
![]() Download the full report (PDF)
Download the full report (PDF)
Overview
Targeted attacks and malware campaigns
Dropping Elephant
Targeted attack campaigns don’t need to be technically advanced in order to be successful. In July 2016 we reported on a group called Dropping Elephant (also known as ‘Chinastrats’ and ‘Patchwork’). Using a combination of social engineering, old exploit code and some PowerShell-based malware this group was able to steal sensitive data from its victims.
This group, which has been active since November 2015, targets high profile diplomatic and economic organizations linked to China’s foreign relations – an interest that is evident from the themes the attackers use to trap their victims.
The attackers use a combination of spear-phishing e-mails and watering-hole attacks. The first involves sending a document with remote content. When the victim opens the document, a ping request is sent to the attackers’ Command-and-Control (C2) server. The victim then receives a second spear-phishing e-mail, containing either a Word document or a PowerPoint file (these exploit old vulnerabilities – CVE-2012-0158 and CVE-2014-6352 respectively). Once the payload has been executed, a UPX-packed AutoIT executable is dropped on to the system: once executed, this downloads further components from the C2 server and the theft of data from the victim’s computer begins.
In Q3 2016, @kaspersky repelled 172m malicious attacks via online resources located in 191 countries #KLreport #Infosec
Tweet
The attackers also created a watering-hole website that downloads genuine news articles from legitimate websites. If a visitor wants to view the whole article, they are prompted to download a PowerPoint file: this reveals the rest of the document, but also asks the victim to download a malicious object. The attackers sometimes e-mail links to their watering-hole website. In addition, they maintain Google+, Facebook and Twitter accounts, to develop relevant search engine optimization (SEO) and to reach out to wider targets.
