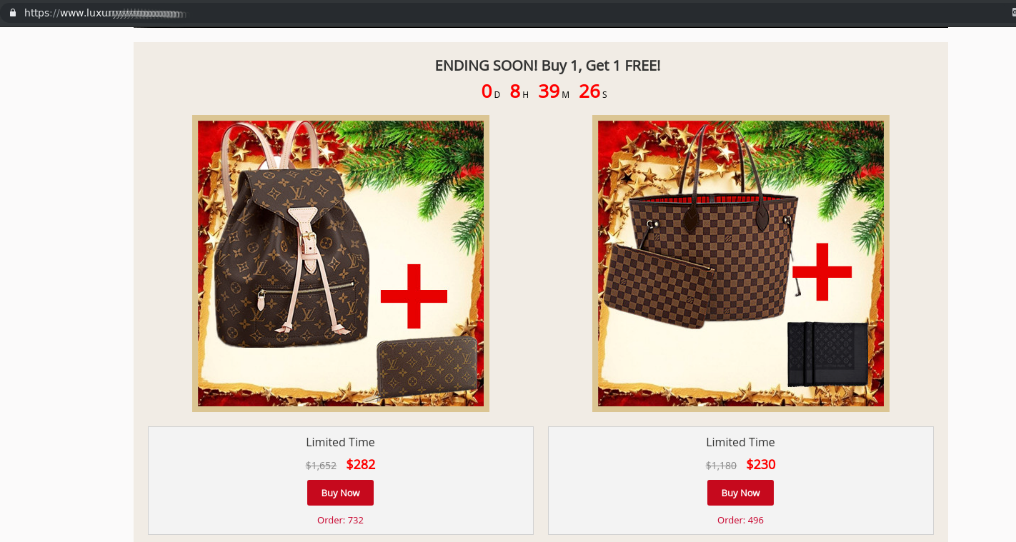
Besides fake versions of real websites, non-existent stores popped up online offering huge discounts. Their catalogs typically contain a very limited range of premium-class products, and the websites themselves look more like landing pages. A characteristic attribute of such sites is a countdown timer showing how much time is left before the “promotion” ends.
In addition to expensive goods, scammers offer libido-boosting drugs — also at great discounts. The product range in such “medical stores” is not very wide:
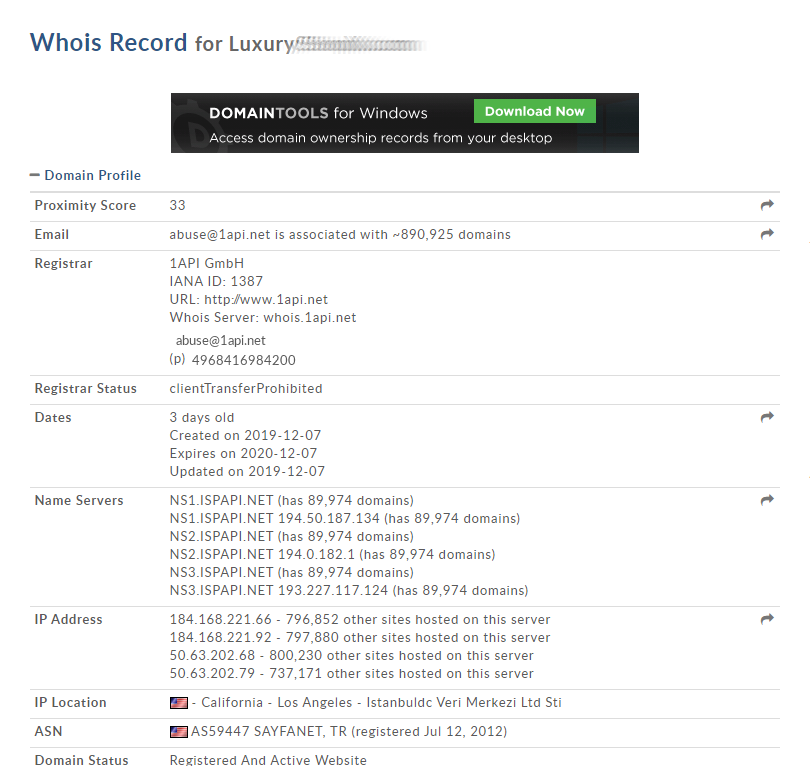
The information about the domain shows that it was registered recently, which is another indicator of fakeness.
