
- IT threat evolution in Q3 2023
- IT threat evolution in Q3 2023. Non-mobile statistics
- IT threat evolution in Q3 2023. Mobile statistics
Targeted attacks
Unknown threat actor targets power generator with DroxiDat and Cobalt Strike
Earlier this year, we reported on a new variant of SystemBC called DroxiDat that was deployed against a critical infrastructure target in South Africa. This proxy-capable backdoor was deployed alongside Cobalt Strike beacons.
The incident occurred in the third and fourth week of March, as part of a small wave of attacks involving both DroxiDat and Cobalt Strike beacons around the world; and we believe this incident may have been the initial stage of a ransomware attack.
DroxiDat, a lean variant of SystemBC that acts as a system profiler and simple SOCKS5-capable bot, was detected at an electric utility company. The C2 (command and control) infrastructure for the incident involved an energy-related domain, ‘powersupportplan[.]com’, that resolved to an already suspicious IP host. This host had been used several years earlier as part of APT activity, raising the possibility that this might be an APT-related targeted attack, although we were unable to establish a link to that previous APT and it was probably unrelated.
No ransomware was delivered to the organization, and we do not have enough information to precisely attribute this activity. However, in a healthcare-related incident involving DroxiDat around the same time, Nokoyawa ransomware was delivered, along with several other incidents involving Cobalt Strike sharing the same license ID, staging directories and/or C2.
Analysis of samples exploiting CVE-2023-23397 vulnerability
On March 14, Microsoft reported a critical Elevation of Privilege (EoP) vulnerability (CVE-2023-23397) in the Outlook client. The vulnerability is triggered when an attacker sends an Outlook object (task, message or calendar event) within an extended MAPI property that contains a UNC path to an SMB share on a server controlled by the threat actor, resulting in a Net-NTLMv2 hash leak. The vulnerability affects all supported versions of Outlook, and no user interaction is required to trigger it.
Even after Microsoft published a patch for the vulnerability, it appears that the implemented fix could be easily bypassed on the client side by forging the malicious UNC path with a specific format. This feature bypass vulnerability (CVE-2023-29324) was itself patched in May.
Evidence that these vulnerabilities were being exploited by an unknown attacker was made public via samples submitted to VirusTotal. Some of the samples submitted to VirusTotal were later found to exploit CVE-2023-23397; others were published after the vulnerability was publicly disclosed. The timestamps in the header indicated that the vulnerability had been at the disposal of the attacker for at least a year.
The targets included government, military, critical infrastructure and IT organizations in Ukraine, Romania, Poland, Jordan, Turkey, Italy and Slovakia.
You can read our analysis of the attack samples here: Comprehensive analysis of initial attack samples exploiting CVE-2023-23397 vulnerability.
Common TTPs in attacks on industrial organizations
In 2022, we investigated a series of attacks against industrial organizations in Eastern Europe. In these campaigns, the attackers aimed to establish a permanent channel for data exfiltration, including data stored on air-gapped systems.
Based on similarities found between these and previously researched campaigns (for example, ExCone, DexCone), including the use of FourteenHi variants, specific TTPs and the scope of the attack, we believe with medium to high confidence that the activity is the work of the threat actor APT31 (aka Judgment Panda and Zirconium).
To exfiltrate data and deliver next-stage malware, the attackers abuse cloud-based data storage, such as Dropbox or Yandex Disk, as well as a temporary file sharing service. They also use a C2 deployed on regular virtual private servers (VPS). In addition, they deploy a stack of implants that collect data from air-gapped networks via infected removable drives.
For most implants, the threat actor uses similar implementations of DLL hijacking (often associated with ShadowPad malware) and memory injection techniques, along with the use of RC4 encryption to hide the payload and evade detection. libssl.dll or libcurl.dll was statically linked to implants to implement encrypted C2 communications.
In total we identified over 15 implants and their variants planted by the attackers in various combinations. The entire stack of implants used in the attacks can be divided into three categories, based on their roles:
- first-stage implants for persistent remote access and initial data gathering;
- second-stage implants for gathering data and files, including from air-gapped systems;
- third-stage implants and tools used to upload data to the C2.
