
![]() Download the full report (PDF)
Download the full report (PDF)
All the statistics used in this report were obtained using Kaspersky Security Network (KSN), a distributed antivirus network that works with various anti-malware protection components. The data was collected from KSN users who agreed to provide it. Millions of Kaspersky Lab product users from 213 countries and territories worldwide participate in this global exchange of information about malicious activity.
Q2 figures
- According to KSN data, Kaspersky Lab solutions detected and repelled 171,895,830 malicious attacks from online resources located in 191 countries all over the world.
- 54,539,948 unique URLs were recognized as malicious by web antivirus components.
- Kaspersky Lab’s web antivirus detected 16,119,489 unique malicious objects: scripts, exploits, executable files, etc.
- Attempted infections by malware that aims to steal money via online access to bank accounts were registered on 1,132,031 user computers.
- Crypto ransomware attacks were blocked on 311,590 computers of unique users.
- Kaspersky Lab’s file antivirus detected a total of 249,619,379 unique malicious and potentially unwanted objects.
- Kaspersky Lab mobile security products detected:
- 3,626,458 malicious installation packages;
- 27,403 mobile banker Trojans (installation packages);
- 83,048 mobile ransomware Trojans (installation packages).
Mobile threats
In Q2 2016, Kaspersky Lab detected 3,626,458 malicious installation packages – 1.7 times more than in the previous quarter.
Number of detected malicious installation packages (Q3 2015 – Q2 2016)
Distribution of mobile malware by type
As of this quarter, we will calculate the distribution of mobile malware by type based on the number of detected malicious installation packages rather than modifications, as was the case in earlier reports.
Distribution of new mobile malware by type (Q1 2016 and Q2 2016)
In Q2 2016, RiskTool software, or legal applications that are potentially dangerous to users, topped the ranking of detected malicious objects for mobile devices. Their share increased from 31.6% in Q1 to 45.1% this quarter.
Adware occupies second place. The share of these programs fell 1.4 p.p. compared to the previous quarter, and accounted for 14.2%.
The share of SMS Trojans fell from 18.5% to 10.8%, pushing this category of malicious programs down from second to third place in the ranking. Trojan-SMS.AndroidOS.Agent.qu and Trojan-SMS.AndroidOS.Agent.f accounted for most of the detected SMS Trojans, with both accounting for approximately 30% of all malicious files in this category.
The Trojan-Dropper share also fell – from 14.5% in Q1 to 9.2%. Trojan-Dropper.AndroidOS.Agent.v led the way: we detected more than 50,000 installation packages related to this Trojan.
TOP 20 mobile malware programs
Please note that this ranking of malicious programs does not include potentially dangerous or unwanted programs such as RiskTool or adware.
| Name | % of attacked users* | |
| 1 | DangerousObject.Multi.Generic | 80.87 |
| 2 | Trojan.AndroidOS.Iop.c | 11.38 |
| 3 | Trojan.AndroidOS.Agent.gm | 7.71 |
| 4 | Trojan-Ransom.AndroidOS.Fusob.h | 6.59 |
| 5 | Backdoor.AndroidOS.Ztorg.a | 5.79 |
| 6 | Backdoor.AndroidOS.Ztorg.c | 4.84 |
| 7 | Trojan-Ransom.AndroidOS.Fusob.pac | 4.41 |
| 8 | Trojan.AndroidOS.Iop.t | 4.37 |
| 9 | Trojan-Dropper.AndroidOS.Gorpo.b | 4.3 |
| 10 | Trojan.AndroidOS.Ztorg.a | 4.30 |
| 11 | Trojan.AndroidOS.Ztorg.i | 4.25 |
| 12 | Trojan.AndroidOS.Iop.ag | 4.00 |
| 13 | Trojan-Dropper.AndroidOS.Triada.d | 3.10 |
| 14 | Trojan-Dropper.AndroidOS.Rootnik.f | 3.07 |
| 15 | Trojan.AndroidOS.Hiddad.v | 3.03 |
| 16 | Trojan-Dropper.AndroidOS.Rootnik.h | 2.94 |
| 17 | Trojan.AndroidOS.Iop.o | 2.91 |
| 18 | Trojan.AndroidOS.Rootnik.ab | 2.91 |
| 19 | Trojan.AndroidOS.Triada.e | 2.85 |
| 20 | Trojan-SMS.AndroidOS.Podec.a | 2.83 |
* Percentage of unique users attacked by the malware in question, relative to all users of Kaspersky Lab’s mobile security product that were attacked.
