
Year-end overview
- The percentage of spam on the Russian Internet ranged between 70 – 80%. The lowest figure (44.1%) was recorded on 4th January 2006, while the yearly high (91%) was recorded on 26th November 2006.
- Most spam sent to Russian Internet users originated in Russia, the US and China.
- 2006 was distinguished by the use of graphical technologies in spam.
- Spammers continue to disguise spam messages as personal correspondence in order to lure the reader into carefully reading the whole message and then taking the action desired by the spammer (calling a designated phone number, clicking on a link, etc.).
- Spam in different languages differs in other ways:
- Russian-language spam contains offers for educational services and different kinds of goods, ranging from busts of Putin to dog bark interpreting devices;
- English-language spam includes advertisements for stocks, Viagra and cheap software.
- Legal and auditing services have appeared as a new category in Russian-language spam.
- The share of criminalized spam is on the rise. Spammers on the Russian Internet are exploiting text messaging services.
Kaspersky Lab receives and analyzes between 300,000 – 600,000 spam messages per day, and sometimes as many as up to 1,000,000. The spam comes from a range of sources, including dedicated spam traps, and it is also submitted by partners and commercial users. This means that spam analysts see a full cross section of varying types of spam. All incoming spam traffic is automatically classified. Some incoming spam is also analyzed manually. Kaspersky Lab’s one-of-a-kind spam classification system helps track spam volume and the different categories of spam
Spam: 70% – 80% of all mail traffic
Last year, spammers demonstrated that they have no intention of making any concessions. Although Russian legislation does not provide a precise definition of “spam,”. Kaspersky Lab spam analysts define ‘spam’ as “mass unsolicited anonymous mail sent via electronic communications, primarily email.” Working from this definition, Kaspersky Lab data shows that spam represents at least 70% of all email traffic (save for several days during the New Year holidays and a handful of sporadic, one-day slumps in spam activity).
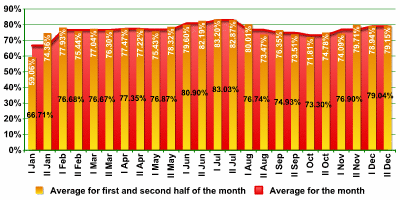
These are, of course, average figures. The volume of spam on free email services – a favorite target of spammers – is often higher, while individual corporate email servers will often see a lower percentage. Nevertheless, spam never comprises less than 50% of all email traffic. This high figure applied both to Russian and Western segments of the Internet.
The lowest volume of spam in 2006 was recorded at 44.1% on 4th January 2006, and the yearly high was on 26th November 2006 at 91%. Overall, the graph illustrating spam volume in 2006 shows a smoother dynamic than those from 2003 – 2005, with far fewer sharp rises and falls over brief 1-2 day periods. The only decline noticeable on the chart took place during the New Year holidays.
2006 Spam Statistics:
2006 Spam Statistics:
- January saw a decline in the share of spam to an annual record low of 44% of all email traffic (4th -5th January);
- A sharp rise then peaked at 86.4% between 14th – 17th February;
- The volume of spam then fluctuated sharply, ranging between 63.8% to 81.2%;
- Spam volume began to stabilize within 70 – 80% from March through mid-November;
- A slight increase was noted in late July;
- During this period, the volume of spam also fluctuated upwards a number of times due to particularly large spam mailings;
- The percentage of spam stayed close to the 80% threshold from mid-November through the end of the year, with the annual high of 91% recorded on 26th November.
Size of spam mails
The size of spam mails varies, just like that of legitimate correspondence:
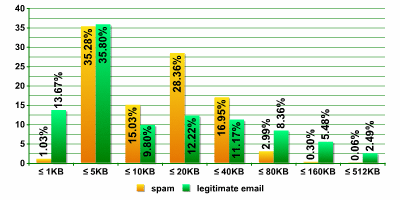
Approximately 35% of both spam and legitimate emails range from 1 – 5 KB in size. A second clearly delineated category is the 28.4% of spam which varies in size from 10 – 20 KB. This phenomenon was not mirrored in legitimate correspondence. The large number of spam mails ranging from 10 – 20 KB is partly due to graphical spam (see below for more information on this).
