
Overview
Botnets reloaded
Today, botnets are one of the principal technologies used by cybercriminals. Botnet technologies have been developing for several years, giving rise to decentralized botnets and botnets managed via social networks, with drive-by downloads becoming the principal method of infection. In this respect, 2011 was a relatively uneventful year and cybercriminals came up with nothing radically new. But everything changed in early 2012.
In Q1 2012, cybercriminals created a botnet using a ‘fileless’ bot for the first time. Security researchers discovered a mobile botnet that was comparable in size with typical Windows botnets, as well as a botnet of more than half a million Apple computers running Mac OSX.
The invisible bot
In Q1 2012, we discovered a botnet created using a new technology: the botmaster used a ‘fileless’ bot. This malware belongs to a very rare breed of malicious programs which exist only in the computer’s RAM.
The problem manifested itself in anomalies on infected computers: they began sending network requests to third-party resources after visiting some popular Russian websites, then in some cases encrypted files appeared on their hard drives. At the same time, no new executable files appeared on hard drives. Further analysis helped to identify the entire chain involved in infecting computers and creating the botnet, which was far from trivial.
In the first stage, a computer was infected via a drive-by attack using a Java exploit for the CVE-2011-3544 vulnerability. The link, which redirected users to the website containing the exploit, was inserted in a teaser ad displayed on news sites. The teaser ad was distributed via AdFox, a Russian banner network.
After successfully exploiting the vulnerability, the exploit injected a malicious DLL directly into the memory of the Java process instead of downloading the malicious file to the hard drive. After being successfully injected and launched, the malware acted on behalf of the Java process, collecting information on the sites visited by the user. If these included bank-related resources, then the Lurk Trojan, which targets users’ online-banking credentials, was installed on the computer.
Thanks to the professional actions of Kaspersky Lab experts, AdFox staff and a researcher who chose to remain anonymous, the infection has been curbed.
Although the malicious process remained in RAM only until the operating system was restarted, the infection spread via popular websites. The cybercriminals were able to infect computers each day, thereby maintaining the bot population. It is worth noting that virtually no traces of the infection or of data collection remained on the computer’s hard drive after the operating system was restarted.
In this incident, two familiar technologies – exploitation of vulnerabilities and injection into a legitimate process without saving a file on the hard drive – were combined in a single piece of dangerous malware. Whenever a ‘fileless’ bot is used, it is very difficult to identify the computers that make up the botnet, since no new executable files appear on the hard drive and the cybercriminals perform all their actions on behalf of Java, which is a legitimate process. Although patching is effective against this and similar threats, some users fail to patch their systems on a timely basis. This means that we may yet come across similar malware in the future, though not on a mass scale: this is, after all, rather sophisticated.
Mobile botnet
In our Q3 2011 report, we mentioned that malware developers for mobile devices had selected Android OS as their platform of choice. In Q1 2012, we detected over 5,000 (5,444) malicious programs for the platform. The total number of malicious programs targeting Android has increased ninefold in the past six months.
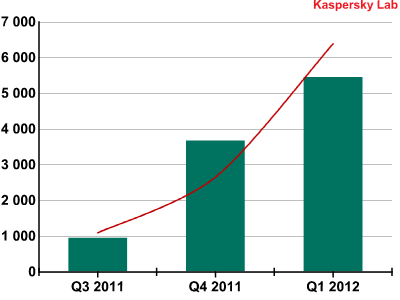
Number of malware modifications for Android OS
Malware writers from China and Russia show the greatest interest in malicious programs for Android. Chinese malware writers have managed to create a botnet with 10,000 to 30,000 active devices and the total number of infected smartphones is in the hundreds of thousands.
The botnet was created using the RootSmart backdoor, which has extensive functionality related to remotely controlling Android phones and tablets. RootSmart is distributed using a proven method: the malware writers have re-packed a legitimate program and uploaded it to the website of an unofficial Android application store that is very popular in China. As a result, people who downloaded the program to help them set up their phones also received a backdoor that made their devices part of the botnet.
The scope of the RootSmart infection means that the attackers have been able to profit from the mobile-phone botnet. They chose the most popular method used by mobile cybercriminals: sending paid SMS messages to premium numbers. But why gain full control of the device if the bot’s main function is to send premium SMS messages? It’s simple: full control allows the attackers to hide the presence of malware on the phone over extended periods of time, letting them syphon money from each user’s account for longer.
Important lessons can be learned from the story of the first large botnet made up of mobile devices.
First, since updates of mobile operating systems are not released very often, attackers can keep using the same exploits for months, because they will work on most devices.
Second, since installing antivirus software on mobile devices has not become common practice, many people use their devices without even suspecting that they have long been infected, allowing botmasters to keep the devices at their disposal.
So far, the situation has not changed significantly, and it is very likely that we will hear of much larger mobile botnets than RootSmart this year.
Mac botnet
Another botnet to have attracted the attention of experts in Q1 was the zombie network built of Mac OS X computers.
Kaspersky Lab detects the Trojan used to build the botnet as Trojan-Downloader.OSX.Flashfake. We published analyses of this malware last year, as well as this year.
The first versions of Flashfake appeared last autumn. The developers of the malware took steps to ensure its presence was harder to detect (they made sure that the Trojan was not installed on computers with protection installed, programmed bots to disable updates of the built-in protection system Mac OS X Xprotect, etc.). Later, we saw that cybercriminals were experimenting with new ways of controlling botnets. For example, some Flashfake versions used Twitter accounts created by the cybercriminals as command servers.
