
Online threats: Steering clear of drive-by downloads
By far the biggest threat to users this month was drive-by downloads. This type of attack can result in users’ computers being infected even when visiting legitimate sites.
Here’s a quick reminder of how drive-by downloads infect computers. First of all, a user visits a legitimate site that has been infected or a site belonging to cybercriminals where a redirect script is located. A good example of just such a script is Downloader.JS.Pegel, one of the most prevalent redirects of recent times. The redirect leads to a script downloader which in turn is used to launch exploits. As a rule, exploits are downloaded to users’ computers and launch malicious executable files that are primarily backdoors to vulnerable programs.
The Top 20 malicious programs detected on the Internet in November included a total of nine exploits, three redirects and one script downloader that were used for carrying out drive-by downloads.
Redirects and script downloaders
The drive-by download process begins with redirects, several of which feature among the leading malicious programs detected on the Internet. November found Trojan.HTML.IFrame.dl in 5th place, Trojan.JS.IFrame.pg at 10th place and Trojan.JS.Redirector.lc appearing in 20th position. They were closely followed by Trojan.JS.Redirector.np at 25th in the table and Trojan-Downloader.JS.Iframe.bzn at 29th.
Second place in our online malware rating went to Trojan-Downloader.JS.Agent.frs. If a user is unlucky enough to end up on an infected site that redirects them to this script downloader, exploits targeting vulnerabilities in Java, PDF, and JavaScript will attempt to download and run such malicious backdoors as Backdoor.Win32.Shiz and Backdoor.Win32.Blakken (Black Energy 2).
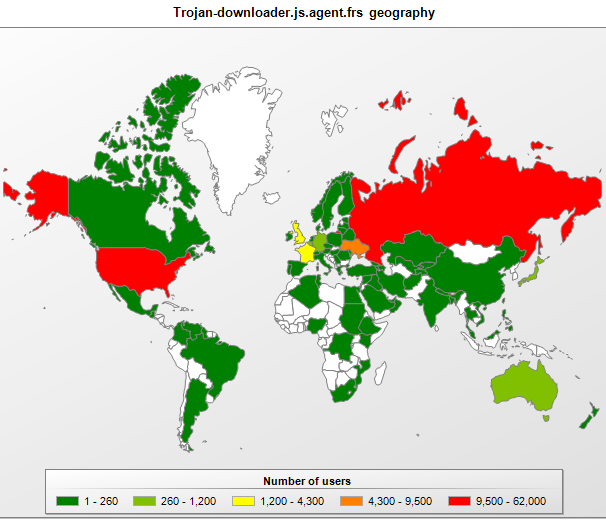
The geographical spread of Trojan-Downloader.JS.Agent.frs detections
Users in the USA, Russia, France and the UK were most at risk of infection by Trojan-Downloader.JS.Agent.frs.
Java-based downloaders and exploits
Malware written in the lingua franca of the digital world, JavaScript, is becoming increasingly common, a trend that was virtually non-existent only twelve months ago.
The last two months has seen an explosion in the number of malicious programs that go to make up the Trojan-Downloader.Java.OpenConnection family. These programs act in just the same way as exploits do in a drive-by attack, but instead of using vulnerabilities to download malware to victims’ computers, they employ the OpenConnection method of a URL class.
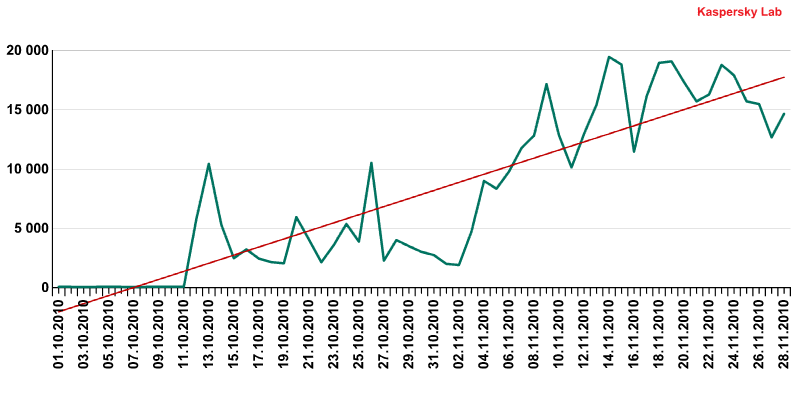
The number of cases of Trojan-Downloader.Java.OpenConnection
detected for the period October-November 2010
In November, Trojan-Downloader.Java.OpenConnection.bu topped the ranking of malicious programs detected on the Internet, with two more programs that also use the OpenConnection method appearing in 21st and 26th places respectively.
