
Contents
- The year in figures
- Trends in 2012
- Sources of spam: musical chairs
- Malicious attachments in email
- Phishing
- Conclusion
The year in figures
- The average amount of spam in email stood at 72.1%.
- The percentage of phishing emails in all email traffic came to 0.02%.
- 3.4% of all emails contained malicious attachments.
Trends in 2012
Lower spam volumes
The amount of spam fell throughout the course of the entire year. At the close of 2012, the percentage of spam settled at 72.1%, or 8.2% less than in 2011.
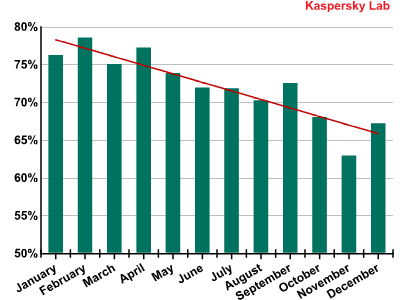
Percentage of spam in mail traffic
This continual and considerable decrease in spam volumes is unprecedented. Moreover, the average percentage of spam in 2012 was substantially lower than in 2010 (82.2%) and 2011 (80.3%), when botnet command centers and pharmaceutical affiliate programs were actively shut down. In 2012, the percentage of unsolicited mail was as low as it’s been over the previous five years.
The main reason behind the decrease in spam volume is the overall heightened level of anti-spam protection.
To begin with, spam filters are now in place on just about every email system, even free ones, and the spam detection level typically bottoms out at 98%.
Next, many email providers have introduced mandatory DKIM signature policies (digital signatures that verify the domain from which emails are sent).
DKIM first entered the scene back in 2006, but it was rather slow to make a name for itself. It has only been in the last couple of years that email providers have started to see DKIM as an important criterion for determining whether or not an email should be delivered to its intended recipient. In response, malicious users started to generate fake DKIM signatures. This was possible since many companies used an algorithm to encrypt their signatures that by 2012 was relatively easy to hack.
However, in 2012 Wired magazine published an article describing the problems associated with un-encrypted DKIM signatures. After this article came out, many major companies such as Google, Yahoo, and Microsoft changed their signature encryption methods, opting to replace 512-bit keys with more modern 1024- or 2048-bit keys. This change made fakes impossible (at least based on current computing capabilities).
As a result of the actions taken to reinforce anti-spam protection, the amount of spam emails reaching user inboxes was cut to a minimum. This makes spam very ineffective, prompting spam clients to start migrating to other platforms. This in turn has led to a decline in the volume of spam in email traffic.
Legal Internet ads as an alternative to spam
When anti-spam experts answer questions about what needs to be done in order to reduce the amount of spam, in addition to anti-spam legislation, quality filters and user education, one factor that is always mentioned is inexpensive advertising on legal platforms. With the emergence of Web 2.0, advertising opportunities on the Internet have skyrocketed: banners, context-based advertising, and ads on social networks and blogs.
Ads in legal advertising venues are not as irritating for users on the receiving end, they aren’t blocked by spam filters, and emails are sent to target audiences who have acknowledged a potential interest in the goods or services being promoted. Furthermore, when advertisers are after at least one user click, legal advertising can be considerably less costly than advertising through spam.
Based on the results from several third-party studies, we have calculated that at an average price of $150 per 1 million spam emails sent, the final CPC (cost per click, the cost of one user using the link in the message) is a minimum of $.4.45. Yet the same indicator for Facebook is just $0.10.
That means that, according to our estimates, legal advertising is more effective than spam. Our conclusion has been indirectly confirmed by the fact that the classic spam categories (such as fake luxury goods, for example) are now switching over to social networks. We have even found some IP addresses for online stores advertising on Facebook that were previously using spam.