A bot’s main purpose is to download and launch additional modules without the user’s knowledge. The attackers made money by generating fake search-engine results: an additional module was designed to replace links in the results of popular search queries. The attackers can obviously use other modules, as well, e.g. to steal data from infected computers.
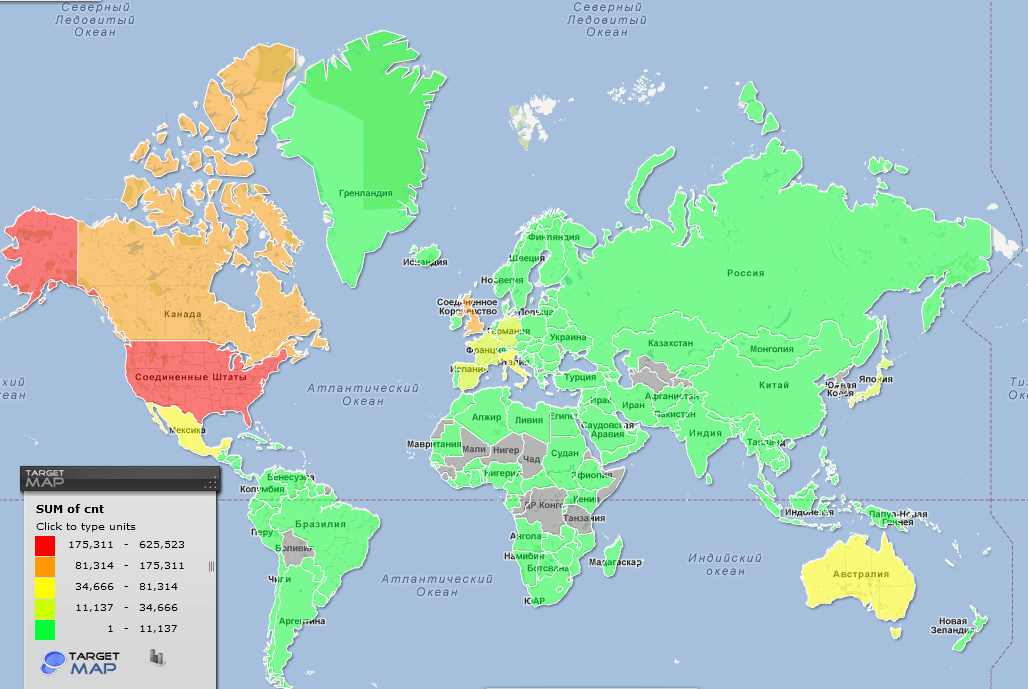
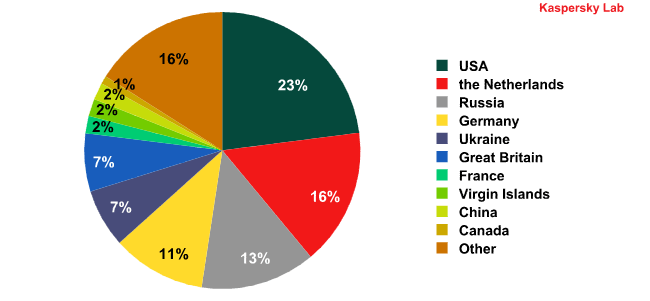
In March 2012, Flashback infected about 700,000 computers across the globe.
Geographical distribution of computers infected by Trojan-Downloader.OSX.FlashFake,
Kaspersky Lab data, Q1 2012
The attackers used a Java exploit to distribute the malware. Importantly, Oracle cannot update Java on Mac OS X computers automatically. Users have to wait for Apple to release an update, which sometimes takes several months. As a result, the time period during which cybercriminals can use an exploit to infect Macs is significantly longer than in the case of Windows. Apple only released the patch closing the vulnerability that was exploited to spread Flashback in early April, even though Oracle made its own patch available back in February.
The number of attacks on Mac OS X machines based on exploiting zero-day vulnerabilities is set to grow. Most vulnerable applications that are popular among cybercriminals are cross-platform, i.e. they work both under Windows and under Mac OS X. This makes creating exploits for Mac OS X easier.
The growing interest in the Apple platform on the part of cybercriminals is confirmed by Kaspersky Lab statistics on detections of new malware versions targeting Mac OS X:
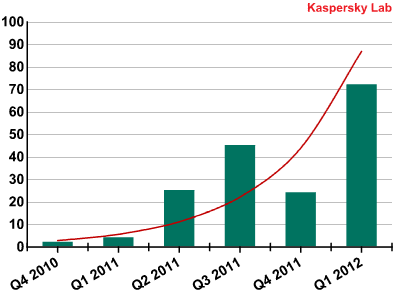
Number of new malware records for the Mac OS X platform added to Kaspersky Lab’s antivirus databases
The main reason for the growth in the amount of malware targeting Mac OS X is the growing popularity of the platform among users. Although the number of malicious programs for Mac OS X is currently significantly smaller than that of malware for Windows, it is obvious that cybercriminals are seriously interested in the Mac platform. This means that users should take care to follow the basic security rules.
This quarter, the story of Mac malware does not end with mass infections. We have discovered instances of malware for the platform being used in targeted attacks – another type of attack that is playing a significant role in today’s cybercriminal ecosystem.
Targeted attacks
Unfortunately, the number of users falling victim to targeted attacks continues to grow. While companies are now taking the problem seriously, this is prompting cybercriminals to develop new attack vectors.