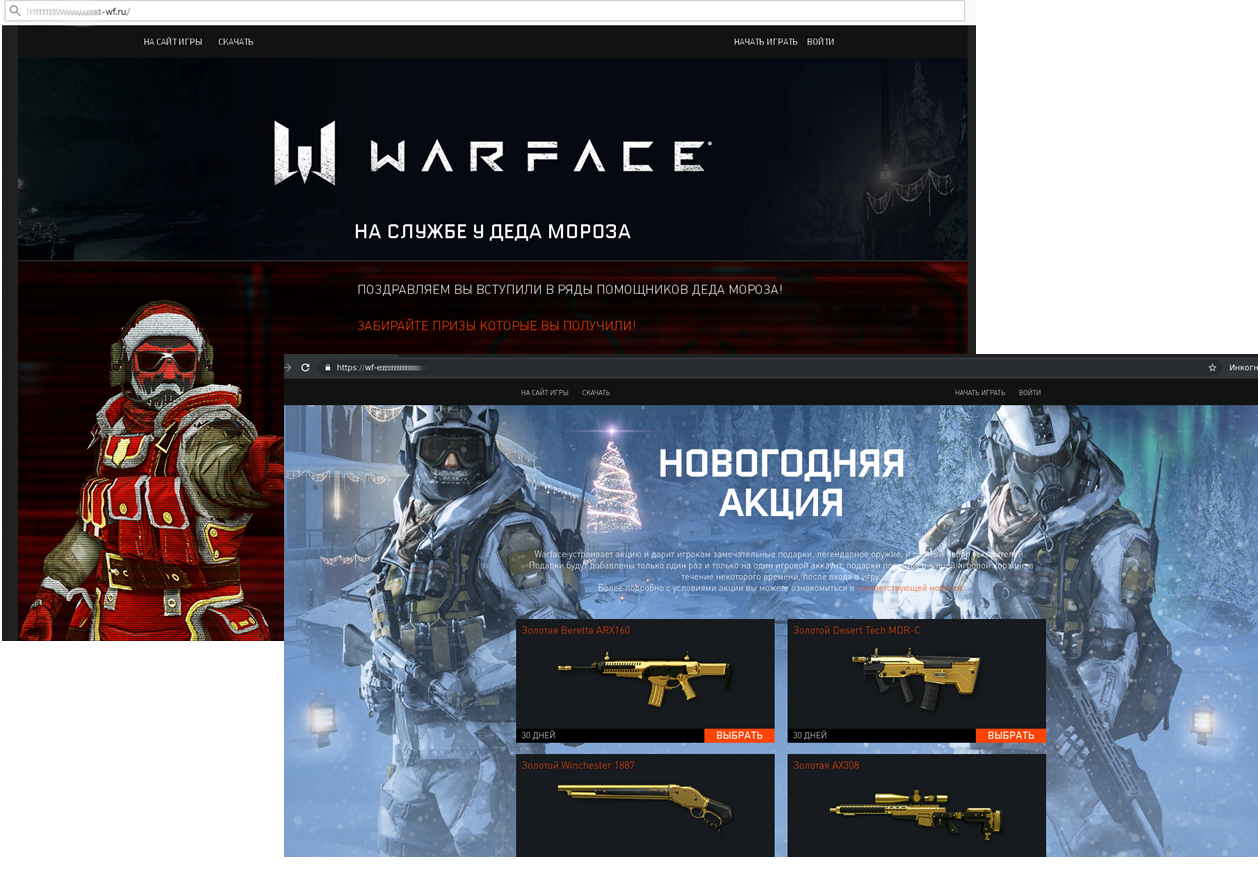
Nor did scammers overlook gamers. For instance, we discovered phishing pages mimicking the Warface multiplayer website. In honor of New Year, one of the fakes promised gamers 30-days’ free use of some powerful weapons, while another presented a golden rifle for joining Santa’s helpers. To receive either “prize,” players had to enter their username and password on a fake login page, thereby giving the scammers access to their account. Accounts with a high in-game rank and unique, paid-for weapons can fetch a good price.
