
Kaspersky Lab presents its malware rankings for October.
Overall, October was relatively quiet, although there were a few incidents worthy of note. Virus.Win32.Murofet, which infected a large number of PE files, was detected at the beginning of the month. What makes this malware interesting is that it generates links using a special algorithm based on the current date and time on the infected computer. Murofet gets the system’s current year, month, date, and minute, generates two double words, hashes them using md5, adds .biz, .org, .com, .net, or .info, and adds “/forum” to the end of the string. This is then used as a link.
Remarkably, this virus does not infect any other types of executable files. It is closely linked to Zeus: the links Murofet generate are part of the Zeus infrastructure, and bot downloaders are placed on these links. This piece of malware demonstrates just how inventive and eager the Zeus developers are to spread their creation around the world.
Fake archiving programs are becoming increasingly common. They are detected by Kaspersky Lab products as Hoax.Win32.ArchSMS. Once this program launches, the user is asked to send one or more SMSs to a premium-rate number so they can access the contents of an archive. In most cases after a message is sent, the user receives instructions on how to use a torrent tracker and/or a link to it. There are a variety of hoax scenarios, but the result is always the same – the victim ends up spending money and does not get the file s/he wants. This type of fraud is relatively new and only came to light a few months ago. It has attracted a lot of interest from cybercriminals, as data from the Kaspersky Security Network (KSN) shows:
 Another noteworthy incident in October was that Microsoft broke its own record for the number of security patches released in a single month. On 12 October, for example, 16 security bulletins were released to cover 49 different vulnerabilities. The previous record was set in August this year, when a total of 34 vulnerabilities were patched. This is a clear sign that cybercriminals are actively exploiting defects in the software giant’s products. For example, when the notorious Stuxnet worm appeared it made use of four unpatched zero-day vulnerabilities. October’s security bulletin took care of a third vulnerability exploited by Stuxnet; one vulnerability still remains unpatched.
Another noteworthy incident in October was that Microsoft broke its own record for the number of security patches released in a single month. On 12 October, for example, 16 security bulletins were released to cover 49 different vulnerabilities. The previous record was set in August this year, when a total of 34 vulnerabilities were patched. This is a clear sign that cybercriminals are actively exploiting defects in the software giant’s products. For example, when the notorious Stuxnet worm appeared it made use of four unpatched zero-day vulnerabilities. October’s security bulletin took care of a third vulnerability exploited by Stuxnet; one vulnerability still remains unpatched.
Malicious programs detected on users’ computers
The following table shows malicious and potentially unwanted programs that were detected and neutralized on users’ computers.
| Position | Change in position | Name | Number of infected computers |
| 1 |  0 0 |
Net-Worm.Win32.Kido.ir | 386141 |
| 2 |  0 0 |
Virus.Win32.Sality.aa | 150244 |
| 3 |  0 0 |
Net-Worm.Win32.Kido.ih | 141210 |
| 4 |  0 0 |
Trojan.JS.Agent.bhr | 104094 |
| 5 |  0 0 |
Exploit.JS.Agent.bab | 85185 |
| 6 |  1 1 |
Virus.Win32.Virut.ce | 81696 |
| 7 |  8 8 |
Packed.Win32.Katusha.o | 74879 |
| 8 |  -2 -2 |
Worm.Win32.FlyStudio.cu | 73854 |
| 9 |  2 2 |
Virus.Win32.Sality.bh | 57624 |
| 10 |  -1 -1 |
Exploit.Win32.CVE-2010-2568.d | 54404 |
| 11 |  1 1 |
Exploit.Win32.CVE-2010-2568.b | 51485 |
| 12 |  -2 -2 |
Trojan-Downloader.Win32.VB.eql | 49570 |
| 13 |  0 0 |
Worm.Win32.Autoit.xl | 43618 |
| 14 |  0 0 |
Worm.Win32.Mabezat.b | 43338 |
| 15 |  5 5 |
Trojan-Downloader.Win32.Geral.cnh | 39759 |
| 16 |  1 1 |
Worm.Win32.VBNA.b | 33376 |
| 17 |  -1 -1 |
Trojan-Dropper.Win32.Sality.cx | 30707 |
| 18 |  New New |
Trojan.Win32.Autoit.ci | 29835 |
| 19 |  New New |
Trojan-Dropper.Win32.Flystud.yo | 29176 |
| 20 |  New New |
Worm.Win32.VBNA.a | 26385 |
There have been no dramatic changes in the rankings since last month. Kido, Sality, Virut, and CVE-2010-2568 still lead the pack. The only other thing worth mentioning is the increase in the number of Packed.Win32.Katusha.o detections (in 6th place). It is used by cybercriminals to protect and spread fake antivirus programs. Worm.Win32.VBNA.a (in 20th place) is similar to Packed.Win32.Katusha.o except it is written in Visual Basic, a high-level programming language. Both packers have been described in detail in earlier editions of our monthly rankings.
Malicious programs on the Internet
The second Top Twenty list below shows data generated by the web antivirus component and reflects the online threat landscape. This table includes malware and potentially unwanted programs which are detected on web pages or downloaded to victim machines from web pages.
| Position | Change in position | Name | Number of attempted downloads |
| 1 |  New New |
Trojan.JS.FakeUpdate.bp | 114639 |
| 2 |  -1 -1 |
Exploit.JS.Agent.bab | 96296 |
| 3 |  8 8 |
Exploit.Java.CVE-2010-0886.a | 89012 |
| 4 |  New New |
Hoax.Win32.ArchSMS.jxi | 78235 |
| 5 |  1 1 |
Trojan.JS.Agent.bhr | 63204 |
| 6 |  -2 -2 |
AdWare.Win32.FunWeb.di | 62494 |
| 7 |  New New |
Trojan.JS.Redirector.nj | 61311 |
| 8 |  -3 -3 |
AdWare.Win32.FunWeb.ds | 52404 |
| 9 |  New New |
Trojan.JS.Agent.bmx | 35889 |
| 10 |  3 3 |
AdWare.Win32.FunWeb.q | 34850 |
| 11 |  -1 -1 |
AdWare.Win32.FunWeb.fb | 34796 |
| 12 |  New New |
Trojan-Downloader.Java.Agent.hx | 34681 |
| 13 |  New New |
Exploit.JS.CVE-2010-0806.i | 33067 |
| 14 |  1 1 |
Exploit.JS.CVE-2010-0806.b | 31153 |
| 15 |  New New |
Trojan-Downloader.Java.Agent.hw | 30145 |
| 16 |  New New |
Trojan.JS.Redirector.lc | 29930 |
| 17 |  New New |
Exploit.Win32.CVE-2010-2883.a | 28920 |
| 18 |  -6 -6 |
Trojan-Downloader.Java.Agent.gr | 27882 |
| 19 |  -3 -3 |
AdWare.Win32.FunWeb.ci | 26833 |
| 20 |  New New |
AdWare.Win32.FunWeb.ge | 25652 |
There have been no substantial changes to the rankings this month – exploits for CVE-2010-0806 and the FunWeb adware family continue to dominate. However, a few unusual pieces of malware have emerged that are worth taking a closer look at.
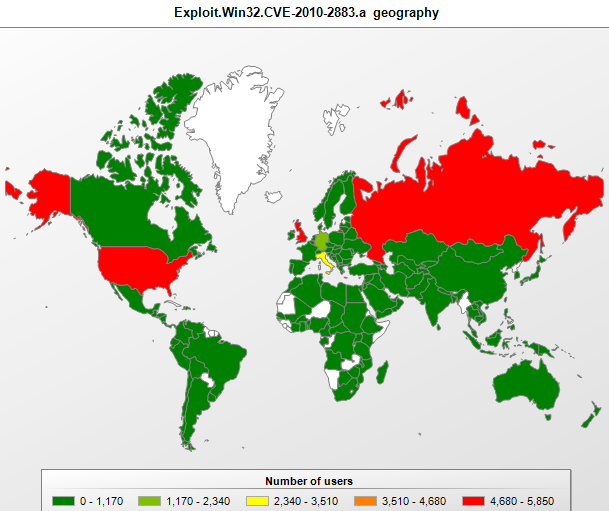
Exploit.Win32.CVE-2010-2883.a (seventeenth place), which exploits the vulnerability of the same name, was first identified a little over a month ago. Cybercriminals obviously wasted no time in exploiting this vulnerability. The vulnerability relates to an Adobe Reader DLL called cooltype.dll, which will incorrectly process a specially crafted font file. A look at the geographic distribution of Exploit.Win32.CVE-2010-2883.a shows that it was detected most often in the USA, the UK and Russia. It appears that cybercriminals assumed these countries would host the largest number of computers with unpatched Adobe Reader software.
The malicious script Trojan.JS.Redirector.nj (seventh place) is found on certain porn sites and displays a message asking the user to send an SMS to a premium-rate number in order to use the site. The script is crafted in such a way that Task Manager or a program with similar functionality has to be used in order to close the page.