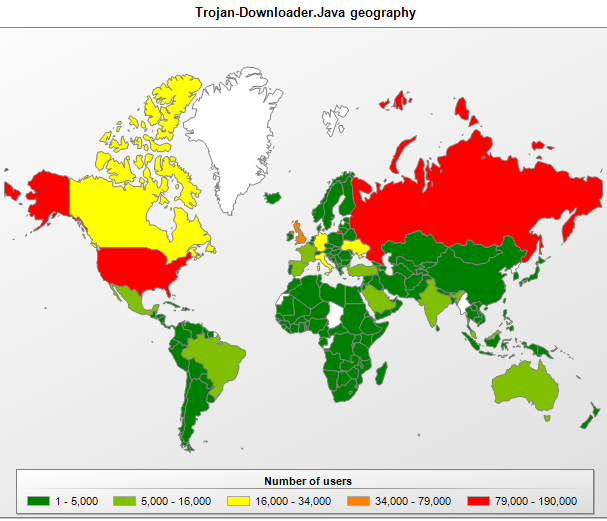
The geographical spread of detected members of the Trojan-Downloader.Java family
The distribution of downloaders written in Java mirrored that of Trojan-Downloader.JS.Agent.frs, suggesting that Java downloaders and script downloaders are being used together by cybercriminals to carry out drive-by download attacks.
In addition to Java downloaders, Java-based exploits are appearing in increasing numbers as well, a good example being exploits for the relatively old CVE-2009-3867 vulnerability in the getSoundBank function. Not to be left out, the abovementioned Trojan-Downloader.JS.Agent.frs also makes use of Java exploits too.
What makes Java so appealing to the cybercriminals is that it is a multiplatform programming language, meaning that malware written in Java can be used on all operating systems where Java virtual machines are installed.
PDF exploits
November saw the detection of a number of exploits, mostly written in JavaScript, targeting vulnerabilities and features in PDF documents. Among them were two unique downloaders, Exploit.JS.Pdfka.cyk in 24th position and Exploit.JS.Pdfka.cyy in 28th place. The overall trend, however, shows the number of PDF exploits is in decline, with a threefold decrease in the average number of Pdfka malware variants detected over the last six months alone.
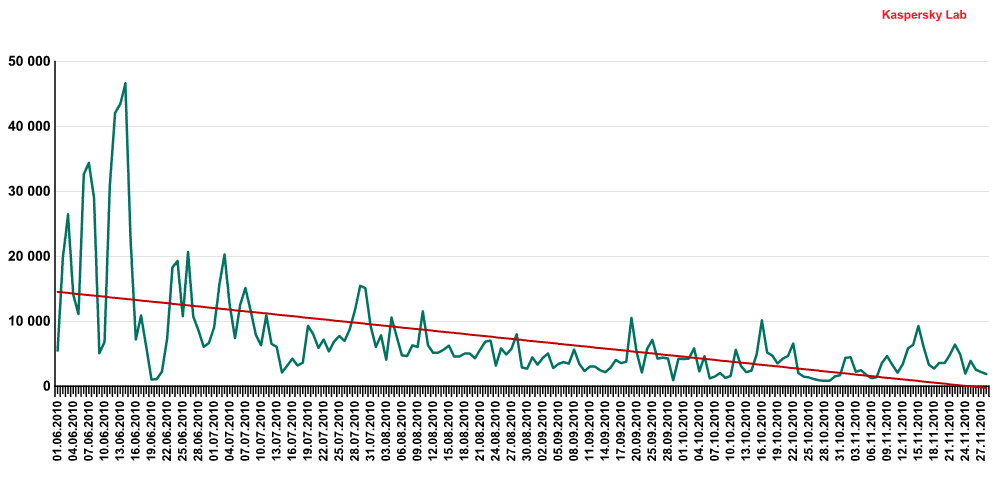
The number of Exploit.JS.Pdfka variants detected for the period June-November
This is most probably linked to Adobe’s efforts to patch holes in its products. In November, the company released Adobe Reader X with a built-in sandbox feature that should allow exploits to be counteracted more effectively.