The vast majority of spam mails (95.6%) vary from 5KB to 40 KB in size. Spam contains fewer small messages than legitimate email. A small message is less than 1 KB in size (1% of spam, 13.7% of legitimate email), while a large message may be over 80 KB (3.4% of spam, 16.3% of legitimate email).
Where does spam come from?
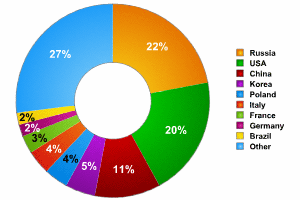
Spam aimed at the Russian Internet originates primarily in three countries: Russia (22%), the US (20%) and China (11%). Both the US and China are among the world’s leading sources of spam.
Spammer Technologies in 2006
Most technologies for generating and sending spam did not undergo many changes in 2006:
:
- Spammers primarily use botnets made up of zombie machines in order to send out mass mailings. Botnets are infected personal computers controlled by malicious users. The infected computers are overwhelmingly those belonging to home users.
- The tricks that spammers use to get around antispam software still consist of automatic text generation based on a predefined template; using HTML to hide text designed to get the message through spam filters from the user; attaching files containing advertising text in graphical form to the spam mail.
The pie chart below shows a breakdown of zombie machines by country:
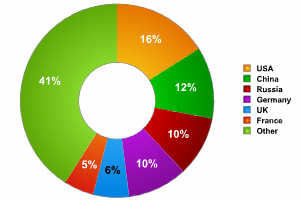 >
>Russia comes third in terms of the number of zombie machines delivering spam to Russian Internet users, being overtaken by the US and China. This might be due to the fact that in Russia, only the residents of big cities have broadband Internet access. Spammers have little to gain from using home computers which do not have high-speed Internet connections as spamming platforms.
2006: The year of graphical spam
While there were not any major developments in spammer technology in 2006, there were a few innovations: spammers have made a lot of improvements in mass mailing graphical attachments. The idea of putting spam into an image, as opposed to text, isn’t a new one. The technology of modified graphical spam was first tested in 2003 – 2004. It was not, however, very popular at the time due to the resources needed to generate different images within one mass mailing. At the time, spammers chose to continue working with HTML instead.
In 2005, spammers’ main goal was to evade spam filters by increasing the speed of mass mailings. However in 2006, most antispam solutions were capable of reacting to spam faster than before. For this reason, spammers who had not previously needed to increase the speed of their mailings were forced to resurrect old tricks and develop them further in order to make each individual message different.
In 2006 spammers again turned to using graphics, this time to such an extent that 2006 could be dubbed “the year of graphical spam”.
Two technologies were implemented with particular success:
- perfecting the modification of graphical attachments within one mass mailing (i.e., the parameters of the image changed from email to email);
- the innovation of animated spam in 2006.
In addition to perfecting the format of mass mailings, in 2006 spammers worked on reducing the amount of time needed to complete their mailings. The newest spammer technologies can send out hundreds of thousands of messages in under an hour. Spammers have also mastered psycholinguistic methods of manipulating spam readers. In other words, spammers are still using text, and are successfully disguising spam as personal correspondence.
Graphical attachments: experiments with color and text
Since the beginning of the year, spammers have made several attempts to improve their graphical spam technologies. This included images of letters for individual text letters, using rare font styles (such as Gothic) in images containing text, and slightly skewing the text in an image. Spammers have essentially returned to the techniques they first mastered in 2003. It seems that these recent efforts were just as unsuccessful as they had been previously, which is why we have not seen such technologies implemented on a wide scale.
