
It has been four months since Microsoft and Kaspersky Lab announced the disruption of Kelihos/Hlux botnet. The sinkholing method that was used has its advantages — it is possible to disable a botnet rather quickly without taking control over the infrastructure.However,as this particular case showed, it is not very effective if the botnet’s masters are still at large.
Not long after we disrupted Kehilos/Hlux, we came across new samples that seemed to be very similar to the initial version. After some investigation, we gathered all the differences between the two versions. This is a summary of our findings:
Let’s start with the lowest layer, the encryption and packing of Kelihos/Hlux messages in the communication protocol. For some reason, in the new version, the order of operations was changed. Here are the steps of processing an encrypted data for retrieving a job message which is organized as a tree structure:
| № | Old Hlux | New Hlux |
| 1 | Blowfish with key1 | Blowfish with new key1 |
| 2 | 3DES with key2 | Decompression with Zlib |
| 3 | Blowfish with key3 | 3DES with new key2 |
| 4 | Decompression with Zlib | Blowfish with new key3 |
To encrypt a message, all the operations need to be in reverse order. It is well known that text strings are more effectively compressed than raw binary data. The initial tree includes many strings such as e-mails, spam templates, etc. Therefore using zlib compression after encrypting a tree in the new Hlux/Kelhihos version makes no sense: the packet size increases without any advantages. It seems that someone obtained the botnet source code and just wanted to make future bots look different by shuffling the order of encryption stages.
Secondly, the encryption keys were changed, which is quite predictable. Also the RSA keys which are used for signing the parts of a tree with the controllers’ IPs and update URLs and the corresponding public RSA keys within the bots were also changed.
| Old Hlux | New Hlux | |
| Controllers’ IP | RSA key1 | New RSA key1 |
| Update/Exec urls1 | RSA key1 | New RSA key1 |
| Update/Exec urls2 | RSA key2 | New RSA key2 |
As you can see, two different RSA keys are used within a tree which makes us think that probably two different groups are in possession of each key and are currently controlling the botnet.
As for the tree structure, all the fields and their meanings remained the same.The most significant change is that the hashing algorithm for the fields’ names is no longer used. Instead, each field now corresponds to 1-2 character name.
This was a tree structure of the old Hlux after decrypting a packet:
This is a tree structure of the new Hlux:
One more innovation in the new Hlux version is a more accurate approach of forming the packets: now every packet (both incoming and outgoing) includes the calculated data checksum in its header.
Our investigation revealed that the new version appeared as early as September 28, right after Microsoft and Kaspersky Lab announced the neutralization of the original Hlux/Kelihos botnet.
The controllers list in the new version remained almost the same and slightly changed over time.
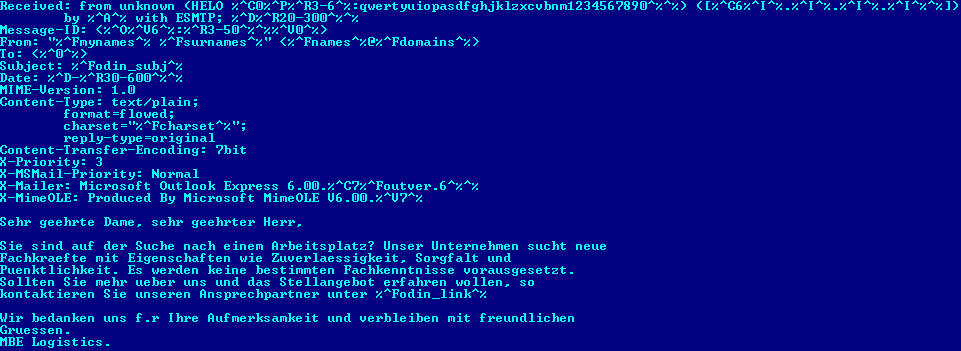
This botnet continues to get orders from spammers and send spam in different languages so far:
The main conclusions are the following:
- It is impossible to neutralize a botnet by taking control over the controller machines or substituting the controller list without any additional actions. The botnet master might know the list of active router IPs, can connect to them directly and push the bot update again along with the new controllers list.
- It is still possible to neutralize the botnet with sinkhoking but using slightly different techniques as was used before.
- It is still possible to push an update tool on infected machines to neutralize the botnet. In this case the botmasters need to infect machines again to build another botnet.
- We believe that the most effective method to disable a botnet is finding the people who are behind it. Let’s hope that Microsoft will carry out its investigation to the end.
P.S. Thanks to Alexey Borzenkov and Tillman Werner for providing technical details.
Kelihos/Hlux botnet returns with new techniques























Enkidu
have u found any new solution to detect and/or stop p2p botnets ?