
IT threat evolution in Q3 2024
IT threat evolution in Q3 2024. Non-mobile statistics
IT threat evolution in Q3 2024. Mobile statistics
Targeted attacks
New APT threat actor targets Russian government entities
In May 2024, we discovered a new APT targeting Russian government organizations. CloudSorcerer is a sophisticated cyber-espionage tool used for stealth monitoring, data collection and exfiltration via Microsoft, Yandex and Dropbox cloud infrastructures. The malware utilizes cloud resources for its C2 (command and control) servers, which it accesses via APIs using authentication tokens. CloudSorcerer also employs GitHub as its initial C2 server. CloudSorcerer functions as separate modules – for communication and data collection – depending on the process it’s running, but executes from a single executable. It leverages Microsoft COM object interfaces to perform its malicious operations.
While the modus operandi of the threat actor is reminiscent of the CloudWizard APT that we reported on in 2023, the malware code is completely different. Consequently, we believe CloudSorcerer is a new threat actor that has emulated a similar approach to interacting with public cloud services.
Two months later, in July 2024, CloudSorcerer launched further attacks against Russian government organizations and IT companies. The campaign, which we dubbed EastWind, used phishing emails with malicious shortcuts attached to deliver malware to target computers. The malware, which received commands via the Dropbox cloud service, was used to download additional payloads.
One of these was an implant called GrewApacha, used by APT31 since at least 2021. The other was an updated version of the backdoor used by CloudSorcerer in its earlier attacks. This one uses LiveJournal and Quora profiles as initial C2 servers.
The latest attacks also use a previously unknown implant with classic backdoor functionality called PlugY. This malware, which is loaded via the CloudSorcerer backdoor, has an extensive command set and is capable of supporting three different protocols for communicating with the C2. The code is similar to that of the DRBControl (aka Clambling) backdoor, which has been attributed to APT27 by several companies.
BlindEagle adds side-loading to its arsenal
In August, we reported a new campaign by Blind Eagle, a threat actor that has been targeting government, finance, energy, oil and gas and other sectors in Latin America since at least 2018. The campaign aligns with the TTPs (Tactics, Techniques and Procedures) and artifacts used by BlindEagle, although the attackers have introduced one new technique to their toolset – DLL side-loading.
The attack starts with phishing emails purporting to be a court order or summons from an institution in Colombia’s judicial system. The email contains a link in the body of the message that is also contained in the attached file, which appears to be a PDF or Word document. Victims are tricked into clicking the link to retrieve documents related to the lawsuit.
These documents are in fact password-protected ZIP or other archives. The archive files contain a clean executable file responsible for initiating the infection process through side-loading, alongside various malicious files used in the attack chain. One of these files carries an embedded loader named HijackLoader, which decrypts and loads the final payload. The final payload is a version of AsyncRAT, one of the Remote Access Trojans (RATs) used by BlindEagle in previous campaigns.
You can read more details about this campaign and the TTPs employed by this threat actor in general here.
Tropic Trooper spies on government entities in the Middle East
The threat actor Tropic Trooper, active since 2011, has historically targeted government, healthcare, transportation and high-tech sectors in Taiwan, the Philippines and Hong Kong. In June 2023, Tropic Trooper initiated a series of persistent campaigns targeting a government body in the Middle East.
We were alerted to the infection in June of this year when our telemetry indicated recurring alerts for a new China Chopper web shell variant discovered on a public web server. China Chopper is widely used by Chinese-speaking actors. The server was hosting a CMS (Content Management System) called Umbraco, an open source CMS platform for publishing content, written in C#. The observed web shell component was compiled as a .NET module of the Umbraco CMS.
In the course of our subsequent investigation, we looked for other suspicious detections on this public server and identified several malware sets. These include post-exploitation tools that we have assessed with medium confidence to be related to this intrusion. We also identified new DLL search-order hijacking implants that are loaded from a legitimate vulnerable executable as it lacks the full path specification to the DLL it needs. This attack chain attempted to load the Crowdoor loader, named partly after the SparrowDoor backdoor described by ESET. During the attack, the security agent blocked the first Crowdoor loader, prompting the attackers to switch to a new, previously unreported variant with almost the same impact.