By the end of 2006, spammers had more or less perfected methods used to generate polymorphic images with a range of changing backgrounds, a range of texts etc. The main aim of these experiments is to ensure that spam filters (a) will not be able to recognize that other messages in the mass mailing contain identical advertisements and (b) will not be able to identify key words and phrases typical of spam (making it difficult to apply OCR technology). With this goal in mind, graphical attachments containing one and the same advertisement are modified by using different background colors, different fonts and different font sizes and even by breaking up the text in different ways. In their attempts to generate images which can evade spam filters, by the end of the year spammers had gone so far that the text became difficult for recipients to read, once again making graphical spam a dead end.
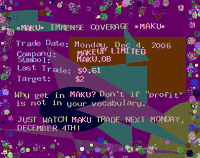
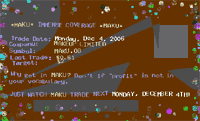
Below are some examples of different emails which contain identical advertising. They clearly illustrate the application of new spammer technologies:
Filtering such spam is complex due to the message structure and design, which made it extremely difficult to detect such messages:
- The message headers are faked to look like the headers generated by one of the most popular versions of MS Outlook.
- The image appears to have been embedded in the text by using the same popular version of MS Outlook. The email appears to be no different from an email created in Outlook where the user inserted the image into the email using the mouse.
- In addition to images containing advertising, the emails also a range of texts which were automatically downloaded from popular sites.
Antispam software developers and major email providers quickly took action and developed techniques to combat this type of spam. There are certain signs which distinguish the images from those typically found in legitimate email: a large amount of text in the image, the use of a small number of colors, an unusual selection of colors, etc. Images used within one mailing were grouped together, making it possible to intercept spam on the basis of a small number of samples.
Innovations in the fight against graphical spam in 2006 were essentially the evolution of technologies which appeared after 2003.
Graphical attachments: animation
In August 2006 spammers introduced animated spam. The first animated mass mailings were detected by Kaspersky Lab spam analysts in late August 2006. A peak in activity was seen in September – October. From late November to the end of the year, animated spam experienced a sharp decrease.
Spammers used animated GIF files, since the GIF format is recognized and automatically displayed by all popular browsers. Animated attachments contain between three to several dozen frames. The most important part of the animation can consist of one or more frames which contain the actual information. All of the other frames are designed to provide background noise – they have no meaningful content and contain elements like background designs, geometric shapes, etc.
The frames with meaningful content are shown to the user from just a few seconds up to 10 minutes. The background elements are shown for under a second and the human eye does not work fast enough to register them. The image is then rotated. Three frames from an animated GIF are shown below:
By October spammers had perfected the technology: the advertising text was split between frames, with each frame displaying 1-2 lines of the advertisement. The frames were then layered over each other, with the end result being a complete text. . The initial and final frames of the animation were those containing ‘noise’.
Most probably, animated spam is used to evade OCR technologies which can be used to filter out spam.
Animated spam did give antispam developers some pause for thought, but from a technical point of view the problem was not overly complex. Additionally, graphical spam does not present a serious threat to email – at least not email that is protected by spam filters.
Spam and Psychology
Sending messages quickly and getting them past all filters to the recipient is an important part of the spamming process, but there’s more to it than that. Spammers also need to ensure that a user will read the message and do what the spammer wants (i.e., call a designated number, click on a link, etc.).
In 2006 spammers continued to master the psychological methods used to manipulate spam recipients. In particular, in order to hook a user into reading an email, spammers tried to persuade recipients that messages were actually personal correspondence, not spam. At the beginning of the year, spammers mainly used primitive approaches, such as adding RE or FW at the beginning of a subject line to indicate that a message was a reply to a previous email or that it had been sent from a known address. By the middle of the year, spammers had begun to use more subtle tactics.
Spammers began working on their message texts. Today, some spam message texts are stylistically and lexically designed to look like personal correspondence. There are some convincing examples that might even fool an expert at first glance, not to mention less experienced users. This kind of spam is often highly impersonal (it doesn’t address anyone in particular or uses words like “girlfriend” or “sweety”, etc.) in order to create the illusion that the email was intended only for the recipient. Sometimes names are used in faked personal correspondence. Whatever the case, the user’s curiosity will be piqued and s/he may well read it to find out who it came from, if s/he should forward it, etc.
