
In late October 2024, a new scheme for distributing a certain Android banking Trojan called “Mamont” was uncovered. The victim would receive an instant message from an unknown sender asking to identify a person in a photo. The attackers would then send what appeared to be the photo itself but was actually a malware installer. Shortly after, reports surfaced of Mamont being disseminated through neighborhood chat groups. Cybercriminals were touting an app to track a parcel containing household appliances they said they were offering for free. In reality, this was malware with no parcel-tracking functionality whatsoever. Both scams targeted individual users only. Recently, however, we noticed a number of websites promoting a variety of bulk-priced goods that could attract both individual bargain hunters and businesses. A closer look revealed a previously unknown Mamont dissemination pattern.
How we tried to save some cash on a purchase
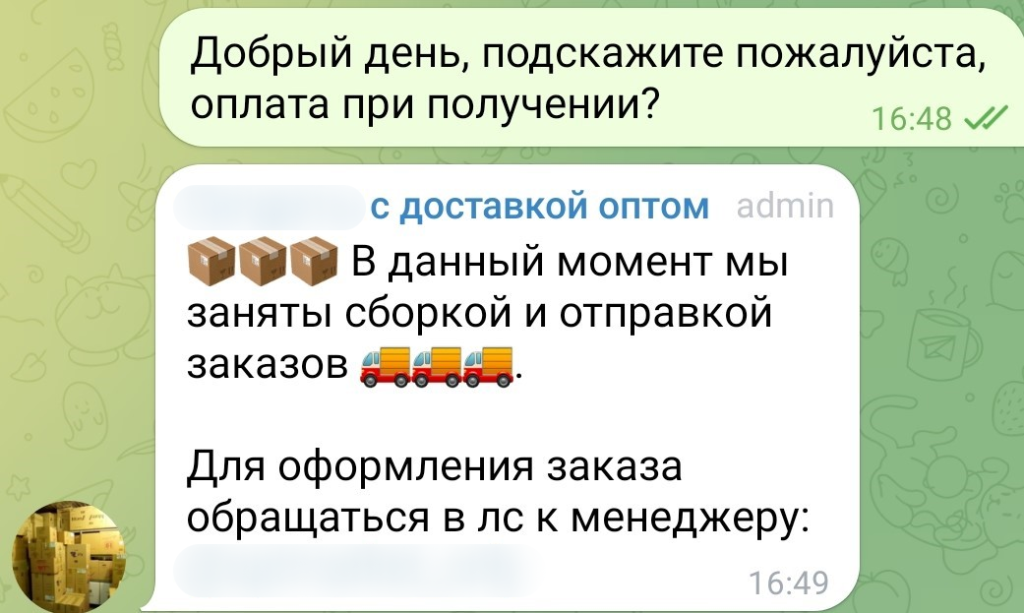
As we began our investigation, our attention was drawn to websites that offered various products at wholesale prices. We decided to place an order to see if there was a catch. The contact details for one of the stores contained a link to a dedicated private Telegram chat that instructed users to DM their manager to place an order.
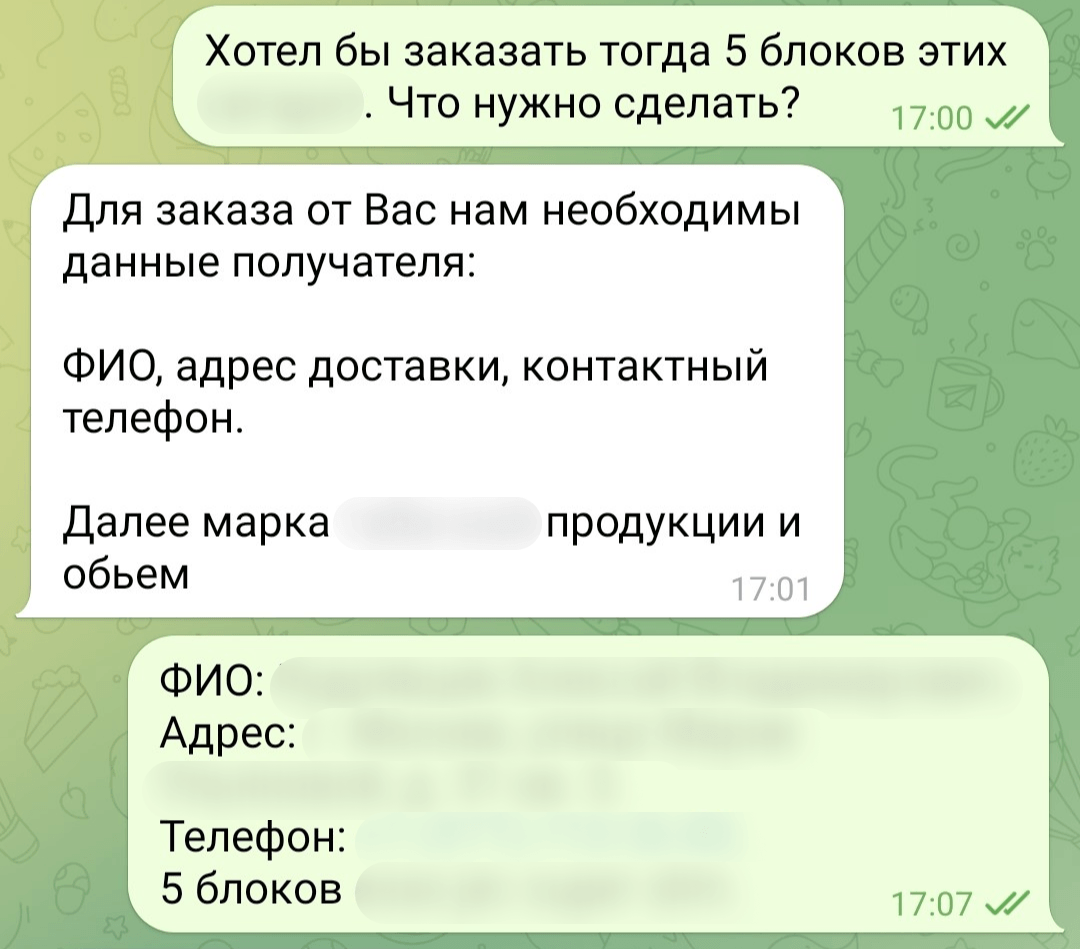
We did just that, checked the details, and made an order. They told us we could pay on delivery with no advance payment whatsoever. This was likely a way for the criminals to avoid arousing suspicions.