We attribute this activity with high confidence to the Chinese-speaking threat actor known as Tropic Trooper. Our findings show an overlap in the techniques reported in recent Tropic Trooper campaigns. The samples we found also demonstrate a high degree of overlap with samples previously attributed to Tropic Trooper.
The significance of this intrusion is that it involved a Chinese-speaking actor targeting a CMS platform that published studies on human rights in the Middle East, with a particular focus on the situation surrounding the Israel-Hamas conflict. Our analysis revealed that the entire system was the sole target during the attack, suggesting a deliberate focus on this specific content.
From 12 to 21: connections between Twelve and BlackJack groups
In the spring of 2024, posts containing personal data of real individuals began appearing on the -=TWELVE=- Telegram channel. This was soon blocked for violating Telegram’s terms of service, and the group remained inactive for several months. However, during our investigation of an attack in late June, we discovered techniques identical to Twelve’s and the use of C2 servers associated with this threat actor.
The Twelve group was established in April 2023 in the context of the Russian-Ukrainian conflict and has been attacking Russian government organizations ever since. The threat actor specializes in encrypting and then deleting its targets’ data, which suggests that the group’s primary objective is to cause as much damage as possible. Twelve also exfiltrates sensitive information from targeted systems and posts it on the group’s Telegram channel.
Interestingly, Twelve shares infrastructure, utilities and TTPs (Tactics, Techniques and Procedures) with the DARKSTAR ransomware group (formerly known as Shadow or COMET). This indicates that the two may belong to the same syndicate or activity cluster. At the same time, while Twelve’s actions are clearly hacktivist in nature, DARKSTAR adheres to the classic double extortion pattern. This variation in objectives within the syndicate highlights the complexity and diversity of modern cyberthreats.
In our September report on Twelve, we used the Unified Kill Chain methodology to analyze the group’s activities.
We also discovered overlapping TTPs with BlackJack, another hacktivist group that emerged in late 2023. This group’s stated aims, from its Telegram channel, is to find vulnerabilities in the networks of Russian organizations and government institutions. The threat actor has claimed responsibility for more than a dozen attacks, and our telemetry also contains information about other undisclosed attacks where indicators point to BlackJack’s involvement.
The group uses only freely available and open source software. This includes the use of the ngrok utility for tunneling, Radmin, AnyDesk and PuTTY for remote access, the Shamoon wiper and a leaked version of the LockBit ransomware. This confirms that this is a hacktivist group that lacks the resources typical of large APT threat actors.
Other malware
How “professional” ransomware groups boost the business of cybercriminals
Cybercriminals who want to get into the ransomware business don’t necessarily need to develop the software themselves. They can find a leaked ransomware variant online, buy ransomware on the dark web, or become an affiliate. In recent months, we have published several private reports detailing exactly this.
In April, IxMetro was hit by an attack that used a still-new ransomware variant dubbed “SEXi”, a group that focuses primarily on ESXi applications. In each of the cases we investigated, the targeted organizations were running unsupported versions of ESXi. This group deploys either LockBit or Babuk ransomware, depending on the platform – Windows or Linux, respectively.
In the majority of cases, the attackers leave a note containing an email address or URL for a leak site. In the case we looked at, the note included a user ID associated with the Session messaging app. The ID belonged to the attackers and was used across a number of different ransomware attacks on a variety of victims. This indicates a lack of professionalism and suggests that the attackers did not have a TOR leak site.
Key Group (aka keygroup777) has utilized no fewer than eight different ransomware families in its relatively short history (since April 2022):
Over the approximately two-year period that the group has been active, it has made minor adjustments to its TTPs with each new ransomware variant. For example, the persistence mechanism was consistently implemented via the registry, though the specific technique differed by family. In most cases, autorun was used, but we’ve also seen them using the startup folder. While Russian-speaking groups typically operate outside Russia, this is not the case with Key Group. Like SEXi’s, Key Group’s operations are not particularly professional. For example, the primary C2 channel is a GitHub repository, which makes the group easier to track, and communication is conducted over Telegram, as opposed to a dedicated server on the TOR network.