Spam by category: 2006
Categories put different spam messages that could be associated with different kinds of businesses into one group. For example, the “education” category unites spam messages with ads for seminars and training courses, foreign language lessons, and special offers on textbooks, etc. The most common categories of spam are shown in the pie chart below:
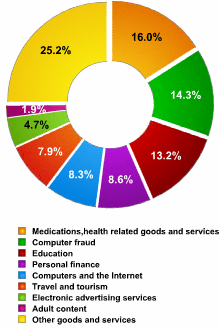
| № | Category | Main subgroups | Percentage |
| 1 | Medications and health-related products and services | Viagra, Cialis and other pills | 16,0 |
| 2 | Computer fraud | Phishing, 419 emails, fake notification of lottery winnings etc. | 14,3 |
| 3 | Education | Seminars and training courses | 13,2 |
| 4 | Personal finance | Stocks at unbelievably low prices | 8,6 |
| 5 | Computers and the Internet | Cheap software and printer cartridges | 8,3 |
Top spam categories in 2006
Nearly all of the leading categories are English-language spam, with the exception of the “education” category, which is predominantly made up of Russian-language messages.
Kaspersky Lab analysts believe that English-language spam is not targeted at Russian Internet users. The fact that English-language messages show up in Russian users’ inboxes can be explained by the large scale of spam attacks. Spam mailings are not targeted; instead, they achieve their goal by the sheer number of messages sent. The victims of one spam attack number in the millions: the typical advertisement for spamming services, which are naturally also circulated in email, claim that a company’s advertisement will reach 3 – 5 million email addresses.
The largest category shown in the pie chart is “other goods and services”. In general, this category consists of advertisements for goods offered by small manufacturers and vendors: car seat heaters, malachite ashtrays, busts of Putin and portraits of the Russian president made of tiny bits of amber, everlasting flashlights, pens with disappearing ink, appliances for braiding hair and devices that will interpret a dog’s bark into 5 different languages. This kind of spam demonstrates the peculiarities of goods offered on the Russian Internet in 2006.
For a long time, this category was too varied and wide-ranging to identify any substantial subgroups, but by the end of 2006, some subgroups specific to the Russian Internet had clearly emerged. These included offers for legal, real estate and polygraph services. During the last three months of 2006, the volume of such offers grew significantly and settled in the ranges shown below (percentage of all spam):
| Category | October | November | December | 3-month average |
| Legal counsel and audit services | 8.0% | 2.1% | 2.1% | 4.0% |
| Real estate | 5.0% | 2.5% | 2.3% | 3.3% |
| Printing and graphics | 2.0% | 2.0% | 2.3% | 2.1% |
Top categories in Russian language spam:
- Education
- Travel and tourism
- Electronic advertising services
- Legal counsel and audit services (a subgroup of the “other goods and services” category)
- Real estate (a subgroup of the “other goods and service” category).
Continued criminalization of spam
Spam has been increasingly used for criminal purposes since the birth of the spam industry. Criminal mass mailings are made possible by anonymity and a lack of any effective legislative control.
Signs of continued criminalization of spam in 2006:
- increase in the proportion of spam categorized as “computer fraud”, a category which includes phishing, 419 emails, false notification of lottery winnings and other similar messages aimed at obtaining money or personal data via fraudulent means;
- the appearance of new types of fraudulent spam;
- the tendency for other spam categories to show signs of criminalization (currently seen in the “personal finance” category);
- using methods to distribute spam that violate the law of various countries (botnets, for example);
- the continued use of spam to spread malicious programs;
- using spam to steal personal data (phishing);
- the demonstrated ability of spammers to unite against the common threat posed by antispam developers – for example, there were a number of successful attacks on the antispam service Blue Frog, which was forced to close as a result.
Some of these aspects will be discussed in more detail below.
