
Last night, we received a new version of the #Madi malware, which we previously covered in our blog.
Following the shutdown of the Madi command and control domains last week, we thought the operation is now dead. Looks like we were wrong.
The new version appears to have been compiled on July 25th as it can be seen from its header:
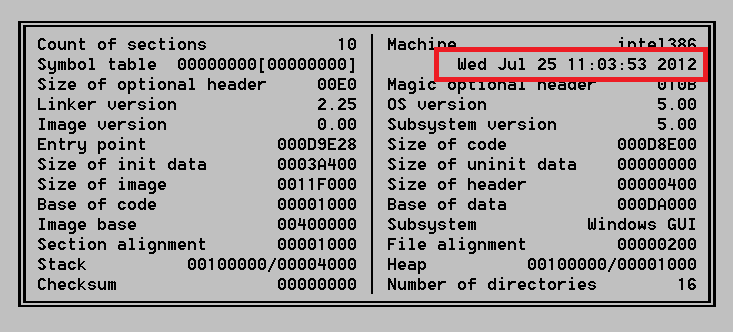
It contains many interesting improvements and new features. It now has the ability to monitor VKontakte, together with Jabber conversations. It is also looking for people who visit pages containing USA and gov in their titles. In such cases, the malware makes screenshots and uploads them to the C2.
Here’s a full list of monitored keywords:
“gmail”, “hotmail”, “yahoo! mail” , “google+”, “msn messenger”, “blogger”, “massenger”, “profile”, “icq” , “paltalk”, “yahoo! messenger for the web”,”skype”, “facebook” ,”imo”, “meebo”, “state” , “usa” , “u.s”,”contact” ,”chat” ,”gov”, “aol”,”hush”,”live”,”oovoo”,”aim”,”msn”,”talk”,”steam”,”vkontakte”,”hyves”, “myspace”,”jabber”,”share”,”outlook”,”lotus”,”career”
Compared to previous variants, there are a number of changes. For instance, when run, the new version creates a MUTEX named miMutexCopy Mohammad Etedali “www.irandelphi.ir. It drops a file named datikal.dll which contains the current date. It checks if poki65.pik is present in folder, which is the keylogger file. They keylogger code is identical to previous variants, but the Hook function is a bit different – code was merged from different subroutines into one single procedure.
Perhaps the most important change is the infostealer no longer waits for commands from the C2 – instead, it simply uploads all stolen data to the server right away.
The new command and control server is located in Canada, Montreal. Previous Madi C2s have also been located in Canada, as well as Tehran.
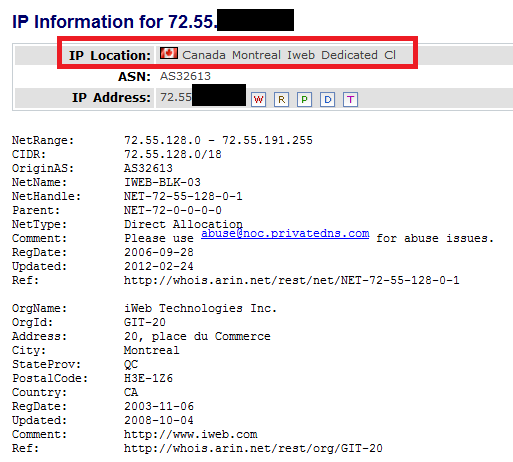
At the time of writing, the new Command and Control server appears operational, however, it doesnt have all the scripts from previously used servers. Nevertheless, the page used to exfiltrate data (with help of “sik.php”) does work fine:
|
1 2 3 4 5 6 7 8 |
./madi-check http://72.55.X.X/Sendfilejj.html HTTP/1.1 200 OK Content-Length: 1361 Content-Type: text/html Last-Modified: Wed, 27 Jul 2011 01:11:21 GMT Server: Microsoft-IIS/7.5 X-Powered-By: ASP.NET Date: Wed, 25 Jul 2012 09:53:47 GMT |
To summarize, todays findings indicate that the Madi campaign is still ongoing and its perpetrators are busy shipping out new versions with improved features and new tricks. The additional checks for USA and gov might indicate a shift of focus from targets in Israel to the USA.
Update:
The Mutex mentioned above: *miMutexCopy Mohammad Etedali “www.irandelphi.ir”* is created in order to know whether the file is already running or not. If the Mutex is already present, the process terminates.
On the first execution, Madi checks if a file named “datikal.dll” is present, and creates one if not.It is filled by the current date: year/month/day
Once written, it jumps to the Mutex check routine, and therefore process terminates as the file is already running.
Upon next executions, it compares the current date with the one from “datikal.dll”. If the difference is lower than 2 days, the infostealer terminates.
Madi stays silent for 2 days before it starts its activities.
Out of the 52 Timers present in the earlier versions, only 12 are left.
Most of the code has been copy pasted from older version of Madi
Changes:
- Madi doesnt connect to C&C to get orders anymore.
- The Monitoring feature (PIK command in the previous version) is enabled by default and the list of keywords is much bigger.
- The keylogger log file are ready to be uploaded as soon as they are 7KB 15 KB in previous versions.
We will continue our analysis and post additional findings soon.





















Madi is back – New Tricks and a New Command&Control Server