
Kaspersky Managed Detection and Response service (MDR) provides round-the-clock monitoring and threat detection, based on Kaspersky technologies and expertise. The annual MDR analyst report presents insights based on the analysis of incidents detected by Kaspersky’s SOC team. It sheds light on the most prevalent attacker tactics, techniques, and tools, as well as the characteristics of identified incidents and their distribution across regions and industry sectors among MDR customers.
This report answers key questions, including:
- Who are the potential attackers?
- What methods are they using today?
- How can their activities be effectively detected?
Security incident statistics for 2024
In 2024, the MDR infrastructure received and processed on average 15,000 telemetry events per host every day, generating security alerts as a result. Around 26% of these alerts were processed by machine learning algorithms and the rest were analyzed by the SOC team. On average, more than two high-severity incidents were detected daily. MDR customers were informed about all identified incidents via the MDR portal.
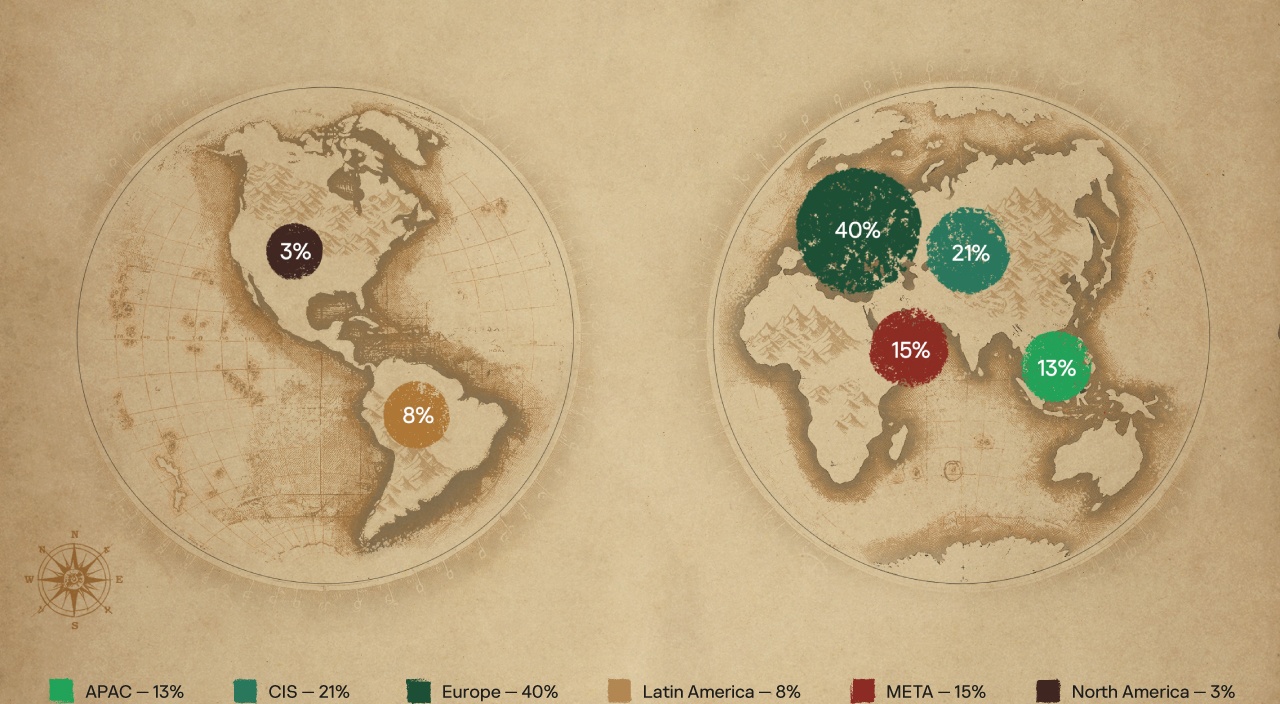
Geography of MDR customers
Kaspersky MDR customers span the globe, giving us a comprehensive and objective view of regional attack behaviors and tactics. The largest concentration of customers is in Europe, the CIS, and the META regions.