The success of the Dropping Elephant group is striking given that no zero-day exploits or advanced techniques were used to target high-profile victims – it’s clear that by applying security updates and improving the security awareness of staff, the success of attacks like this can be prevented. At the start of the year we predicted that APT groups would invest less effort in developing sophisticated tools and make greater use of off-the-shelf malware. Dropping Elephant provides a further example of how low investment and use of ready-made toolsets can be very effective when combined with high quality social engineering.
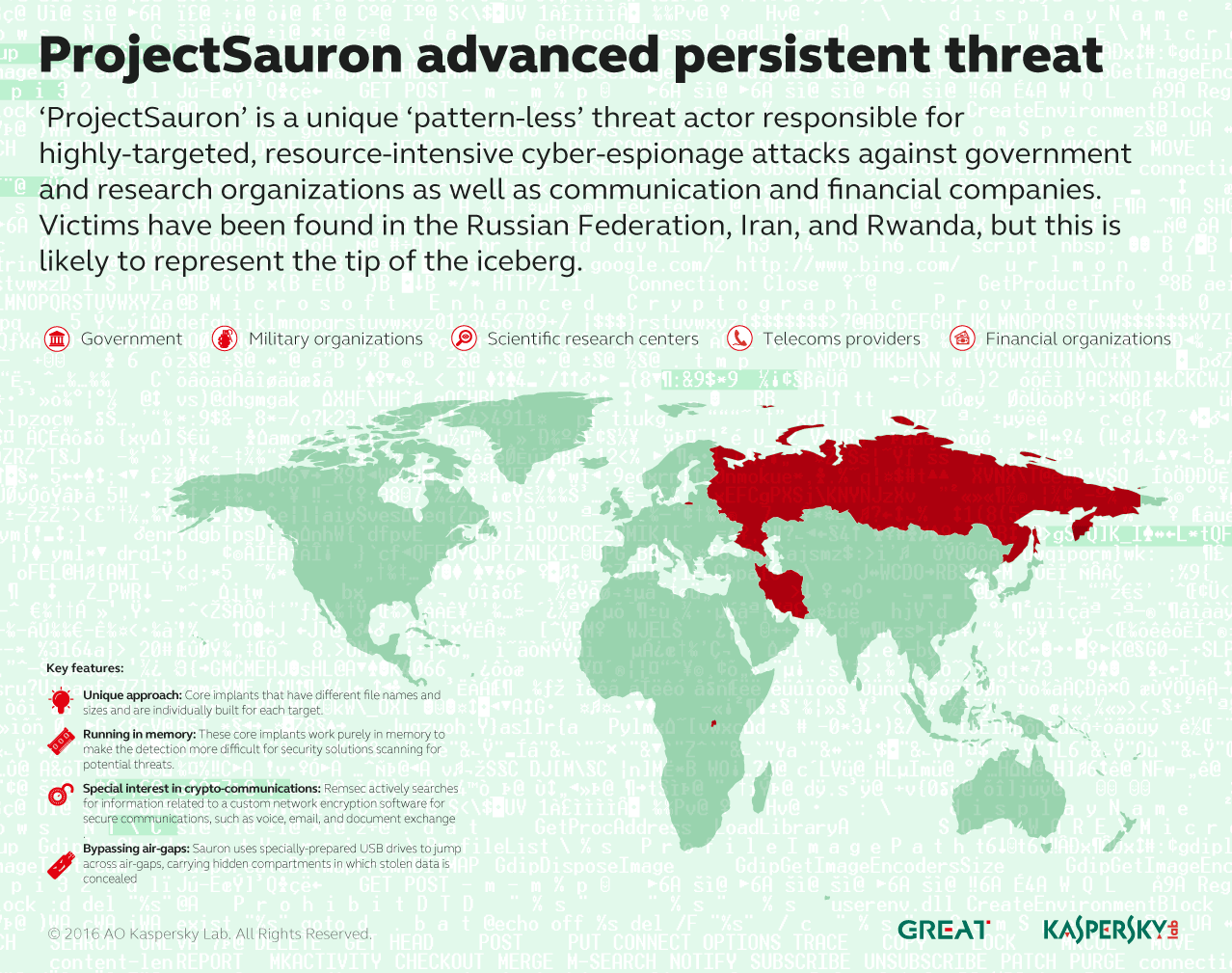
ProjectSauron
In September, our Anti-Targeted Attack Platform flagged an anomaly in the network of a customer’s organization. Further investigation led us to uncover ProjectSauron, a group that has been stealing confidential data from organizations in Russia, Iran and Rwanda – and probably other countries – since June 2011. We have identified more than 30 victims: the target organizations all play a key role in providing state services and come from government, military, scientific research, telecommunications and financial sectors.
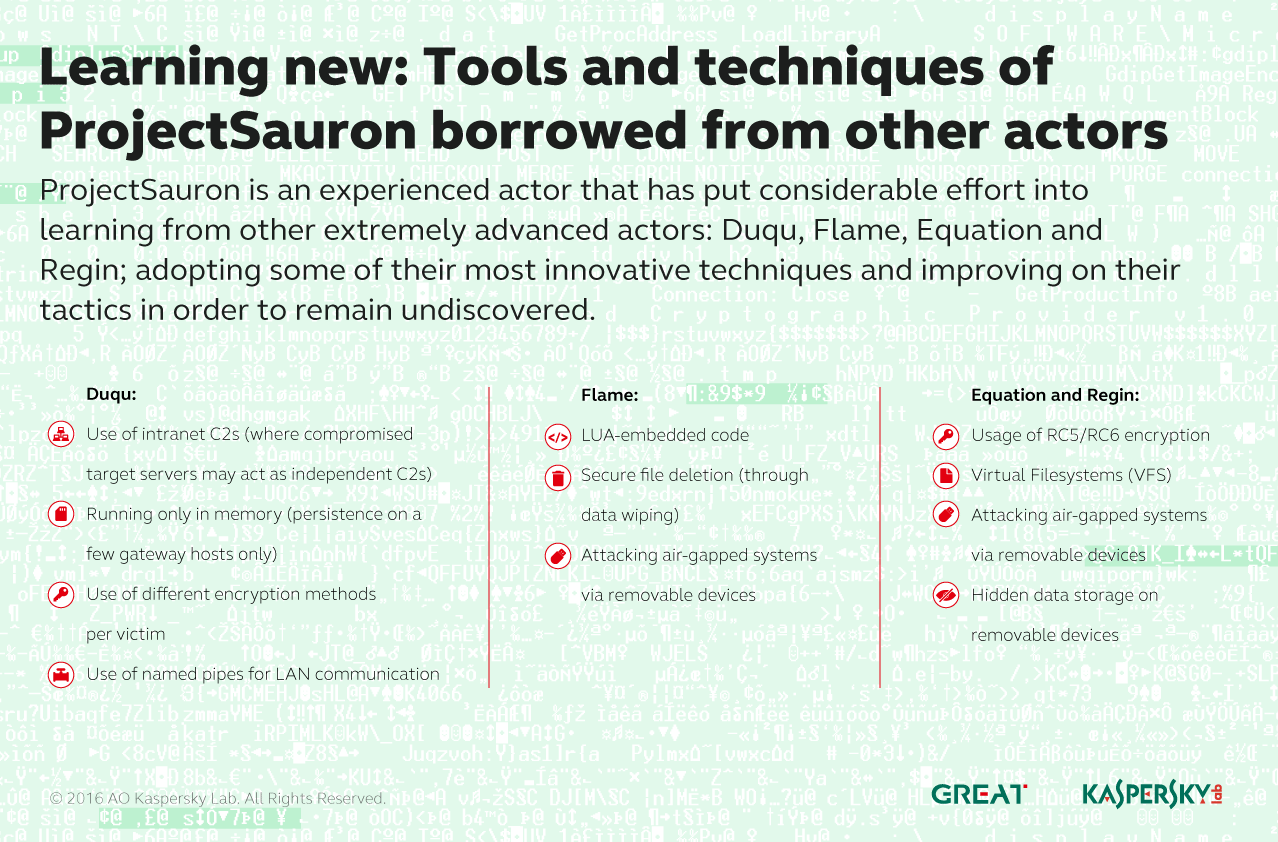
ProjectSauron is particularly focused on obtaining access to encrypted communications, hunting for them using an advanced, modular cyber-espionage platform that incorporates a set of unique tools and techniques. The cost, complexity, persistence and the ultimate goal of the operation (i.e. stealing secret data from state-related organizations) suggest that ProjectSauron is a state-sponsored campaign. ProjectSauron gives the impression of an experienced threat group that has made a considerable effort to learn from other highly advanced attacks, including Duqu, Flame, Equation and Regin – adopting some of their most innovative techniques and improving on their tactics in order to remain undiscovered.