You can read the full report here: Common TTPs of attacks against industrial organizations.
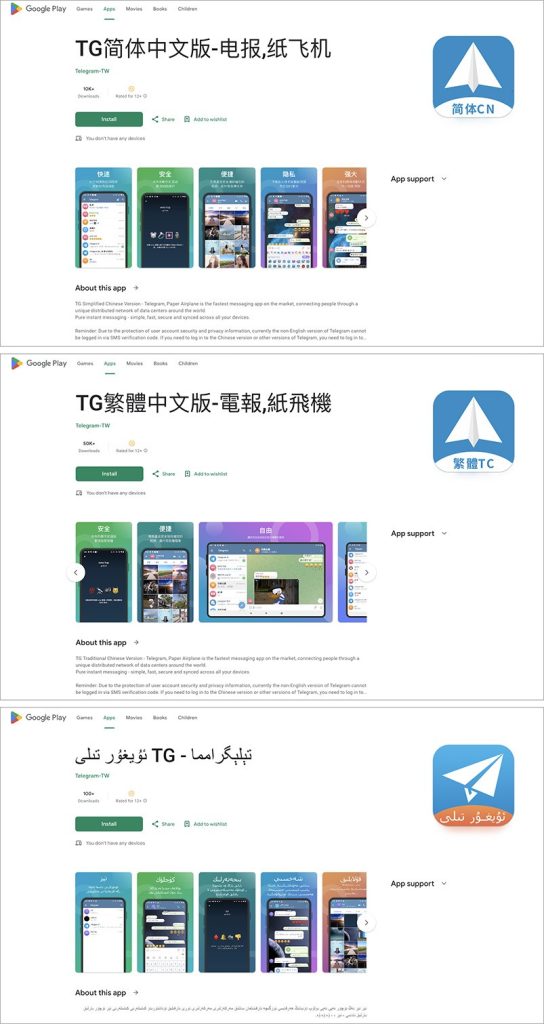
Evil Telegram doppelganger used to target people in China
We discovered several infected apps on Google Play masquerading as Uyghur, Simplified Chinese and Traditional Chinese versions of Telegram. The app descriptions were written in the respective languages and contained images very similar to those on the official Telegram page on Google Play.
To persuade people to download these mods instead of the official app, the developer claimed that they worked faster than other clients thanks to a distributed network of data centers around the world.
We examined the code in the apps and found that they were only slightly modified versions of the official Telegram app. However, they included an additional module that constantly monitored the messenger and sent data to the spyware creator’s C2 server. This included all contacts, sent and received messages with attached files, names of chats/channels, name and phone number of the account owner – the target’s entire correspondence. Even if they changed their name or phone number, this information was also sent to the attackers.
While we would recommend that people only download apps from official stores, even that doesn’t guarantee an app’s security, so it’s important to be wary of third-party mods, even those distributed by Google Play. We reported this threat to Google, who removed all the apps from Google Play.
Other malware
Possible supply-chain attack on Linux machines
In recent years, Linux machines have become a growing target for all sorts of threat actors – our telemetry shows that 260,000 unique Linux samples appeared in the first half of this year. Unfortunately, campaigns targeting Linux can operate for years without being noticed by the cybersecurity community. We discovered one such long-running attack while investigating a set of suspicious domains.
We discovered that the domain in question has a deb.fdmpkg[.]org subdomain that claims to host a Debian repository of software called “Free Download Manager”. We also discovered a Debian package of this software available for download from the URL https://deb.fdmpkg[.]org/freedownloadmanager.deb. This package turned out to contain an infected postinst script that is executed upon installation. This script drops two ELF files to the paths /var/tmp/crond and /var/tmp/bs and then establishes persistence by creating a cron task (stored in the file /etc/cron.d/collect) that launches the /var/tmp/crond file every 10 minutes.
The version of Free Download Manager installed by the infected package was released on January 24, 2020. The postinst script contains comments in Russian and Ukrainian, including information about improvements made to the malware, as well as statements by activists. They mention the dates 20200126 (January 26, 2020) and 20200127 (January 27, 2020).
