
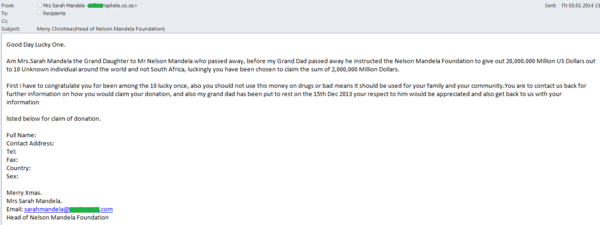
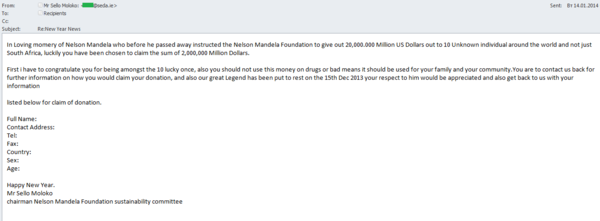
In December, we registered ‘Nigerian’ mailings exploiting the theme of Nelson Mandela’s death to trick users. The same topic is still inspiring spam mailings in January – but this time there are some differences in the content – the intro and the author’s signature. At first glance there seemed to be nothing in common between the emails.
For example, the first email was written on behalf of Mandela’s granddaughter while the author of the second message claimed to be the chairman of one of Mandela’s funds. These names were identified in the ‘From’ field and in the signature at the end of the message. The supposed granddaughter from the first email wrote about a fund whose chairman turns out to be the author of the second email. The remaining text of both messages was identical down to the last letter.
‘Nigerian’ scammers used their traditional trick of informing the user that before his death Nelson Mandela had given instructions to distribute $20 million from the fund to randomly selected people around the world, and of course the recipient of the email was among the ten lucky people. For more information about this windfall, the victim had to contact the author of the email. In the ‘granddaughter’ message the contact address was different from the sender’s address; the ‘chairman’ suggested no alternative contacts. Yet another specific feature of the mass mailing was the scammers’ attempt to link their ‘Nigerian letters’to the recent holidays: Christmas and New Year were mentioned both in the subject and at the end of the email.






















Mandela’s Millions