‘Hello’.
Mac OS X + APT (advanced persistent threat)
Many users of the Mac OS X platform still view it as absolutely safe, primarily because Apple has assured them for many years that the system is more secure than PCs. However, recent analysis has challenged that assertion. There are significant numbers of Mac users in corporate environments as well as in state organizations. Every day they work with lots of important documents, and in most cases their computers are not protected by an antivirus solution.
Targeted attacks on organizations ought to serve as wake-up call for these users. Cybercriminals will attempt to gain access to secret documentation by simultaneously using two Trojans – one for Mac and another for Windows. The appropriate malicious program is loaded to the targeted computer depending on which operating system it is running. Both the Mac and Windows malware receive commands from the same C&C server.
In order to penetrate the system in the first place, an exploit of the CVE-2011-3544 vulnerability in Java is used. This works just as well on a Mac OS X platform as it does on Windows. A successful attack saw Mac OS X systems infected with Backdoor.OSX.Lasyr. This backdoor allows cybercriminals to gain control of an infected machine and get access to all the information on the computer. It was detected in mid-March 2012.
This was not the only case of targeted attacks using Mac malware in the first quarter of 2012. The second case involved only a backdoor for Mac OS X – Backdoor.OSX.MaControl. An exploit was also used to carry out the initial infection, but this time it targeted a vulnerability in Microsoft Office, which is popular on all platforms. The method of delivering the exploit was entirely conventional – it came in an email. To infect an employee’s computer with the backdoor, the .doc file attached to the message simply needed to be opened by the recipient.
Malware for targeted attacks on Mac OS X platforms obviously isn’t difficult for cybercriminals to develop considering the speed with which the programs are appearing. The lack of concern shown by many Mac users about the risks, combined with the absence of anti-malware solutions on their computers, make Macintosh the weakest link in an organization’s security system.
Duqu is back
After a four-month break the authors of Duqu got back to work: in March a new driver was detected in the wild that was almost identical to previous Duqu drivers. The earlier drivers were created on 3 November 2010 and 17 October 2011, while the latest driver dates to 23 February 2012.
The functionality of the new driver is consistent with that of previous versions. The code contains only minor modifications that were made to evade detection by antivirus programs. The main Duqu module associated with the driver was not detected.
Our assumption that it won’t be that easy to shut down expensive projects like Duqu and Stuxnet turns out to be correct. Instead the cybercriminals have done what they always do – modified their code to evade detection and carried on with their attacks.
With the help of the international community of developers and researchers, we managed to determine that the Duqu Framework was written in OO C. This approach would be typical for developers of “old school” programming working on serious projects, but it is almost never used in today’s malicious programs. This is yet more evidence that Duqu, along with Stuxnet, is a unique development that stands out from other malware.
With fewer than 50 victims worldwide, Duqu remains the most mysterious Trojan ever detected. The fact that its targets are based in Iran suggests its authors have a definite plan for carrying out persistent attacks. The Trojan’s sophisticated and multi-layered protective measures underline just how important it is for this project to go unnoticed. It is quite possible that in future the Tilded platform will undergo further development to make the technology that masks and obfuscates code even more complex.
The war on cybercrime
Apart from new malware and major hacks (which we wrote about here and here), the first quarter of 2012 was also memorable for the successful joint actions of antivirus companies and law enforcement authorities. These partnerships took control over of the Hlux (Kelihos) botnet, took down the administration centers of several ZeuS botnets and arrested a gang of Russian cybercriminals.
Hlux.b – takeover 2.0
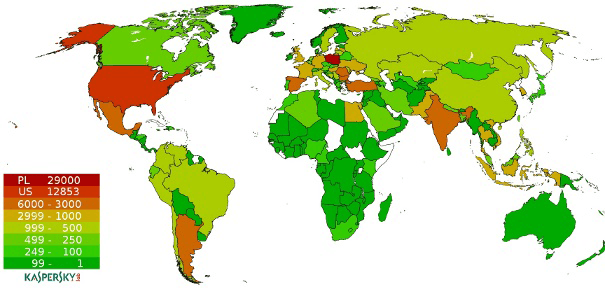
In late March 2012 Kaspersky Lab, in cooperation with CrowdStrike Intelligence Team, Dell SecureWorks and the Honeynet Project, took control of the peer-to-peer Hlux botnet based on the second variant of Hlux.b bot. At the time of the operation the botnet included over 110,000 bots.
Distribution of computers infected by Hlux.b bot (according to Kaspersky Lab, Q1 2012)
This is the second version of Hlux.b, which was detected in autumn 2011 several weeks after the first Hlux botnet was taken down. In spring 2012 a backup bot emerged much faster: the third version of the bot – Hlux.с – was detected several days after the botnet was taken over. All the new botnets modified the way their bots communicated with each other.
In terms of profitability, Hlux is a model botnet for cybercriminals. Its hosts are involved in virtually all types of cybercrime: after loading different modules the bot is able to distribute spam, participate in DDoS attacks and steal critically important information from computers. The botnet hosts will not give up their cash cow without a fight, and until these cybercriminals are captured new versions of the bot will appear every time it is taken over.
How effective is it to take over control of a botnet? From our perspective, this method is worth using. First, we disable the bots which are already installed, thus reducing the number of actively infected computers. Secondly, we make the life of cybercriminals much more difficult – they have to modify the code and distribute malware again, which is a costly business. Further takeover operations remain possible unless serious modifications are introduced into the botnet’s architecture.