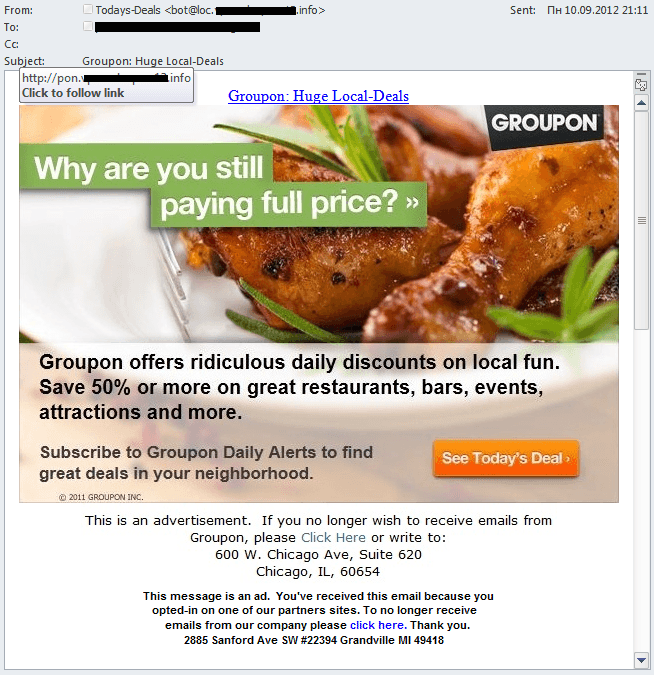
Advertisers have also been drawn to yet another means of legal Internet promotion: coupon services, or group discount websites where users can purchase so-called coupons. These services appeared several years ago. After a user buys a coupon, he/she presents it when purchasing a product or service and receives a discount. In 2012, coupon services gained a lot of popularity. Many companies around the world are striving to grow their client base, and in turn, clients receive generous offers.
And coupon services have caught the attention of advertisers that previously used spam services. For example, over 10% of the offers on coupon services fall into the “travel and tourism” category — a category that has more or less disappeared in spam. The popularity of coupon services has made the migration of advertisers from spam to other platforms more noticeable.
At the same time, the prevalence of coupon services has had an impact on spam. Malicious users have started to copy emails from major coupon services, using the originals to advertise their own goods or services, or to lure users to a malicious website.
This migration to legal platforms could potentially be advantageous for promoting legal goods and services. This is particularly relevant for Russia and other Eastern European countries where spam traffic still features quite a lot of small and mid-sized businesses. However, in light of the fact that most spam in these countries advertises counterfeit goods, fraudulent services, and malicious emails, the amount of spam will continue to remain high.
Malicious emails and fraud in spam
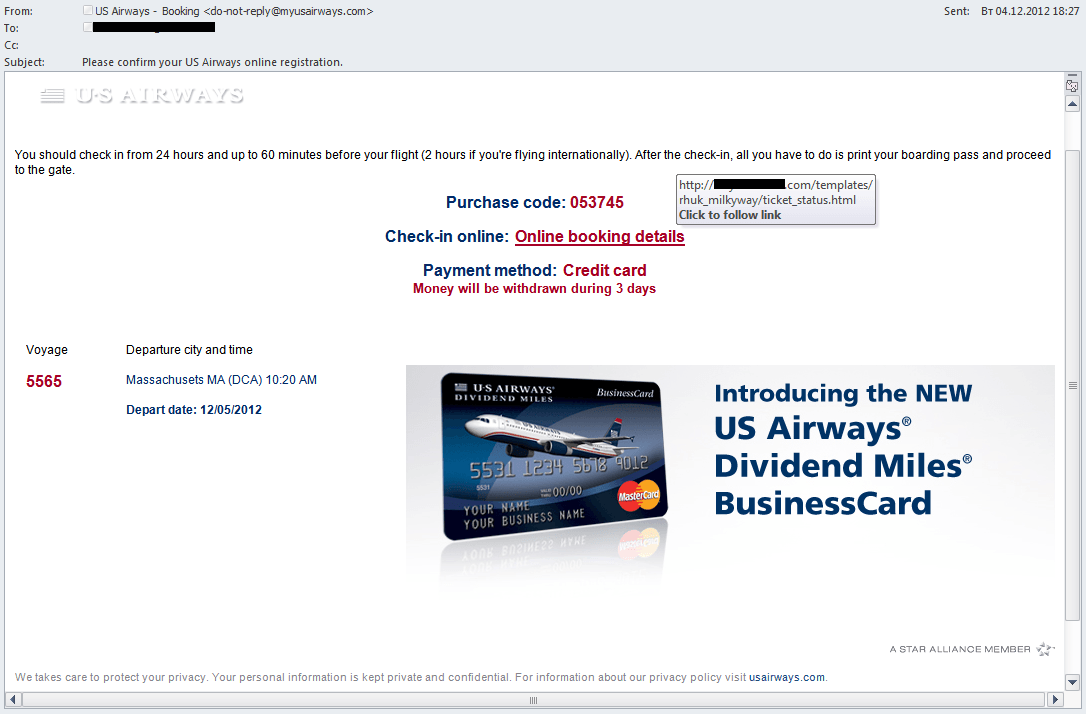
In 2012, the range of different subjects used in malicious emails was impressive. Previously malicious users relied on fake notifications from hosting services, social networks, delivery services, and messages from financial and government organizations. In 2012, they expanded their repertoire. We saw the emergence of fake messages from a variety of airlines, hotel reservation services, and the coupon services mentioned above.
