
Introduction
The fifth part of our regular overview of mobile malware evolution was published one year ago, and now it’s time to review the events of 2012 to see just how accurate our forecasts were. This report will provide qualitative and quantitative data on malware evolution and analyze the main trends, both for malicious programs and malware attacks. This report will also set out Kaspersky Lab’s forecasts on the continued development of mobile malware in 2013.
What were our predictions for 2012? In brief, we expected to see more growth in the number of malicious programs targeting Android, as cybercriminals were focusing more on that particular platform. This prediction turned out to be true — malicious users did in fact concentrate their efforts on developing and proliferating malicious programs specifically for the Android operating system.
Kaspersky Lab predicted that cybercriminals would extend their arsenal beyond Android rootkits in their efforts to infect devices and gain full access to the operating system; we also projected the first drive-by attacks exploiting vulnerabilities in the Android OS. This prediction did not come to pass, probably because at this stage in the development of malware targeting Android, cybercriminals simply do not need to launch that type of attack. Users remain as likely as ever to unwittingly infect their own mobile devices.
Another unfulfilled prediction concerned the appearance of the first mass worms for Android — more specifically, SMS worms.
We also suggested that 2012 would see an increase in the number of malware detections in official app stores. Unfortunately, this prediction did turn out to be true. Furthermore, Google Play saw the emergence of a variety of threats (the number of victims varied from several dozen to tens of thousands), and malicious programs were detected for the first time in the App Store for iOS.
Kaspersky Lab’s prediction that we would see the first mobile botnets for Android was also accurate. Note, however, that the botnets that emerged varied greatly in terms of where in the world devices were infected, as well as the number of infected devices, and the functions of the malware.
The predictions addressed above only affected the most commonly used platform today – Android. As far as other mobile platforms and operating systems are concerned, we expected targeted attacks to be among the key threats targeting Symbian, BlackBerry, and other mobile platforms. Typical attacks of this kind usually involve ZitMo and SpitMo (ZeuS- and SpyEye-in-the-Mobile). This prediction also proved correct. Furthermore, the family of threats designed to steal mTANs (ZitMo and SpitMo) gained a new addition – the prevalent bank Trojan Carberp now has a mobile version with the alias CitMo, or Carberp-in-the-Mobile.
Two other general, but critically important, predictions that will play a key role in determining the future of attacks on mobile platforms also came true. First, we saw the development of a fully-fledged mobile malware development industry. Second, mobile espionage went beyond the realm of law enforcement agencies and firms specializing in detective work.
The main developments in mobile malware in 2012 are the subject of this sixth edition of Kaspersky Lab’s Mobile Malware Evolution report.
Statistics
In this section, we will take a look at the statistics on mobile threat developments. This time, in addition to information about the growth in the number of malicious programs, the frequency with which they emerged, and their distribution by platform and behavior, we have also included data received from KSN’s cloud service, which is now available in our mobile product for Android.
Key statistics of 2012
The most significant stats for 2012 are linked to the explosive growth in the number of new malicious programs for Android. Judge for yourself — in 2011, Kaspersky Lab detected nearly 5,300 new malicious programs for all mobile platforms; for some months in 2012 the number of new detections for Android alone exceeded that number. Meanwhile, the number of unique malicious files has exceeded 6 million!
The total amount of modifications and families of mobile malware in Kaspersky Lab’s collection as of January 1, 2013:
| Platform | Modification | Family |
| Android | 43600 | 255 |
| J2ME | 2257 | 64 |
| Symbian | 445 | 113 |
| Windows Mobile | 85 | 27 |
| Others | 28 | 10 |
| Total | 46415 | 469 |
The growth rate for threats targeting mobile platforms has increased dramatically: 40,059 of the 46,415 modifications and 138 of the 469 mobile malware families were added to our database in 2012!
As far as distribution by platform is concerned, the pie chart below illustrates the situation very clearly:
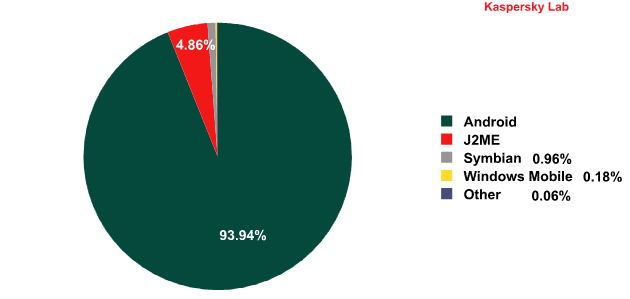
Distribution of mobile threats by platform, 2004 – 2012
In late 2011, roughly 65% of mobile threats targeted the Android platform; by late 2012, that percentage was just short of 94%.
At the same time, 99% of all mobile malware detections in 2012 were threats targeting Android devices. By mid-year, it had become clear that for the next two years at least, mobile malware will predominantly target Android. The fact that the Android OS has become the most common operating system for mobile devices has made it the number one target among virus writers. The old formula still holds true: “the most prevalent OS” + “installation of software from any source” = “the greatest number of threats”.
The most prevalent threats targeting Android
In spring 2012, Kaspersky Lab launched its new KSN cloud service for mobile on the Android OS, which has allowed us to provide additional protection for users of Android devices and collect interesting data on the modifications of malicious programs that users encounter most frequently.
The most frequently detected threats on Android devices can be broken down into three main groups: SMS Trojans, adware, and exploits to gain root access.

