
February in figures
The following statistics were compiled in February using data from computers running Kaspersky Lab products:
- 228,649,852 network attacks blocked;
- 70,465,949 attempted web-borne infections prevented;
- 252,187,961 malicious programs detected and neutralized on users’ computers;
- 75,748,743 heuristic verdicts registered.
Cybercriminals perfecting drive-by attacks
February saw considerable growth in the use of Cascading Style Sheets (CSS) that contain partial data for script downloaders, a new method for spreading malware that makes it much harder for many antivirus solutions to detect malicious scripts. This method is currently being used in the majority of drive-by download attacks and allows cybercriminals to download exploits to users’ machines without those exploits being detected.
Drive-by attacks using this method involve redirecting users from an infected site to a page containing CSS data and a malicious script downloader, usually with the help of iFrame. Three infected pages of this type were among the Top 20 most malicious programs detected on the Internet in February: Trojan-Downloader.HTML.Agent.sl took 1st place, while Exploit.JS.StyleSheeter.b came in at 13th place and Trojan.JS.Agent.bte at 19th place.
The script downloaders on these malicious web pages download two types of exploits. One of them, which targets the CVE-2010-1885 vulnerability and that we detect as Exploit.HTML.CVE-2010-1885.ad, took 4th place in the ranking. On average, this exploit was recorded on the computers of 10 thousand unique users every day.
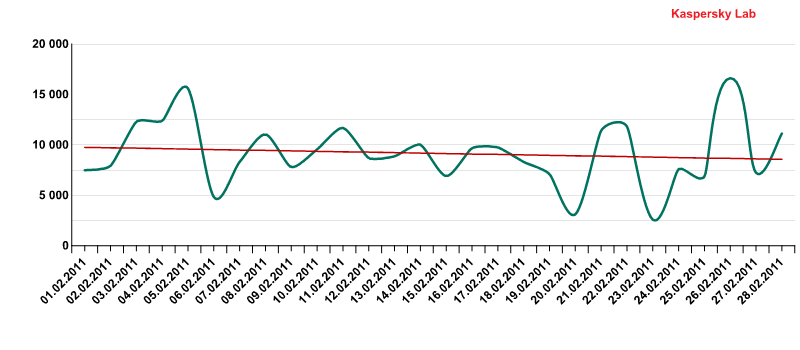
The number of unique cases of Exploit.HTML.CVE-2010-1885.ad detected in February 2011
The other type of exploit uses vulnerability CVE-2010-0840 and three such examples made the Top 20. They are detected by us as Trojan-Downloader.Java.OpenConnection.dd in 3rd place, Trojan.Java.Agent.ak in 7th place, and finally, Trojan-Downloader.Java.OpenConnection.dc in 9th place.
Use of the first of these two vulnerabilities by cybercriminals is nothing new, but the active use of CVE-2010-0840 was recorded for the first time in February.
Statistics from our products’ heuristic modules confirm that the use of CSS for protecting exploits, and ultimately spreading malware, is currently the most prevalent method being used by cybercriminals in drive-by attacks. The majority of the domains where the redirects take place are already detected as Blocked in our web antivirus database.
Vulnerabilities in PDF still posing a threat
Statistical data generated by the heuristic modules in our products shows that the number of unique computers on which PDF exploits were detected exceeded 58 thousand. Exploitation of vulnerabilities in PDF files is currently one of the most popular methods of delivering malware to users’ computers. One PDF exploit – Exploit.JS.Pdfka.ddt – entered the Top 20 malicious programs on the Internet in 8th place.
Packaged Palevo
The malicious packer that is used to help protect the Palevo P2P worm was detected on more than 67 thousand unique computers. The Palevo worm was responsible for the creation of the Mariposa botnet that was shut down by Spanish police a while ago. It seems likely that the recent spread of this packed worm is linked to an attempt by cybercriminals to create a new botnet or restore the old one.
One interesting aspect of this packer is that it adds lots of random lines to the file that is being packed.