These types of fake emails may contain malicious attachments in a packed archive file, or malicious links.
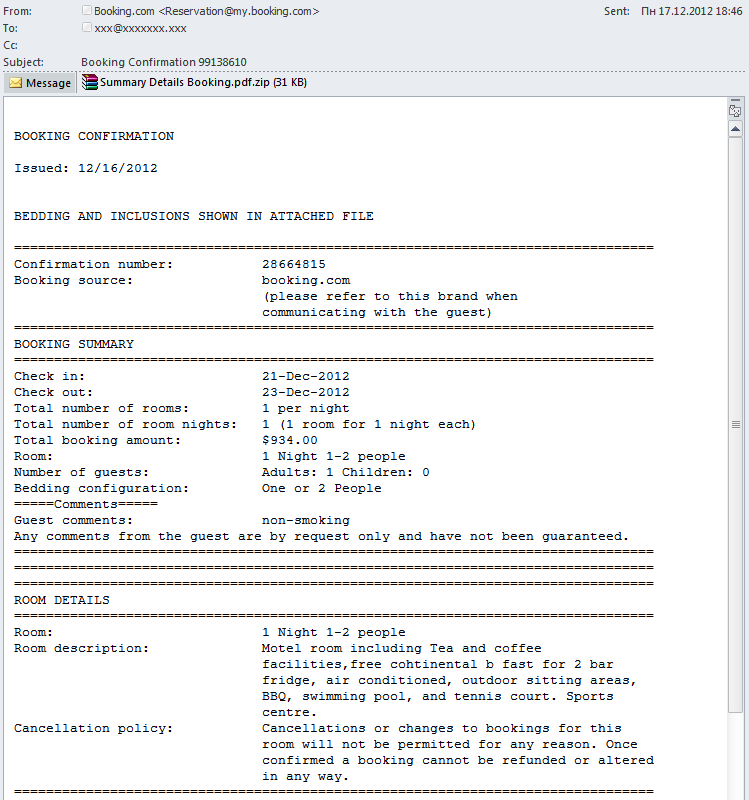
The orchestration of attacks that use links is the same. An unsuspecting user will click on a link that will lead him/her to a hacked site with seeded script, which in turn will redirect the user to a malicious website with exploits. Most often, redirects lead to the Blackhole exploit kit, but other exploit packs have also been used.
In addition to the process described above, malicious users have occasionally used official ways of publishing content on some legitimate websites. Kaspersky Lab experts detected notices seeded with links to Wikipedia and Amazon. The cybercriminals took advantage of the ability to make their own pages on these resources to post malicious content. However, malicious content is promptly removed from these sites, even before the spam mailings and their respective links reach their destination. This seems to have ensured that this method is not popular among malicious users.
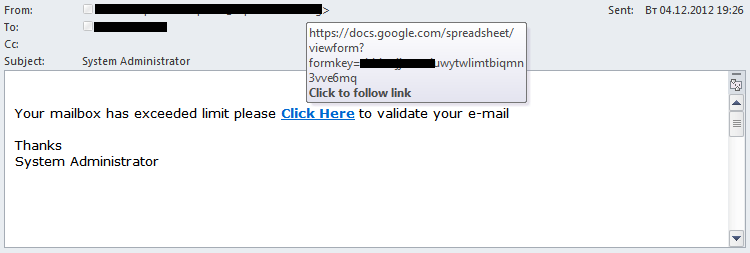
Links to other legitimate resources were also found in spam. For instance, scammers are still using Google spreadsheets to steal confidential user data (primarily usernames and passwords for email accounts).
Among the more common social engineering methods employed by malicious users, Kaspersky Lab experts continued to see fake personal correspondence. They are often done so well that it’s not always immediately evident that they are in fact spam. When running antivirus scans of attached archive files, modifications of various malicious programs were detected.
