
This latest report continues Kaspersky Lab’s sequence of quarterly reports on malware and cyber threat evolution.
The third quarter of 2005 brought some important events which will undoubtedly have a significant influence on the information security industry in the coming months. The end of the summer is traditionally a period of high virus activity, and it was no exception in 2005.
Critical vulnerability in Microsoft Windows Plug ‘n’ Play
Our recent analytical articles have repeatedly emphasised the fact that attack vectors are changing. Malicious users are starting to use viruses which propagate by exploiting vulnerabilities within web applications, particularly Internet Explorer, rather than network and email worms. One consequence of this is an increase in the number of compromised sites. Exploits for IE are placed on compromised sites, which means that users who visit these sites will have Trojans downloaded to their machines.
The most widespread such attack is the constant compromising of South Korean gaming sites. Trojan spies, which steal passwords to the on-line games Legend of Mir and LineAge, are usually placed on these sites. Russian hackers have been just as active as their foreign colleagues; the Trojan most often placed on compromised sites is LdPinch, which we’ve written about more than once.
We have noticed that such attacks tend to become more prevalent at times when there are no critical vulnerabilities in Windows. Given this, it’s unsurprising that there have been many similar attacks lately – After all, more than a year has passed since the security loophole in Windows LSASS was identified, and a significant number of potentially vulnerable computers have since been patched.
The ‘secure’ condition of Windows seemed unlikely to last long. And on the 9th August, Microsoft published a list of vulnerabilities for which it was issuing patches, including a patch for a vulnerability in the Plug’n’Play service (MS05-039), which was rated as critical. As usual, members of the computer underground reacted swiftly to news of the vulnerability, attempting to identify it, and to write code to exploit. The list of vulnerable operating systems included all current versions of MS Windows:
- Microsoft Windows 2000 (SP4);
- Microsoft Windows XP (SP1 or SP2);
- Microsoft Windows XP Professional x64 Edition;
- Microsoft Windows Server 2003;
- Microsoft Windows Server 2003 (for Itanium-based systems);
- Microsoft Windows Server 2003 x64 Edition.
This meant that potentially hundreds of millions of vulnerable computers around the world would be vulnerable to code which successfully exploited the PnP vulnerability.
The day after the vulnerability was publicized, the Russian hacker houseofdabus had already created proof of concept (PoC) code to exploit the vulnerability. However, it only functioned on computers running under Windows 2000. On 12th August the code was published on all major security sites, which resulted, as usual, in the appearance of malicious programs exploiting the vulnerability.
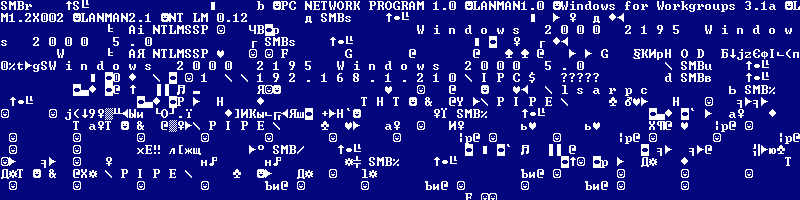
It’s worth highlighting that this was not the first time that houseofdabus acted as the catalyst for a virus epidemic. The Sasser worm, which caused a global epidemic in May 2004, and dozens of other similar worms utilized the PoC created by houseofdabus for the LSASS vulnerability. Incidentally, the Plug’n’Play and LSASS vulnerabilities are very similar to each other, as the screenshots below show.
On 13th August, new variants of Mytob (an old family of worms) were detected. In these new variants, the LSASS exploit had simply been replaced by the PnP exploit. Over the course of the next few days a range of worms and bots appeared which also included this code. News of some of these made it to the front pages, and caused one of the most widely reported security incidents of 2005. This was because the networks of some major American media companies – including ABC and CNN – had been infected by these worms. Information on this outbreak is widely available, so we won’t go into detail. It should be noted that this was not a global epidemic caused by a by a single worm, on the scale of the epidemics caused by Sasser and LoveSan.