The most frequently detected malicious programs targeting Android
The most prevalent Android malware turned out to be SMS Trojans which primarily target users in Russia. This comes as no surprise, as sending costly text messages from infected devices without user consent remains the number one means of generating cash for cybercriminals specializing in mobile platforms.
The second group of threats in the Top 10 is made up of Plangton and Hamob adware. The Plangton family is detected as a Trojan – and for good reason. Plangton is often found in free apps and does in fact display ads. However, it also has another function and changes the browser start page without notifying the user and without user consent, which is considered malicious behavior. As far as AdWare.AndroidOS.Hamob is concerned, it is the type of app that is portrayed as useful, when in fact all it does is display advertising.
The third and final group consists of various modifications of Lotoor — exploits to gain root access on smartphones running on different versions of Android.
User threats
While we saw a substantial rise in the number of incidents involving malware targeting Android in 2012, malicious users didn’t forget altogether about other mobile operating systems. The most notable incidents involving other platforms are addressed below.
Mobile botnets
Technically, the first mobile botnet appeared in the autumn of 2009. The second most widespread program targeting jailbroken iOS devices had just been detected. It was capable of accepting and executing commands from a remote service. At the time, it was a sign that fully-fledged botnets for mobile devices were in the works.
The emergence of mobile botnets in 2012 running on Android devices did not come as a surprise. The first cause for concern came in January with the detection of an IRC bot for Android that worked together with an SMS Trojan. Both threats were named Foncy.

Foncy’s MADDEN NFL 12 icon after installation
In addition to the SMS Trojan and IRC bot, the ARK dropper also contained a root exploit. After launching the exploit on an infected system, it would increase privileges up to root level, and then launch the IRC bot, which would then install and launch the SMS Trojan. The SMS Trojan, once it had performed its function, would stop running, while the IRC bot would continue to run, waiting for commands. As a result, the IRC bot was capable of controlling the smartphone post-infection. In fact, all smartphones infected with the Foncy IRC bot comprised a fully-fledged botnet and could have been used to execute just about any actions at the command of the botnet owner.
French police were able to locate and arrest two suspects allegedly involved in the creation and proliferation of this threat. According to police data, the virus writers infected over 2,000 devices and generated over EUR 100,000 from their scheme. This was the first time anyone has ever been arrested on charges of spreading malware targeting mobile devices.
In February, a mobile botnet was detected with between 10,000 and 30,000 active infected devices at any one time. The total number of infected phones was in the hundreds of thousands. This botnet was created by Chinese virus writers, and was based on the RootSmart backdoor, which features a variety of functions for remotely controlling Android mobile devices. The cybercriminals were counting on a tried and true tactic to spread RootSmart: they bundled it with legitimate programs with packers and uploaded the archive files to unofficial app stores that are widely used in China to download Android apps. As a result, users downloading apps allegedly designed to customize their phones were in fact downloading a backdoor that hooked their device up to a botnet.
The scale of the RootSmart infection allowed malicious users to efficiently monetize their network of infected phones. They employed the most commonly used method among cybercriminals in the mobile field: sending text messages to short numbers. Malicious users found the least costly numbers to prevent their victims from noticing anything. The cybercriminals gained full control over the mobile devices, giving them the ability to hide the malware on the phone over long periods of time and continue to withdraw funds from victim accounts.
In 2012, we discovered backdoors that, fortunately, were not able to infect a large number of devices. Nonetheless, these threats and their specific features are of interest.
One threat targeting Android known as Cawitt is curious in that, first and foremost, it features a mechanism used to obtain the command center domain name through Twitter. The body of the malicious program contains strings from which, bit-by-bit, it generates user pseudonyms on the social network. After generating imaginary user names, the backdoor sends requests to the Twitter server in order to receive their tweets. These tweets contain the command center domain names.