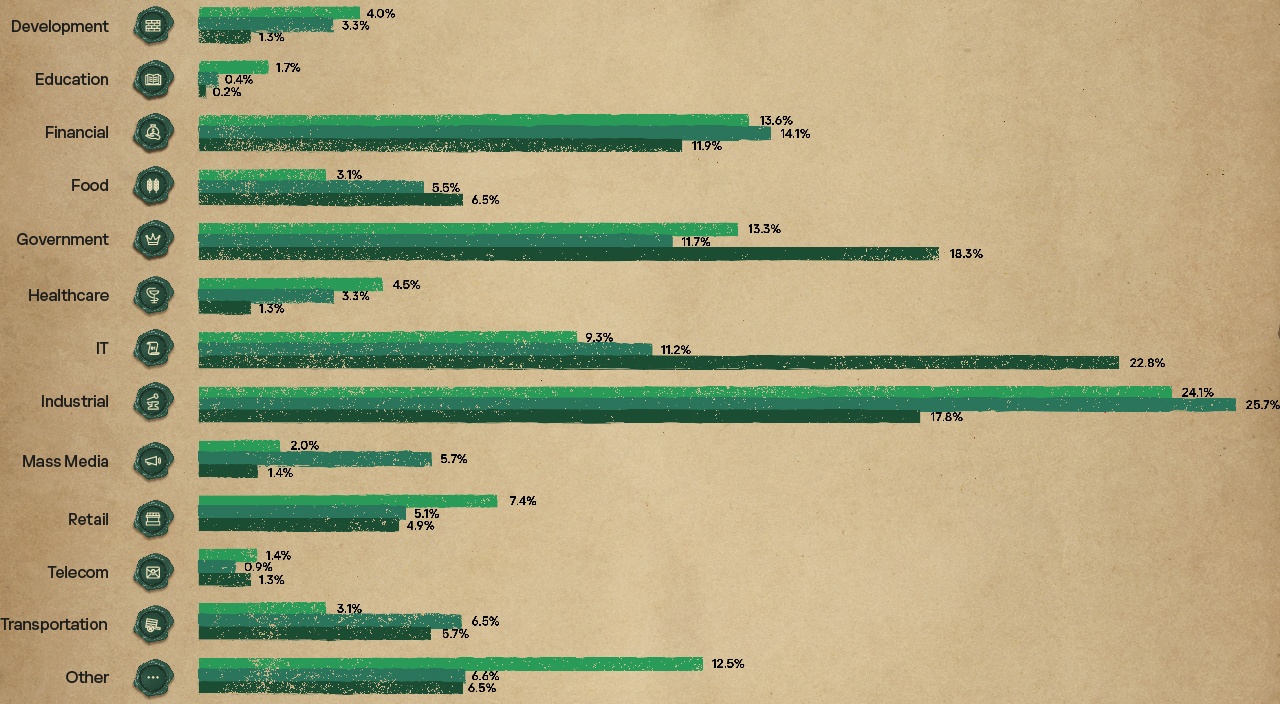
Distribution of incidents by industry
In 2024, the MDR team observed the highest number of incidents in the industrial (25.7%), financial (14.1%), and government (11.7%) sectors. However, if we consider only high-severity incidents, the distribution is somewhat different: 22.8% in IT, 18.3% in government, 17.8% in industrial, and 11.9% in the financial sector.
General observations and recommendations
In 2024, we observed the following trends in the incidents detected by our SOC team:
- High-severity incidents decreased, but complexity increased. The number of high-severity incidents decreased by 34% compared to 2023. However, the mean time to investigate and report these incidents increased by 48%, indicating a rise in the average complexity of attacks. This is supported by the fact that the vast majority of triggered detection rules and IoAs were from specialized XDR tools. This marks a shift from previous years, where OS log-based detection played a significant role. Given this trend, specialized tools like XDR are essential for effectively detecting and investigating modern threats.
- Human-driven targeted attacks are increasing. Human-driven targeted attacks accounted for 43% of high-severity incidents – 74% more than in 2023 and 43% more than in 2022. Despite advances in automated detection tools, motivated attackers continue to find ways to bypass them. To counter such threats, human-driven solutions like Managed Detection and Response are critical. For organizations with in-house security operations teams, internal processes and technologies must be equipped to handle the modern threat landscape. Comprehensive SOC consulting services can help achieve this.
- Attackers often return after a successful breach. The statistics consistently show that attackers often return after a successful attack. This is especially evident in the government sector, where attackers aim to persist in the system long-term for espionage purposes. In such cases, combining an XDR-equipped in-house SOC or outsourced MDR with regular Compromise Assessments is an effective way to detect and investigate incidents that may be missed by existing security measures.
- Living off the Land techniques remain prevalent. Attackers often use Living off the Land (LotL) methods in infrastructures lacking proper system configuration controls. A significant number of incidents are linked to unauthorized changes, such as adding accounts to privileged groups or weakening secure configurations. To minimize false positives in these scenarios, effective configuration management and formal procedures for implementing changes and managing access are crucial.
- User Execution and Phishing remain top threats. User Execution and Phishing techniques ranked again in the top three threats, with nearly 5% of high-severity incidents involving successful social engineering. Users are still the weakest link, making Security Awareness training an important focus for corporate information security planning.
To explore these and other trends in detail, download full report (PDF).


















Managed detection and response in 2024