First place is occupied by DangerousObject.Multi.Generic (80.87%), the classification used for malicious programs detected by cloud technologies. Cloud technologies work when the antivirus database contains neither the signatures nor heuristics to detect a malicious program, but the cloud of the antivirus company already contains information about the object. This is basically how the very latest malware is detected.
As in the previous quarter, 16 Trojans that use advertising as their main means of monetization (highlighted in blue in the table) made it into the TOP 20. Their goal is to deliver as many adverts as possible to the user, employing various methods, including the installation of new adware. These Trojans may use superuser privileges to conceal themselves in the system application folder, from which it will be very difficult to delete them.
Trojan.AndroidOS.Iop.c (11.38%) moved from third to second in the TOP 20 and became the single most popular malicious program of the quarter. Over the reporting period we detected this Trojan in 180 countries, but the majority of attacked users were in Russia, India and Algeria. Iop.c can exploit a variety of vulnerabilities in the system to gain superuser privileges. The main method of monetization is displaying advertising and installing (usually secretly) various programs on the user’s device, including other malicious programs.
Q2’16, @kaspersky repelled 172M malicious attacks via online resources located in 191 countries #KLreport #Infosec
Tweet
Representatives of the Trojan-Ransom.AndroidOS.Fusob ransomware family claimed fourth and seventh places. These Trojans demand a ransom of $100-200 from victims to unblock their devices. Attacks using this Trojan were registered in over 120 countries worldwide in Q2, with a substantial number of victims located in Germany and the US.
Trojan-SMS.AndroidOS.Podec.a (2.83%) has now spent over a year in the mobile malware TOP 20, although it is starting to lose ground. It used to be an ever-present in the TOP 5 mobile threats, but for the second quarter in a row it has only made it into the bottom half of the ranking. Its functionality has remained practically unchanged; its main means of monetization is to subscribe users to paid services.
The geography of mobile threats
The geography of attempted mobile malware infections in Q2 2016 (percentage of all users attacked)
TOP 10 counties attacked by mobile malware (ranked by percentage of users attacked)
| Country* | % of users attacked ** | |
| 1 | China | 36.31 |
| 2 | Bangladesh | 32.66 |
| 3 | Nepal | 30.61 |
| 4 | Uzbekistan | 22.43 |
| 5 | Algeria | 22.16 |
| 6 | Nigeria | 21.84 |
| 7 | India | 21.64 |
| 8 | Indonesia | 21.35 |
| 9 | Pakistan | 19.49 |
| 10 | Iran | 19.19 |
* We eliminated countries from this ranking where the number of users of Kaspersky Lab’s mobile security product is lower than 10,000.
** Percentage of unique users attacked in each country relative to all users of Kaspersky Lab’s mobile security product in the country.
China topped the ranking, with more than 36% of users there encountering a mobile threat at least once during the quarter. China also came first in this ranking in Q1 2016.
In all the countries of this ranking, except China, the most popular mobile malware was the same – advertising Trojans that appeared in the TOP 20 mobile malware, and AdWare. The most popular malicious program was Trojan.AndroidOS.Iop.c. In China, a significant proportion of attacks also involved advertising Trojans, but the majority of users there encountered the Backdoor.AndroidOS.GinMaster and Backdoor.AndroidOS.Fakengry families, while Trojan.AndroidOS.Iop.c only occupied sixteenth place.
Russia (10.4%) was 26th in this ranking, Germany (8.5%) 38th, Italy (6.2%) 49th, and France (5.9%) 52th. The US (5.0%) came 59th and the UK (4.6%) 64th.