Mallox is a relatively new ransomware variant that first came to light in 2021 and kicked off an affiliate program in 2022. It’s unclear how the authors obtained the source code: perhaps they wrote it from scratch, used a published or leaked version, or – as they claim – purchased it. Although it started as a private group running its own campaigns, it launched an affiliate program shortly after its inception. It is noteworthy that the group only engages with Russian-speaking affiliates and does not do business with novices. Affiliates are explicitly instructed to target organizations with a minimum revenue of $10 million and to avoid hospitals and educational institutions. Mallox uses affiliate IDs, making it possible to track affiliate activity over time. In 2023, there were 16 active partners. In 2024, only eight of the original affiliates were still active, with no newcomers. Other than that, Mallox has all the typical Big Game Hunting attributes that other groups have, such as a leak site and a server hosted on TOR.
You can read more about the above threats here. You can also read our full report on Mallox ransomware here. To learn more about our crimeware reporting service, contact us at crimewareintel@kaspersky.com.
HZ Rat backdoor for macOS
In June, we discovered a macOS version of the HZ Rat backdoor. The backdoor was being used to target users of the enterprise messenger DingTalk and the social networking and messaging platform WeChat. Although we do not know the original distribution point for the malware, we were able to locate an installation package for one of the backdoor samples – a file named OpenVPNConnect.pkg.
The samples we discovered almost exactly replicate the functionality of the Windows version of the backdoor with the exception of the payload, which is received in the form of shell scripts from the attackers’ server. We noticed that some versions of the backdoor utilize local IP addresses to connect to the C2, leading us to believe the threat might be targeted. This also suggests that the attackers intend to use the backdoor for lateral movement through the target network.
The data collected about the targets’ companies and contact information could be used to spy on people of interest and lay the groundwork for future attacks. During the course of our investigation, we did not encounter the use of two of the backdoor’s commands (write file to disk and send file to server), so the full scope of the attacker’s intentions remains unclear.
Hacktivist group Head Mare targets Russia and Belarus
Since the start of the Russo-Ukrainian conflict, numerous hacktivist groups have emerged whose main goal is to cause damage to organizations on the opposing side of the conflict. One such group is Head Mare, which targets organizations in Russia and Belarus.
While such hacktivist groups tend to use similar TTPs, Head Mare uses more up-to-date methods to gain initial access. For example, the attackers leveraged a recently discovered vulnerability in WinRAR (CVE-2023-38831) that allowed them to execute arbitrary code on a compromised system via a specially crafted archive. This approach allows the group to more effectively deliver and disguise the malicious payload.
As is the case with most hacktivist groups, Head Mare maintains a public account on the X social network, which it uses to post information about some of its victims.
Head Mare has targeted a variety of industries, including government, energy, transportation, manufacturing and entertainment. The group mainly uses publicly available software, which is typical of hacktivist groups. However, Head Mare’s toolkit also includes custom malware, PhantomDL and PhantomCore, delivered via phishing emails. In addition to its primary goal of causing damage to targeted organizations, Head Mare also deploys LockBit and Babuk ransomware, which demand a ransom for restoring encrypted data.
Loki: a new private agent for the popular Mythic framework
In July, we discovered a previously unknown backdoor called Loki, which was used in a series of targeted attacks against Russian companies in various industries, including engineering and healthcare. From our analysis and information gleaned from open sources, we determined that Loki is a private version of an agent for the open source Mythic framework. This has its origins in an open source framework for post-exploitation of compromised macOS systems, called Apfell. Two years later, several developers joined the project, the framework became cross-platform and was renamed Mythic. Mythic allows the use of agents in any language, for any platform, with the required functionality. Around two dozen agents have been published in the official Mythic repository, including Loki.
The Loki agent we discovered is a Mythic-compatible version of the agent for another framework, Havoc. The Loki modification inherited several techniques from Havoc to make it more difficult to analyze the agent, such as encrypting its memory image, indirectly calling system API functions, searching for API functions by hash and more. However, unlike the agent for Havoc, Loki was split into a loader and a DLL, where the main functionality of the malware is implemented.
Based on our telemetry, and the filenames of infected files, we believe that in several cases Loki was distributed via email, with unsuspecting victims launching the file themselves. More than a dozen companies have encountered this threat, although we believe the number of potential victims may be higher.
