
Miners are a class of malware whose popularity has grown substantially this year. The actual process of cryptocurrency mining is perfectly legal, though there are groups of people who hoodwink unwitting users into installing mining software on their computers, or exploiting software vulnerabilities to do so. This results in threat actors receiving cryptocurrency, while their victims’ computer systems experience a dramatic slowdown. Over the last month alone, we have detected several large botnets designed to profit from concealed crypto mining. We have also observed growing numbers of attempts to install miners on servers owned by organizations. When these attempts are successful, the companies’ business processes suffer because data processing speeds fall substantially.
In general, the number of users that have encountered cryptocurrency miners has increased dramatically in recent years. For example, in 2013 our products protected around 205,000 of users globally when they were targeted by this type of threat. In 2014 the number increased to 701,000, and the number of attacked users in the first eight months of 2017 reached 1.65 million.
Propagation methods
The main method for installing miners makes use of adware installers that are spread using social engineering. There are also more sophisticated propagation methods – one is exploiting vulnerabilities such as EternalBlue. In that case, the victim is a server, which is especially advantageous for the threat actors because they end up with a more powerful asset.
The following types of ads can be found in the Telegram messaging service:
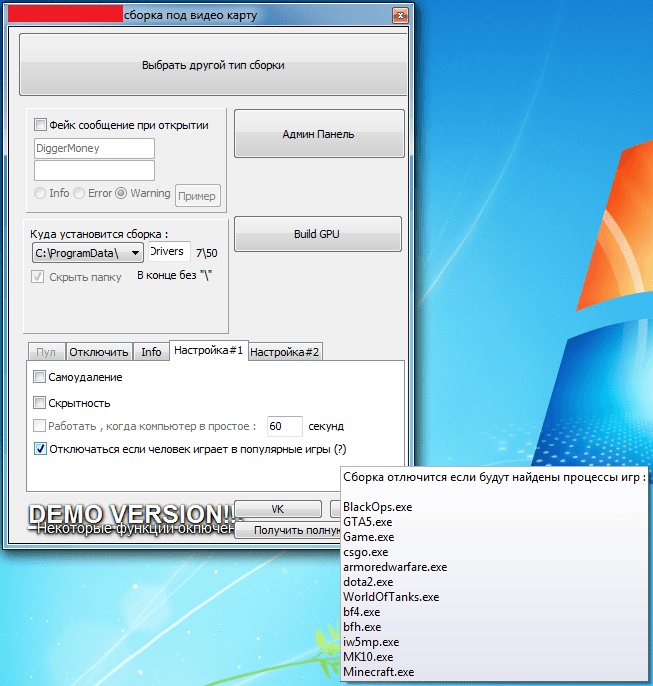
By following the advertised link, the user can download a trial version of a builder which assembles a dropper for a miner with some extra features, including suspension of the software whenever the user launches a popular game.
To receive the full version, the user is prompted to contact the administrators of a group on the VKontakte social media site.
Main principles of operation
Concealed miners are very difficult to detect due to their specific nature and operating principles. Any user can independently install this kind of software on their computer and legally use it for mining a cryptocurrency.
Often, a crypto miner comes with extra services to maintain its presence within the system, automatic launch every time the computer is switched on, and concealed operation.
These services can, for example:
- Try to turn off security software;
- Track all application launches, and suspend their own activities if a program is started that monitors system activities or running processes;
- Ensure a copy of the mining software is always present on the hard drive, and restore it if it is deleted.
We recently detected a network containing an estimated 5,000+ computers on which Minergate, a legal console miner, was installed without the users’ knowledge or consent. The software was distributed via an adware installer, and was installed as a service on the victim computer in the following way:
- The user downloads an installer from a file hosting service under the guise of a freeware program or keys to activate licensed products;
- When launched, the installer downloads the miner’s dropper (exe) to the victim computer;
- The dropper writes Minergate and the tool exe to the hard drive, using srvany.exe when the system boots to launch the miner as a service named windows driver.exe;
- The dropper creates an additional service named exe which ensures the continuous operation of Minergate; if Minergate is deleted, the dropper restores it on the hard drive.