Cash gifts
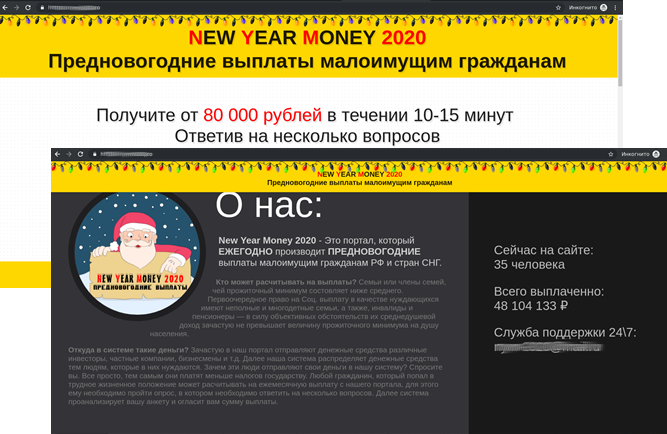
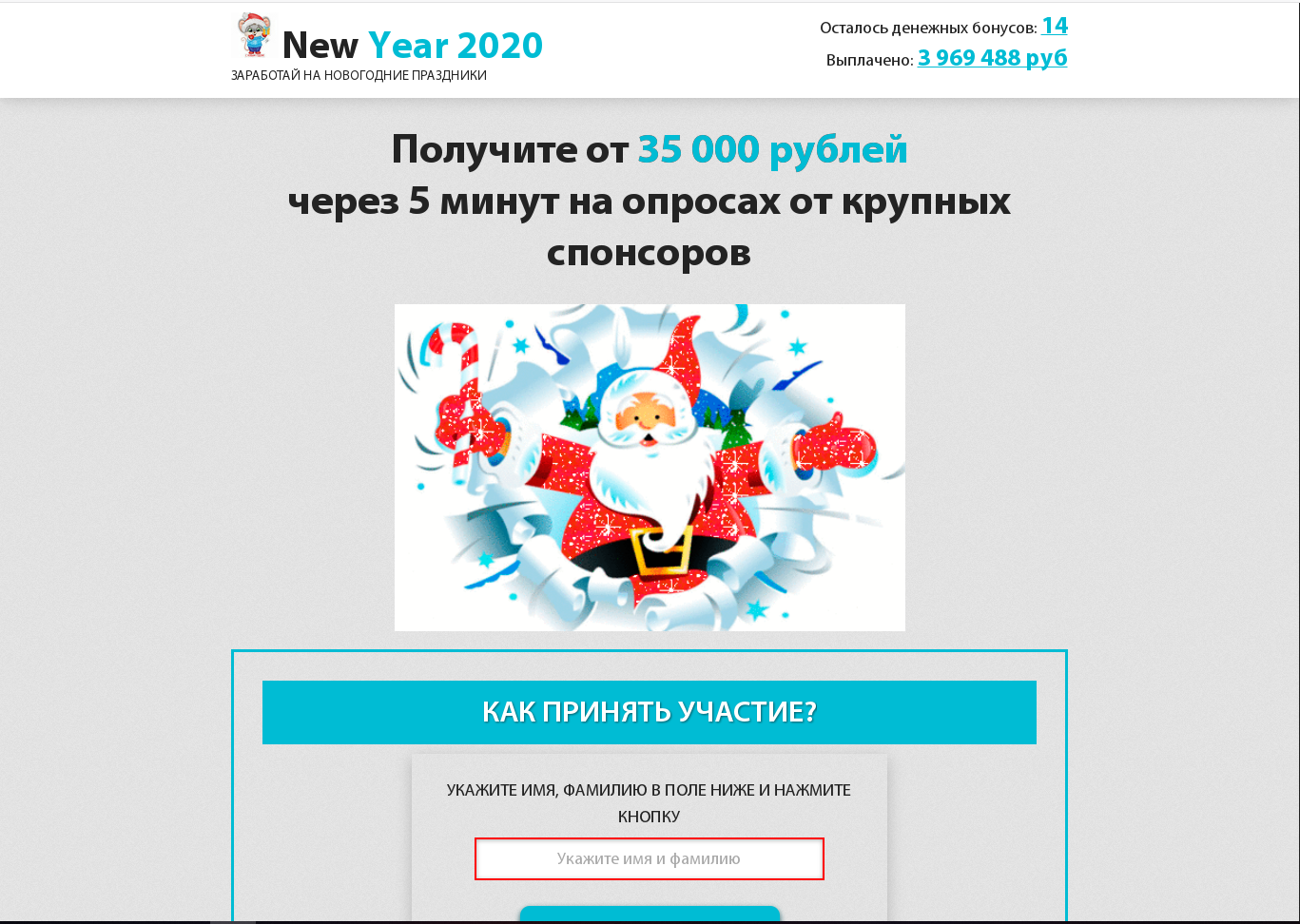
Fake websites promising easy money were also given a festive makeover: they offered New Year payouts to the poor, sponsorship gifts, giveaways, etc. As usual in such cases, visitors are invited to complete a simple task, for example, take a survey and enter some personal data. After a five-digit sum seemingly ready for transfer is displayed on screen, the victim is asked to pay a service fee — which, of course, goes straight to the scammers.
