
It comes as no surprise that mobile devices are gaining wider acceptance and usage with each passing day. Small and convenient, they can easily be carried between work and home and used efficiently at each. But it is exactly the ease with which they are transported which makes them particularly liable to both loss and theft – thus becoming the source of a confidential information leak with major consequences for companies or individuals alike. So how can we protect such mobile devices against such vulnerabilities?
What follows is the first Russian project to focus on mobile device usage from the point of view of their data-protection issues, and the leakages which arise due to theft or loss.
Summary
- Mobile device use is widespread. More than half those surveyed (60.8%) have at least one, and almost a third (29.3%) have two.
- The vast majority of users (70.7%) keep confidential information on their mobile device – be it their own or their employer’s.
- Almost all users (78.1%) who lost a portable device containing confidential information still do not encrypt their data today.
- The culture of carelessness about leakages via mobile devices will doubtless lead to major losses both for the users themselves and their employers.
Methodology
The survey was conducted between February 1st and March 1st, 2007. 1500 mobile device users participated in the survey, which was conducted on the websites of Zoom.CNews and InfoWatch. Percentages are rounded off to the nearest tenth of a percent. Where total percentages exceed 100%, this is due to multiple answers to a question being allowed.
Fig. 1 shows what mobile devices are in use. The laptop is the most widely used (47.3%). Next come the Smartphone (45.8%) and the pocket computer (26.6%). A significant proportion of respondents (30.4%) use other devices.
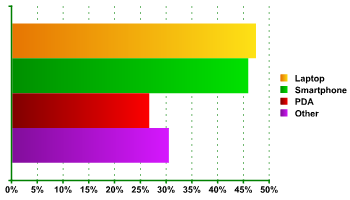
Fig. 1. Types of mobile device
As noted above, total percentages exceed 100% where respondents were allowed to give more than one answer to a question. The numbers here demonstrate the high take-up of mobile devices with many people having more than one. With each new device, the chances of an information leak naturally increase.
Fig. 2 demonstrates these tendencies. Here we can see that 8.5% of users have three times more likelihood of losing data than the 60.6% percent who have only one device.
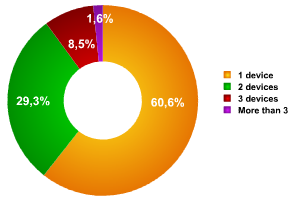
Fig. 2. Number of mobile devices
Where mobile devices are used
Fig. 3 shows the most common areas where mobile devices are used. The most popular usages are to store contact lists (friends / colleagues) and to check email (sending and reading). These options were chosen by 77.7% and 70.8% of respondents, respectively. In third place was Internet usage (63.8%), followed by diary use (33.5%) and online shopping (23.4%).
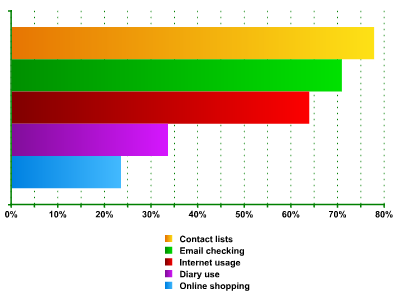
Fig. 3. Mobile device usage
By understanding the uses to which respondents put their mobile devices, it is possible to understand what kind of data they keep on them. Of primary importance is the fact that 77.8% of users keep records of their personal friends and colleagues on their portable devices. Such data is kept in the address book or in a contacts holder. A further 70.8% of respondents keep their personal and/or their business correspondence on their mobile device, along with access details to email accounts. The leakage of such data can not only lead to unwanted dissemination of private details, but also to blackmail, identity theft, industrial espionage, etc.
A less hazardous use of mobile devices is Internet usage. In the event of either loss or theft of the device, the most the thief can get his hands on is the history of web pages visited. However, if the user also makes purchases online – as 23.4% of respondents do – then such a leak can lead to direct financial losses since the browser often cache credit card information, user login and passwords to online shops as well as other details. All these items are highly valuable and interesting to criminals.