The PnP vulnerability provoked a chain of small, localized epidemics caused by a variety of worms and bots. The reasons for this are fairly clear.Firstly, the fact that the exploit was not universal – it worked only on computers running Windows 2000 with SP4. Virus writers used ‘off the shelf’ code without bothering to research the vulnerability further. If the PoC provided by the Russian hacker had been created to affected XP and Windows 2003 then the epidemic would have been far greater. Secondly, the fact that the PnP and LSASS vulnerabilities are similar to each other also played a role. When the computer is attacked, these vulnerabilities behave in an identical manner, and display an identical error message. Users whose machines had previously been infected by code exploiting the LSASS vulnerability would know from bitter experience what should be done in such a situation and would be able to address the issue themselves, before it became serious. And finally, past epidemics have led to an increase in the technical know how of users. It’s now extremely difficult to find a person who doesn’t use an antivirus solution and/ or a firewall. Two years ago this was certainly not standard practice.
The facts above sum up the epidemic that never was. Individual users and major corporations demonstrated that they were prepared for the publication of new Windows vulnerabilities, and also ready to install patches in short order. Where infection did occur, it was swiftly dealt with. This gives us reason to believe that the truly global epidemics which followed in the wake of new Windows vulnerabilities, and which were able to take down whole segments of the Internet will not pose such a threat in the future.
An interesting related event was the arrest of two men suspected of being involved in the creation of the Mytob family of worms. As has already been stated, Mytob was the first worm to exploit the PnP vulnerability, and Mytob was the most conspicuous malware family in 2005.) On the 26th August, Farid Essebar (Diabl0) and Atilla Ekici (Coder) were simultaneously arrested in Morocco and Turkey. The former was suspected of creating the worm itself, and the latter was his accomplice, who allegedly distributed the worm and maintained the IRC channels which were used to control the victim machines. The case is still being investigated – however, it can be stated with confidence that the number of new Mytob variants fell sharply in September.
This case highlights the fact that virus writers who are tracked down, and whose viruses have caused security incidents within the networks of major companies, will be tracked by the police and eventually brought to justice.
Hardware antivirus solutions and a Cisco IOS vulnerability.
The PnP vulnerability described above confirmed security experts’ opinion that one of the most effective ways of preventing a global epidemic is an antivirus solution integrated into networking equipment.
If an antivirus solution is integrated with the router/switch, it is able to detect the body of a virus, or packets which are sent using an exploit, within network traffic. And once such a packet has been detected it can be diverted to prevent it from reaching the end user.
At the moment nearly all major manufacturers of networking equipment (Cisco, Juniper, SonicWall, Zyxel etc) work with antivirus companies and offer their clients such hardware antivirus solutions.
It’s clear that this type of protection is extremely effective, if expensive. As a result, a significant number of IT security researchers have focussed on potential threats to this type of solution. It is true that an attack on networking equipment could cause far more serious problems for the Internet than a single worm which only affects computers running Windows. If such an attack were to take place, all network users might be left without the Internet, regardless of what sort of operating system they were using.
The issue is further complicated by the fact that last year, some or all of the source code for the IOS operating system was leaked. On 13th May 2004, all source code for Cisco IOS versions 12.3 and 12.3t was leaked. An archive file 800MB in size was leaked as the result of the internal company network being compromised.
The Internetwork (IOS) operating system is used as a program platform for the majority of Cisco switches and routers. In addition to this, data suggests that Cisco has approximately 60% of the world router market.
Before long, the news broke: in summer 2005, the security world was shaken by the results of research conducted by Michael Linn from ISS, a well known information security company.
In April 2005 he detected a critical vulnerability in Cisco which made it possible to conduct a DoS attack on a device and execute random code in the system. This vulnerability theoretically places the entire infrastructure of the Internet under threat. This information was sent directly to Cisco, but the vulnerability was still not fixed more than three months after the information was provided.
ISS estimated the severity of the potential threat on the fact that the IOS source code was presumably already in the hands of the computer underground. It was therefore reasonable to assume that the underground would be aware of the vulnerability.
ISS itself had been the cause of a small virus outbreak, and this was still fresh in the security world’s memory. In March 2005, software released by this company was found to have an vulnerability, and in spite of the fact that it was fairly quickly patched, a number of ISS clients suffered from the Witty worm, which started to spread only two days after the vulnerability was detected.
Linn suggested that details of the vulnerability should publicized at BlackHat, a major security conference. In spite of the threat of legal action, and the possibility of being sacked, Linn’s paper “The Holy Grail: Cisco IOS Shellcode and Exploitation Techniques” was published. This meant that the information was now accessible to a wide range of interested parties, in spite of the fact that Cisco attempted to obscure the details of the vulnerability. Cisco is currently taking legal action against Linn.