There is currently not enough data to attribute Loki to any known group. Rather than using standard email templates to distribute the agent, we think it’s likely that the attackers are approaching each target individually. We have also not found any unique tools on the infected machines that could help with attribution. The attackers seem to prefer using only publicly available traffic tunneling utilities such as gTunnel and ngrok, and the goReflect tool to modify them.
Tusk: unravelling a complex infostealer campaign
The Kaspersky Global Emergency Response Team (GERT) recently identified a complex campaign consisting of several sub-campaigns orchestrated by Russian-speaking cybercriminals. The sub-campaigns imitate legitimate projects, with slight modifications to names and branding, and using multiple social media accounts to enhance their credibility.
All the active sub-campaigns host the initial downloader on Dropbox. This downloader is responsible for delivering additional malware samples to the target’s machine, mostly infostealers (Danabot and StealC) and clippers (which monitor clipboard data). Additionally, the threat actors employ phishing tactics to entice individuals into revealing further sensitive information, such as credentials, which can then be sold on the dark web or used to gain unauthorized access to gaming accounts and cryptocurrency wallets, resulting in direct financial loss.
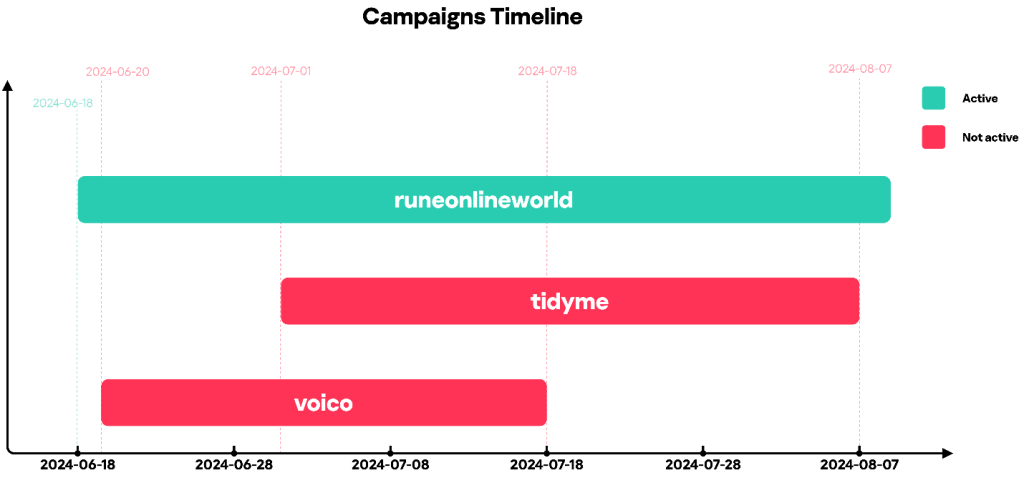
We identified three active sub-campaigns and 16 inactive sub-campaigns related to this activity, which we dubbed “Tusk”. In the three active sub-campaigns we analyzed, the threat actor uses the word “Mammoth” (a slang word used by Russian-speaking threat actors to refer to victims) in log messages of initial downloaders. Analysis of the inactive sub-campaigns suggests that they are either old campaigns or campaigns that haven’t started yet.
Our report includes our analysis of the three most recently active sub-campaigns – TidyMe, RuneOnlineWorld and Voico.
These campaigns underscore the persistent and evolving threat posed by cybercriminals who are adept at mimicking legitimate projects to deceive victims. By capitalizing on user trust in well-known platforms, these attackers effectively deploy a range of malware designed to steal sensitive information, compromise systems, and ultimately reap financial gain.
The use of social engineering techniques such as phishing, coupled with multi-stage malware delivery mechanisms, demonstrates the advanced capabilities of the threat actors involved. Their use of platforms like Dropbox to host initial downloaders, along with the deployment of infostealer and clipper malware, suggests a coordinated effort to evade detection and maximize the impact of their operations.
The similarities between different sub-campaigns and the shared infrastructure across them indicates a well-organized operation, potentially linked to a single actor or group with specific financial motives.
The discovery of 16 inactive sub-campaigns further illustrates the dynamic and adaptable nature of the threat actor’s operations.
You can read our report here.