One of the most noteworthy features of ProjectSauron is the deliberate avoidance of patterns: the implants used by the group are customized for each victim and are never re-used. This makes the use of traditional Indicators of Compromise (IoC) almost useless. This approach, along with the use of multiple routes for the exfiltration of stolen data (such as legitimate e-mail channels and DNS) enables ProjectSauron to conduct well-hidden, long-term spying campaigns in targeted networks.
Key features of ProjectSauron:
- core implants that are unique for each victim;
- use of legitimate software update scripts;
- use of backdoors that download new modules or run commands in memory only;
- focus on information relating to custom network encryption software;
- use of low-level tools orchestrated by high-level LUA scripts (the use of LUA is very rare – previously seen only in Flame and Animal Farm attacks;
- use of specially prepared USB drives to jump across air-gapped networks, with hidden compartments for storing stolen data;
- use of multiple exfiltration mechanisms to conceal transfer of data in day-to-day traffic.
The method used to initially infect victims remains unknown.
The single use of unique methods, such as control server, encryption keys and more, in addition to the adoption of cutting-edge techniques from other major threats groups, is new. The only effective way to withstand such threats is to deploy multiple layers of security, with sensors to monitor for even the slightest anomaly in organizational workflow, combined with threat intelligence and forensic analysis. You can find further discussion of the methods available to deal with such threats here.
ShadowBrokers
In August, a person or group going under the name ‘ShadowBrokers’ claimed to possess files belonging to the Equation group. They provided links to two PGP encrypted archives. They provided the password to the first for free, but ‘auctioned’ the second, setting the price at 1 million BTC (1/15th of the bitcoins in circulation).