Examples of C&C tweets
In order to start receiving commands from a C&C, Cawitt issues a POST request to the domain name received via Twitter, and then adds “/carbontetraiodide” to the end of it. The bot will receive a command in response to that request.
Another interesting threat detected in late 2012 is SpamSold, a spam bot that targets Android devices. This is the first malicious program for mobile devices designed to send out SMS spam from infected devices.
This backdoor attempts to conceal its presence on a smartphone by deleting its icon and downloading a free version of a game, which it uses as its cover. Then, SpamSold responds to command server GET requests like the one below:

A SpamSold GET request
In response, it receives a text message to send out and the first 100 numbers to which the message will be sent.
After receiving the response, the bot attempts to send the text message included in the command to the specified numbers, and then when it runs out of numbers, SpamSold sends a request to the server for a new set of numbers and a new text message. Meanwhile, the program hides the text messages that it sends, thus concealing its presence and operations.
Fortunately, malicious users have not yet managed to build a large-scale botnet. But the very fact that mobile malware is now being used for sending out text messages suggests we will see more than one malicious program with similar functions in 2013.
On the hunt for mTans
Several new threats were used in targeted attacks in 2012, such as attacks launched using ZitMo and SpitMo (ZeuS- and SpyEye-in-the-Mobile). These threats are designed to intercept text messages from online banking services which contain transaction authorization numbers, or mTANs.
New versions of ZitMo and SpitMo appear regularly, both for Android and other operating systems. Virus writers continue to use the same methods to conceal their threats as they did two years ago. The method of choice varies between a disguise as a “security certificate” or smartphone security software. Users end up actually downloading malware to their devices instead of the antivirus app they think they’re getting.

ZitMo disguised as a security application
Just because Android is so prevalent today does not mean that no one is using other operating systems. For example, virus writers seemed to ignore the rumors of the BlackBerry platform’s impending demise. In 2012, new versions of ZitMo appeared for BlackBerry; in one particular attack, cybercriminals used threats targeting both the BlackBerry and Android platforms, and the C&C numbers were the same in both.
Several new ZitMo modifications for Android have started to look more like their “brothers” targeting other platforms. Previously ZitMo for Android had only relatively primitive functions (primarily the ability to forward incoming text messages containing mTANs). However, the latest versions of this Trojan have included an expanded list of commands that are used by the writers of the malicious program to control and manage the threat’s operations.

An example of some of the commands in ZitMo for Android
Before 2012, attacks launched to steal mTANs had been detected in just a handful of European countries: Spain, Italy, Germany, Poland, and a few others. These attacks involved users of a variety of mobile platforms: Android, BlackBerry, Symbian, and Windows Mobile. In late 2012, Russia became one of the targets, as online banking became more commonplace — a factor that did not go unnoticed by virus writers. The widespread Trojan Carberp, which operates in a similar way to that of ZeuS, got its own mobile version: Trojan-Spy.AndroidOS.Citmo.
Just like its partner in crime ZeuS ZitMo, the CitMo Trojan is capable of concealing incoming text messages containing mTANs and forwarding them to malicious users. Different versions of CitMo forward intercepted text messages both to the telephone numbers of cybercriminals and to their remote servers.
One version of Carberp changed the landing page of a Russian bank’s online banking system. Users were asked to download and install a program allegedly required to enter the system. Users could opt to receive a link to the program by text message, either by providing their phone number in advance, or by scanning a QR code.