The safest countries were Austria (3.6%), Sweden (2.9%) and Japan (1.7%).
Mobile banking Trojans
As of this quarter, we will calculate the distribution of mobile malware by type based on the number of detected malicious installation packages rather than modifications, as was the case in earlier reports. Over the reporting period, we detected 27,403 mobile Trojans, which is 1.2 times less than in Q1.
Number of mobile banking Trojans detected by Kaspersky Lab solutions (Q3 2015 – Q2 2016)
The TOP 5 most popular mobile banking Trojans in Q2 consisted of representatives from just two families – Trojan-Banker.AndroidOS.Asacub and Trojan-Banker.AndroidOS.Svpeng.
Trojan-Banker.AndroidOS.Asacub.i was the most popular mobile banking Trojan of the quarter. It uses different methods to trick users and bypass system constraints. In Q1 we identified a modification of this mobile Trojan that overlaid the regular system window requesting device administrator privileges with its own window containing buttons. The Trojan thereby conceals the fact that it is gaining elevated privileges in the system from the user, and tricks the user into approving these privileges. In Q2, we detected a modification that requested the user’s permission to become the main SMS application.
Dialog window of Trojan-Banker.AndroidOS.Asacub.i asking for the user’s approval to become the main SMS application
This allows the Trojan to bypass the system constraints introduced in Android 4.4, and to hide incoming SMSs from the user (as a rule, it hides messages from banks and payment systems). In order to make users save this malicious program in the settings as the main SMS application, the Trojan authors had to, among other things, implement a messenger interface.
The Trojan-Banker.AndroidOS.Asacub.i interface used to create and send messages
Asacub is actively distributed via SMS spam.
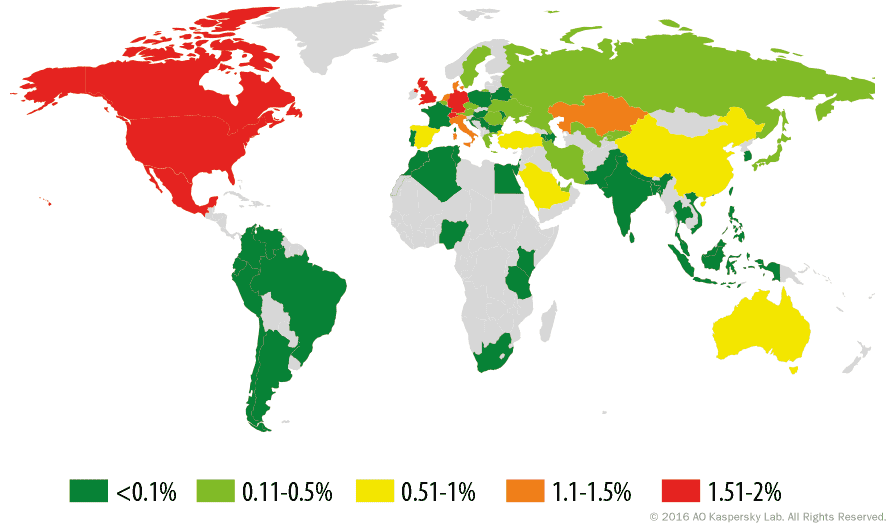
Russia and Germany lead in terms of the number of users attacked by mobile banking Trojans:
Geography of mobile banking threats in Q2 2016 (percentage of all users attacked)
The number of attacked users depends on the overall number of users within each individual country. To assess the risk of a mobile banker Trojan infection in each country, and to compare it across countries, we created a country ranking according to the percentage of users attacked by mobile banker Trojans.
TOP 10 counties attacked by mobile banker Trojans (ranked by percentage of users attacked)
| Country* | % of users attacked** | |
| 1 | Russia | 1.51 |
| 2 | Australia | 0.73 |
| 3 | Uzbekistan | 0.45 |
| 4 | Korea | 0.35 |
| 5 | China | 0.34 |
| 6 | Ukraine | 0.33 |
| 7 | Denmark | 0.28 |
| 8 | Germany | 0.24 |
| 9 | Turkey | 0.23 |
| 10 | Kyrgyzstan | 0.17 |
* We eliminated countries from this ranking where the number of users of Kaspersky Lab’s mobile security product is lower than 10,000.