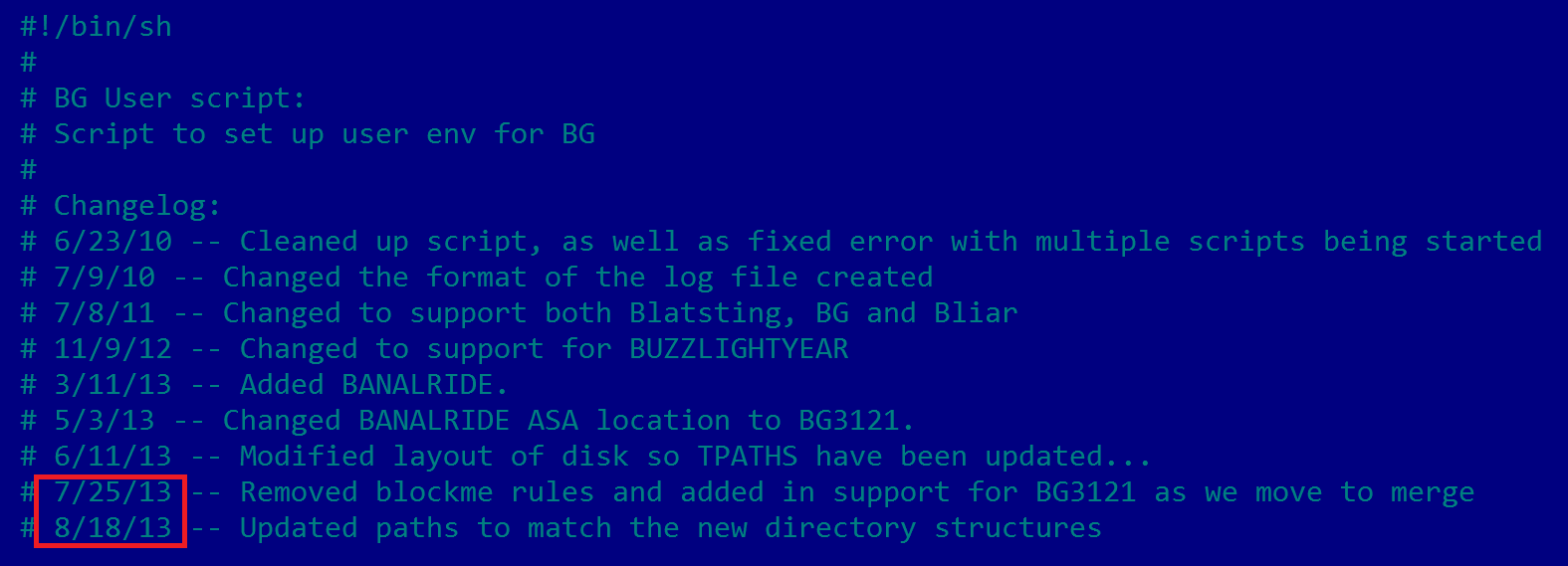
Having uncovered the Equation group in February 2015, we were interested in examining the first archive. It contains almost 300MB of firewall exploits, tools and scripts, under cryptonyms such as BANANAUSURPER, BLATSTING and BUZZDIRECTION. Most of the files are at least three years old, with change entries pointing to August 2013 and the newest time-stamp dating to October 2013.
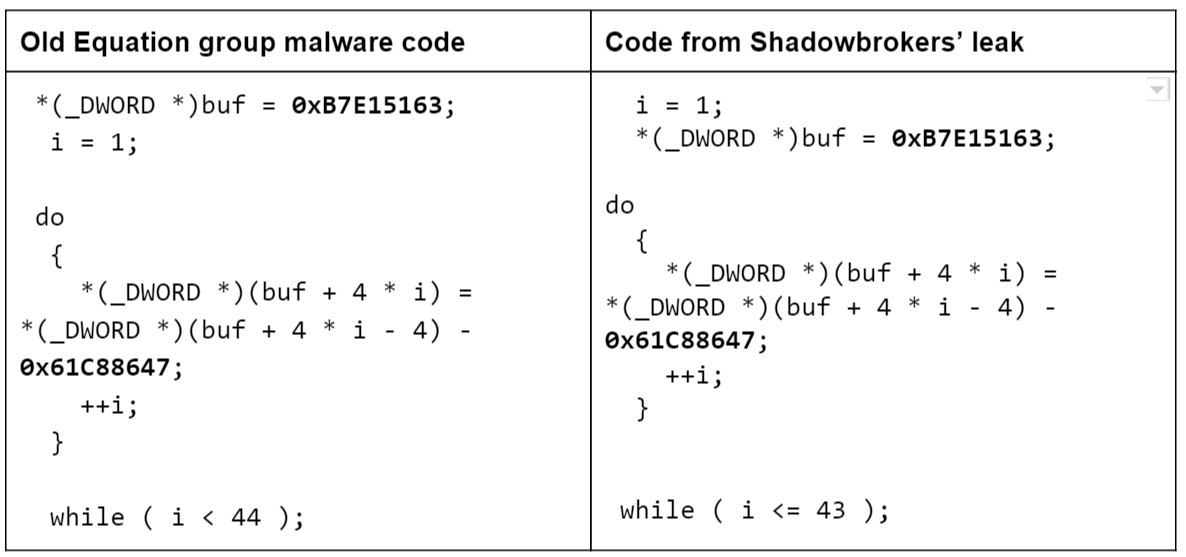
The Equation group makes extensive use of RC5 and RC6 encryption algorithms (these algorithms were designed by Ronald Rivest in 1994 and 1998 respectively). The free trove provided by ShadowBrokers includes 347 different instances of RC5 and RC6 implementations. The implementation is functionally identical with that found in the Equation malware – and has not been seen elsewhere.
