
Over the last week there has been an enormous upsurge in reports of so called “MonaRonaDona” malware.
When MonaRonaDona is installed on the system it shows the user an alert:
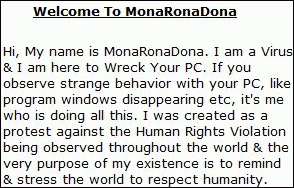
When active, it terminates applications which have the names listed below in the Windows title bar:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
Date And Time Windows Task Manager Registry Editor Irfanview Google Talk Macromedia Adobe Microsoft Visual Windows Media Player Winamp Microsoft Office Microsoft Excel Microsoft Word Messenger |
The IE title bar will also contain a reference to MonaRonaDona.How the malware actually reaches the system isn’t entirely clear at the moment. When first run, the only thing the program does is register itself to start at Windows boot. As symptoms of infection aren’t immediately visible, this makes it harder for victims to pinpoint what they were doing when they actually got infected. These characteristics make it look as though this malware was created by a cyber hooligan, someone simply interested in causing damage to victim machines. However, a bit more digging revealed a completely different story.
Even though it may not be immediately clear that the machine has been infected, in contrast to the majority of today’s malware MonaRonaDona is very visible. It’s an approach clearly designed to cause the user to search for information on MonaRonaDona using their favourite search engine.
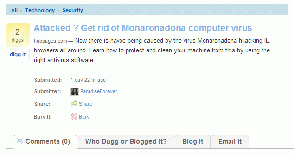
Once the victim searches using this name, s/he will end up at sites displaying the following:
Or at Digg:
which leads to:
Incidentally, at the time I received the malware, no antivirus product was detecting it. However, the names of the antivirus products listed on the screenshot above will probably be familiar to most users – apart from the unknown Unigray antivirus.
A bit of research uncovered the following facts: firstly, unigray.com has only been in existence for two weeks now, which is a bit of a red flag.
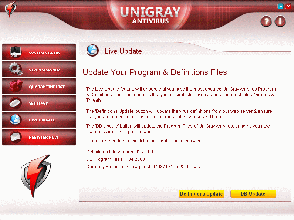
Secondly, that’s a pretty large anti-malware database for a product that has only been around for a very short period of time.
Interestingly, the ‘number of records’ value is hardcoded in the product, but when updating, the program will always report (falsely) that the latest updates have been installed. Another red flag.
Digging a bit deeper, I found that the product only has ‘detection’ for the following malicious programs:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
Win32.CIH BlazeFind e2give Hancer Cydoor PowerStrip EliteBar DyFuCa 2020Search Aurora Spy Trooper SpySheriff CoolWebSearch W32.Gampxia!html W32.Gampxia W32.Imaut.CN W32.Selex.B@mm Win32.ch MonaRonaDona |
The program generated almost 200 false alarms on a completely clean system, choosing names seemingly at random from the list of malicious programs shown above. Interestingly, on a machine infected with MonaRonaDona, the ‘antivirus’ also generated false alarms on clean files, detecting them as MonaRonaDona.
It seems very strange that such a new program would include detection for MonaRonaDona while legitimate antivirus products don’t.
Analysing the program further I found that it has only one removal routine. Guess for which malicious program? That’s right – MonaRonaDona. Unigray will clean it up for only $39.90 – this doesn’t sound like the best of deals to me.
A comparison of the code of MonaRonaDona and Unigray Antivirus show that there are many, many similarities. This leaves very little doubt that the same group is behind both MonaRonaDona and Unigray. And this case clearly shows that the bad guys are getting very good at social engineering. They obviously put a lot of thought into manipulating the user into doing what they want.
We detect MonaRonaDona as Trojan.Win32.Monagrey.a and Unigray Antivirus as not-a-virus:FraudTool.Win32.Unigray.a.






















MonaRonaDona malware