SambaSpy
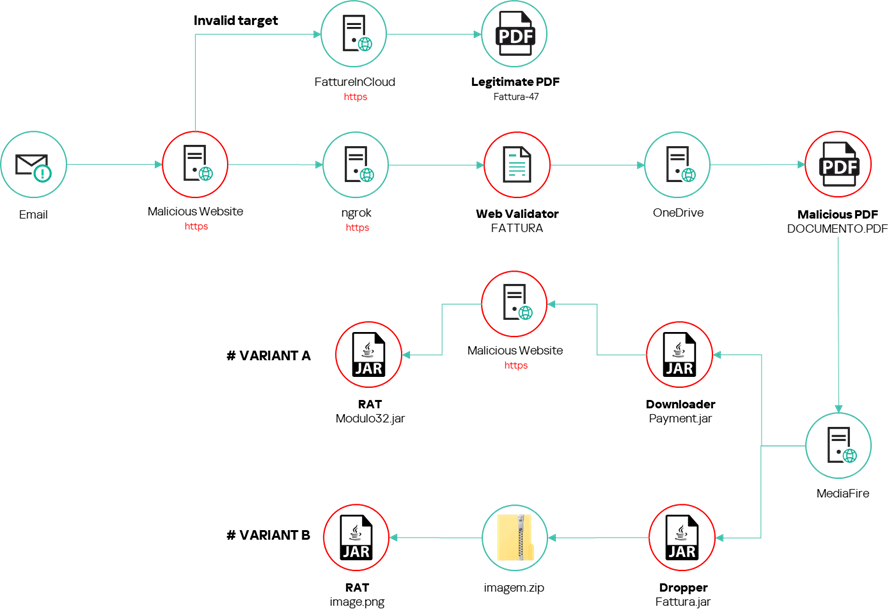
In May, we discovered a campaign exclusively targeting victims in Italy, which is quite unusual, as cybercriminals typically broaden their range of targets to maximize their profits. However, in this campaign, the attackers check at various stages of the infection chain to ensure that only people in Italy are infected.
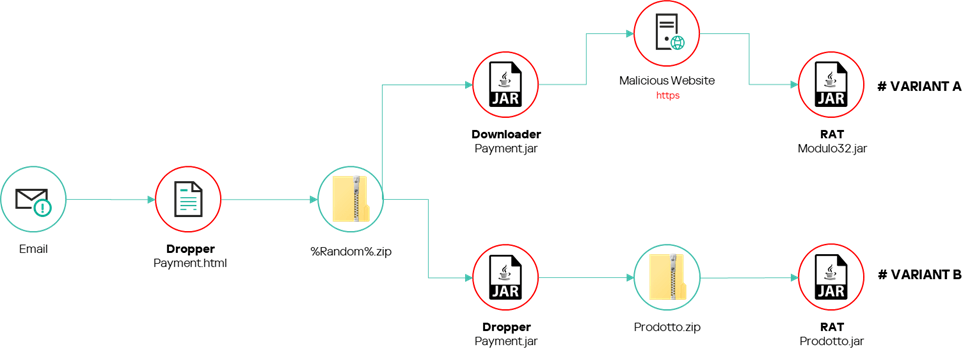
The final payload of the infection is a new RAT (Remote Access Trojan) called SambaSpy, a full-featured RAT developed in Java and obfuscated using the Zelix KlassMaster protector. The malware includes an extensive list of functions, including file system management, process management, keylogging, screen grabbing and webcam control.
The attackers lure their targets with phishing emails disguised as messages from a real estate agency. If the target clicks the link in the message, they are redirected to a malicious website that checks the system language and browser. If the potential victim’s system is set to Italian and they open the link in Edge, Firefox or Chrome, they receive a malicious PDF file that infects their device with either a dropper or a downloader. The difference between the two is minimal: the dropper installs the Trojan immediately, while the downloader first downloads the necessary components from the attackers’ servers. Those who don’t meet these criteria are redirected to the website of an Italian cloud-based solution for storing and managing digital invoices.
While we don’t yet know which cybercriminal group is behind this sophisticated attack, circumstantial evidence indicates that the attackers speak Brazilian Portuguese. We also know that they’re already expanding their operations to Spain and Brazil, as evidenced by malicious domains used by the same group in other detected campaigns.























IT threat evolution Q3 2024