Arrest of cybercriminals in Russia
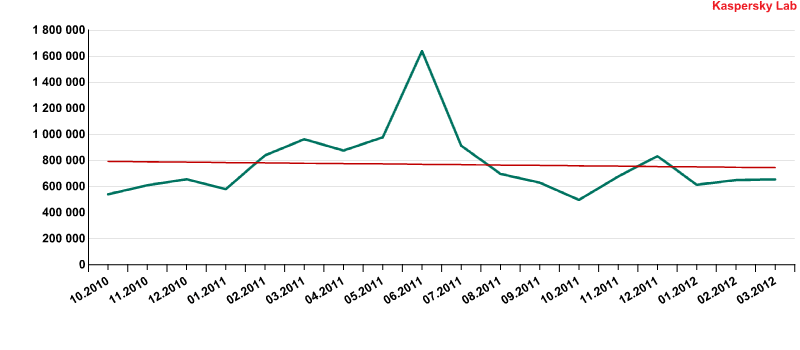
During the last three years Russia has seen the active development of Trojans targeting users of online banking systems.
Detected malicious programs aimed at stealing data from online banking systems
In Europe and Brazil cybercriminals mainly use banking Trojans to conduct attacks on home users. The characteristic feature of cybercriminals in Russia is that they actively develop malware aimed at stealing funds from the accounts of Russian businesses by manipulating Internet banking systems on accountants’ computers. Trojan-Spy.Win32.Carberp is one of the best-known examples of this type of Trojan.
On 20 March, Department К of Russia’s Ministry of Internal Affairs announced the arrests of several members of a major gang who used a pre-purchased version of Carberp Trojan to create a botnet. Several so-called mules – people who withdrew the stolen money – were also arrested. The suspects are believed to have stolen more than US$2 million. A large number of infected computers was required to steal such a large sum. Carberp was distributed via drive-by attacks: cybercriminals posted links to malicious resources on the websites of well-known Russian organizations, mass media and state services.
This announcement was very welcome, particularly in Russia, where cybercriminals are rarely arrested. In most cases, such arrests prompt other cybercriminals to reduce their activities for a while. Unfortunately, the authors of the Carberp Trojan remain at large and it is still being sold on specialized forums and distributed via hacked websites. Nevertheless, we hope that the authors of Carberp will eventually face justice.
Statistics
Here we will discuss the statistics obtained from the work of different anti-malware components. The report is based on data collected by the Kaspersky Security Network. The statistics were acquired from those KSN users who consented to share their local data. Millions of users of Kaspersky Lab products in over 200 countries take part in the global information exchange on malicious activity.
Threats on the Internet
The statistics in this section are based on the web-antivirus solution that protects users as soon as malicious code is uploaded from an infected web page. Infections can be found on web pages where users are allowed to create their own content (e.g. forums) and even on legitimate pages which have subsequently been compromised by hackers.
Malicious programs on the Internet (attacks via the web)
In the first quarter of 2012, 481,411,722 attacks from web resources located in different countries were neutralized. 95,331 unique modifications of malicious and potentially unwanted programs were detected in those incidents.
Top 20 malicious programs on the Internet
| Rank | Name* | % of all attacks** |
| 1 | Malicious URL | 84.3% |
| 2 | Trojan.Script.Iframer | 4.8% |
| 3 | Trojan.Script.Generic | 2.2% |
| 4 | Trojan-Downloader.Script.Generic | 0.5% |
| 5 | Trojan.Win32.Generic | 0.4% |
| 6 | Trojan.JS.Popupper.aw | 0.2% |
| 7 | Trojan-Spy.JS.Agent.c | 0.2% |
| 8 | Trojan-Downloader.JS.Agent.gmf | 0.2% |
| 9 | Trojan-Downloader.Win32.Agent.gyai | 0.2% |
| 10 | AdWare.Win32.Screensaver.e | 0.1% |
| 11 | Trojan-Downloader.JS.Agent.gmr | 0.1% |
| 12 | Trojan-Downloader.JS.JScript.ag | 0.1% |
| 13 | Trojan-Downloader.MSIL.Small.eq | 0.1% |
| 14 | Hoax.Win32.ArchSMS.gen | 0.1% |
| 15 | Trojan-Downloader.JS.Agent.gnk | 0.1% |
| 16 | Exploit.Script.Generic | 0.1% |
| 17 | Packed.Win32.PasswordProtectedEXE.gen | 0.1% |
| 18 | AdWare.Win32.Screensaver.i | 0.1% |
| 19 | Trojan.JS.Redirector.ue | 0.1% |
| 20 | AdWare.Win32.Shopper.lq | 0.1% |
*These statistics represent detection verdicts of the web-based antivirus module and were submitted by the users of Kaspersky Lab products who consented to share their local data.
**The total number of unique incidents recorded by web-based antivirus on user computers.
First in the rating are various malicious URLs (we previously detected them as Blocked) that are already on our denylist. Compared with the previous quarter these were down 2 percentage points to 84% of all detected problems. This list is principally filled with the websites that users are redirected to. Typically users get to these sites from hacked legitimate resources with embedded malicious scripts (a so-called drive-by attack). However, users can click on dangerous links all by themselves, for instance when looking for pirate software. Nowadays, though, the main guarantee of a successful Internet-based attack is the use of exploits targeting unpatched software: a significant proportion of malicious URL detections still come from websites related to exploit packs.