The code similarity makes us believe with a high degree of confidence that the tools from the ShadowBrokers leak are related to the malware from the Equation group.
Operation Ghoul
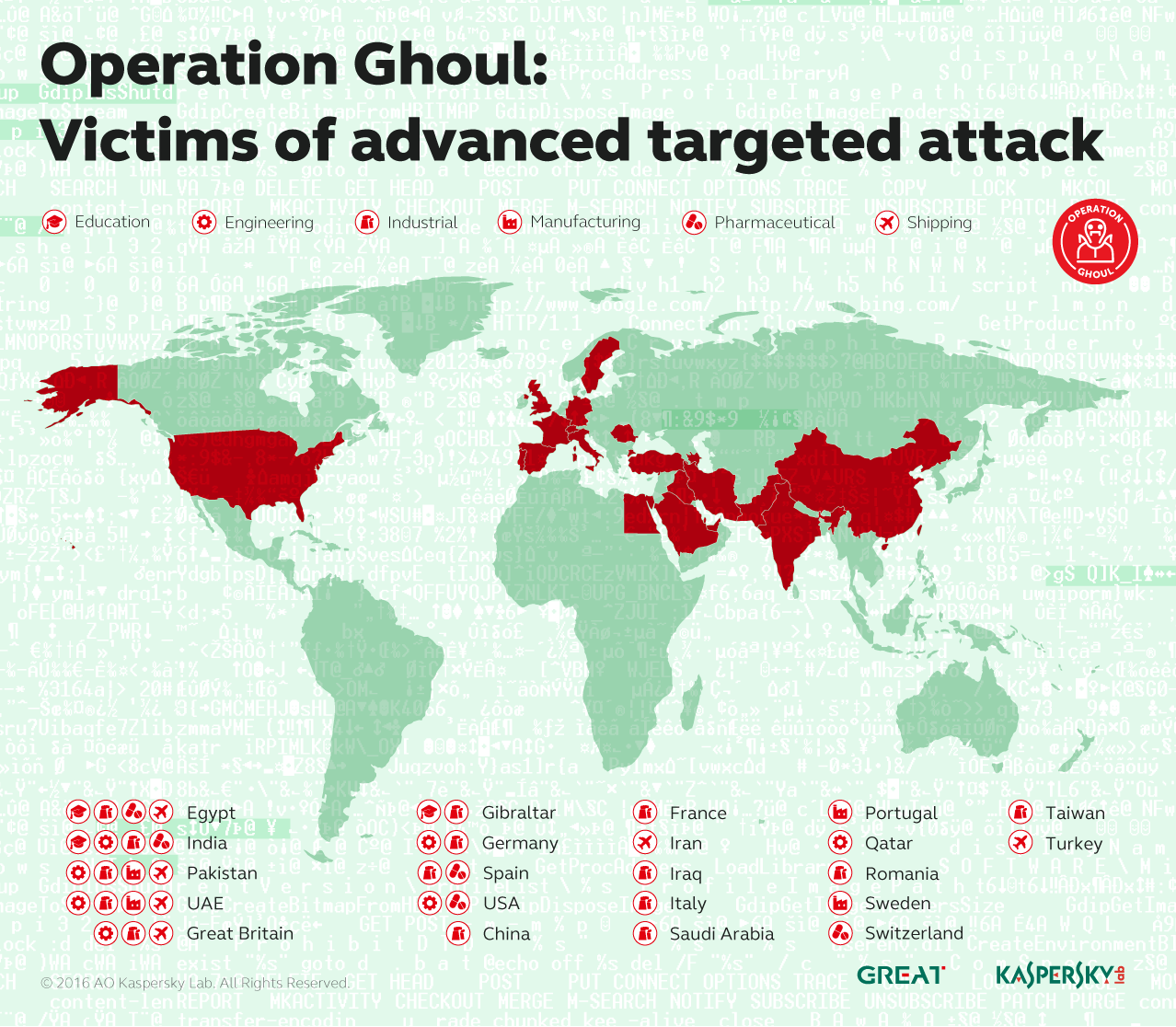
In June, we noticed a wave of spear-phishing e-mails with malicious attachments. The messages, sent mainly to top and middle level managers of numerous companies, appeared to be coming from a bank in the UAE. The messages claimed to offer payment advice from the bank and included an attached SWIFT document. But the archive really contained malware. Further investigation revealed that the June attacks were the most recent operation of a group that researchers had been tracking for more than a year, named Operation Ghoul by Kaspersky Lab.