To add credibility and urgency, the attackers place eye-catching information to nudge the victim into acting: notifications about the limited nature of the offer, number of visitors who are currently filling in the form, or a “bonuses” countdown:
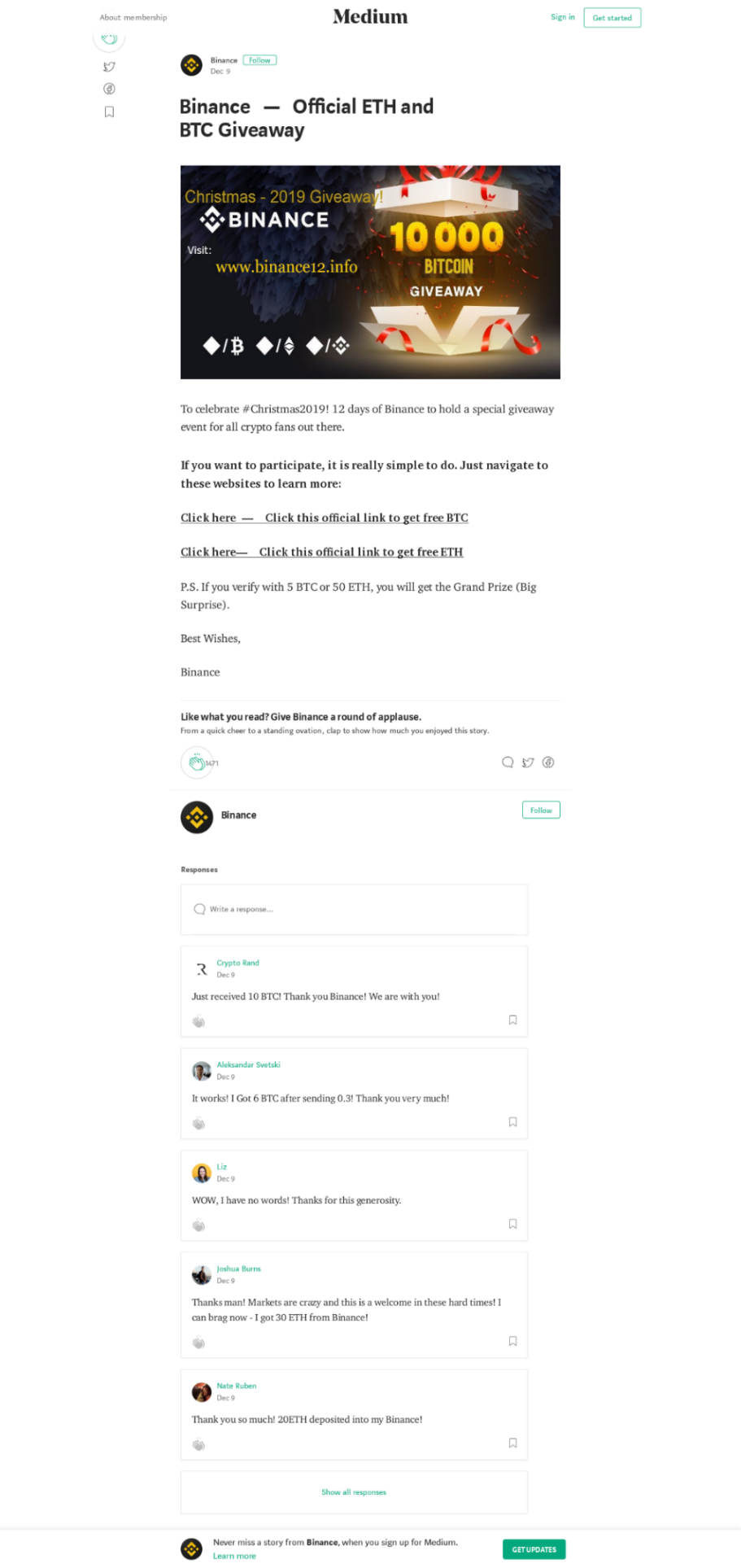
Crypto fans did not escape phishers’ attention either. It was shortly before Christmas that we came across a scheme offering a festive giveaway of bitcoins and ether supposedly from the Binance crypto exchange. Naturally, to receive a “gift” it was necessary to confirm participation by transferring 5 BTC or 50 ETH to the “organizers.”
