
March in figures
The following statistics were compiled in March using data from computers running Kaspersky Lab products:
- 241,151,171 network attacks blocked;
- 85,853,567 attempted web-borne infections prevented;
- 219,843,736 malicious programs detected and neutralized on users’ computers;
- 96,702,092 heuristic verdicts registered.
One man’s misfortune is another man’s gain
We have already written on a number of occasions that criminals are not averse to exploiting tragedies, and the Japanese earthquake and tsunami, plus the death of Elizabeth Taylor, did nothing to buck this trend.
Thousands of people in Japan have lost loved ones and have been left homeless, while the world looks on in trepidation as events unfold at the Fukushima nuclear plant. But that hasn’t stopped scammers and malware writers from spreading malicious links to their own versions of the “latest news”, creating malicious websites with content connected in some way to the disaster in Japan and sending out ‘Nigerian’ letters making emotional requests for money to be transferred to the message sender in order to help those who have suffered.
One spam message contained a link that claimed to lead to the latest news from Japan. Clicking on the link triggered a drive-by download attack that made use of exploit packs. If the attack was successful, Trojan-Downloader.Win32.CodecPack was downloaded to the user’s computer. Each variant of this family is inextricably linked to three command centers with which it communicates and receives lists of malicious files that are downloaded and run on infected computers. On one website that we detected, visitors were asked to download a video clip showing events from Japan. However, instead of a video, users ended up downloading a backdoor.
It seems the most switched-on cybercriminals use Twitter – malicious links exploiting Elizabeth Taylor’s death appeared on the social network within a day of the news being announced.
Exploits
Exploits remain one of the favorite tools in the cybercriminals’ arsenals, so the appeals from IT security companies to regularly update computer software are as relevant as ever.
Java exploits
The number of Java exploits is considerable – they make up approximately 14% of all known exploits. Three of them made it into this month’s Top 20 malicious programs detected on the Internet. Two of them – Exploit.Java.CVE-2010-0840.d in 15th place and Exploit.Java.CVE-2010-0840.c in 19th – are new exploits for the CVE-2010-0840 vulnerability in Java. Active use of this loophole was recorded for the first time in February.
According to Kaspersky Security Network (KSN) statistics, malware writers are actively modifying the exploits they use in drive-by attacks in order to avoid detection. This is demonstrated in the graph below which shows detections for the Exploit.Java.CVE-2010-0840 family.
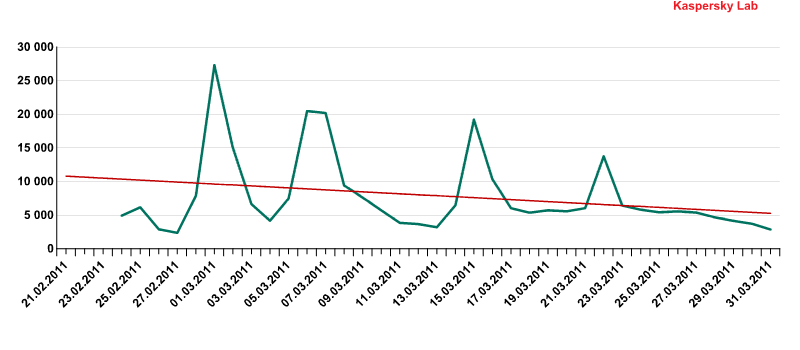
Detection of the Exploit.Java.CVE-2010-0840 family
The peaks in the graph correspond to periods when exploits of this family were detected in drive-by attacks, while the troughs show when newer variants of the exploit replaced older versions.
Exploits and vulnerabilities in Adobe Flash Player
Malware writers are surprisingly quick to react to announcements of new vulnerabilities. A good example of this is a vulnerability in Adobe Flash Player that was announced on 14 March. The vulnerability in question was in authplay.dll and because it offered cybercriminals an opportunity to gain control of a user’s computer it was rated as critical.
On 15 March, Kaspersky Lab had already detected an exploit for the vulnerability – an Excel file that contained a malicious SWF file and which is detected as Trojan-Dropper.SWF.CVE-2011-0609.a.
On 25 March, we detected one more variant of the exploit – an HTML page that contained shellcode in JavaScript and which loaded a malicious Flash file. The malicious SWF file exploited a security breach which allowed the shellcode to gain control. The malicious HTML and SWF files are detected as Exploit.JS.CVE-2011-0609 and Exploit.SWF.CVE-2011-0609 respectively.
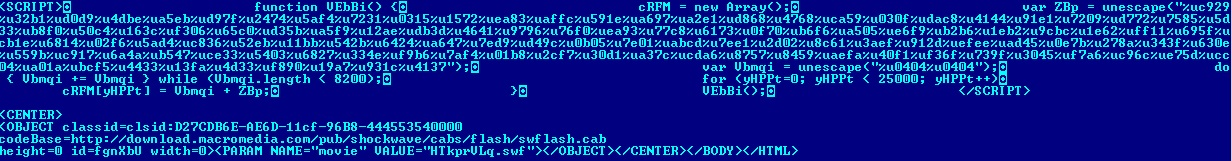
A fragment of the Exploit.JS.CVE-2011-0609.d code
This story has a happy ending though – the vulnerability was quickly fixed. Adobe announced the problem had been resolved on 22 March. Of course, the happy ending will only apply to those users who updated the software on their computers in time.
Malicious HTML pages: avoiding detection
We make regular announcements about the detection of HTML pages that cybercriminals use as part of their scams or to spread malware. The malevolent people behind such pages are constantly coming up with new ways to hide their creations from antivirus programs.
Use of


