The group successfully attacked more than 130 organizations from 30 countries, including Spain, Pakistan, UAE, India, Egypt, the United Kingdom, Germany and Saudi Arabia. Based on information obtained from the sink-hole of some C2 servers, the majority of the target organizations work in the industrial and engineering sectors. Others include shipping, pharmaceutical, manufacturing, trading and educational organizations.
The malware used by the Operation Ghoul group is based on the commercial spyware kit Hawkeye, sold openly on the Dark Web. Once installed, the malware collects interesting data from the victim’s computer, including keystrokes, clipboard data, FTP server credentials, account data from browsers, messaging clients, e-mail clients and information about installed applications. This data is sent to the group’s C2 servers.
The aim of the campaign seems to be financial profit – all the targeted organizations hold valuable data that can be sold on the black market.
The continued success of social engineering as a way of gaining a foothold in target organizations highlights the need for businesses to make staff awareness and education a central component of their security strategy.
Malware stories
Lurk
In June 2016 we reported on the Lurk banking Trojan, used to systematically siphon money from the accounts of commercial organizations in Russia – among them, a number of banks. The police estimate the losses caused by this Trojan at around $45 million.
During our research into this Trojan, it became apparent that victims of Lurk had also installed the remote administration software, Ammyy Admin. While we didn’t give it much thought at first, it became apparent that the official Ammyy Admin website had been compromised and was being used by the Lurk gang as part of a watering-hole attack: the Trojan was downloaded to victim’s computers along with the legitimate software.
The dropper on the Ammyy Admin site started distributing a different Trojan on 1 June 2016, ‘Trojan-PSW.Win32.Fareit’: this was the day that the alleged creators of the Lurk Trojan were arrested. It seems that those responsible for the Ammyy Admin website breach were happy to sell their Trojan dropper to anyone who wanted to distribute malware from the compromised site.
The banking Trojan wasn’t the only cybercriminal activity the Lurk group was involved in. The group also developed the Angler exploit kit, a set of malicious programs designed to exploit vulnerabilities in widespread software to install malware. This exploit kit was originally developed to provide a reliable and effective delivery channel for the group’s malware. However, in 2013 the group started to rent out the kit to anyone who was willing to pay for it – probably to help pay for the group’s huge network infrastructure and large number of ‘staff’. The Angler exploit kit became one of the most powerful tools available on the criminal underground. Unlike the Lurk banking Trojan, which focused on victims in Russia, Angler has been used by attackers across the world – including the groups behind the CryptXXX and TeslaCrypt ransomware and the Neverquest banking Trojan (the latter was used against almost 100 banks). The operations of Angler were disrupted after the arrest of the alleged members of the Lurk group.
In Q3 2016, 45.2M unique malicious URLs were recognized by @kaspersky web antivirus components #KLreport #IT
Tweet
The group was involved in other side activities too. For more than five years, the group moved from developing very powerful malware for automated money theft with Remote Banking Services software, to sophisticated theft involving SIM-card swap fraud, to becoming hacking specialists familiar with the internal infrastructure of banks.
Kaspersky Lab provided assistance to the Russian police in the investigation into the group behind the Lurk Trojan. The arrests marked the culmination of a six-year investigation by our Computer Incidents Investigation Team. You can read about the investigation here.
Ransomware
Hardly a month goes by without reports of ransomware attacks in the media: for example, a recent report suggested that 28 NHS trusts in the UK have fallen victim to ransomware in the last 12 months. Most ransomware attacks are directed at consumers, but a significant proportion target businesses (around 13 per cent in 2015-16). The Kaspersky Lab IT Security Risks Survey 2016 indicated that around 42 per cent of small and medium businesses became victims of ransomware in the 12 months up to August 2016.