12 programs in the Top 20 exploit software vulnerabilities and are used to deliver malware to users’ computers.
Only three pieces of advertising malware – or adware – made it into the Top 20 in the first quarter of 2012. Their task is simple – after being installed on a computer (as a rule, in the guise of a browser expansion pack), they show advertisements. The amount of adware is appreciably less than in the previous quarter, when a third of the Top 20 was in this category. This indicates that cybercriminals have switched again to more harmful and more profitable categories of malware.
Vulnerable applications targeted by malicious users
Since the majority of attacks via the Internet are performed with exploits that target vulnerabilities in software to breach security and execute malicious code without the user’s knowledge, it is logical to ask which programs are usually targeted by exploits. It is strongly recommended to update these programs in the first instance, and subsequently set automatic updates in future.
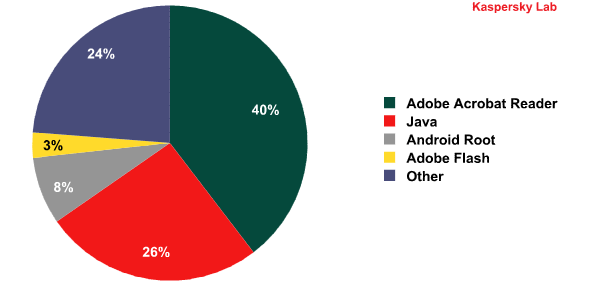
Applications with vulnerabilities targeted by online exploits in the first quarter of 2012
According to the diagram, 66% of exploit-based attacks target just two programs – Adobe Reader and Java.
Roughly one in four attacks on Java target the vulnerability CVE-2011-3544, which was popular among cybercriminals over the whole quarter: it was used for the distribution of the Hlux bot, the Carberp Trojan and a ‘fileless’ bot.
Countries where web resources are seeded with malware
In order to determine the geographical source of an attack, the domain name is compared to the actual IP address where the domain in question is located, and the geographical location of the IP address is determined (GEOIP).
In the first quarter of 2012, 84% of web resources used for malware distribution were concentrated in 10 countries – 7 percentage points higher than in the previous quarter.
Countries where web resources were seeded with malware in the first quarter of 2012
A new country entered the Top 20 as Canada ousted Romania with 0.9%. The US, the Netherlands and Russia continue to lead the table. Over the last three months the percentage of dangerous hosts located in the UK went up 4.6 percentage points to 7%, resulting in a rise of two places from 8th to 6th. The percentage of other countries did not change significantly, with all fluctuations within a range of 1 percentage point.
Countries where users run the most serious risk of infection via the Internet
In order to assess the risk of infection to which computers are exposed in any given country, we have calculated the frequency at which antivirus programs on user computers detected threats for each country during the last quarter.
20 Countries where users run the most serious risk of infection via the Internet*
*When calculating, we excluded those countries in which the number of Kaspersky Lab product users is relatively small (less than 10,000).
**The percentage of unique users in the country with computers running Kaspersky Lab products that blocked web-borne threats.
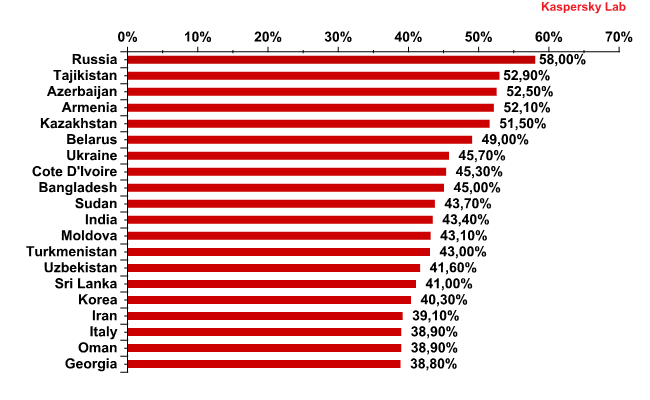
About half of the top 20 is comprised of former Soviet republics.
The countries can also be broken down into different risk groups.
- High risk. With an infection risk of 41-60%, this group consists of the first 15 countries from the Top 20, including Russia (58%), Ukraine (45.7%), Armenia (52.1%), Belarus (49%), Kazakhstan (51.5%) and India (43.3%).
- Moderate risk. 95 countries have an infection risk of 21-40% including Italy (38.9%), Turkey (36.8%), the US (31.9%), Brazil (29.3%), Spain (34.4%) and France (28.4%).
- Low risk. The safest group in Q1 2012 comprised 25 countries with the scores ranging from 11.9–20%.
The lowest Internet infection rates were recorded in Japan (14.3%), Denmark (15.2%), Taiwan (15.2%), Luxemburg (17.4%), Slovakia (19.6%) and New Zealand (20%).
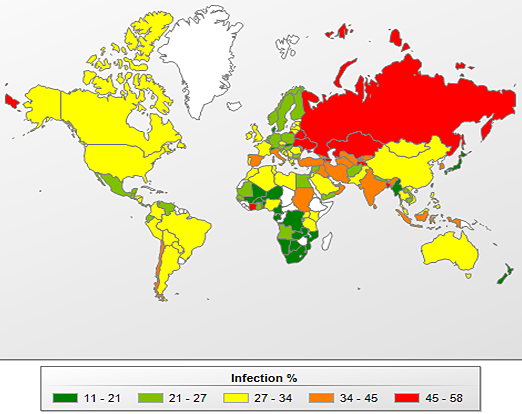
The risk of online infection around the world, Q1 2012
On average 28.8% of the computers hooked up to KSN were subjected to an attack at least once while surfing the Internet during the first quarter. Extrapolating from those figures, it suggests that one in three computers worldwide faces frequent, active threats. However, there is some good news: the proportion of computers having to fend off attacks was down 3.2 percentage points compared with the previous quarter.