Linn’s paper attracted attention, and his work in identifying the vulnerability in IOS has been continued by other researchers. From time to time information surfaces that independent experts have already created a PoC IOS worm, found out how to launch random code, etc. Although none of this information has been officially confirmed, but we believe it should be taken seriously. We believe that it would currently be possible to launch an attack on the Internet via a security loophole in networking equipment software.
One factor which seriously hinders the conducting of such an attack the relatively limited number of people who have the requisite knowledge and experience. Another factor is the absence of any clear commercial gain which such an attack would bring. Cyber criminals have no vested interest in bringing down discrete segments of the Internet. However, the likelihood is that a PoC IOS worm will appear like a bolt from the blue, just as happened in 1988 with the Morris worm, or in 2003 with Slammer.
We have absolutely no doubt that the near future will show a change of approach from malicious users. They will move away from searching for vulnerabilities in traditional operating systems – Windows/*nix and associated applications – towards networking equipment, firewalls, and antivirus solutions.
Social engineering
This is a topic which comes up on a regular basis in our reviews and analysis. We continually stress that the human factor is one of the foundations of any security policy. It is clear that major companies, specifically those in the financial sector, ought to address such issues as a matter of priority. In our last overview, we noted that malicious users were now changing their focus from conducting mass attacks to targeting specific business structures, and these attacks are tailored to each individual case. This makes it more difficult to counter such attacks using standardized protection measures.
However, rank and file Internet users should not let down their guard, and should learn how to recognise such attacks. A computers with a fully patched operating system which is not running any vulnerable applications can be infected just as successfully as an unpatched computer, and this one of the problems of contemporary information security. In this case, the easiest way to penetrate a system is to utilize social engineering techniques. This means attracting the attention of the user of the system under attack, and cause the user to complete some course of action, whether it is visiting a site and entering some information, downloading and launching a file, or opening a file which has arrived via email.
The imagination of social engineers knows no bounds. One of the most interesting recent approaches is phishing attacks in which the victims are not required to view specific sites or enter data on these sites. All that the attack consists of is a form which is sent to the user by fax. This method is relatively new, and users which have heard of fake sites and the danger of entering account or other details anywhere on the Internet may be extremely trusting if requested to send their personal data by fax. However, lack of trust in on line systems may lead to increased trust in traditional offline systems (such as telephone and fax) of data transmission. As the example above shows, social engineers are highly aware of Internet users’ psychology and well able to exploit current anxieties.
In connection with this it should be stressed that the attempts of some companies to create a browser which is capable of determining the veracity of any site visited, or a browser which protects information stored on the potential victim machine are unlikely to be 100% successful, as they will be unable to solve the problem entirely and will always be one step behind virus writers and cyber scammers.
The third quarter of 2005 was rich in catastrophe. Sad as it is, cyber criminals did not hesitate to use other’s grief (and to exploit human curiosity about disasters both natural and industrial) for their own ends. In August and September there was a large volume of spam and virus mass mailings which used various recent catastrophes as a subject heading. The biggest mass mailings were comparable in size to the activity shown in December and January of 2004/5, when cyber scammers exploited the tsunami in South East Asia.
The main topics used this quarter were the explosions in London (July) and Hurricanes Katrina and Rita (August – September).
It was only a few days after the bombings in the London underground that antivirus companies detected several malicious programs similar to each other. Email-Worm.Win32.Vote, Email-Worm.Win32.Chet (which seems to have been written in Russia) and SpamTool.Win32.Delf.h became the most widespread malicious programs spread by these mass mailings.
However, the virus writers and scammers really got into their stride at the end of August/ beginning of September, when one of the strongest hurricanes of the last decade hit the south coast of the USA. The day after Hurricane Katrina hit, Internet users were inundated by dozens of emails with subjects such as ‘watch the video’, ‘find out the real numbers of dead’ ‘an urgent message from the president’ etc. All these messages had a single aim: to attract the users to specially crafted sights which contained IE exploits. Exploit.HTML.Mht was used, as has come to be expected, but so were the relative newcomers Exploit.JS.JavaPrxy and IframeBof. However, in many cases the remote malicious users didn’t even bother to place exploits on the site, but simply invited the unwary users to download a file which was in actual fact a Trojan.
The cyber criminals didn’t limit themselves to installing Trojans on victim machines. Some of them also attempted to steal money more directly, by sending emails with the request to donate to the victims of the hurricane. These emails purported to be from aid agencies. The SANS Institute conducted some independent research and concluded that the number of domains using the word ‘Katrina’ rose sharply.
