
Not so long ago we wrote (https://securelist.com/gold-rush/30848/) about cybercriminals using infected computers to generate virtual money via Bitcoin. A couple of days ago we discovered a malicious program called Trojan-Downloader.Win32.MQL5Miner.a which also uses the resources of infected computers, but this time to make money in MQL5 Cloud Network, a distributed computing network.
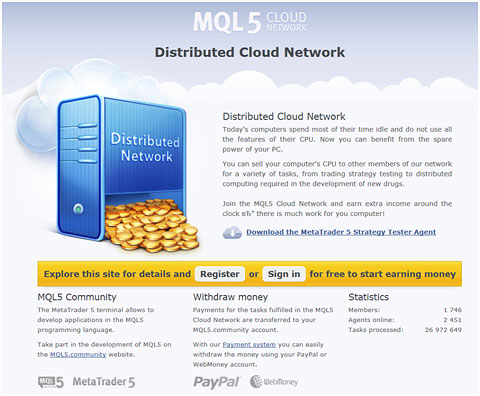
The MQL5 Cloud Network site
MetaQuotes is a developer of software for financial markets. Several weeks ago, information appeared on the net that the company was offering to pay users to participate in distributed computing. Apparently, this is what attracted malicious users to the new cloud service.
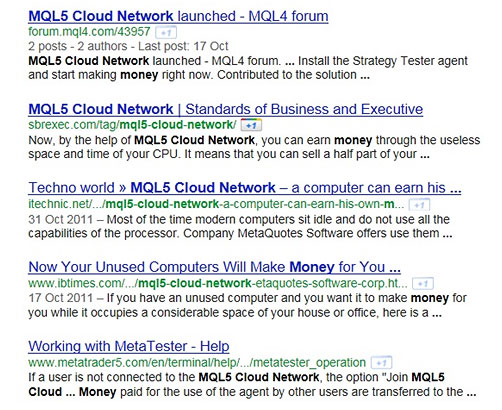
Google search results for the phrase: “MQL5 Cloud Network money”
There are grounds to believe that the malicious program spreads via email. Having infected a computer, the malicious program first determines if the operating system is 32-bit or 64-bit. It then downloads the appropriate version of the official software from MetaQuotes SoftWare. MQL5Miner then launches the service to participate in the cloud computing network. But the cybercriminals specify their own account data and receive the payments for any distributed computing operations that are performed on an infected machine.
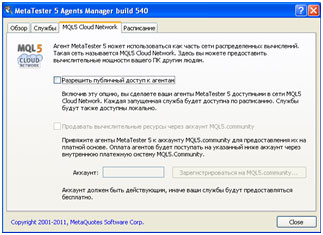
A window from the legitimate MetaQuotes software
When it comes to making money, cybercriminals don’t miss a trick. That includes exploiting the resources of infected computers without their owners’ knowledge or consent.
We have notified MetaQuotes about the account being used by cybercriminals.






















Money from the cloud