Once the malicious package is installed, the executable /var/tmp/crond is launched on every startup through cron. This executable is a backdoor and doesn’t import any functions from external libraries. To access the Linux API, it invokes syscalls with the help of the statically linked dietlibc library.
Upon startup, this backdoor makes a type A DNS request for the <hex-encoded 20-byte string>.u.fdmpkg[.]org domain. In response, the backdoor receives two IP addresses that encode the address and port of a secondary C2 server. After parsing the response to the DNS request, the backdoor launches a reverse shell, using the secondary C2 server for communications. The communication protocol is either SSL or TCP. In the case of SSL, the crond backdoor launches the /var/tmp/bs executable and delegates all further communication to it. Otherwise, the reverse shell is created by the crond backdoor itself.
The attackers use the reverse shell to deploy a Bash stealer that collects data such as system information, browsing history, saved passwords, cryptocurrency wallet files and credentials for cloud services (AWS, Google Cloud, Oracle Cloud Infrastructure, Azure). The stealer downloads an uploader binary from the C2 server, saves it to /var/tmp/atd and uses this binary to upload stealer execution results to the attackers’ infrastructure. The whole infection chain is shown below:
The redirection to the malicious deb.fdmpkg[.]org domain did not occur in all cases. It appears that the malware developers scripted the malicious redirection to occur with some degree of probability or based on the digital fingerprint of the potential victim.
We also checked for code overlaps with other malware samples and it turned out that the crond backdoor represents a modified version of a backdoor called Bew, which we have been detecting since 2013.
The Cuba ransomware gang
In September we took a close look at the history and TTPs (Tactics, Techniques and Procedures) of the Cuba ransomware gang, a group that first appeared on our radar in late 2020 under the name “Tropical Scorpius”. The group has changed names several times since its inception – other names include ColdDraw and Fidel. This February, we came across another name for the gang – “V Is Vendetta”, which deviated from the hackers’ favored Cuban theme and may have been a moniker used by a sub-group or affiliate.
The group has targeted numerous companies around the world, with victims including retailers, financial and logistical services companies, government agencies and manufacturers. Most have been located in the US, with some victims in Canada, Europe, Asia and Australia.
As with most cyber-extortionists, the Cuba gang encrypts victims’ files and demands a ransom in exchange for a decryption key. The group employs both well-known “classic” credential access tools, such as Mimikatz, and self-written applications. It exploits vulnerabilities in the software used by the target companies: mostly known issues, such as the combination of ProxyShell and ProxyLogon for attacking Exchange servers, and security holes in the Veeam data backup and recovery service. It has also been known to use compromised remote desktop (RDP) connections for initial access.
The group had adopted the double extortion model: as well as encrypting data, it threatens to publish the stolen information online if the victim doesn’t pay up. Data is encrypted with the Xsalsa20 symmetric algorithm, and the encryption key with the RSA-2048 asymmetric algorithm. This is known as hybrid encryption, a cryptographically secure method that prevents decryption without the key.
The incoming and outgoing payments in the bitcoin wallets whose identifiers the hackers provide in their ransom notes exceed a total of 3,600 BTC – more than $103,000,000 (converted at the rate of $28,624 for 1 BTC). The gang owns numerous wallets, constantly transferring funds between them, and uses bitcoin mixers – services that send bitcoins through a series of anonymous transactions to make the origin of the funds harder to trace.
The exact origins of the Cuba gang and the identities of its members are unknown, although some researchers believe it may be a successor to another gang, Babuk. Like many other ransomware gangs, Cuba is a Ransomware-as-a-Service (RaaS) group, allowing its partners to use the ransomware and associated infrastructure in exchange for a share of any ransom they collect.
Leaked Lockbit 3 builder
Lockbit is one of the most prevalent ransomware strains. It comes with an affiliate Ransomware-as-a-Service (RaaS) program that offers participants up to 80 percent of the ransom. It also includes a bug bounty program for those who detect and report vulnerabilities that allow files to be decrypted without paying the ransom (according to the criminals behind Lockbit, there have been bounty payments of up to $50,000). Lockbit also offers a searchable portal to query leaked information from companies targeted by the ransomware family.