** Percentage of unique users in each country attacked by mobile banker Trojans, relative to all users of Kaspersky Lab’s mobile security product in the country.
In Q2 2016, first place was occupied by Russia (1.51%) where the majority of affected users encountered the Trojan-Banker.AndroidOS.Asacub, Trojan-Banker.AndroidOS.Svpeng and Trojan-Banker.AndroidOS.Faketoken families of mobile banker Trojans.
China, last quarter’s leader, fell to fifth place this quarter.
In second place again was Australia where the Trojan-Banker.AndroidOS.Acecard family was replaced by the Trojan-Banker.AndroidOS.Marcher family as the most popular threat.
Banking Trojans were especially popular with attackers in Russia and Australia. The percentage of users attacked by this malware in the two countries relative to all attacked users accounted for 14%.
Mobile Trojan-Ransomware
As of this quarter, we will calculate the distribution of mobile malware by type based on the number of detected malicious installation packages rather than modifications, as was the case in earlier reports.
In Q2 2016, we detected 83,048 mobile Trojan-Ransomware installation packages, which is about the same number as the previous quarter and seven times more than in Q4 2015.
Number of mobile Trojan-Ransomware installation packages detected by Kaspersky Lab
(Q3 2015 – Q2 2016)
The sharp rise in the number of mobile Trojan-Ransomware installation packages in 2016 was caused by the active proliferation of the Trojan-Ransom.AndroidOS.Fusob family of Trojans. In the first quarter of 2016, this family accounted for 96% of users attacked by mobile ransomware. In Q2 its share was 85%.
In Q2 2016, 54.5M unique malicious URLs were recognized by @kaspersky web antivirus components #KLreport #IT
Tweet
Trojan-Ransom.AndroidOS.Fusob.h became the most popular mobile Trojan-Ransomware in the second quarter – it accounted for nearly 60% of users attacked by mobile ransomware. Once run, the Trojan requests administrator privileges, collects information about the device, including the GPS coordinates and call history, and downloads the data to a malicious server. After that, it may get a command to block the device. In the second quarter we registered a growth in the number of installation packages related to Trojan-Ransom.AndroidOS.Congur.b: their share grew from 0.8% to 8.8%. This Trojan, targeting Chinese-speaking users, changes the system password (PIN), or installs it if no password was installed earlier, thus making it impossible to use the device. The notification containing the ransom demand is displayed on the screen of the blocked device.
Germany, the US and Russia had the highest number of users attacked by Trojan-Ransomware this quarter:
Geography of mobile Trojan-Ransomware in Q2 2016 (percentage of all users attacked)
To assess the risk of a mobile banker Trojan infection in each country, and to compare it across countries, we created a country ranking according to the percentage of users attacked by mobile Trojan-Ransomware.
TOP 10 counties attacked by mobile Trojan-Ransomware (ranked by percentage of users attacked)
| Country* | % of users attacked** | |
| 1 | Canada | 2.01 |
| 2 | Germany | 1.89 |
| 3 | US | 1.66 |
| 4 | Switzerland | 1.63 |
| 5 | Mexico | 1.55 |
| 6 | UK | 1.51 |
| 7 | Denmark | 1.35 |
| 8 | Italy | 1.35 |
| 9 | Kazakhstan | 1,35 |
| 10 | Netherlands | 1.15 |
* We eliminated countries from this ranking where the number of users of Kaspersky Lab’s mobile security product is lower than 10,000.
** Percentage of unique users in each country attacked by mobile Trojan-Ransomware, relative to all users of Kaspersky Lab’s mobile security product in the country.
In all the countries of the TOP 10, except for Kazakhstan, the most popular Trojan-Ransom family was Fusob. In the US, the Trojan-Ransom.AndroidOS.Svpeng family was also popular. These Trojans demand a ransom of $100-500 from victims to unblock their devices.