Fragment of the packed Palevo worm
Mobile threats
Android
February saw the discovery of a number of new malicious programs for the Android platform. One of them – Trojan-Spy.AndroidOS.Adrd.a – has backdoor functionality. It connects to a remote server and sends the infected mobile phone’s IMEI and IMSI identification data. In response, the command center sends information that is used by the malware to run queries on the search system in background mode. The queries are used to increase the hit rating of specific sites. It’s worth noting that this malicious program has only been detected in Chinese repositories.
A second piece of malware for Android called Trojan-Spy.AndroidOS.Geinimi.a is an “enhanced” version of the Adrd family and was detected not only in China but also the USA, Spain, Brazil and Russia.
Trojan-SMS on J2ME
Malicious programs for the J2ME platform are also proving to be popular. For example, Trojan-SMS.J2ME.Agent.cd entered the Top 20 most widespread malicious programs on the Internet at 18th place. Its main function is to send SMSs to premium-rate numbers. It spreads primarily via links in spam messages sent over the ICQ instant messenger service and is most prevalent in Russia and Spain.
TOP 20 malicious programs on the Internet
| Current rank | Delta | Verdict |
| 1 |  New New |
Trojan-Downloader.HTML.Agent.sl |
| 2 |  18 18 |
Trojan-Downloader.Java.OpenConnection.cx |
| 3 |  New New |
Trojan-Downloader.Java.OpenConnection.dd |
| 4 |  New New |
Exploit.HTML.CVE-2010-1885.ad |
| 5 |  -1 -1 |
AdWare.Win32.FunWeb.gq |
| 6 |  -5 -5 |
AdWare.Win32.HotBar.dh |
| 7 |  New New |
Trojan.Java.Agent.ak |
| 8 |  New New |
Exploit.JS.Pdfka.ddt |
| 9 |  New New |
Trojan-Downloader.Java.OpenConnection.dc |
| 10 |  New New |
Trojan.JS.Iframe.rg |
| 11 |  -2 -2 |
Trojan-Downloader.Java.OpenConnection.cg |
| 12 |  -7 -7 |
Trojan.HTML.Iframe.dl |
| 13 |  New New |
Exploit.JS.StyleSheeter.b |
| 14 |  -1 -1 |
Trojan.JS.Fraud.ba |
| 15 |  -8 -8 |
Trojan-Clicker.JS.Agent.op |
| 16 |  -8 -8 |
Trojan.JS.Popupper.aw |
| 17 |  -7 -7 |
Trojan.JS.Agent.bhr |
| 18 |  New New |
Trojan-SMS.J2ME.Agent.cd |
| 19 |  -New -New |
Trojan.JS.Agent.bte |
| 20 |  -6 -6 |
Exploit.JS.Agent.bab |
TOP 20 malicious programs detected on users’ computers
| Current rank | Delta | Verdict |
| 1 |  0 0 |
Net-Worm.Win32.Kido.ir |
| 2 |  0 0 |
Virus.Win32.Sality.aa |
| 3 |  6 6 |
HackTool.Win32.Kiser.zv |
| 4 |  -1 -1 |
Net-Worm.Win32.Kido.ih |
| 5 |  2 2 |
Virus.Win32.Sality.bh |
| 6 |  -2 -2 |
Hoax.Win32.Screensaver.b |
| 7 |  -2 -2 |
AdWare.Win32.HotBar.dh |
| 8 |  0 0 |
Virus.Win32.Virut.ce |
| 9 |  -3 -3 |
Trojan.JS.Agent.bhr |
| 10 |  1 1 |
HackTool.Win32.Kiser.il |
| 11 |  -1 -1 |
Packed.Win32.Katusha.o |
| 12 |  0 0 |
Worm.Win32.FlyStudio.cu |
| 13 |  2 2 |
Trojan-Downloader.Win32.VB.eql |
| 14 |  2 2 |
Worm.Win32.Mabezat.b |
| 15 |  3 3 |
Packed.Win32.Klone.bq |
| 16 |  -2 -2 |
Trojan-Downloader.Win32.Geral.cnh |
| 17 |  New New |
Trojan.Win32.Starter.yy |
| 18 |  New New |
AdWare.Win32.FunWeb.gq |
| 19 |  Returned Returned |
Worm.Win32.Autoit.xl |
| 20 |  New New |
Trojan-Downloader.HTML.Agent.sl |

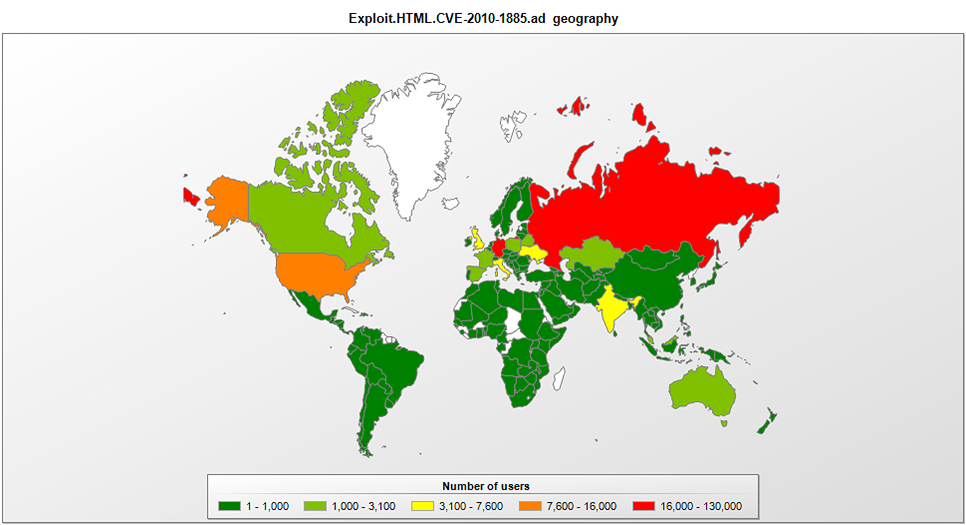


















Monthly Malware Statistics, February 2011