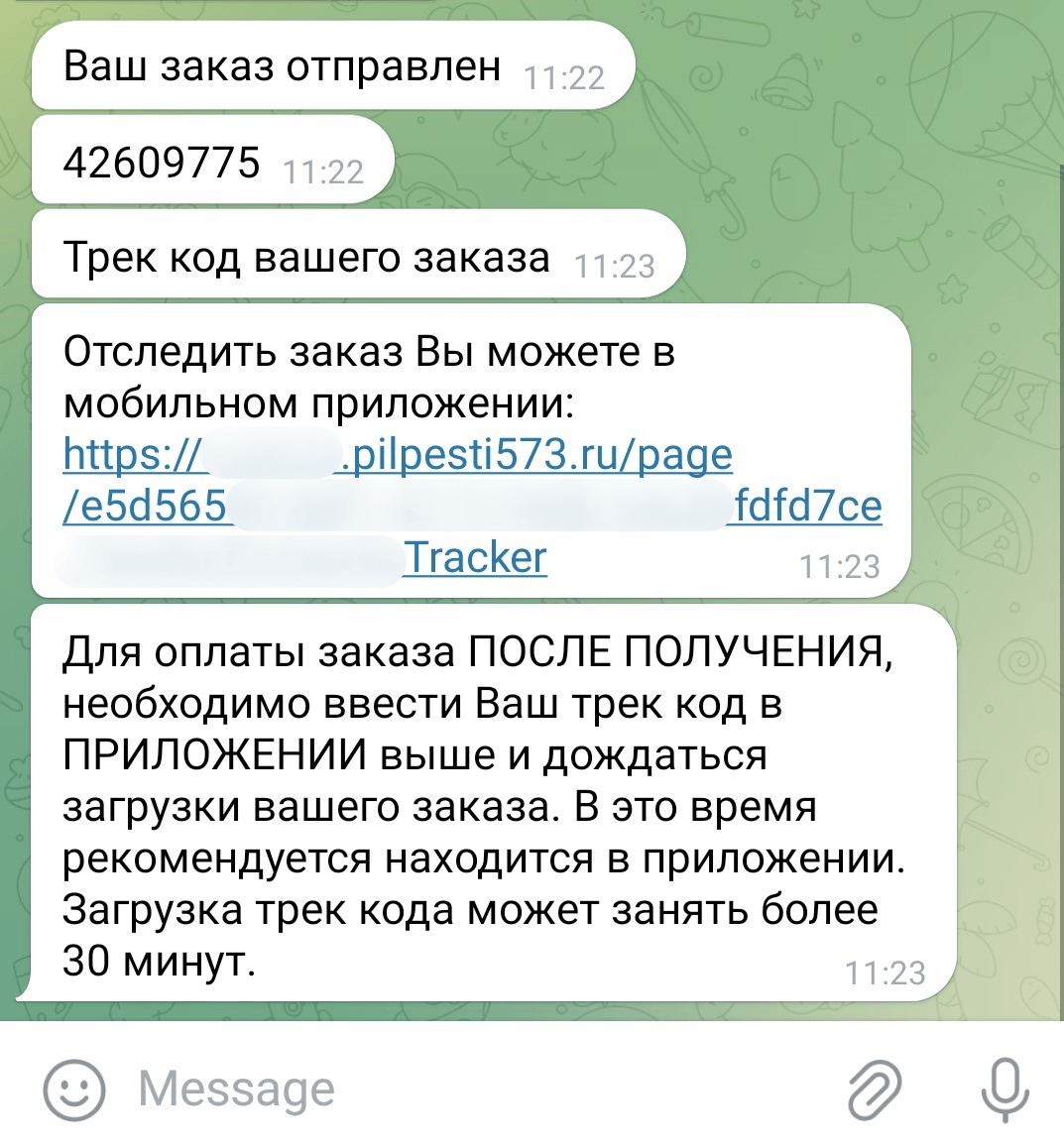
We were notified the following day that our order had shipped and could be tracked with a special mobile app linked in a message from the manager. The link directed users to a phishing site offering to download Mamont for Android (12936056e8895e6a662731c798b27333). The link came with a tracking number that had to be entered in the app. We reported the scam accounts and channels to Telegram, but the messaging service had done nothing to block them at the time of writing this.