Lockbit version 3, also known as Lockbit Black, was first detected in June last year and poses a challenge for analysts and automated analysis systems. Some of the most challenging characteristics include the use of encrypted executables with randomly generated passwords to hinder automatic analysis, strong protection techniques against reverse engineering and the use of many undocumented kernel-level Windows functions.
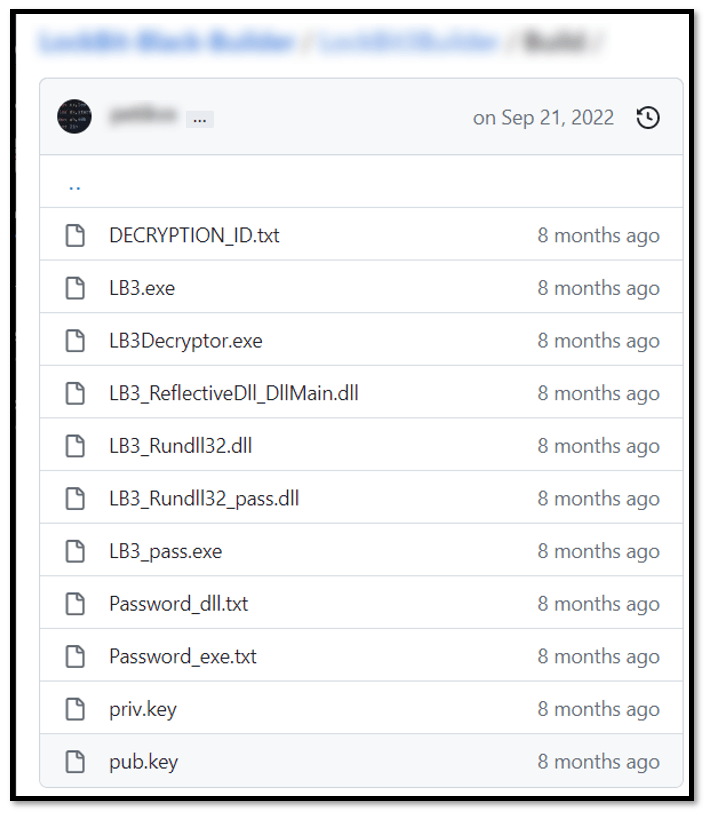
In September 2022, a builder for Lockbit 3 was leaked, allowing anyone to create their own customized version of the ransomware.
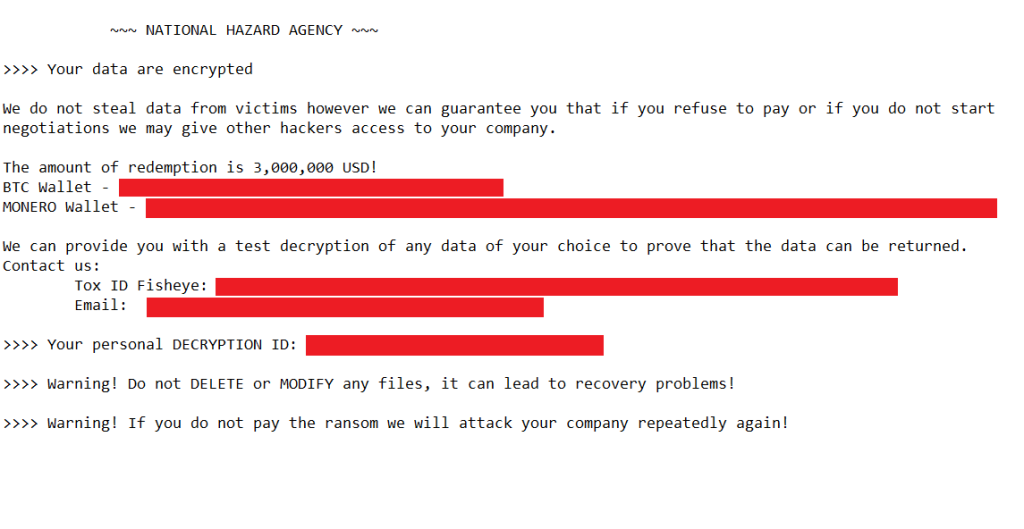
Immediately after this leak, during an incident response by our Global Emergency Response Team (GERT), we found an intrusion that leveraged the encryption of critical systems with a variant of Lockbit 3, detected as Trojan.Win32.Inject.aokvy. The intrusion included TTPs similar to those highlighted in our report about the top eight ransomware groups behind ransomware attacks. Although this variant was confirmed as Lockbit, the ransom demand procedure was quite different from those known to be implemented by this threat actor, with a ransom note that included a headline related to a previously unknown group called “NATIONAL HAZARD AGENCY”.