Lastly, diary use (33.5%) indicates that the mobile device user is likely a corporate employee. He has a packed schedule and uses the diary to plan his time. This data is also confidential or, at the very least, private. Therefore, its loss or theft can be a blow not only to the user, but also to the employer.
Top 10 most expensive mobile device information leaks
| № | Incident | Date | Victims | Potential Cost | Details |
| 1 | Leak of US military personnel and veterans’ data | May 2006 | 28.7 million | $45 billion | Read |
| 2 | Laptop stolen from Nationwide Building Society, UK | Aug 2006 | 11 million | $1.5 billion | Read |
| 3 | A portable hard drive with company data stolen by insider at Dai Nippon Printing | Jul 2006 | 8.64 million | $1.2 billion | Read |
| 4 | A laptop stolen from the US war veterans’ medical centre in Birmingham with doctors’ and patients’ personal data | Jan 2007 | 1.8 million | $367 million | ReadSee also |
| 5 | A mobile computer stolen from Computer Services (ACS) with personal client data | Oct 2006 | 1.4 million | $320 million | Read |
| 6 | Laptop lost by subcontractor for Texas Guaranteed with TG’s client data | May 2006 | 1.3 million | $237 million | Read |
| 7 | Laptop stolen from a Boeing employee’s car | Nov 2006 | 382,000 | $147 million | Read |
| 8 | Laptop stolen from CS Stars with names, addresses and Social Security numbers of New York workers | Jul 2006 | 540,000 | $84 million | Read |
| 9 | Laptop with personal data stolen from an employee of the accountancy firm Hancock Askew | Oct 2006 | 401,000 | $73 million | Read |
| 10 | Investigation at the Vassar Brothers medical centre found the loss of a laptop and backup disk with patient data | Jan 2007 | 257,800 | $47 million | Read |
Sensitive data held on mobile devices
The next part of the survey regarded the data held on portable devices. It found that only 29.3% of respondents did not keep sensitive data on their mobile computers. Fig. 4 shows that the majority of users (68.1%) keep personal data on their mobile devices. And corporate and confidential documents as well as intellectual property are held by 16.5% and 14.9% of respondents. A mere 12.2% of respondents use their mobile devices to hold private client or partner data.
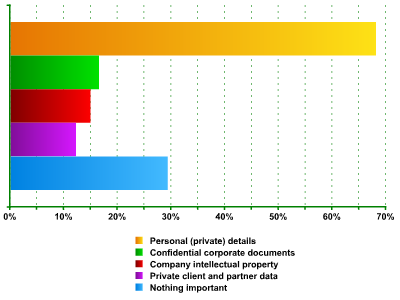
Fig. 4. Confidential information on mobile devices
Thus, the overwhelming majority (70.7%) of respondents keep some kind of confidential information on their mobile device. But how well is this data protected against leakage?
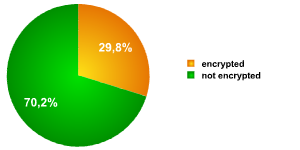
Fig. 5. Is data protected?
We know that only 29.8% of respondents use data encryption (see fig. 5). If we transpose this figure to mobile device users who keep confidential corporate documents, intellectual property or private client or partner data on their drives, then only 40.7% of them are using encryption. This means that more than half the respondents who keep valuable and secret data on their mobile devices do not protect their data at all. They are vulnerable to data leakage in the event of loss or theft of their devices.
We can also say that part of the reason for such an attitude is the fact that 83% of respondents had never lost a mobile device. However, 78.1% of those users who had been the victims of theft – or lost device – containing confidential data, admitted that they still did not use encryption. This indicates that we have a weak culture of information security and the main obstacle is laziness both on the part of individuals and companies.
Conclusions
The constant development of mobile technology will doubtless aggravate the problem of leaks via portable devices. Already, the vast majority (70.7%) of respondents keep some form of confidential information on their mobile devices. In addition, 17% of users have lost a device at one time. But, even though that had been hit by a leak, 78.1% of respondents still do not use encryption. This figures indicate that the problem of confidential data leaks via mobile devices is on the increase. This situation will either lead to serious losses for companies and users, or force them to protect themselves.






















Mobile device security 2007