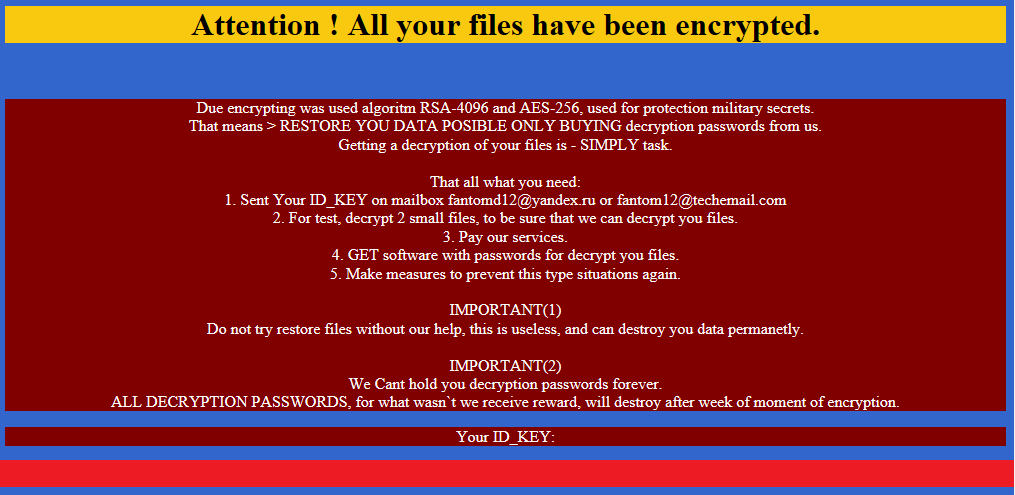
One recent ransomware campaign demanded a massive two bitcoins (around $1,300) as a ransom. The ransomware program, named Ded Cryptor, changes the wallpaper on the victim’s computer to a picture of an evil-looking Santa Claus.
The modus operandi of this program (i.e. encrypted files, scary image, and ransom demand) is unremarkable, but the pre-history of this attack is interesting. It is based on the EDA2 open-source ransomware code, developed by Utku Sen as part of a failed experiment. Utku Sen, a security expert from Turkey, created a ransomware program and published the code online. He realized that cybercriminals would use the code to create their own cryptors, but hoped that this would help security researchers to understand how cybercriminals think and code, thereby making their own efforts to block ransomware more effective.
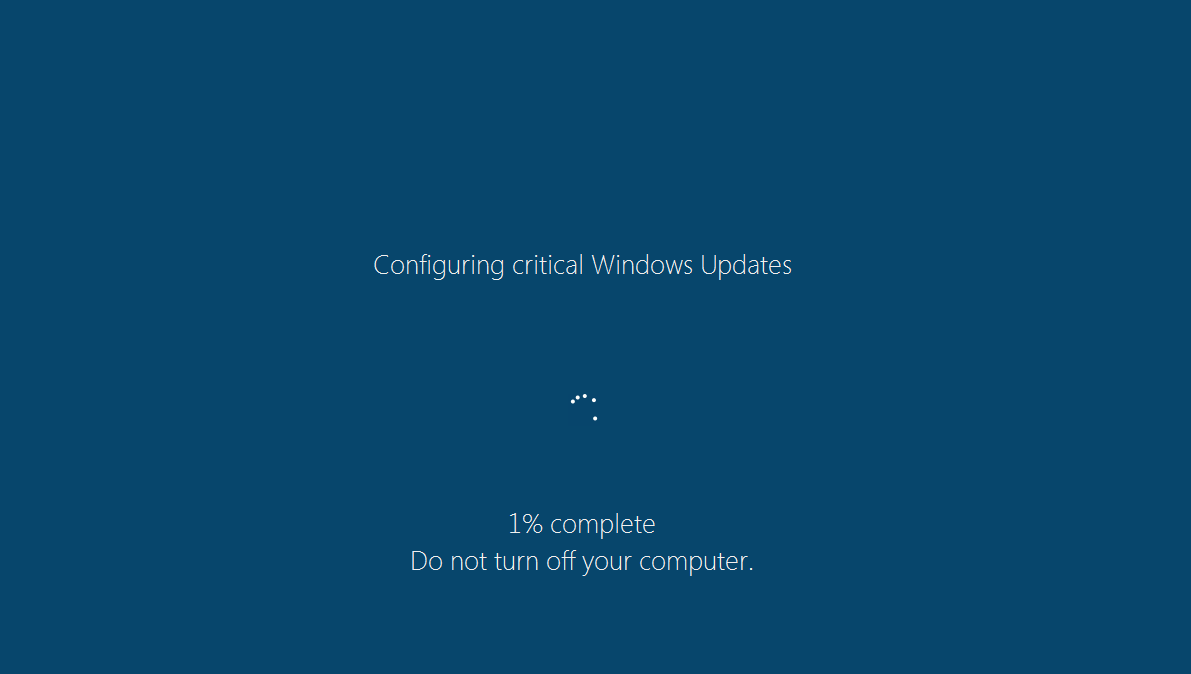
Ded Cryptor was just one of many ransomware programs spawned by EDA2. Another such program that we saw recently was Fantom. This was interesting not just because of its connection to EDA2, but because it simulates a genuine-looking Windows update screen
This is displayed while Fantom is encrypting the victim’s files in the background. The fake update program runs in full-screen mode, visually blocking access to other programs and distracting the victim from what’s really happening. Once the encryption has been completed, Fantom displays a more typical message.
