
In our search for various types of malicious code for Mac we recently came across a rather interesting peculiarity in Safari. It turns out that Safari for Mac OS, like many other contemporary browsers, can restore the previous browsing session. In other words, all the sites that were open in the previous session – even those that required authorization – can be restored in a few simple steps when the browser is launched. Convenient? Of course. Safe? No, unfortunately.
So that the browser knows what was open at the end of the previous session, the relevant information needs to be stored somewhere. Obviously, that needs to be somewhere that isn’t easily accessible to just anybody, and the information definitely needs to be encrypted.
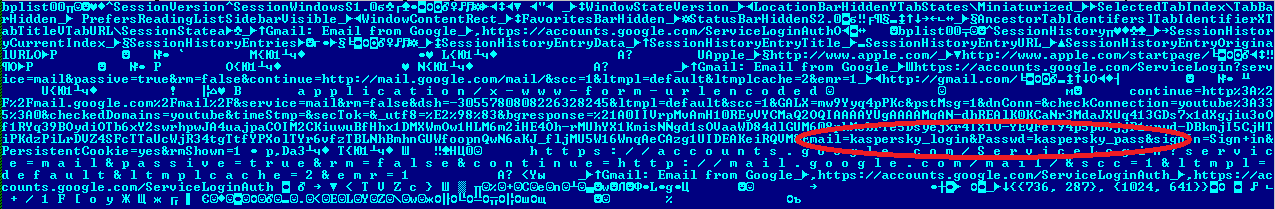
Safari, however, doesn’t encrypt previous sessions and stores them in a standard plist file that is freely accessible. As a result, it’s easy to find a user’s login credentials:
Screenshot of a plist file following an attempt to log in to Gmail
It’s pretty clear that the login and password are not encrypted (see the red oval in the screenshot).
The complete authorized session on the site is saved in the plist file in full view despite the use of https. The file itself is located in a hidden folder, but is available for anyone to read.
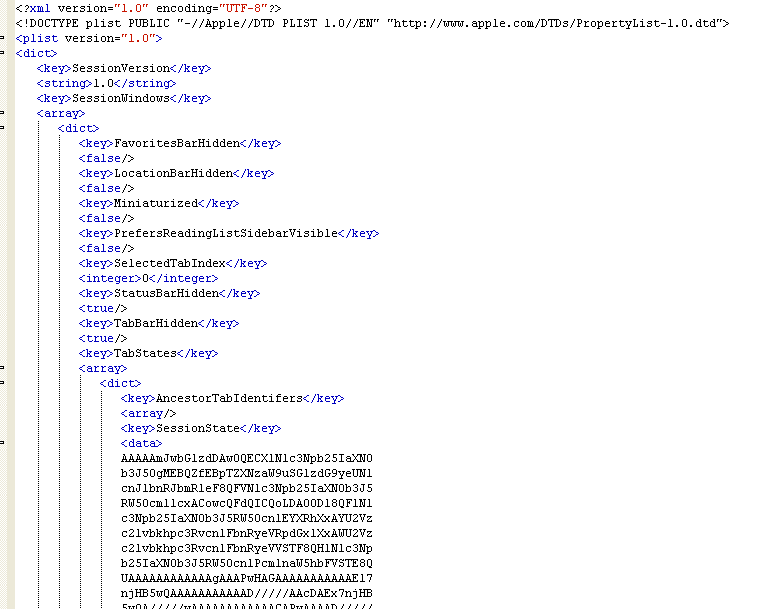
The system can easily open a plist file. It stores information about the saved session – including http requests encrypted using a simple Base64 encoding algorithm – in a structured format.
An open plist file
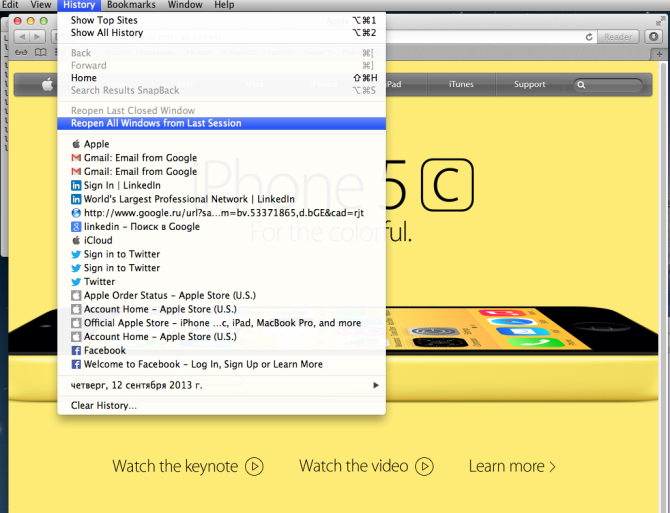
There is a function in Safari – ‘Reopen All Windows from Last Session’ – that allows sites to be opened exactly as they were at the end of the previous session. This is the function that uses LastSession.plist.
The ‘Reopen All Windows from Last Session’ function in Safari
The function is available in the following versions of Mac OS X and Safari:
OSX10.8.5, Safari 6.0.5 (8536.30.1)
OSX10.7.5, Safari 6.0.5 (7536.30.1)
You can just imagine what would happen if cybercriminals or a malicious program got access to the LastSession.plist file on a system where the user logs in to Facebook, Twitter, LinkedIn or their online bank account.
As far as we are concerned, storing unencrypted confidential information with unrestricted access is a major security flaw that gives malicious users the opportunity to steal user data with a minimum of effort.
We have informed Apple about the problem.
At the current time we can’t confirm whether or not there is malicious code out there that targets this file, but we’re ready to bet that it won’t be long before it appears.
This vulnerability has been fixed in Safari 6.1





















Loophole in Safari