In Kazakhstan and Uzbekistan, the main threat to users originated from representatives of the Small mobile Trojan-Ransom family. This is a fairly simple ransomware program that blocks operation of a device by overlaying all the windows on the device with its own window and demanding $10 to unblock it.
Vulnerable applications exploited by cybercriminals
In Q2 2016, exploits for Adobe Flash Player remained popular. During the reporting period two new vulnerabilities were discovered in this software:
- СVE-2016-4117
- CVE-2016-4171
An exploit for CVE-2016-4117 was added to the Magnitude and Neutrino exploit kits. The CVE-2016-4171 vulnerability was used by the ScarCruft group to carry out targeted attacks. We wrote a more detailed account of this group’s activities in a blog published in mid-June.
In Q2 2016, @kaspersky web #antivirus detected 16,119,489 unique malicious objects #KLreport #netsec
Tweet
The main event this quarter was the demise of the long-term market leaders – the Angler and Nuclear exploit kits. Angler’s departure resulted in market players shifting to other kits to distribute malware. In particular, we registered a dramatic growth in the popularity of the Neutrino exploit kit.
This is how the overall picture for the use of exploits in the second quarter looks:
Distribution of exploits used in attacks by the type of application attacked, Q2 2016
The chart shows that despite the exit of the market leaders the breakdown of exploits was almost unchanged from the previous quarter: the proportion of exploits for Microsoft Office (14%) and Java (7%) fell by 1 p.p., while the share for Android grew 2 p.p. and reached 24%. This suggests that demand for exploit kits has been spread among the remaining players: RIG, Magnitude and Neutrino. The latter was the undisputed leader this quarter in terms of the number of attempts to download malware.
Online threats (Web-based attacks)
The statistics in this section were derived from web antivirus components that protect users from attempts to download malicious objects from a malicious/infected website. Malicious websites are created deliberately by malicious users; infected sites include those with user-contributed content (such as forums), as well as compromised legitimate resources.
In the second quarter of 2016, Kaspersky Lab’s web antivirus detected 16,119,489 unique malicious objects: scripts, exploits, executable files, etc. 54,539,948 unique URLs were recognized as malicious by web antivirus components.
Online threats in the banking sector
These statistics are based on the detection verdicts of Kaspersky Lab products, received from users of Kaspersky Lab products who have consented to provide their statistical data.
Number of users attacked by malware targeting finances
Due to the constant emergence of new representatives of banking Trojans and functional changes in existing banking Trojans, in the second quarter of 2016 we have significantly updated the list of verdicts classed as banking risks. This means the number of financial malware victims has changed significantly compared to the data published in previous quarters. As a comparison, we have recalculated the statistics for the previous quarter, taking into account all the malware from the updated list.
Kaspersky Lab solutions blocked attempts to launch malware capable of stealing money via online banking on 1,132,031 computers in Q2 2016. The quarter saw an increase in financial malware activity: the figure for Q2 is 15.6% higher than that for the previous quarter (979, 607).
Number of users attacked by malware targeting finances, Q2 2016
Geography of attack
To evaluate and compare the risk of being infected by banking Trojans worldwide, we calculate the percentage of Kaspersky Lab product users who encountered this type of threat during the reporting period in the country, relative to all users of our products in the county.
Geography of banking malware attacks in Q2 2016 (percentage of attacked users)
TOP 10 countries by percentage of attacked users
| Country* | % of attacked users** | |
| 1 | Turkey | 3.45 |
| 2 | Russia | 2.92 |
| 3 | Brazil | 2.63 |
| 4 | Pakistan | 2.60 |
| 5 | Venezuela | 1.66 |
| 6 | Tunisia | 1.62 |
| 7 | Japan | 1.61 |
| 8 | Singapore | 1.58 |
| 9 | Libya | 1.57 |
| 10 | Argentina | 1.48 |
These statistics are based on the detection verdicts returned by the antivirus module, received from users of Kaspersky Lab products who have consented to provide their statistical data.
* We excluded those countries in which the number of Kaspersky Lab product users is relatively small (less than 10,000).