TOP 20 Malicious Programs on the Internet
| Position | Change in position | Name | Number of user |
| 1 |  New New |
Trojan-Downloader.Java.OpenConnection.bu | 167617 |
| 2 |  New New |
Trojan-Downloader.JS.Agent.frs | 73210 |
| 3 |  1 1 |
Exploit.Java.CVE-2010-0886.a | 68534 |
| 4 |  New New |
Trojan.HTML.Iframe.dl | 56075 |
| 5 |  1 1 |
Trojan.JS.Agent.bhr | 46344 |
| 6 |  -3 -3 |
Exploit.JS.Agent.bab | 42489 |
| 7 |  6 6 |
Trojan.JS.Agent.bmx | 40181 |
| 8 |  New New |
Trojan.HTML.Agent.di | 35464 |
| 9 |  29 29 |
Trojan.JS.Iframe.pg | 28385 |
| 10 |  74 74 |
Trojan.JS.Redirector.nz | 26203 |
| 11 |  9 9 |
Trojan.JS.Popupper.aw | 25770 |
| 12 |  New New |
Trojan-Downloader.Java.Agent.il | 23048 |
| 13 |  -2 -2 |
AdWare.Win32.FunWeb.q | 22922 |
| 14 |  11 11 |
Trojan-Downloader.Win32.Zlob.aces | 22443 |
| 15 |  3 3 |
AdWare.Win32.FunWeb.ci | 19557 |
| 16 |  -1 -1 |
Exploit.JS.CVE-2010-0806.b | 19487 |
| 17 |  -3 -3 |
Exploit.JS.CVE-2010-0806.i | 18213 |
| 18 |  9 9 |
Exploit.SWF.Agent.du | 17649 |
| 19 |  -3 -3 |
Trojan.JS.Redirector.lc | 16645 |
| 20 |  -10 -10 |
Trojan-Downloader.Java.Agent.hx | 16242 |
Fake archives
We’ve already written about them, but there appears to be no let up in the popularity of fake archives. The method behind this scam is highly effective – when users look for something via a search engine, a page is automatically generated with a banner offering the desired information.
The user is then asked to send one or more SMSs to a premium-rate number so they can access the contents of an archive. The end result being that instead of receiving the information they wanted, users normally find that the archive is either empty, “corrupt” or contains a torrent file, etc.
The screenshot below shows an example of a fraudulent offer to download archived information:
This Russian language screenshot purports to offer users a list of high-speed
download options for a manual by a Russian design engineer
Fake archives are detected by Kaspersky Lab products as variants of the Hoax.Win32.ArchSMS family. ArchSMS is primarily blocked on computers in the CIS.
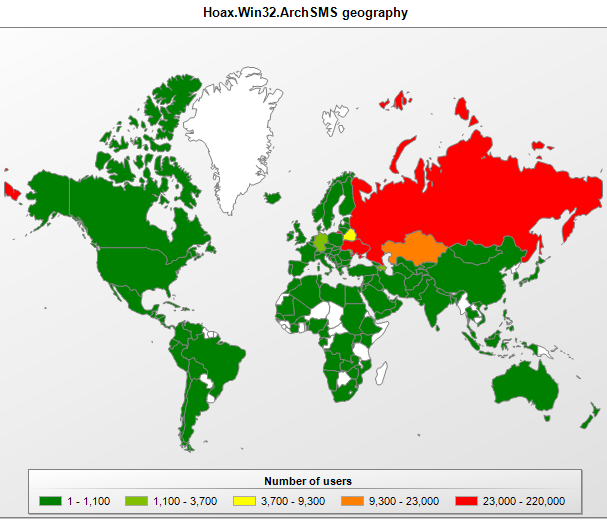
The geographical spread of Hoax.Win32.ArchSMS detections
Malware detected on users’ computers
For the cybercriminals, threats that spread via local networks and removable media are far too good to be ignored.
That is why it should be no surprise that Virus.Win32.Sality.aa made it to 3rd place in this month’s table, with Virus.Win32.Virut.ce in 6th place and Virus.Win32.Sality.bh in 8th position – these three being among some of the most common threats detected on users’ computers during November. What makes these threats all the more dangerous is the fact that they can also infect executable files.
Malware targeting vulnerabilities that have already been patched also pop up in this month’s Top 20 rating, with Kido, or Conficker as it is otherwise known, occupying the two top slots. However, exploits that target the CVE-2010-2568 vulnerability in shortcuts are still doing the rounds too, coming in at 13th and 14th places respectively. These two are renowned for spreading Stuxnet and other potent malware, which once again highlights how important it is for users to ensure that they install any patches and updates for their operating systems and software as soon as they become available.




















Monthly Malware Statistics, November 2010