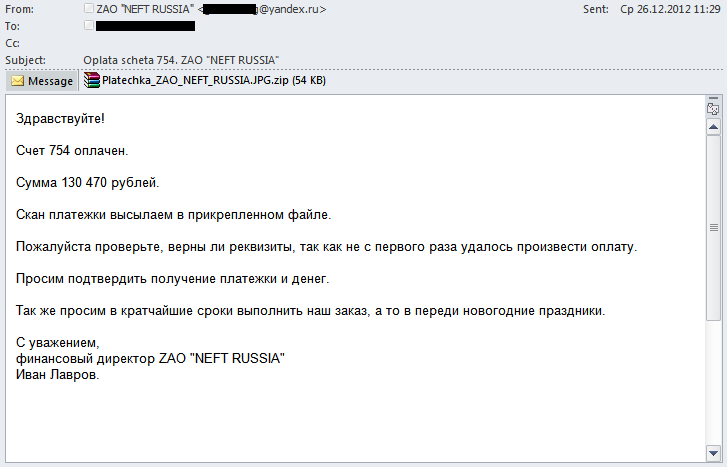
Translation from Russian:
Hello!
Bill No. 754 has been paid.
Amount: 130 470 rubles.
A scan of the payment receipt is attached.
Please check to make sure the records are correct, since the payment did not go through the first time.
Please confirm receipt of the payment and the funds.
We also request that you fill our order as quickly as possible, in light of the upcoming New Year’s holidays.
Sincerely,
Ivan Lavrov
CFO, ZAO NEFT RUSSIA
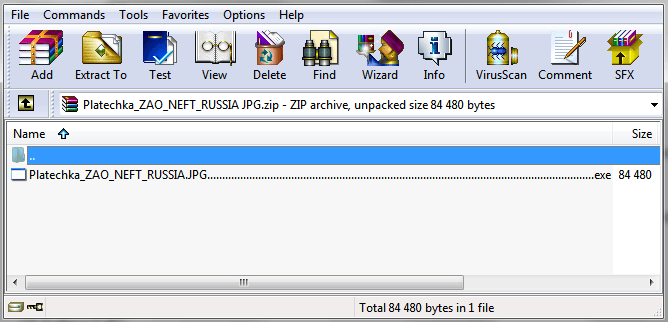
Malicious users typically try to hide the fact that files in the ZIP file are executable (.exe) by disguising them as office applications.
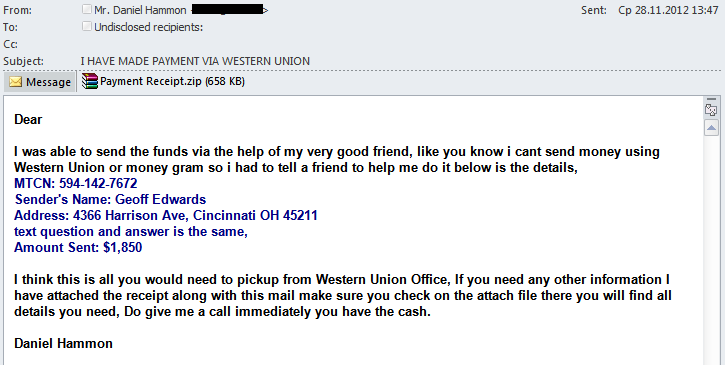
We have also seen emails designed to look like correspondence in the hope that greed will drive the recipient to open the file in the ZIP attachment: the user will accidentally receive a letter with Western Union information with which he/she can allegedly receive a certain amount of money.
However, instead of data from Western Union, the attached archive file contains a Zbot family Trojan.
Sources of spam: musical chairs
2012 saw some major changes among the countries from which spam originates.