And this is where the imagination of the social engineers was shown in all their glory. Having ‘collected’ the donations, they also harvested the credit card details of the donors. In order to make it ‘easier’ for users to donate, the criminals created sites where the user was required to enter the numbers of their credit card. And of course, these numbers were forwarded to carders, who either used the accounts themselves, or sold them on.
These tried and tested methods were used again only a few days later when Hurricane Rita hit the USA. Thankfully, this time the devastation was on a much smaller scale, and perhaps as a consequence of this, the number of scams and amount of malicious code exploiting the situation was smaller.
These recent cases once again demonstrate both that social engineering remains a threat, and that the methods used are continuing to evolve. Company employees should be taught how to recognize such attacks, and home users should be particularly cautious and appropriately sceptical when receiving messages which ask for financial support. This is particularly appropriate in the wake of a catastrophe of any sort.
IM worms
Our first quarterly report noted that a new class of network worms – IM worms – had appeared and was evolving in explosive fashion. These worms propagate via a range of Instant Messaging applications. The report stressed that the evolution of this class of worms was very similar to the evolution of P2P worms. It also noted that a number of factors (the majority of the worms being written in Visual Basic, and based on one standard piece of code) indicated that IM worms were at an initial stage in their evolution. IM worms were at the peak of their development in spring and summer 2005, and showed the highest growth rate among all classes of network worms. In the first six months of this year, we detected an average of 28 new IM worms every month. It should be stressed here that when P2P worms were at the peak of their evolution in 2003, approximately 10 new variants were detected every week.
However, suddenly the situation changed. The flood of IM worms suddenly dried up, and at the time of writing, we are detecting approximately one new IM worm version a week, and these new versions are only slightly modified versions of already well known families. What has happened to IM malware?
AOL and MSN, both of which have proprietary IM clients, were the main targets for such worms. Both companies took measures to protect their users: firstly, by blocking the transmission of files with names and extensions which were known to be used by IM worms. In spite of the fact that IM worms rarely use file transmission as a propagation method, the move did have a noticeable effect. The next step was to block the worms’ main method of propagation: hyperlinks leading to files containing the body of the worm.
These actions closed the majority of security loopholes being exploited by virus writers. And most importantly, they closed the loopholes which IM worms based on source code circulating in the computer underground used. Most of the code used in IM worms is of fairly low quality. We came to the conclusion that the majority of these worms are created by script kiddies who have no significant programming skills. When the off the shelf code was no longer effective, these self styled virus writers were unable to create new propagation methods on their own, and this led to a sharp drop in the number of new worms.
However, we believe that another equally important factor is the PnP vulnerability mentioned at the beginning of this report. Why did IM worm evolution and activity take off so dramatically at the beginning of the year? Because there were no new critical vulnerabilities in Windows, and this meant that virus writers had to find other popular methods of data transmission to distribute their creations. Email didn’t meet their requirement for a number of objective reasons which we have already described in other places. P2P networks and IRC channels are currently becoming less and less popular. The relatively small number of users means that such networks and channels are of less interest to virus writers. The only real choice remaining was Instant Messaging, and it seems likely that this caused the increase in malicious code targeting this platform.
However, the PnP vulnerability acted as a catalyst which caused virus writers to sharply shift their focus. There are several popular IM clients, and it seemed to be beyond the virus writers’ skill to develop a universal worm which would affect all of them. Additionally, AOL and MSN developers took steps to secure these clients. The result of all this was that the PnP vulnerability provided virus writers with far greater opportunities and a far larger number of potentially vulnerable machines than IM.
All the evidence above confirms that the PnP vulnerability was the most notable security event of 2005. It significantly altered the virology landscape and will influence the evolution of malicious programs for several months to come.
As for IM worms, their evolution currently mirrors the evolution of P2P worms, which showed a sharp increase in numbers, followed by an equally sharp fall. And these reasons for these rises and falls are also extremely similar; P2P worms became far less popular following the announcement of the RPC DCOM and LSASS vulnerabilities. It is likely that IM worms will not cause any significant outbreaks in the next few months and will not represent any serious threat. However, it is probable that over the course of time, if no new critical vulnerabilities are detected in Windows, then virus writers will return to using IM as a launching pad for their creations.