Local threats
This section contains analysis of statistics based on data obtained from the on-access scanner and scanning statistics for different disks including removable media (on-demand scanner).
Objects detected on user computers
In the first quarter of 2012 our antivirus solutions successfully blocked 966,981,163 attempts at local infection on user computers participating in Kaspersky Security Network.
In total, 481,592 unique modifications of malware and potentially unwanted programs attempting to launch on user computers were detected (on-access scanner).
Objects detected on user computers: Top 20
| Rank | Name | % of individual users* |
| 1 | DangerousObject.Multi.Generic | 35.56% |
| 2 | Trojan.Win32.Generic | 31.49% |
| 3 | Trojan.Win32.Starter.yy | 13.92% |
| 4 | Virus.Win32.Sality.bh | 12.61% |
| 5 | Net-Worm.Win32.Kido.ih | 10.79% |
| 6 | Virus.Win32.Sality.aa | 9.32% |
| 7 | Trojan.Win32.AutoRun.gen | 8.71% |
| 8 | Net-Worm.Win32.Kido.ir | 8.63% |
| 9 | Hoax.Win32.ArchSMS.gen | 8.60% |
| 10 | HiddenObject.Multi.Generic | 6.58% |
| 11 | AdWare.Win32.InstallCore.gen | 6.41% |
| 12 | Virus.Win32.Generic | 6.18% |
| 13 | Virus.Win32.Nimnul.a | 5.83% |
| 14 | Worm.Win32.Generic | 5.52% |
| 15 | Trojan.WinLNK.Runner.bl | 4.56% |
| 16 | Trojan.Script.Iframer | 3.72% |
| 17 | Trojan-Dropper.VBS.Agent.bp | 3.61% |
| 18 | Virus.Win32.Sality.ag | 3.51% |
| 19 | Trojan.Script.Generic | 3.38% |
| 20 | Packed.Win32.Krap.ar | 3.26% |
These statistics are compiled from the malware detection verdicts generated by the antivirus modules of users of Kaspersky Lab products who have agreed to submit their statistical data.
* The number of individual users on whose computers the antivirus module detected these objects as a percentage of all individual users of Kaspersky Lab products on whose computers a malicious program was detected.
Top 10 threats on the Internet
At the top of the chart we see an assortment of malicious programs which were detected using ‘cloud’ technologies (35.56%). These technologies reinforce antivirus databases: when there is no signature or heuristic data to detect a specific piece of malware, an antivirus company’s cloud resources may already have data about the threat. In this case the detected object is marked as DangerousObject.Multi.Generic.
In second place is the verdict provided by the heuristic analyzer during proactive detection of numerous malicious programs – Trojan.Win32.Generic (31.49%).
Fifteenth place is occupied by Trojan.WinLNK.Runner.bl which is used to automatically launch and distribute exploits for Windows shortcuts. The first programs of this type emerged after Stuxnet was discovered and are still very popular with virus writers.
Over the past year Kido held on firmly to third place. The first quarter of this year saw an interesting change: for the first time in four years Net-Worm.Win32.Kido dropped two positions and was outstripped by Virus.Win32.Sality and Trojan.Win32.Starter.yy. This shows that the main distribution method for Kido – via the MS08-067 vulnerability – is losing its effectiveness as more and more computers around the world update their systems. As long as file infectors (Virus) remain effective, they retain their position in the rankings, regardless of whether users update their OS.
Countries with the highest risk of local infection for user computers
These figures show the average rate of PC infection in different countries.
Computer infection levels by country *
* We excluded from our calculations the countries where the number of KL users is relatively low (less than 10,000).
Percentage of all local threats of user computers, compared to all unique users of KL products in the country.
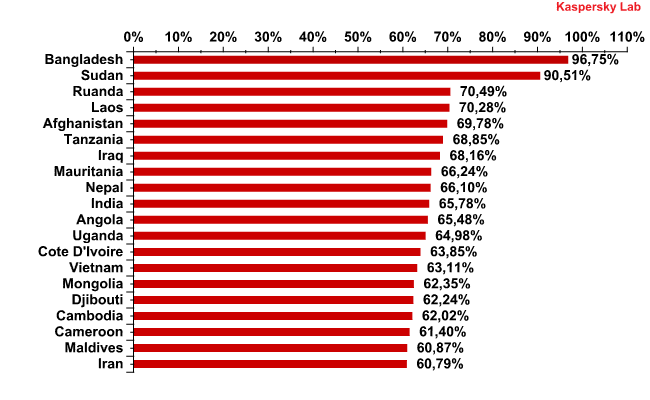
On average, at least one malicious file was detected on 42.2% computers of all KSN users in the world – either on the computer itself or on removable media connected to it.
Bangladesh remains the most dangerous computing environment: the rate for this country is still increasing and is now at 96.8%. Our products detected and blocked malicious programs on almost every one of our users’ computers in the country.
Local infection rates can also be categorized into separate categories. These categories tend to be more stable than those for web threats facing each country.