Financial spam
The volume of spam in the category ‘personal finance’ (which includes insurance, debt reduction, loans at low rates, and investment opportunities) increased sharply in August 2006 and this increase continued to the end of the year. The chart below shows the movement in this category throughout 2006:
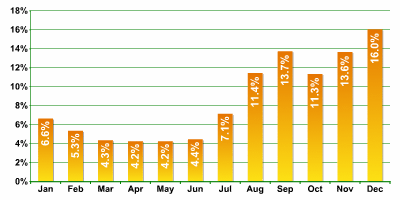
Most of the spam in the “personal finance” category consisted of messages urging readers to invest in the stock market (Stock Spam). Growth in this subgroup spurred an upsurge in the “personal finance” category as a whole. In September (the start of the “stock” boom), the share of stock spam amounted to 66% of the “personal finance” category and roughly 9% of all spam.
Spammers urged email users to buy shares in little known companies. Despite the fact that analysts initially classified these emails as belong to the “personal finance” category, such spam is clearly gravitating towards the criminal. These exhortations contain false information and are designed to stimulate artificial growth in stock value:
One widespread type of fraud seen on the Russian Internet in 2006 was the exploitation of mythical vulnerabilities in e-payment systems such as WebMoney, Yandex-money, etc. Spammers claim that these “vulnerabilities” can help a user increase the amount of money on his account. All the user allegedly needs to do is to deposit money in an account (the account number is indicated in the spam), and sit back and wait for the profits to roll in. It is not known where this urban legend stems from, but tales of “magic” WebMoney accounts spread like wildfire, helping spammers make significant profits.
Only very inexperienced users will fall for this type of scam, but the number of users on the Russian Internet is constantly on the rise, and many of these new users are young and gullible.
In 2006 spammers on the Russian Internet invented new types of fraud which exploited phenomena specific to Russia.
By autumn, “magic e-payment accounts” had been replaced by “magic text messages”. The basic fraud scheme was the same: a spammer would send out various offers persuading the user to transfer money from his account to the spammer’s account. Only in this case, the spammer does not rely on online payment systems, but dedicated text message services that are intended for conducting money transfers from a mobile phone account to any other kind of account.
In order to make a money transfer using a text message service, the user must enter a certain message and send it to a specific number. In order to persuade the user to do this, a spammer needs to present a convincing argument. For example, there is spam which informs the recipient that s/he has won a prize in a lottery. To claim the prize, instructs the spam, all the recipient has to do is send an sms to a designated number. However, funds will then be transferred from his/ her account, even though this is not what s/he intended.
Beyond technology
This report is primarily concerned with discussing the technical aspects of spam mailings and their contents. But spam isn’t purely a technical issue. While this report cannot provide a detailed explanation of all of the many facets of spam – particularly legal and social aspects – there were some events in 2006 that are so significant that they must be mentioned.
Russian legislation against spam: taking the first step
On 1 July 2006, the new amendments to the Russian federal law on advertising came into force. The revisions include a section (Article 18) governing advertising that is “distributed via electronic communications networks”. That means that spam is now partially covered under Russian law for the first time.
This applies only to some kinds of spam, since the law on advertising is designed to regulate advertising and advertising services. Not all spam is advertising (i.e., not all of it can be clearly identified as “advertising” as defined in the text of the law). The many varieties of spam include so-called “political spam”, test emails for validating spammers’ address databases, fraud and other kinds of unsolicited email.
Spammers reacted to the changes in the law quickly and more actively than other Internet users. May 2006 saw the beginning of spam mailings on the Russian Internet advertising spammer services. The argument was that potential clients ought to order spam mailings as soon as possible in light of the upcoming legislative changes: “Order your mass mailing before the new law on advertising comes into force. Work within the confines of the law”, spammers wrote, making reference to the new amendments. The amount of emails advertising spam services grew steadily until early July and, it would seem, this wave of propaganda played a fairly significant role in the increased number of spam orders in June and July.
But from the end of July, the percentage of spam in all email traffic began to slide. It’s possible that spam clients chose to wait and see what happened after the amendments came into force. Or perhaps they had simply run out of funds for advertising for that period. It’s hard to say for sure in this case, but the fact remains that by the end of summer 2006, the volume of spam had fallen. This decrease was most obvious in the sector advertising specific goods.
