IT threat evolution Q1 2024
IT threat evolution Q1 2024. Mobile statistics
IT threat evolution Q1 2024. Non-mobile statistics
Quarterly figures
According to Kaspersky Security Network, in Q1 2024:
- 10.1 million attacks using malware, adware, or unwanted mobile software were blocked.
- The most common threat to mobile devices was adware: 46% of all threats detected.
- Over 389,000 malicious installation packages were detected, of which:
- 11,729 packages were related to mobile banking Trojans,
- 1,990 packages were mobile ransomware Trojans.
Quarterly highlights
The number of attacks using malware, adware, or unwanted software on mobile devices increased compared to the same period last year, but dropped slightly against Q4, to 10,100,510.
Number of attacks targeting users of Kaspersky mobile solutions, Q3 2022–Q1 2024 (download)
The rapid growth in the total number of attacks between Q2 and Q4 2023 is primarily attributed to the surge in adware and Trojan activity, which roughly doubled in absolute terms during this period. However, other types of malicious and unwanted apps also increased their activity, so the distribution of threats by type showed no dramatic swings.
In Q1, the number of WhatsApp modification attacks continued to grow. For example, we found Trojan-Spy.AndroidOS.Agent.ahu, a Trojan hidden inside a WhatsApp mod, that steals encrypted messenger databases along with their decryption keys. Another malicious WhatsApp mod, Trojan-Downloader.AndroidOS.Agent.ms, is capable of downloading and installing arbitrary software. According to our statistics, this Trojan came pre-installed on some devices.
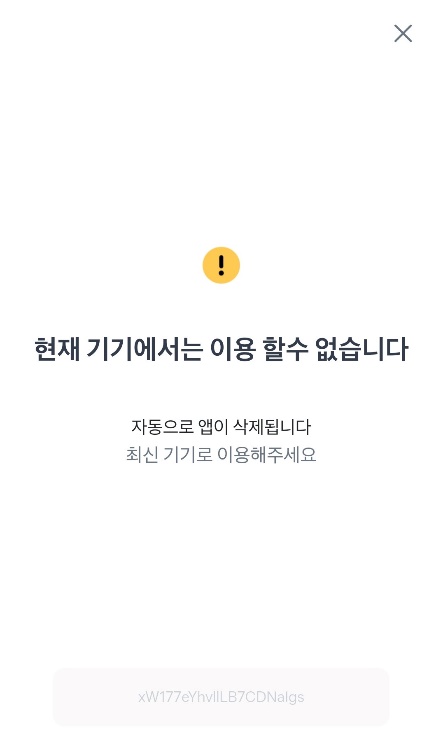
We also discovered a noteworthy banking Trojan targeting users in Korea. When installed, it displays a notification claiming the app is unavailable and will be removed:
In reality, the app hides its icon and continues to operate in the background, stealing text messages, contacts, photos, and even online banking digital certificates. To conceal the malicious code and hinder analysis, threat actors exploited numerous bugs and flaws in the Android OS code responsible for parsing the app package. This enabled them to create files that successfully install on the device, but cause many analysis tools, including official Google utilities, to go haywire.
Mobile threat statistics
The number of detected samples of Android malware and unwanted software fell in Q4 2023 and climbed again in Q1 2024, reaching 389,178 installation packages.
Number of detected malicious and unwanted installation packages, Q1 2023 – Q1 2024 (download)
The distribution of detected packages by type underwent no significant changes, but the number of Trojan droppers increased noticeably (by 8.76 p.p.). This sharp increase in their share is linked primarily to the activity of the Wroba family, commonly employed to deliver banking Trojans in countries in the Asia-Pacific region.
Distribution of detected mobile apps by type, Q4 2023* and Q1 2024 (download)
* Data for the previous quarter may differ slightly from previously published data due to some verdicts being retrospectively revised.
The most common threats remained adware (46.16%) and RiskTool-type unwanted apps (21.27%). The most prevalent adware families were BrowserAd (28.5% of all adware), Adlo (15.3%), and HiddenAd (12.65%).
Share* of users attacked by the given type of malicious or unwanted software out of all targeted users of Kaspersky mobile products (download)
*The sum may exceed 100% if the same users encountered multiple attack types.
The HiddenAd (60.5%), Adlo (17.5%), and TimeWaste (7.5%) adware families attacked the most users. At the same time, the Triada adware Trojan, mentioned in our previous report and distributed in WhatsApp mods, accounts for an increasingly large share of attacks by Trojan-type malware (35.7%).