QR codes are one way to download malware
The link in this example led to the AberSafe application, which was actually Trojan-Spy.AndroidOS.Citmo, and was in the Google Play app store within two weeks.
After launching the malicious program, potential victims would be asked to enter their telephone numbers. The numbers would be recorded in an auth.txt file and sent to a remote server run by the malicious users. After a while, the users would receive a text message with a five-figure code meant to be entered in the application. This code was written into an authcode.txt file and used with the telephone number as data ID which the malware would then send to the remote server.
During the attack and theft of mTANs, the Trojan would need to hide incoming text messages from the online banking system. Otherwise, when malicious users made attempts to transfer funds from the compromised account, the messages could arouse suspicion.
CitMo downloaded information from the malicious users’ server about the numbers associated with those incoming text messages that needed to be hidden. It forwarded that data to the remote server (written in the file hide.txt), as well as data on numbers associated with incoming texts that did not need to be hidden (written into the view.txt file). When an incoming text message was received, CitMo would check the sender. If the sender’s data was on the hide list, then the text would be hidden and written into the file messages.txt, which was sent to the malicious users’ remote server.
SMS Trojans
The most common methods of monetizing mobile threats among malicious users continue to evolve. Back in 2011, one of the most interesting trends was the emergence of SMS Trojans targeting users in Europe and North America. In 2012, Kaspersky Lab detected fully-fledged affiliate programs used to spread SMS Trojans among users in these same regions. Affiliate programs, as is well known, are some of the most effective tools for creating, spreading, and monetizing malicious programs.
In 2012, the Vidro family of SMS Trojans for Android was detected, primarily targeting users from Poland. This SMS Trojan did not seem particularly special in any way, but there was one small detail that set it apart from the others: this threat spread via adult content sites associated with mobile affiliate programs intended to monetize adult content traffic.
This threat was downloaded from the malicious domain vid4droid.com. This domain was controlled by two name servers with the address carmunity.de, and the mail server vid4droid.com, on tecmedia.eu. There are several hosts (sex-goes-mobile.biz, sexgoesmobile.biz, sexgoesmobil.com, to name a few) where the name and mail servers are the same as on vid4droid.com. If a potential victim were to visit one of these hosts, he would be redirected to sexgoesmobile.com. This site is the affiliate program website for monetizing mobile-based adult content traffic.

The home page of the SexGoesMobile.com affiliate program
Many mobile affiliate programs (at least the Russian ones) offer full access to so-called promo tools to all of their participants, and SexGoesMobile is no exception. Each affiliate involved with SexGoesMobile has its own ID. An affiliate can create a mobile site with an existing template (each template has its own domain name) and generate a unique URL with its own ID that then leads to vid4droid.com, and then post this URL on their website.
Once a potential victim clicks on one of these standard websites, the user will be taken to vid4droid.com. At the same time, a unique string of letters and numbers will be generated on the remote server based on the referrer’s information (unique URL and affiliate ID). The website will then invite users to download an alleged adult content app (vid4droid.apk), which is in fact the Vidro Trojan.
Once on a mobile device, the Trojan sends a text message to the Poland-based paid number 72908 with the text “PAY {unique sequence of letters and numbers}” — the same unique string of letters and numbers that was generated using the affiliate’s URL and ID. As a result, each affiliate stole user money using their “own” SMS Trojan, which sent text messages containing a unique string.
The emergence of similar affiliate programs outside of Russia or Ukraine points to the existence of a fully functioning mobile malware industry – not just in Russia, but other countries as well.
Incidents involving official app stores
In spite of the fact that Google introduced its new antivirus module Google Bouncer, which automatically scans all new apps on Google Play (formerly known as Android Market), there has been no major change to the average number or scope of incidents.
The public’s attention is usually drawn to the largest number of infections as was the case with the Dougalek incident that infected tens of thousands of users (primarily in Japan). This led to one of the largest personal data leakages caused by a mobile device infection. A while after this incident took place, Tokyo police arrested five people suspected of creating and spreading the threat, making it the second mobile malware incident to result in arrests in 2012.
In 2012, we saw another major event: the first malicious program for iOS was detected in Apple’s App Store. In early July, a suspicious application entitled “Find and Call” was detected. Copies were found in both the App Store and Android Market.