Mobile malware
Recently Kaspersky Lab published an analysis of malware for mobile devices, with forecasts as to how this type of malicious code might evolve. One of the main conclusions was that the status quo (with virus writers shifting their attention from creating older threats towards writing effective mobile malware) is likely to be maintained for at least another 6 months. This means that we will continue to see a steady stream of viruses which are simply modifications of older malicious programs. However, there is likely to be a very occasional technological innovation.
Since the report was published, our predictions have been proved correct. Several new Trojans for Symbian have appeared which do have some new features.
At the end of September Cardtrap (Trojan.SymbOS.Cardtrap) was detected. This has all the functions to be expected in a Symbian Trojan: when installing itself to the system it overwrites some firmware files with empty or corrupted copies of these files. However, it differs from existing Trojans in that in addition to overwriting files, it also installs two malicious programs for Win32 on the memory card. The first of these is a variant of the multi-functional backdoor Padobot, and the second a known variant of the Rays email worm. (Incidentally, this is the second time that mobile devices have been infected by Rays – at the end of August, approximately 4,000 Zen Neeon MP3 players in Japan were found to be infected with Rays. We still don’t know exactly how these players became infected, and the manufacturer has not published the results of the investigation which it conducted into the matter.)
Padobot and Rays, even when installed on the memory card, do not pose any direct threat to the mobile device. These malicious programs can only run in a Windows environment. It seems that the Padobot’s author is banking on the fact that an infected phone will be connected to a computer, and it will then be possible to launch these files for execution, infecting the computer. To achieve this, the authors make Padobot install itself to the memory card as an autorun file. However, as far as we know autorun files on a memory card will not be function in Windows, so this effectively eliminates any risk. Rays is installed on the card as a file named system.exe, with an icon normally used for directories, not files. This means it would be possible for the worm to be launched if the user mistook the icon for a directory and attempted to open it.
We have not seen this type of behaviour – attempting to infect two operating systems simultaneously – in mobile malware before. It is in some ways reminiscent of Lasco; however, in this case, the Windows component searched the computer for .sis format files and attempted to infect them with its Symbian component.
This example shows that virus writers still see Windows as their main target, and view infecting a telephone with a Trojan is simply a step in penetrating the desktop machine.
The second noteworthy Symbian Trojan was Cardblock, which was detected at the end of September. This Trojan represents a significant threat due to its extremely destructive payload.
Once installed, it deletes system directories and information about applications installed on the victim device. The result of this is that the address book stored in the phone memory will be deleted, as well as SMS and MMS messages which have been saved. Many handset models are then unable to boot, and require a hard-reset.
The innovation here is the way in which the Trojan attacks the MMC (multi-media card). The Trojan blocks this by using a randomly generated password, and as long as the card remains in the infected handset, the device will function properly. However, as soon as the device is restarted, or the card placed in another handset, the card will be blocked. Without the password, the data stored on the card cannot be accessed, and as the password is randomly generated, the user is naturally unable to guess it.
This case is not simply a matter of data stored on the device being deleted or corrupted. This is the first step towards a Trojan for mobile devices which acts in a similar way to the Windows Gpcode Trojan mentioned in our previous quarterly report; the Trojan encrypts user data and demands payment for decryption. This is a very worrying sign, and if it becomes a firm trend this will mean that cyber criminals will have found a way to make money by infecting mobile devices.
While this report was being written we received information that the first Trojan for gaming consoles had been discovered. Sony PlayStationPortable was the first victim – the Trojan targeting this device deleted system files causing the console to cease functioning correctly. This behaviour is very similar to Trojans for mobile phones. A few days later, a Trojan targeting Nintendo DS was detected. It may be that these new Trojans for gaming consoles signal the start of a new interest among virus writers. We’ll return to this topic in our final quarterly report of 2005.
Conclusion
The third quarter of 2005 was extremely varied in terms of incidents and cyber-threats. The last three months not only brought information about new critical Windows vulnerabilities (none of which have been fully exploited yet) but also about the potential threat posed by the widely used Cisco routers. Mobile devices are now threatened by new, more complex Trojans, and spammers and phishers actively exploited a series of natural disasters.
On the other hand, there were no full-scale epidemics. The media hullaballoo surrounding one version of Mytob was not due to the worm’s propagation potention. Rather, it was because the media itself had been affected by this worm, as some companies had not updated or patched their systems promptly.
Our next report will analyse the events of the fourth quarter, and also summarize the events of the year as a whole.




















Malware Evolution: July – September 2005