Top 20 mobile malware programs
Note that the malware rankings below exclude riskware or potentially unwanted software, such as RiskTool or adware.
| Verdict | %* in Q4 2023 | %* in Q1 2024 | Difference in p.p. | Change in ranking |
| Trojan.AndroidOS.Triada.fd | 2.79 | 10.38 | +7.59 | +11 |
| DangerousObject.Multi.Generic. | 8.76 | 9.82 | +1.07 | 0 |
| Trojan.AndroidOS.Fakemoney.v | 6.25 | 8.60 | +2.35 | +1 |
| Trojan.AndroidOS.Boogr.gsh | 5.28 | 6.62 | +1.34 | +2 |
| Trojan.AndroidOS.Triada.ga | 0.00 | 5.66 | +5.66 | |
| Trojan-Downloader.AndroidOS.Dwphon.a | 1.85 | 5.26 | +3.41 | +13 |
| Trojan.AndroidOS.Fakemoney.bj | 0.00 | 4.26 | +4.26 | |
| DangerousObject.AndroidOS.GenericML. | 1.99 | 3.83 | +1.84 | +9 |
| Trojan-Spy.AndroidOS.SpyNote.bz | 1.03 | 3.52 | +2.48 | +18 |
| Trojan.AndroidOS.Sheetfit.d | 0.00 | 2.42 | +2.42 | |
| Trojan.AndroidOS.Triada.ex | 7.23 | 2.42 | -4.81 | -8 |
| Trojan-Downloader.AndroidOS.Agent.mm | 3.51 | 2.12 | -1.39 | -1 |
| Trojan-Dropper.AndroidOS.Agent.sm | 1.08 | 2.09 | +1.01 | +13 |
| Trojan.AndroidOS.Generic. | 2.22 | 2.08 | -0.14 | +2 |
| Trojan.AndroidOS.Piom.baiu | 0.80 | 1.95 | +1.15 | +16 |
| Trojan-Dropper.AndroidOS.Badpack.g | 2.57 | 1.87 | -0.70 | -3 |
| Backdoor.AndroidOS.Mirai.b | 5.32 | 1.76 | -3.56 | -12 |
| Trojan-Spy.AndroidOS.CanesSpy.a | 5.10 | 1.67 | -3.42 | -11 |
| Trojan.AndroidOS.Triada.et | 3.58 | 1.66 | -1.92 | -9 |
| Trojan.AndroidOS.Triada.ey | 4.33 | 1.55 | -2.79 | -11 |
* Unique users who encountered this malware as a percentage of all attacked users of Kaspersky mobile solutions.
The generalized cloud verdict DangerousObject.Multi.Generic yielded the top spot in the ranking of the most common malicious apps to the WhatsApp modification Trojan.AndroidOS.Triada.fd. Next comes Fakemoney, a Trojan that scams users out of personal data by promising easy money in return. Interestingly, Dwphon also made it into the Top 20. Pre-installed on some devices, this Trojan collects the personal data of the device owner and can download arbitrary apps without the user’s knowledge.
Region-specific malware
This section describes malware whose activity is concentrated in specific countries.
| Verdict | Country* | %* |
| Trojan-Banker.AndroidOS.Agent.nw | Turkey | 99.79 |
| Trojan.AndroidOS.Piom.bcqp | Turkey | 99.28 |
| Trojan-Banker.AndroidOS.BrowBot.q | Turkey | 99.28 |
| Trojan-Spy.AndroidOS.SmsThief.wk | India | 99.02 |
| Trojan.AndroidOS.Piom.bbfv | Turkey | 98.97 |
| Trojan-Banker.AndroidOS.BrowBot.a | Turkey | 98.81 |
| Trojan.AndroidOS.Piom.azgy | Brazil | 98.69 |
| HackTool.AndroidOS.FakePay.c | Brazil | 98.39 |
| Trojan-Banker.AndroidOS.Coper.b | Turkey | 98.28 |
| Trojan-Banker.AndroidOS.BrowBot.n | Turkey | 97.87 |
| Trojan-SMS.AndroidOS.EvilInst.b | Thailand | 97.33 |
| Backdoor.AndroidOS.Tambir.c | Turkey | 97.19 |
| Trojan-Banker.AndroidOS.BRats.b | Brazil | 96.96 |
| Trojan-Spy.AndroidOS.SmsThief.tt | Iran | 96.88 |
| Trojan-Banker.AndroidOS.Rewardsteal.dn | India | 96.76 |
| Trojan-Banker.AndroidOS.Rewardsteal.c | India | 96.65 |
| Backdoor.AndroidOS.Tambir.a | Turkey | 96.58 |
| Trojan-Dropper.AndroidOS.Hqwar.hc | Turkey | 96.19 |
| Trojan-Banker.AndroidOS.UdangaSteal.b | Indonesia | 96.04 |
| Backdoor.AndroidOS.Tambir.b | Turkey | 95.55 |
| Trojan-Spy.AndroidOS.SmsThief.vb | Indonesia | 95.29 |
* The country where the malware was most active.
** Unique users who encountered this Trojan modification in the indicated country as a percentage of all Kaspersky mobile security solution users attacked by the same modification.