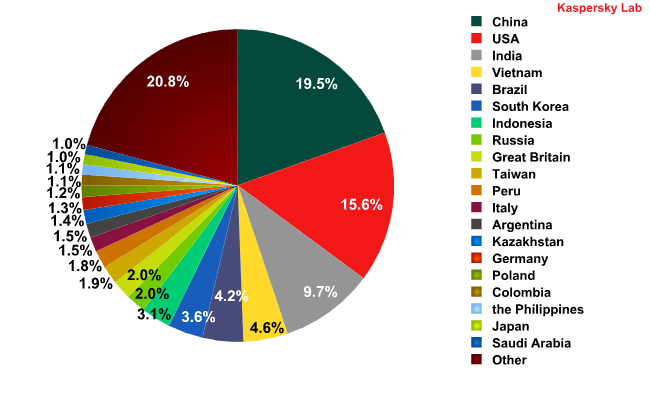
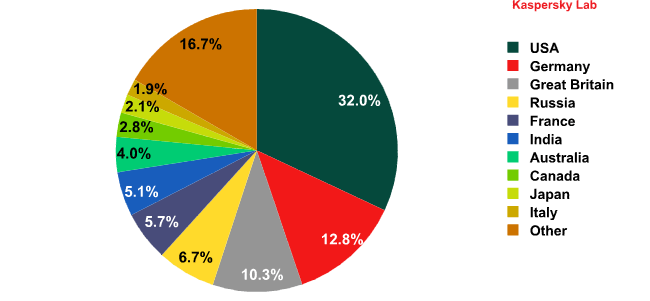
China, which was not even in the Top 20 sources of spam in 2011, took first place in 2012, accounting for 19.5% of all spam. Spam originating in the US increased 13.5 percentage points, to 15.6% – enough to take second place.
Both of these countries had previously been among the world’s leading sources of spam, but fell from the top of this rating in recent years. The amount of spam sent from China fell in 2007 after the country introduced anti-spam laws. Spam originating in the US was nearly wiped out after several botnet command centers were shut down in 2010. However, these countries have the highest numbers of Internet users, far more than most other countries. The US and China combined represent over 30% of all Internet users worldwide. Naturally, with such large numbers of potential victims, cybercriminals who set up botnets can’t help but be interested in expanding their networks of infected machines.
Sources of spam by country
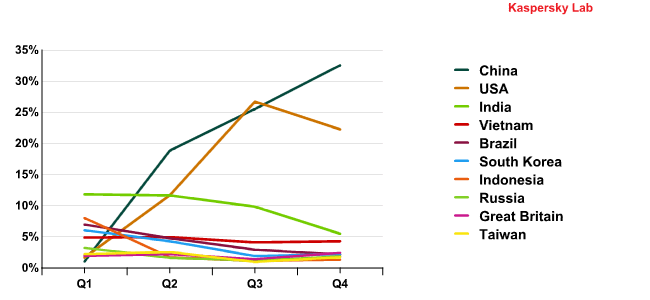
Changes in the sources of spam rankings were noted throughout the year. They were especially evident in the Asian region, where China took first place while the previous leaders in that region such as India, Indonesia, and South Korea lost ground.
Changes in the Top 10 sources of spam by country
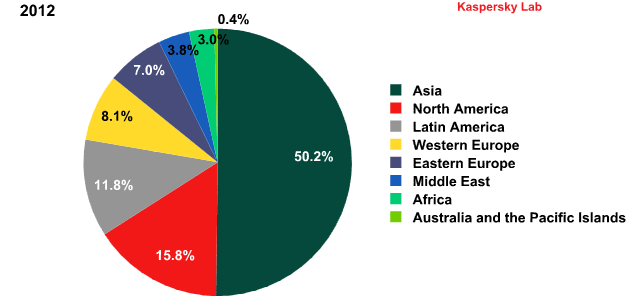
Asia remains the leading region for spam distribution. Over the year, the region’s share of the world’s junk mail rose 11.2 percentage points to clear 50%.
Sources of spam by region, 2012
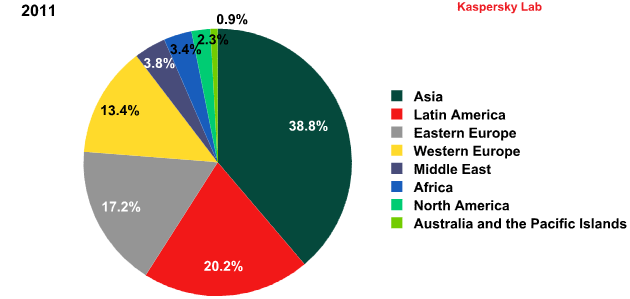
Sources of spam by region, 2011
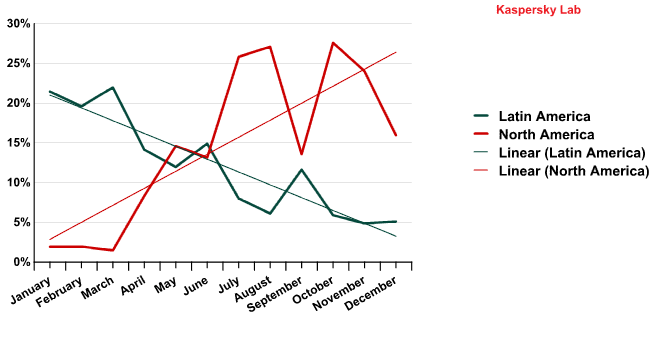
Due to the increased spam contribution from the US, North America took second place in the Top 10 with 15.8% — up from just 2% in 2011. Meanwhile, the amount of spam originating in Latin America fell by 8 percentage points and closed at 11.8%.