Original Lockbit ransom note and a different ransom note related to a previously unknown group
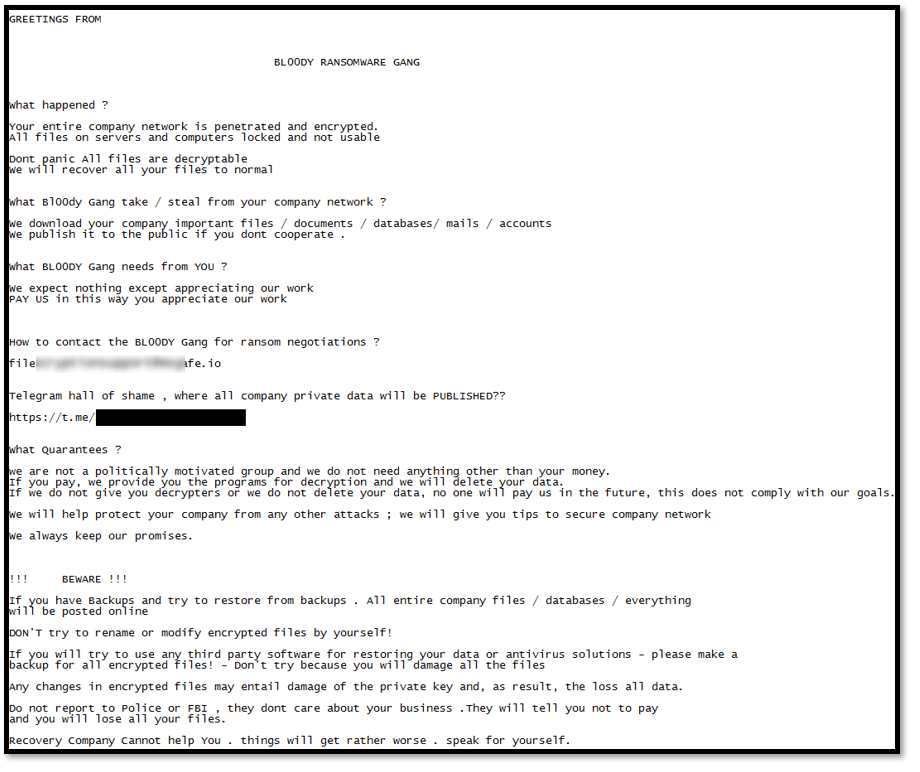
According to other analyst publications, different groups appeared using the exfiltrated builders, but with their own notes and communication channels. It turned out that many threat actors took advantage of the leak.