Turkey continues to be flooded with banking Trojan variants. In particular, users there are targeted by Trojan-Banker.AndroidOS.Agent.nw, which opens VNC access to the device. It’s based on the open-source library droidVNC-NG. Tambir also gives attackers VNC access. In addition, its functionality includes keylogging, stealing texts, contacts, and app lists, as well as sending texts. Besides VNC backdoors, we observed a concentration of BrowBot attacks in Turkey. The primary functionality of that Trojan is stealing texts. As for Piom, it represents a collective verdict created for various malware within the context of our automated systems. Specifically in Turkey, hiding behind this verdict are modifications of the now infamous Godfather banking Trojan.
Two text-stealing Trojans are active in Indonesia: SmsThief.vb and UdangaSteal.b. They are often sent to victims under the guise of wedding invitations.
The spread of FakePay applications is noticeable in Brazil. These applications visually simulate payment but do not actually execute it. Unlike most Trojans, users often intentionally download such apps in order to deceive sellers who accept payment by transfer. BRats is another banking Trojan that continues to be distributed predominantly in Brazil.
Users in Thailand encountered the EvilInst Trojan, which spreads under the guise of games but in fact, just opens a website with cracked games and sends paid texts.
Mobile banking Trojans
The number of new unique installation packages for banking Trojans remains low.
Number of installation packages for mobile banking Trojans detected by Kaspersky, Q1 2023 — Q1 2024 (download)
Nevertheless, the total number of Trojan-Banker attacks continues to grow, with Trojan-Banker even moving up one spot in the distribution structure of malware and unwanted programs by the number of affected users.
Top 10 mobile bankers
| Verdict | %* in Q4 2203 | %* in Q1 2024 | Difference in p.p. | Change in ranking |
| Trojan-Banker.AndroidOS.Agent.eq | 27.73 | 13.39 | -14.34 | 0 |
| Trojan-Banker.AndroidOS.Coper.b | 3.72 | 12.58 | +8.86 | +3 |
| Trojan-Banker.AndroidOS.Bian.h | 16.06 | 10.21 | -5.85 | -1 |
| Trojan-Banker.AndroidOS.Mamont.k | 2.48 | 9.18 | +6.70 | +5 |
| Trojan-Banker.AndroidOS.UdangaSteal.b | 0.00 | 7.00 | +7.00 | |
| Trojan-Banker.AndroidOS.Mamont.o | 0.00 | 4.58 | +4.58 | |
| Trojan-Banker.AndroidOS.Agent.cf | 2.79 | 4.23 | +1.44 | 0 |
| Trojan-Banker.AndroidOS.Coper.a | 0.65 | 4.21 | +3.56 | +19 |
| Trojan-Banker.AndroidOS.Rewardsteal.c | 0.55 | 3.99 | +3.45 | +20 |
| Trojan-Banker.AndroidOS.BrowBot.q | 0.00 | 2.53 | +2.53 |
* Unique users who encountered this malware as a percentage of all users of Kaspersky mobile security solutions who encountered banking threats.
Mobile ransomware Trojans
Following a surge in the number of ransomware installation packages in Q4 2023, linked to the emergence of a large number of ransomware from the Rasket family, the number returned to its usual level amid a decrease in Rasket activity. Rasket Trojans are built on Tasker automation scripts, which are designed to automate routine actions on a device but have sufficient functionality to write ransomware.
Number of installation packages for mobile ransomware Trojans detected by Kaspersky, Q1 2023 — Q1 2024 (download)
The same dynamic is reflected in the distribution of attacks for the most active samples: after a sharp rise (to 74% of all ransomware attacks), the share of the Rasket Trojan in Q1 almost halved.
| Verdict | Prev % | New % | % diff | Pos diff |
| Trojan-Ransom.AndroidOS.Rasket.a | 74.38 | 37.22 | -37.16 | 0 |
| Trojan-Ransom.AndroidOS.Pigetrl.a | 9.14 | 15.56 | +6.41 | 0 |
| Trojan-Ransom.AndroidOS.Rkor.eg | 5.29 | 11.59 | +6.30 | 0 |
| Trojan-Ransom.AndroidOS.Svpeng.ac | 0.22 | 11.17 | +10.95 | +19 |
| Trojan-Ransom.AndroidOS.Congur.cw | 0.51 | 10.96 | +10.45 | +2 |
| Trojan-Ransom.AndroidOS.Small.cj | 0.30 | 10.49 | +10.19 | +9 |
| Trojan-Ransom.AndroidOS.Congur.ap | 0.28 | 6.66 | +6.38 | +9 |
| Trojan-Ransom.AndroidOS.Rkor.ef | 2.00 | 6.40 | +4.40 | -4 |
| Trojan-Ransom.AndroidOS.Svpeng.ah | 0.12 | 6.03 | +5.91 | +34 |
| Trojan-Ransom.AndroidOS.Svpeng.snt | 0.07 | 5.72 | +5.64 | +47 |


















IT threat evolution in Q1 2024. Mobile statistics