
So what else have we found out about Yxe.e, which we discovered yesterday? It spreads via MMS, but attaches a skull and crossbones image to the message, rather than its body. The message includes a link – http://tran******.com – and suggests the recipient has the opportunity to view private information about a Chinese actress called Zhang Zii.
Following the link from a victim device results in an offer to download and install a file called LanPackage.sisx, which is 57573 bytes in size. But following the link from a browser installed on a computer simply results in a 404:
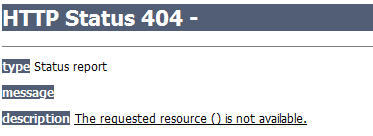
In other words, the server’s checking whether the request to connect to the site is coming from a mobile device browser.Once LanPackage.sisx is run, this message is shown:

And the certificate looks like this:
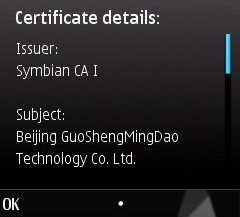
If the user says they want to install, the following files get copied to the device:
• C:sysbinInstaller_SV.exe
• C:sysbinLanPackage.exe – the worm executable
• C:private101f875aimport[20028B98].rsc
Once installed, the worm starts harvesting data about the smart phone; uploading the data to the cybercriminal server; sending SMS messages containing a link to itself to all contacts in the address book; attempting to terminate AppMngr, TaskSpy, Y-Tasks, ActiveFile, TaskMan; and blocking access to Software Manager in order to prevent itself from being deleted. It also tries to connect to a Chinese social networking site, “Happy Net” and download yet another file, but at the time of writing, the file wasn’t accessible.
It looks as though Worm.SymbOS.Yxe is now on a par with malware such as Cabir and Comwar. Cabir was the first Bluetooth worm, and the first malware for mobile platforms; Comwar was the first malware to spread via MMS; Yxe was the first in-the-wild malicious program with a valid certificate. A number of variants of Cabir and Comwar spread at intervals in the years following their first appearance. Worm.SymbOX.Yxe is over a year old now and looks as though it’s not planning to stop its evolution or its spread any time soon.





















More on Yxe