To promote the “event,” the scammers posted an article about it on the Medium platform with dozens of enthusiastic comments from “winning” users.
Statistics
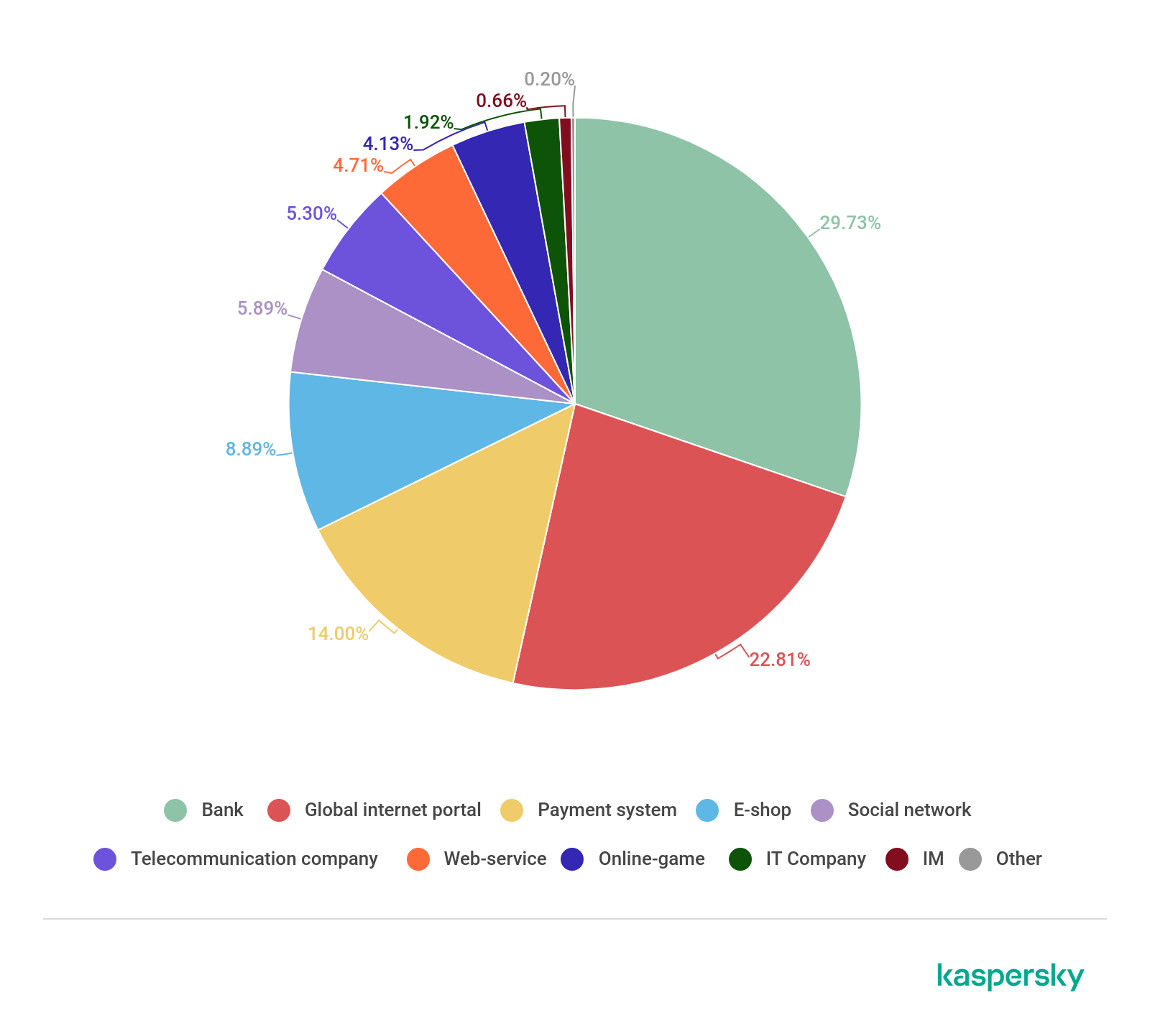
In Q4 2019, the share of attacks that sought to steal financial data and accounts at online banks and stores out of the total number of phishing attacks amounted to 52.61%. This exceeds both the indicator for the previous quarter (43.19%) and the indicator for the whole year (51.4%). We observed a similar situation in 2018 and 2017, with the only difference being that the jump was more noticeable last year — from 44.67% on average for the entire year and 34.67% in Q3 to 51.18% in Q4.

The share of phishing attacks on online stores and financial services during Q3 and Q4 of 2017, 2018, and 2019
It is curious that by the end of 2019, fraudsters had partially lost interest in electronic payment services. For the first time in three years, in Q4 the share of phishing attacks on such resources decreased by 1.21 percentage points compared to the previous reporting period and amounted to 14%.

The share of phishing attacks on online stores and financial services during Q3 and Q4 of 2017, 2018, and 2019
At the same time, the popularity of non-financial categories of websites also fell, and in the ranking of the most popular attack targets for the last quarter, payment services rose from fourth to third place, displacing social networks and blogs, which were attacked only in 5.89% of cases. The leading targets by number of phishing attacks in Q4 were bank resources (29.73%), ahead of global Internet portals (22.81%), which had led the ranking during the previous quarter (23.81%).
We analyzed the number of attacks on major commercial platforms during the period of November 11 to December 31. The number of attacks during this period jumped as expected shortly before Black Friday, which occurred on November 29, and remained at a high level until the Christmas and New Year holidays. In particular, the number of phishing schemes that were perpetrated under the Ebay brand since mid-November has remained at 1% (of the total number of attacks that used the brand for the specified period), and as of November 27, this figure was 3.15%, and as of December 2, it grew by almost one-and-a-half percentage points to 4.63%.