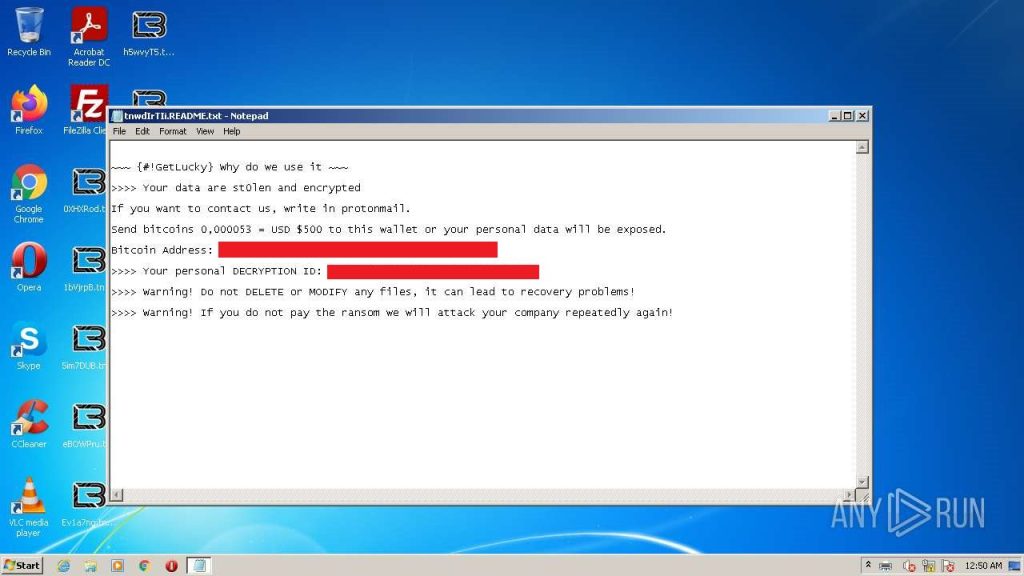
BL00DY RANSOMWARE GANG ransom note and GetLucky ransom note
Our GERT team analyzed the builder to understand its construction methodology and define additional analysis opportunities.
The evolving world of crimeware
The malware landscape continues to evolve: new malware families emerge, others disappear, others drop off the radar only to appear again later. That’s why we track all these changes, relying both on samples that we detect and our monitoring efforts, including botnets and underground forums.
We recently found a new loader called “DarkGate”, a new LokiBot infostealer campaign and new Emotet samples.
Our discovery of DarkGate began in June 2023, when a well-known malware developer posted an advertisement on a popular dark web forum, boasting of having developed a loader that he had been working on for more than 20,000 hours since 2017. Some of the main features went beyond those of a typical downloader, allegedly including a hidden VNC, Windows Defender exclusion, browser history stealer, reverse proxy, file manager and Discord token stealer.
The fact that the sample we obtained was missing some of these features isn’t significant, since they are enabled or disabled in the builder anyway. However, we were able to reconstruct the infection chain, which consists of four stages, all the way to loading the final payload: DarkGate itself.
- VBS downloader script. This sets several environment variables to obfuscate subsequent command invocations. Two files (exe and script.au3) are then downloaded from the C2, and Autoit3.exe is executed with script.au3 as an argument.
- AutoIT V3 script. This is a BASIC-like freeware scripting language often used by malware authors, as it can simulate keystrokes and mouse movements, among other things. The executed script is obfuscated, but ultimately allocates memory to the embedded shellcode and finally executes the shellcode.
- This constructs a PE file in memory, resolves imports dynamically and transfers control to the file.
- DarkGate executor (the PE file constructed by the shellcode). The executor loads the au3 file into memory and locates an encrypted blob within the script. The encrypted blob is then decrypted (using an XOR key and a final NOT operation). This results in a PE file whose import table is dynamically resolved. The end result is the DarkGate loader.
LokiBot first surfaced in 2016 and remains active today. It steals credentials from various applications such as browsers, FTP clients and others. We recently detected a phishing campaign targeting cargo shipping companies that drops LokiBot.
In the cases we investigated, the victims received an email that appeared to come from a business contact listing port charges that needed to be paid. An Excel document was attached to the message. When the document was opened, the target was asked to enable macros. This was a fake warning because the document didn’t contain any macros. Instead, it tried to exploit the CVE-2017-0199 vulnerability. This vulnerability makes it possible to open a remote document by providing a link. This leads to the download of an RTF document, which in turn exploits another vulnerability, namely CVE-2017-11882, which enables the download and execution of LokiBot.
Once executed, LokiBot collects credentials from various sources and saves them in a buffer inside the malware, after which it sends them to the C2. After sending out system information, the malware listens for additional C2 commands that can be used to download additional malware, run a keylogger, and so on.