The message displayed by Trojan.JS.Redirector.nj prompts
the user to send an SMS to access the required site
Trojan.JS.Agent.bmx (in 9th place) is a classic browser exploit; it downloads a Trojan- Downloader which in turn gets a list of as many as 30 links leading to various malicious programs, including Trojan-GameThief.Win32.Element, Trojan-PSW.Win32.QQShou, Backdoor.Win32.Yoddos, Backdoor.Win32.Trup, Trojan-GameThief.Win32.WOW and others.
FakeUpdate – Trojan.JS.FakeUpdate.bp, a script from the FakeUpdate family, is at the top of the ranking. It is also found on porn sites and offers the user the opportunity to download a video clip. However, when an attempt is made to play the clip, a popup window appears saying a new media player has to be installed in order to watch the clip.

The popup displayed by Trojan.JS.FakeUpdate.bp prompts the user
to install a media player so they can watch video clips on a porn site
Analysis has shown that the installer contains a Trojan along with the legitimate Fusion Media Player application. The Trojan modifies the “hosts” files, associating a number of popular sites with 127.0.0.1, the local IP address, and then installs a local web server on the infected computer. After this, every time the user tries to access one of the sites, a page appears in the browser demanding that the user pay for viewing adult content.

The page displayed instead of the site bash.org.ru reads: “You have been watching gay porn”.
The user is asked to send an SMS to pay for the service and to receive a code that will remove the message
The other newcomers may not be quite as interesting, but they are still worth mentioning. Two new Java downloaders – Trojan-Downloader.Java.Agent.hx (12th place) and Trojan-Downloader.Java.Agent.hw (15th place) use openStream (class URL) methods to download other malicious programs. Hoax.Win32.ArchSMS.jxi (3rd place) belongs to the same family mentioned above. Even though there were no major incidents to talk of this month, there was still plenty of new and interesting malicious programs out there.



















Monthly Malware Statistics, October 2010