The amount of spam originating in North and Latin America, January – December 2012
Europe also dropped down the ranks. In 2012, the total amount of spam originating in Western and Eastern Europe combined came to 15.1%, which is about half the amount recorded in 2011 (30%).
Malicious attachments in email
In spite of the drop in the overall percentage of spam in mail traffic, the proportion of emails with malicious attachments fell only slightly to 3.4%. This is a very large percentage, considering that this number reflects only emails with malicious attachments and ignores other spam emails containing links to malicious websites.
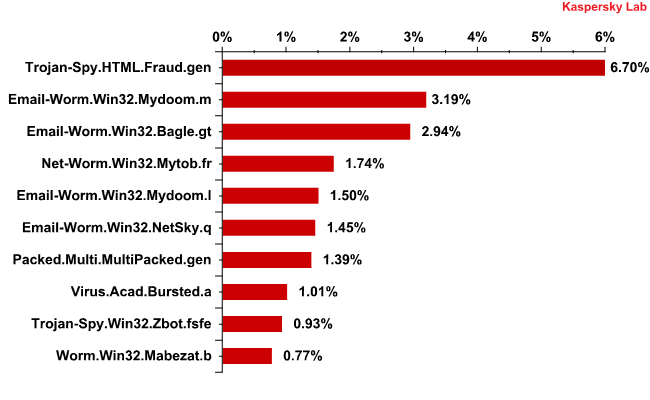
The most common malicious attachment in 2012 was Trojan-Spy.HTML.Fraud.gen, which was firmly in the lead and ahead of the other two malicious programs in the Top 3 in this category for the first nine months of the year. In the fourth quarter, the most prevalent malicious attachments were Trojan-Spy.Win32.Zbot.fsfe and Trojan-PSW.Win32.Tepfer.cfwf. These three malicious programs were designed to steal user account information (usernames and passwords) – Fraud.gen and Zbot (ZeuS) exclusively target passwords from financial and payment systems, while Tepfer steals other passwords as well.
The Top 10 malicious programs in email in 2012
Email worms were in second and third places in the rankings. This large number of worms is a result of the way worms function: once they are on a computer, they begin to actively send themselves to the addresses in user address books. These types of worms are especially prevalent in Asian countries, where people often use bootleg software and do not update their antivirus databases. The Bagle worm, in addition to its main functions, also has the ability to install a variety of programs on an infected machine.
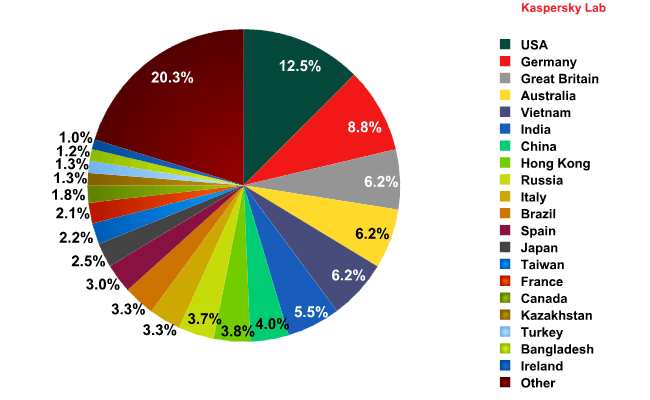
Email antivirus detections by country
The largest number of email antivirus detections in 2012 was recorded in the US. Germany led for several months over the year, but ended up in second place at the close of the year. Third place went to the UK. Russia, which was the number one target in 2011, fell to 9th place in 2012.