- Maximum level of local infection (over 60%): 23 Asian countries (India, Vietnam, Mongolia etc.), Middle East countries (Iran, Iraq) and parts of Africa (Sudan, Angola, Nigeria, Cameroon).
- High level of local infection (41-60%): 49 countries, including Egypt, Kazakhstan, Russia, Ecuador and Brazil.
- Moderate level of local infection (21-40%): 41countries including Turkey, Mexico, Israel, Latvia, Portugal, Italy, the US, Australia and France.
- Lowest level of local infection (20% or less): 18 countries including Canada, New Zealand, Puerto Rico, 13 European countries (including Norway, Finland, the Netherlands, Ireland, Germany, Estonia) plus Japan and Hong Kong.
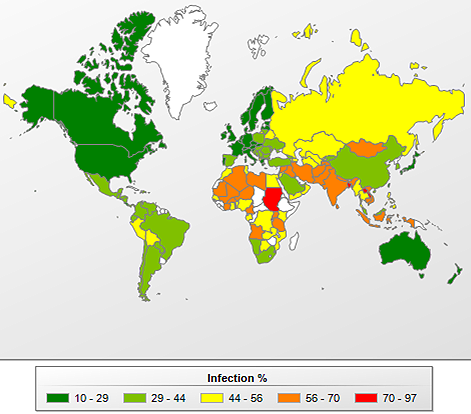
The risk of local PC infection around the world
The 10 countries where users faced the least risk of local infection via the Internet were:
| Rank | Country | % of unique users |
| 1 | Denmark | 10.1% |
| 2 | Switzerland | 14.3% |
| 3 | Japan | 14.4% |
| 4 | Sweden | 15.3% |
| 5 | Germany | 15.7% |
| 6 | Austria | 16.2% |
| 7 | New Zealand | 16.4% |
| 8 | Luxembourg | 16.6% |
| 9 | Finland | 16.9% |
| 10 | Hong Kong | 17.6% |
Vulnerabilities
In the first quarter of 2012 a total of 34,825,675 vulnerable programs and files were detected on the computers of KSN users – an average of 9 different vulnerabilities on each affected computer.
The Top 10 are listed in the table below.
| № | Secunia ID – Unique vulnerability number | Vulnerability name and link to description | What the vulnerability lets malicious users do | Percentage of users on whose computers the vulnerability was detected |
Date of latest change | Rating |
| 1 | SA 48009 | Oracle Java JDK / JRE / SDK Multiple Vulnerabilities | Gain access to a system and execute arbitrary code with local user privileges
Gain access to sensitive data Manipulate data |
29.07% | 10.04.2012 | Highly Critical |
| 2 | SA 46113 | Adobe Flash Player Multiple Vulnerabilities | Gain access to a system and execute arbitrary code with local user privileges XSS Bypass security system |
22.13% | 22.09.2011 | Highly Critical |
| 3 | SA 48281 | Adobe Flash Player Two Vulnerabilities | “Gain access to a system Gain access to sensitive data” |
20.81% | 10.04.2012 | Highly Critical |
| 4 | SA 46512 | Oracle Java SE Multiple Vulnerabilities | DoS attack. Gain access to a system. Gain access to sensitive data. Hijack communication sessions or channels Manipulate data Spoofing |
19.31% | 27.10.2011 | Highly Critical |
| 5 | SA 23655 | Microsoft XML Core Services Multiple Vulnerabilities | Gain access to a system and execute arbitrary code with local user privileges DoS attack XSS |
15.26% | 13.07.2011 | Highly Critical |
| 6 | SA 47133 | Adobe Reader/Acrobat Multiple Vulnerabilities | Gain access to a system and execute arbitrary code with local user privileges | 14.50% | 11.01.2012 | Extremely Critical |
| 7 | SA 46618 | Apple QuickTime Multiple Vulnerabilities | Gain access to a system and execute arbitrary code with local user privileges Gain access to sensitive data XSS |
12.15% | 06.01.2012 | Highly Critical |
| 8 | SA 46882 | Winamp AVI / IT File Processing Vulnerabilities | Gain access to a system and execute arbitrary code with local user privileges | 10.89% | 29.12.2011 | Highly Critical |
| 9 | SA 41917 | Adobe Flash Player Multiple Vulnerabilities | Gain access to a system and execute arbitrary code with local user privileges Gain access to sensitive data Bypass security system |
10.22% | 28.10.2010 | Extremely Critical |
| 10 | SA 47932 | Adobe Shockwave Player Multiple Vulnerabilities | Gain access to a system and execute arbitrary code with local user privileges | 9.93% | 15.02.2012 | Highly Critical |
*Percentage of all users on whose computers at least one vulnerability was detected
A vulnerability in Oracle’s Java was detected on one third of all vulnerable machines. Since the Java vulnerabilities served as the vector of some of the most notorious infections, including the Mac botnet and the spreading of the ‘fileless’ bot, users should update the component as soon as possible. If you do not use the Java virtual machine, it is a good idea to remove it from your computer.