The distribution of phishing attacks using the Ebay brand by day, November 11, 2019 — December 31, 2019
We observed a similar situation with phishing attacks that utilized the Alibaba brand:
The peak of activity occurred on November 27 and lasted until December 4. In both cases there was a short break in fraudulent activity in the middle of December: On December 15 it fell practically to zero, but it again began to rise with the approach of Christmas and New Year.

The distribution of phishing attacks using the Alibaba brand by day, November 11, 2019 — December 31, 2019
Tips and recommendations
So as not to fall for scams and tricks, it is important to take easy money offers with a massive pinch of festive salt.
If you are a consumer:
- Remember that the only free cheese is in a mousetrap. If you are suddenly offered a reward for taking part in a survey, or a huge discount on luxury goods, be very wary.
- Do not follow links in е-mails or messages in social networks if you have even the slightest doubt.
- Be very careful when making purchases on unfamiliar websites. If an online store has few products, it might not be real. If the URL of a well-known website seems strange, that too is cause for concern.
- Do not install software from unknown sources advertised in е-mails.
- Use a reliable security solution.
If you are a company employee:
- Read incoming е-mails from strangers with a critical eye. To spot malicious content in business correspondence, we recommend that you first check the sender address and autosignature. If they do not match, it should raise a red flag. It is also worth comparing the information in the е-mail with that on the website of the company in whose name the message was sent — the contact details might be completely different.

























Happy New Fear! Gift-wrapped spam and phishing