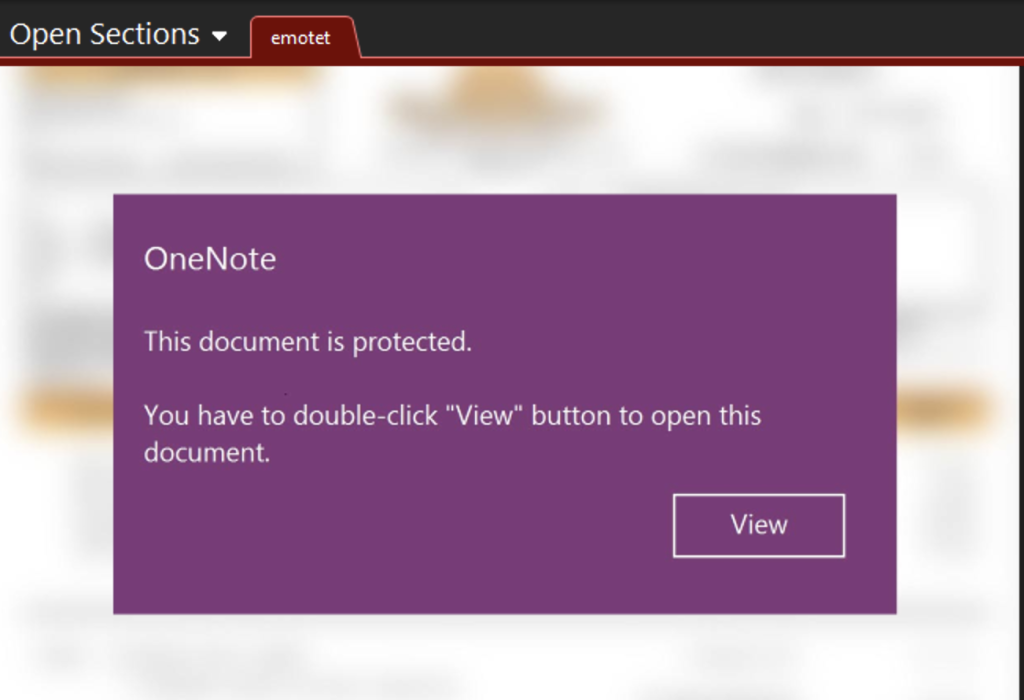
Emotet is a notorious botnet that was taken down in 2021, but subsequently resurfaced. In its recent wave of attacks, the group jumped on the OneNote infection bandwagon, sending emails with malicious OneNote files. Opening one of these files displays an image similar to the one below.
If someone clicks the View button, it executes an embedded and obfuscated malicious VBScript. There are several sites that contain the payload. The script tries each one until it succeeds, and then saves the payload, a DLL, in the temp directory, executing it with regsvc32.exe. The executed DLL then loads a resource (LXGUM) from its resource section and decrypts it with a simple rolling XOR algorithm.
The decrypted payload is actually shellcode that performs a typical import by hash. Two of the resolved functions are LdrLoadDll and LdrGetProcedureAddress, often used by malware authors to evade dynamic analysis of well-known APIs – in this case LoadLibrary and GetProcAddress. Next, memory is allocated, and a blob (a PE file) from the resource section is written to the allocated memory, which is the final Emotet payload. DLL dependencies are resolved, and the Import Address Table (IAT) is reconstructed. The shellcode then overwrites the DOS header of the PE file, in order to make it more difficult for EDR (Extended Detection and Response) solutions to detect the binary in the memory. Finally, Emotet is executed. The Emotet payload is the same as in the previous waves of attacks.
You can read the full details in our crimeware report.
A cryptor, a stealer and a banking Trojan
We monitor many underground forums. On one of them we saw an advertisement promoting a new cryptor/loader variant called ASMCrypt. The idea behind this type of malware is to load the final payload without the loading process or the payload itself being detected by antivirus, EDR, etc. This sounds a lot like the DoubleFinger loader we discussed previously, and we believe that ASMCrypt is an evolved version of DoubleFinger. However, it works slightly differently and is more of a “front” for the actual service that runs on the TOR network.
First, the buyer obtains the ASMCrypt binary, which connects to the malware’s backend service over the TOR network using hardcoded credentials. If everything is okay, the options menu is displayed.