Remarkably, the percentage of emails with malicious attachments targeting users in the US has increased at the same rate at which the percentage of spam originating in the US increased. The amount of malicious emails targeting China also rose. This malware was most likely, among other things, downloading spam bots onto users’ computers. As a result, the infected computers became part of the botnet system and also started sending out spam.
Phishing
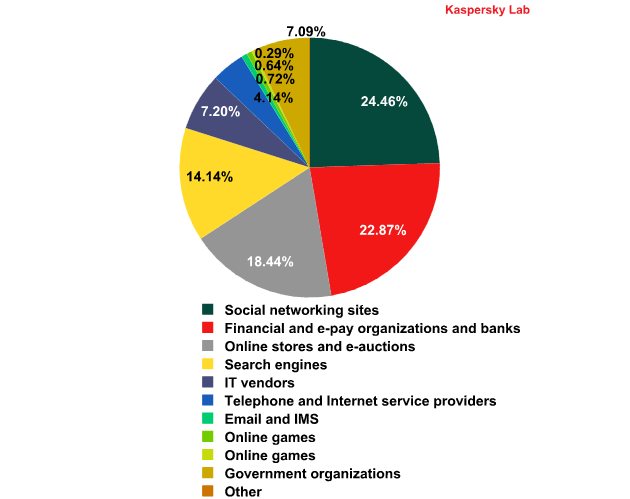
Top 100 organizations targeted by phishers, by category
This rating is based on Kaspersky Lab’s anti-phishing component detections, which are activated every time a user attempts to click on a phishing link, regardless of whether the link is in a spam email or on a web page.
The phisher’s top targets in 2012 were various social networks (24.5%). Most attacks were launched on Facebook. The stolen accounts were used by malicious users primarily to send spam and malware to the people on the victims’ friend lists.
The number of phishing attacks against financial organizations was down on 2011, but remained high at 22.9%. The third most common phishing target was online stores and auctions (18.4%), where phishers hope to get their hands on account information such as credit card numbers.
The fourth most frequent phishing target in 2012 was search engines (14.1%). Since many search engines such as Google are major websites, they also feature many different types of user services. These accounts also draw the attention of scammers.
Phishing site hosts by country
Aside from Russia and India, which took fourth and sixth places, respectively, the Top 10 countries targeted by phishers were all countries with developed economies.
Nearly all of the countries on the list have well-developed online banking systems and a large number of social network users — the top two phishing targets. Phishing site hosts are not necessarily in the same country as the users who are being targeted. There is, however, one small nuance — phishers typically try to give their fake websites names that are as close as possible to those of actual online resources (for example, by changing one letter in the real website’s name) so that users do not notice that they are on a fake website. The domains are set up in the same way as the real site’s domain, to make it look as much like the real thing as possible. This is perhaps why we get this sort of domain zone distribution.
It’s interesting that the three countries where the most phishing websites were found (the US, Germany, and the UK) are also the top three countries on the receiving end of emails with malicious attachments.
Conclusion
In 2012, the percentage of spam decreased over the course of the year, and during the final three months of 2012, the percentage of spam remained below 70%. This drop is one result of the gradual departure of advertisers from spam to other, more convenient and legal means of promoting goods and services. However, that doesn’t mean spam is headed the way of the dodo anytime soon: malicious spam, fraud, and advertising of illegal goods cannot simply or easily migrate to legal platforms, due to their own inherently criminal nature. We expect that the decline in spam volumes in 2013 will be negligible at best.
In 2012, the percentage of spam originating in the US and China grew substantially. These two countries have both previously been leading sources of spam, but after anti-spam laws were passed and botnets were shut down, junk mail coming from these countries decreased markedly. Clearly, spammers still want to take advantage of the powerful computing resources available in the US and China to set up new botnets in those countries.
The most common malicious programs in 2012 are programs that steal usernames and logins, focusing primarily on account information for financial services. However, malicious users are also interested in other types of passwords, such as those for social network, email accounts, and other services.
The volume of malicious emails remained high throughout the year. Malicious users are copying an even broader range of legitimate notifications. In this situation, Kaspersky Lab reminds Internet users to keep safe: when you receive an email, make sure that it was actually sent from the resource that it claims to be. Never click on links in suspicious emails, and remember, it is critically important to update your software regularly.



















Kaspersky Security Bulletin: Spam Evolution 2012