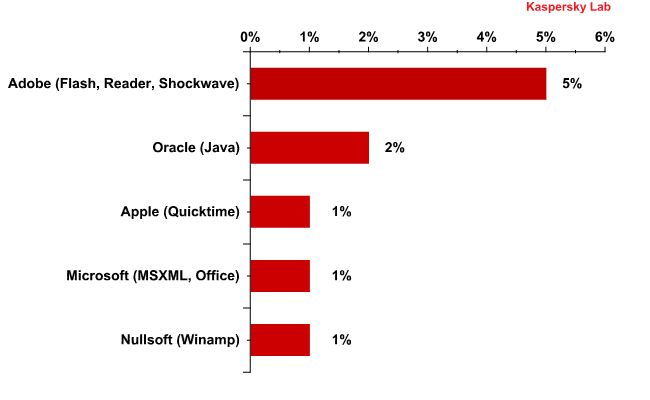
Our ranking features two Java vulnerabilities. Five positions are taken by Adobe products, including Flash and Shockwave players and Reader, a popular application for reading pdf documents. It is worth noting that dozens of exploits have been created for these programs in the past few years, most of which are publicly available. This is why it is essential for users to ensure that these programs are patched in time.
Vendors of products with the Top 10 vulnerabilities
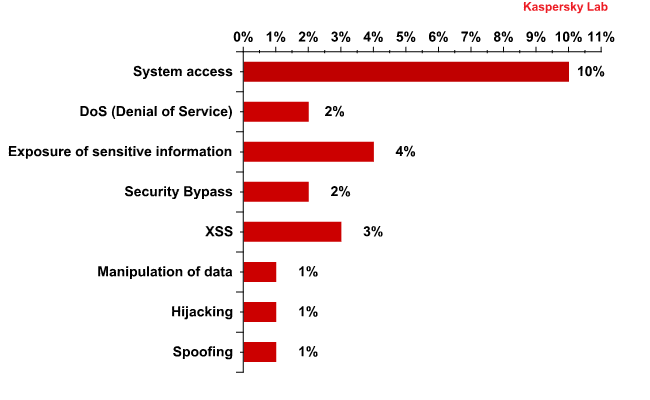
Any of the Top 10 vulnerabilities can jeopardize a computer’s security, because they all allow cybercriminals to gain full control of the system using exploits. Of the ten vulnerabilities, four enable attackers to gain access to sensitive data on the computer and two also make it possible to bypass security systems and conduct DoS attacks on a machine where a vulnerable application is installed. Three vulnerabilities open the way for XSS attacks. The Top 10 also features vulnerabilities that enable attackers to manipulate data, gain important information about the system and perform spoofing (i.e., a cybercriminal can pass himself off as the owner of a user account on the computer).
Distribution of Top 10 vulnerabilities by type of system impact
Conclusion
The beginning of 2012 was marked by a qualitative change in the botnet ecosystem. Botmasters, who had begun to feel overcrowded in the Windows world actively targeted the mobile and Mac OS segments. Unfortunately, few users realize that their smartphones are fully-functional computers which contain valuable data that may be of interest to cybercriminals. In the case of Mac OS X users, the situation is more complicated: first the operating system’s vendor insisted for a long time that no malware existed for the platform, and then they insisted that Macs were more secure than PCs.
Mobile devices and Macs are very attractive to cybercriminals. In addition to limited competition in the segment, a large proportion of mobile devices and Macs operate without any security solutions installed on them. Over 5,000 malicious programs for Android were detected in Q1 2012, which is one third more than last quarter’s figure. Over 70 malicious programs for Mac OS X were detected over the same period, double the figure for Q4 2011. This year, the number of threats targeting home devices in these two segments is set to continue growing rapidly.
One of the quarter’s most significant technological developments was the attack of the ‘fileless’ bot, which performed all of its functions in RAM without creating any files on the hard drive. This made detecting the malware more difficult. Although the bot remained on the computer only until the machine was rebooted, the fact that it was distributed via a banner network used by popular legitimate sites made repeated infections, and hence a large number of active bots, very likely. Kaspersky Lab acted quickly in cooperation with the banner network’s owner to curb the attack. Since this type of attack is impossible without using exploits, only timely patching combined with antivirus protection can help to secure computers against it.
In the light of the above, the security of the iOS mobile platform remains an open issue. Apple enforces policies that make distributing malicious code via the App Store very difficult. On the other hand, developers cannot create solutions which provide effective protection against possible attacks. If cybercriminals attack mobile devices based on the tried and tested Windows scenario where drive-by attacks lead to exploits executing arbitrary code on the system, users will effectively be on their own to cope with any malware running on their devices. All the technical prerequisites for this scenario are currently in place.
In our review of malware evolution in 2011, we wrote that cybercriminals would search for new ways to conduct targeted attacks. Unfortunately, this quickly turned out to be true: in the first quarter of 2012, malware for Mac OS X used in targeted attacks was detected. It is worth noting that in the first stage, the attackers used an exploit for the Java virtual machine, which can be installed on virtually any platform. The malware detected turned out to be backdoors, i.e., programs giving the attackers full access to infected Macs. Corporate Mac users, who are convinced that their computers are ‘beyond suspicion’ and who therefore do not have any security solutions installed on their computers, jeopardize the security of the entire corporate network. It is very likely that this year will see more targeted attacks on corporate networks conducted via Mac OS X.
The joint efforts of law enforcement agencies and IT companies are yielding results. In the first quarter the C&C servers of several ZeuS botnets were taken down in the US and the Hlux.b botnet was taken over. Several groups and individuals were arrested, including the authors of mobile malware known as Foncy in France, several groups of cybercriminals behind Carberp banking Trojans in Russia, and the notorious hacker TinHole, as well as several hackers from the Anonymous group in Romania.
These successes should have a sobering effect on cybercriminals. We expect the number of attacks on home users to gradually stabilize in the near future.


















IT Threat Evolution: Q1 2012