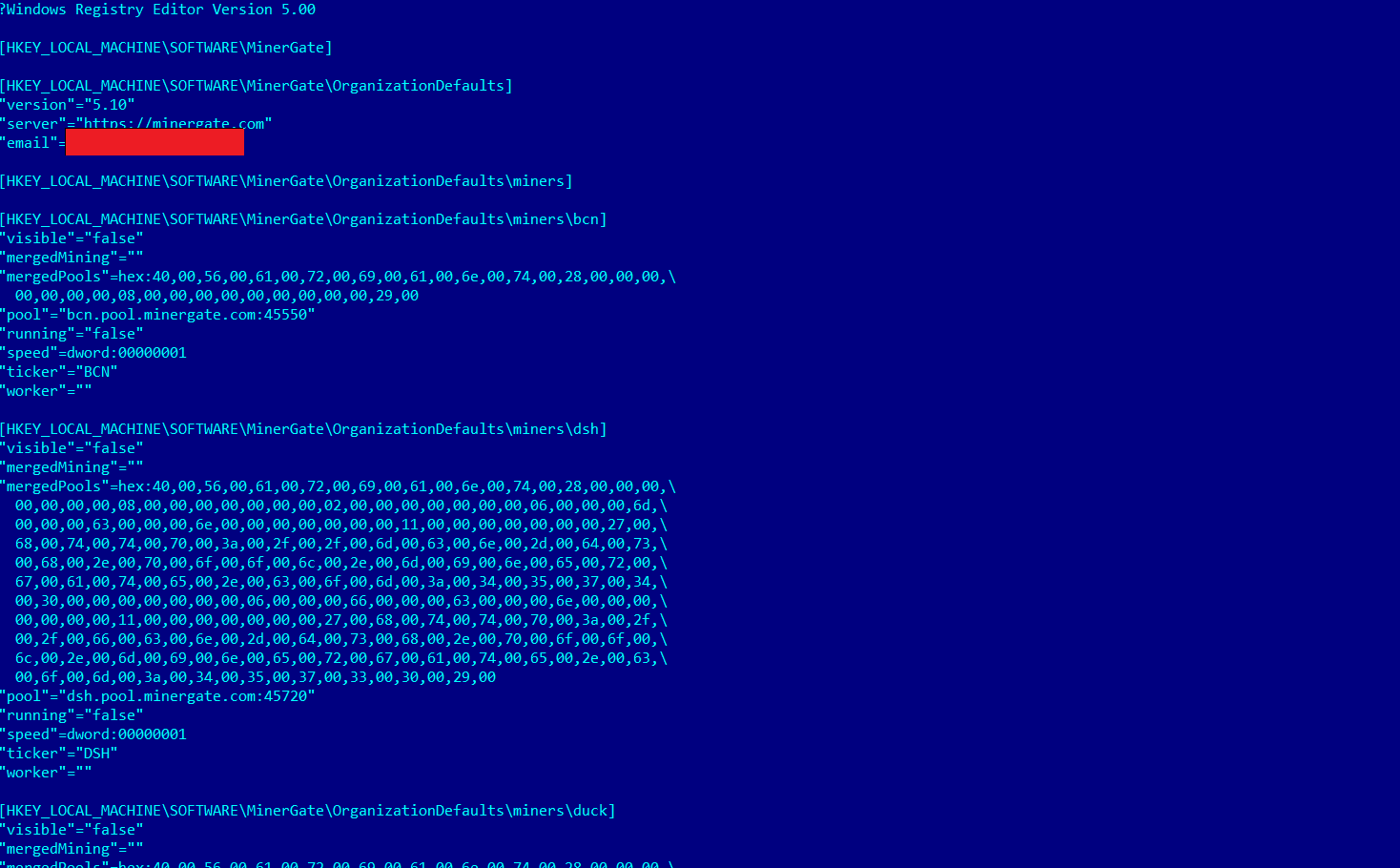
The dropper stores the miner configuration info in a registry record.
Moneymaking scheme
The two currencies most often used in concealed mining are monero (XMR) and zcash. These two ensure the anonymity of transactions, which comes in very handy for threat actors.
According to the most conservative estimates, the mining network can generate anything up to $30,000 a month to its owners.
The above screenshot shows a wallet coded into the miner’s configuration data. At the time of writing, a total of 2,289 XMR had been transferred from this wallet, which at the current exchange rate is equivalent to $208,299.
Assuming a regular desktop computer yields a hash rate of 30-100 H/sec, this bot may contain in the region of 4,000 computers.
Conclusion
As we see, threat actors will grasp any opportunity to make illegal money, and the methods to make money online are continuously evolving. The development of the cryptocurrency market has led to an explosive growth in cases where miners are installed without users’ knowledge or consent. This can be explained by the fact that when a new cryptocurrency is emerging, it is much easier to mine and make money from it. Threat actors are on the lookout for ways to use the resources of somebody else’s hardware, and often it is regular users who fall victim.
Kaspersky Lab’s solutions detect all the threats described in this article under the verdicts:
- Win32.BitCoinMiner.hxao
- PDM:Trojan.Win32.Generic
IOCs:
185b23c602e64dc6bcd2a2776095653e
33e46f76bc9bf1ff8380406f111f56af
26f42df21371bd4afe86a643ac0a6b44
25451e6fe30b54b432854bde5b9abb74
Miners on the Rise
























Karthik
Hi Securelist team,
I analysed same sample and I have a question about your findings.
I figured out that they are using MinerGate admin V5.10 version. This app
does not require a wallet address to mine for the cyber criminal which makes it
perfect for them. Also, the second last picture (wallet of mining botnet) is not from minergate
website.
So my question is how is it possible to find that they mined 2,289 XMR?
Ben
I’m wondering about the same thing. Doesn’t Monero ensure that address measurements are impossible? My guess is they accessed the mining pool and reviewed the stats there.
DARK ANGEL
Tracking the bitcoin address, harcoded in the miner configuration file