There’s no doubt that public awareness of the problem is growing, but it’s clear that consumers and organizations alike are not doing enough to combat the threat; and cybercriminals are capitalising on this – this is clearly reflected in the growing number of ransomware attacks.
It’s important to reduce your exposure to ransomware (and we’ve outlined important steps you can take here and here). However, there’s no such thing as 100 per cent security, so it’s also important to mitigate the risk. In particular, it’s vital to ensure that you have a backup, to avoid facing a situation where the only choices are to pay the cybercriminals or lose your data. It’s never advisable to pay the ransom.
In Q3 2016, @kaspersky web #antivirus detected 12,657,673 unique malicious objects #KLreport #netsec
Tweet
If you do find yourself in a situation where your files are encrypted and you don’t have a backup, ask your anti-malware vendor if they can help and check the No More Ransom website, to see if it holds the keys to decrypt your data. This is a joint initiative by the National High Tech Crime Unit of the Netherlands’ police, Europol’s European Cybercrime Centre, Kaspersky Lab and Intel Security – designed to help victims of ransomware retrieve their encrypted data without paying cybercriminals.
In a recent ‘ask the expert‘ session, Jornt van der Wiel, an expert from Kaspersky Lab’s Global Research and Analysis Team, provided useful insights into ransomware.
Data breaches
Personal information is a valuable commodity, so it’s no surprise that cybercriminals target online providers, looking for ways to bulk-steal data in a single attack. We’ve become accustomed to the steady stream of security breaches reported in the media. This quarter has been no exception, with data leaks from the official forum of DotA 2, Yahoo and others.
Some of these attacks resulted in the theft of huge amounts of data, highlighting the fact that many companies are failing to take adequate steps to defend themselves. Any organization that holds personal data has a duty of care to secure it effectively. This includes hashing and salting customer passwords and encrypting other sensitive data.
Consumers can limit the damage of a security breach at an online provider by ensuring that they choose passwords that are unique and complex: an ideal password is at least 15 characters long and consists of a mixture of letters, numbers and symbols from the entire keyboard. As an alternative, people can use a password manager application to handle all this for them automatically.
It’s also a good idea to use two-factor authentication, where an online provider offers this feature – requiring customers to enter a code generated by a hardware token, or one sent to a mobile device, in order to access a site, or at least in order to make changes to account settings.
Given the potential impact of a security breach, it’s hardly surprising to see regulatory authorities paying closer attention to the issue. The UK Information Commissioner’s Office (ICO) recently issued a record fine of £400,000 to Talk Talk for the company’s ‘failure to implement the most basic cyber security measures’, related to the attack on the company in October 2015. In the view of the ICO, the record fine ‘acts as a warning to others that cyber security is not an IT issue, it is a boardroom issue’.
The EU General Data Protection Regulation (GDPR), which comes into force in May 2018, will require companies to notify the regulator of data breaches, with significant fines for failure to secure personal data. You can find an overview of the regulation here.
We took a look back at the impact of the Ashley Madison breach, one year after the attack that led to the leak of customer data, offering some good tips to anyone who might be considering looking online for love (and good advice for managing any online account).


















IT threat evolution Q3 2016