One could surmise that spammers were worried by the situation and began actively searching for new clients. This process is clearly illustrated in the chart below, which shows the dynamic in the “electronic advertising services” category during the summer months:
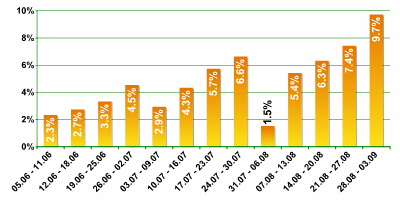
This time spammers have also appealed to the new law, but in a different sense. Spammers have virtually described their plans, including how mass mailings will be conducted, demonstrating that there are no legal violations. The foundation of this work plan is a formal contract for rendering information services (i.e. not advertising) which does not fall under the terms of the law on advertising.
The lower volume of spam in relation to all email traffic was maintained in September 2006, but by the end of November, it had climbed back up to 80% and higher.
One gets the impression that for the time being, the revised law is not an effective tool for combating spam. It’s not clear who should provide computer users with timely information about mass mailings or how that information should be provided in order to ensure documented evidence for subsequent submission to judicial authorities. For now, the technical solutions offered via antispam software and filters are more user-friendly for computer users than resorting to legal proceedings.
Spammers are uniting and… winning?
In May 2006 the Blue Frog project was closed. The project was an antispam solution based on the idea of compiling a list of email addresses of people who do not want to receive spam. The idea was not a new one, but the authors were particularly aggressive in implementing their project. If a client who had ordered a spam mailing ignored a request to remove an address from the database of email addresses used, the client’s website would be bombarded automatically by thousands of requests from the personal computers of Blue Frog participants. In some ways this is similar to a distributed denial of service attack. But unlike the hackers who normally conduct such attacks, the Blue Frog organizers did not conceal their identities and gave fair warning of their intentions. The ethics of applying these kinds of measures in the fight against spam is a debatable subject, but in any case based on the project’s success and the number of people participating, spammers began to feel the pressure, ,and they ultimately decided to take action.
Blue Frog was closed by attacks on the project’s main server. The owners of the resources were worried that the people participating in the project who had put their addresses in the Blue Frog database could be victimized by the spammers; similar concerns about users with no connection to the project were voiced by the provider. In the end, Blue Frog was closed down.
The Blue Frog incident demonstrated spammers’ ability to consolidate against the common threat posed by antispam developers. This was a warning: the ostensible lack of connections between spammers (similar to the links between hacker groups) was a charade. In reality, spammers maintain regular contact with each another – they have to, otherwise they would not be able to organize so quickly and unite as a team.
The ability of spammers to consolidate and centralize efforts on an international scale represents a new threat to the security of electronic communications.
Forecasts
2006 has shown us that as far as the technical aspects are concerned, antispam developers have already figured out how to provide reliable protection against spammers. But the volume of spam is not falling, and it’s much too early to declare the problem of spam solved. The continued development of today’s situation with spam in 2007 is already clear:
- Don’t expect spam to stop arriving in your inbox, and don’t expect the amount of spam to decline. Spammers will look for ways to penetrate security measures, and antispam professionals will continue to repel their attacks.
- 2007 will not likely bring new spam technologies, but existing technologies will be developed further.
- Spammers will continue to develop graphical methods, but it doesn’t currently look as though the outlook for these tactics is very promising. Top antispam developers will be able to put an end to this threat.
- The technologies used to automatically create a large number of related texts for a single mailing using a template will also be further developed, possibly with the addition of linguistic algorithms as opposed to the previous usage of random text.
- The criminalization of spam will also continue: English-language spam mailings will be adapted for a Russian-speaking audience, and new Russia-specific types of computer fraud will appear on the Russian Internet.

























Kaspersky Security Bulletin 2006: Spam