The buyer can choose different options:
- stealth or invisible injection method;
- the process the payload should be injected into;
- folder name for startup persistence;
- stub type – either the malware itself masquerading as Apple QuickTime, or a legitimate application that sideloads the malicious DLL.
After selecting all the desired options and pressing the Build button, the application creates an encrypted blob hidden inside a .PNG file. This image needs to be uploaded to an image hosting site. The malicious DLL (or binary) from the last bullet point above is also created and will be distributed by the cybercriminals. When the malicious DLL is executed on a victim system, it downloads the .PNG file, decrypts it, loads it into memory and then executes it.
We also published a report on a new version of the Lumma stealer. The Arkei stealer, written in C++, first appeared in May 2018 and has been forked/rebranded several times over the last few years. It has been variously known as Vidar, Oski, Mars and now Lumma – which has a 46 percent overlap with Arkei.
Lumma is distributed via a spoofed website that mimics a legitimate .DOCX to .PDF site. When a file is uploaded, it is returned with the double extension .PDF.EXE.
Over time, the main functionality of all the variants has remained the same: stealing cached files, configuration files and logs from crypto wallets. It does this by acting as a browser plugin, but it also supports the stand-alone Binance application. In our report, we highlight the main changes Lumma has undergone since it first appeared in August 2022.
Zanubis, an Android banking Trojan, first appeared around August 2022, targeting users of financial institutions and crypto-currency exchanges in Peru. The Trojan’s main infection path is to impersonate legitimate Peruvian Android applications, then trick the user into enabling accessibility permissions to take full control of the device.
We spotted more recent samples of Zanubis in the wild around April 2023. The malware was disguised as the official Android application for the Peruvian governmental organization SUNAT (Superintendencia Nacional de Aduanas y de Administración Tributaria). We explored the new design and features of the malware, which seemed to have gone through several evolutionary stages to reach a new level of sophistication.
Zanubis is obfuscated using Obfuscapk, a popular obfuscator for Android APK files. After the victim grants accessibility permissions to the malicious app, allowing it to run in the background, the malware uses WebView to load a legitimate SUNAT website used to look up debts. The intention here is to trick the unsuspecting user into believing that the app is part of the SUNAT ecosystem of services.
Communication with the C2 relies on WebSockets and the library called Socket.IO. The latter allows the malware to establish a persistent connection to the C2, which provides failover options (from WebSockets to HTTP and vice versa). Another advantage is that it provides the C2 with a scalable environment where all new infections by Zanubis can receive commands (also called events) from the C2 on a massive scale if required.
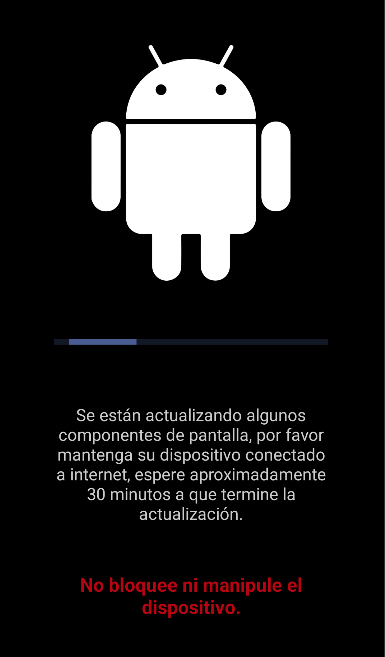
An interesting feature of the malware is that it pretends to be an Android update, thus blocking the phone from being used. While the “update” is running, the phone remains unusable to the point that it can’t be locked or unlocked, as the malware monitors those attempts and blocks them.
You can read our report on ASMCrypt, Lumma and Zanubis here.
Malware continuously evolves, and TTPs change, hindering detection. It can also be difficult for an organization to decide which type of malware threat to defend against first. Intelligence reports can help identify the threats relevant to your business and to stay protected. To stay up to date on the latest TTPs used by criminals, or if you have questions about our private reports, reach out to us at crimewareintel@kaspersky.com.






















IT threat evolution Q3 2023