Find and Call installed on an iOS phone
Once this application was downloaded and launched, the user would see a request to register the program, which required entering an email and phone number. If, after doing so, the user tried to find friends in his contacts using this app, then all of his contacts would be uploaded to a remote server – without the user suspecting a thing – in the following format.
|
1 |
http://abonent.findandcall.com/system/profile/phoneBook?sid= |
Each number stolen from contacts would then receive a spam text message with a link suggesting the recipient download the Find and Call app.
After information was published about this incident, Kaspersky Lab began to receive questions about why exactly this app qualified as malicious. It is considered malware because it hides the fact that it downloads user contact information to a remote server to subsequently send text messages.
Fortunately, this incident is thus far the only confirmed detection of a malicious program in the iOS App Store.
Cyberespionage
Throughout 2012, we expected to see more cases of data theft from mobile phones and people being tracked via their phones and GPS services. Unfortunately, this is exactly what happened. The number of malicious programs exhibiting the behavior of either Trojan spies or backdoors has increased hundreds of times over. It’s also true that there is a growing number of commercial apps for monitoring, and it can be hard to differentiate these from malicious programs.
There have been a number of remarkable episodes in the history of mobile espionage. Readers may recall an event in 2009 when one of the largest operators in the UAE sent out a text message with a link to spyware under the pretext of a BlackBerry security update. Another critical aspect is government interest in gaining access to secure communications utilized in BlackBerry smartphones.
The most notable and scandalous mobile espionage events of 2012 were:
- the detection of a mobile version of the spyware module FinSpy, developed by the British firm Gamma International;
- the disclosure of technical details of cyber intelligence operations, dubbed Red October, an incident where data and secret information was collected not only from the computers and network equipment of the organizations that were attacked (diplomatic and government agencies), but the mobile devices of their employees, as well.
Both these events deserve a more in-depth review.
FinSpy
The mobile versions of FinSpy are part of Gamma International’s portfolio. Data about the existence of this suite of remote monitoring tools first appeared back in the first half of 2011. That same year, more information was released pointing to mobile versions of FinSpy. Then, in 2012, The Citizen Lab managed to get its hands on mobile versions of FinSpy for Android, iOS, Windows Mobile, Symbian, and BlackBerry for analysis.
The modifications of FinSpy for various platforms have many features in common:
- logging incoming and outgoing calls;
- concealed calls to eavesdrop on the target’s surroundings;
- stealing information from smartphones (call logs, text and media messages, contacts, etc.);
- coordinate tracking;
- Internet and text message communication with the command center.
But each platform’s version has some special features, as well. For example, FinSpy for Symbian is able to take screen shots; FinSpy for BlackBerry can also monitor communication via BlackBerry Messenger; the version for Android can turn Airplane Mode on and off, and FinSpy for iOS can be installed with a limited customized selection of devices and specific UDIDs, while the Windows Mobile version uses so-called XML provisioning of configuration files to change security policies.
One curious aspect of all the mobile versions of FinSpy is the creation and use of the 84c.dat configuration file. The mechanisms used to generate it differ based on the operating system, but in the end, it contains the data needed for the spyware module to operate (the C&C server address, the mobile C&C number, the ports used, and other data).

A part of the 84c.dat configuration file for Android, encrypted with base64
The main function of all of FinSpy’s mobile modules is nothing new or unique. A similar set of functions has already been seen multiple times in commercial spyware such as FlexiSpy or MobileSpy. What makes FinSpy different is its developer: a company that is officially registered in Great Britain and, based on information about the company on its official website, develops remote monitoring tools for government organizations.
There is currently no information on who commissioned the FinSpy attacks and the specific victims, and any questions are likely to remain unanswered in the future. However, even without that information, the appearance of FinSpy has opened a new chapter in the history of mobile malware.
Red October
By late 2012, if anyone had any lingering doubts about the relevance of mobile spyware, they were surely quashed after the publication of information about Red October operations: mobile devices are finding themselves on the receiving end of targeted and espionage attacks, just like conventional computers.
We have evidence that certain unknown individuals behind this operation are interested in harvesting data from mobile devices. They can access this information not only by using mobile malware, but also by using modules for Windows that operate when devices are connected to an infected computer. In this section, we will summarize the information we have about Red October’s mobile modules as well as other information that may be related in some way.
One of the Red October modules — RegConn — is responsible for collecting system data and information about the software installed and used on the infected computer. This data is harvested by reading certain registry keys (a list of keys is contained in the module itself). Among the keys, the following stand out:

Registry keys in the RegConn module
In one way or another, these registry keys are all associated with software that works with mobile devices (iTunes, Nokia PC Suite, etc.) that might be installed on an infected computer.
Another component of Red October was created for iPhone. This module is designed to harvest information from a smartphone when it is connected to a computer infected with the module. It uses the iTunes directory file CoreFoundation.dll. Note that the module can launch one of two different services: one for phones that have been jailbroken, and one for phones that have not. In either case, the module will attempt to collect the following:
- information about the device itself, starting with its EMEI and ending with its firmware version;
- files with the following extension: .jpg, .jpeg, .txt, .doc, .docx, .xls, .xlsx, .ppt, .pptx, .dot, .dotx, .odt, .djvu, .odts, .reg, .rtf, .zip, .rar, .pdf, .7z, .wab, .pab, .vcf, .ost, .wav, .mp4, .m4a, .amr, .log, .cer, .em, .msg, .arc, .key, .pgp, .gpg;
- the contents of files with data on SMS text messages, contacts, call logs, notes, the calendar, voicemail, Safari browser history, and email.
The module for Nokia has a similar function and also harvests data about the device itself, text and media messages, the calendar, contacts, and installed apps. It also attempts to locate and harvest files with the following extensions: .txt, .cdb, .doc, .docx, .xls, .xlsx, .ppt, .pptx, .dot, .dotx, .odt, .djvu, .odts, .reg, .rtf, .zip, .rar, .pdf, .7z, .wab, .pab, .vcf, .ost, .jpg, .waw, .mp4, .m4a, .amr, .exe, .log, .cer, .eml, .msg, .arc, .key, .pgp, .gpg. It uses ConnAPI.dll from PC Connectivity Solution to interact with mobile devices hooked up to the infected computer.
Equally worthy of mention are the components of Red October that run on Windows Mobile. These modules can be broken down into two groups:
- modules running on infected Windows computers (used to infect/update Windows Mobile devices connected to an infected computer);
- modules installed on connected Windows Mobile smartphones by a Windows component.
With the first group, the objective is not to harvest information from the connected Windows Mobile device. Instead, the main goal is to install a backdoor onto the smartphone (or update one that has already been installed). A backdoor component that installs a module in the first category onto a smartphone is referred to in some circles as a “zakladka” or “bookmark.”
In addition to backdoors, the Windows component also downloads other executable files onto devices. These .exe files are used to change the device’s configuration, and launch, update, and delete backdoors. They can also copy a special configuration file (winupdate.cfg) from a computer onto a smartphone.
This file is initially encrypted. The deciphered file looks like this:

winupdate.cfg deciphered
This file contains data on MCC/MNC codes (MCC = Mobile Country Code; MNC = Mobile Network Code – in other words, the country code and the cellular provider’s code). We have tallied up a total of 129 unique countries and over 350 cellular providers in those countries.
The zakladka backdoor component determines a smartphone’s MCC/MNC and then compares the data it has collected with the data from the winupdate.cfg file, and writes everything into a log file.
In its operations with the C&C the zakladka module attempts to send a POST request to the command center addresses specified in the module (win-check-update.com or, if that domain is unavailable, mobile-update.com):
|
1 |
'POST %s HTTP/1.0 Accept: */* User-Agent: Mozilla/4.0 Content-Length: %d Host: %s' |
In response, the module receives a file from the remote server which it then stores in Windows%u.exe and launches.
And speaking of C&C domains – in addition to win-check-update.com and mobile-update.com, Kaspersky Lab has detected the following names of suspected C&Cs:
- cydiasoft.com
- htc-mobile-update.com
- mobile-update.com
- playgoogle-market.com
- security-mobile.com
- world-mobile-congress.com
In brief, one can draw the following conclusions.
First of all, we know about several Red October modules designed to steal information from different types of mobile devices.
Second, there are indirect signs (registry key lists, domain names) that there are other Red October modules designed to work with other mobile devices, including those running on Android and BlackBerry. However, at the time of this article’s publication, we have not detected modules for those platforms.
Conclusion
Since the appearance of mobile malware, we see events and incidents each year that set the tone for the next stage of mobile malware evolution – and 2012 can be considered one of the most notable thus far. Why?
For starters, the number of mobile threats skyrocketed in 2012.
Next, we saw Android become mobile Target Number One among cybercriminals.
Third, mobile threats have gone international. Today, cybercriminals are no longer focusing most of their efforts on mobile device users in Russia and China. Major incidents causing no small amount of damage took place in a number of countries.
Last but not least, evidence was found that mobile devices and the data stored on them are targets not only for your run-of-the-mill cybercriminals but also a variety of organizations behind attacks like Red October.






















Mobile Malware Evolution: Part 6