We have to give it to the operators: the scam was quite convincing. The private channel was full of users asking questions, no prepayment was necessary, and the “shipping” took a credible length of time. We can’t rule out, however, that some of the group members were, in fact, bots keeping potential victims distracted. Our security products detect the malware spreading via this scam as Trojan-Banker.AndroidOS.Mamont.
The inner workings of the “tracker app”
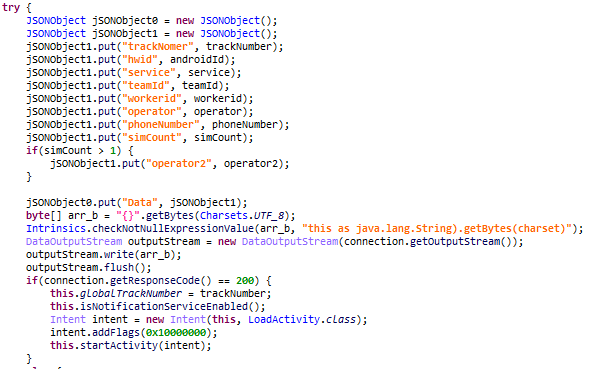
When launched, the Trojan requests permission to run in the background, and access to push notifications, text messaging, and calls. It then asks the victim to enter the tracking number previously received from the scammers, and sends a POST request containing device information along with the number to the C2 server. We believe the scam operators use that number for victim identification. If the POST request returns a 200 code, the Trojan opens a window that supposedly downloads order details.
The app also starts two malicious services. The first one hijacks all push notifications and forwards them to the attackers’ server. The other one sets up a connection with the attackers’ WebSocket server. The server responds with JSON-formatted commands. The “type” field in the object contains the command name. The object may also contain other fields with command arguments. The full list of commands with their descriptions is given in the table below.
| Command (type) | Description | Arguments (field name and content) |
| call | Sends a USSD request. The result of the request is forwarded to the C2. | number: request code. |
| callTwo | Sends a USSD request from the secondary SIM card. The result of the request is forwarded to the C2. | number: request code. |
| changeIcon | Changes the app icon. | useAlternativeIcon: a flag that changes the app icon to transparent if set to true, or restores the original icon if set to false. This is set to false by default. |
| custom | Runs an activity that displays a custom message. | text: the text of the message shown to the user. |
| hide | Hides the app icon. | N/A |
| oldsms | Sends all incoming text messages received in the last three days. | N/A |
| photo | Runs an activity that uploads a photo from the gallery. | text: the text of the message shown to the user. |
| show | Restores the original app icon. | N/A |
| sms | Sends a text message. | text: message text; number: recipient. |
| smsTwo | Sends a text message from the secondary SIM card. | text: message text; number: recipient. |
The “custom” and “photo” commands, designed to trick the user into giving away data, call for special attention. The “custom” command can be used to manipulate the victim into giving up various login details. When the app receives that command, the user sees a window with a text box for entering data, which is then sent to the command-and-control server. The “photo” command is similar to “custom”, but instead of a text box, it displays an image upload window. It appears that the attackers do this to harvest data for further social engineering scams like posing as law enforcement or a regulatory agency to trick users into sending money. Additionally, cybercriminals can leverage the banker’s capabilities to directly extract data from victims during this manipulation for added credibility.
Victims
The Mamont campaign exclusively targets Android phone users in Russia as highlighted by the operators themselves.
According to Kaspersky Security Network (KSN) anonymized telemetry data consensually provided by users, our security products blocked more than 31,000 Mamont attacks under the guise of a parcel-tracking app in October and November 2024.
Conclusion
What makes the scam detailed above notable is that both individual users and businesses may take the bait. The attackers lure victims with bulk-priced offers, spreading malware disguised as parcel-tracking apps. Admittedly, the scam is highly convincing and may well look like a bona fide offer to the victim. Besides, the scammers get the victim to contact them first, which boosts the level of trust.
Simple as it may be, the Trojan possesses the essential feature set for stealing login credentials through windows with customizable text elements and controlling SMS banking. We recommend following a few simple rules to avoid getting infected with this and other malware.
- Don’t click links in messages you get from strangers.
- Be wary of overly generous offers you come across online.
- Avoid downloading apps from anywhere but official sources.
- Use a reliable security solution to keep malware away from your device.
Indicators of compromise
C2 server
apisys003[.]com





















Download a banker to track your parcel