** Unique users whose computers have been targeted by banking Trojan attacks as a percentage of all unique users of Kaspersky Lab products in the country.
The highest percentage of Kaspersky Lab users attacked by banking Trojans was in Turkey. One of the reasons for the growth in financial threats there was a burst of activity by the Gozi banking Trojan whose developers have joined forces with the creators of the Nymaim Trojan.
In Russia, 2.92% of users encountered a banking Trojan at least once in Q2, placing it second in this ranking.
Brazil rounds off the top three. We expect a surge in financial threats in Latin America in the next quarter due to the Olympic Games in Brazil. This event is just too tempting for cybercriminals to ignore – they regularly use the theme of major sporting events in their attacks to lure potential victims.
The top five countries where users were least affected by banking Trojans were Canada (0.33%), the US (0.4%), the UK (0.4%), France (0.43%) and the Netherlands (0.5%).
The percentage of banking Trojan victims in Italy was 0.62%, in Spain it was 0.83%, while in Germany the figure was 1.03%.
The TOP 10 banking malware familie
The table below shows the top 10 malware families most commonly used in Q2 2016 to attack online banking users (as a percentage of users attacked):
| Name* | Percentage of users attacked** | |
| 1 | Trojan-Spy.Win32.Zbot | 15.72 |
| 2 | Trojan-Banker.Win32.Gozi | 3.28 |
| 3 | Trojan.Win32.Qhost | 2.35 |
| 4 | Trojan-Banker.Win32.Shiotob | 2.27 |
| 5 | Trojan-Banker.Win32.BestaFera | 2.12 |
| 6 | Trojan.Win32.Nymaim | 1.98 |
| 7 | Trojan-Banker.Win32.ChePro | 1.90 |
| 8 | Trojan-Banker.Win32.Banbra | 1.77 |
| 9 | Trojan.Win32.Neurevt | 0.67 |
| 10 | Backdoor.Win32.Shiz | 0.66 |
* The detection verdicts of Kaspersky Lab products, received from users of Kaspersky Lab products who have consented to provide their statistical data.
** Unique users whose computers have been targeted by the malware in question as a percentage of all users attacked by financial malware.
Trojan-Spy.Win32.Zbot in first place is a permanent fixture in the leading positions of this ranking, and it is no coincidence: the source codes of this Trojan became publicly available back in 2012. This has resulted in the emergence of new banking Trojans that have adopted fragments of the Zbot code.
The second quarter of 2016 saw a surge in malicious activity by Trojan.Win32.Nymaim. As a result, this Trojan made it into the top 10 for the first time, going straight in at sixth place. Nymaim was initially designed to block access to valuable data and then demand a ransom (ransomware) to unblock it, but the latest version now also includes banking Trojan functionality for stealing financial information. This can be explained by the fact that the creators of Nymaim and Gozi (which also appears in the Q2 TOP 10 financial risks) have joined forces. Nymaim’s source code now includes fragments of Gozi code that provide attackers with remote access to infected computers.
In Q2 2016, Attempted infections by financial #malware were registered on 1.1M user computers #KLreport #banking
Tweet
A permanent resident in this ranking and one of the reasons financial threats are so prominent in Brazil is the Trojan-Banker.Win32.ChePro family. This banking malware lets cybercriminals take screenshots, register keystrokes, and read the contents of the clipboard, i.e., it possess functionality capable of attacking almost any online banking system. Criminals are trying to implement new techniques to avoid detection for as long as possible. Some of the Trojans from this family use geolocation or ask for the time zone and the Windows version from the system in order to infect users in a particular region.
Yet another newcomer to the top 10 most active financial threats in Q2 was the Trojan.Win32.Neurevt family. Representatives of this family were first discovered in 2013 and are used by cybercriminals not only to steal user payment data in online banking systems but also to send out spam (some versions, for example, sent spam messages on Skype) and implement DDoS attacks (with the addition of functionality capable of performing the Slowloris HTTP flooding scenario).
Ransomware Trojans
The overall number of cryptor modifications in our virus collection to date is approximately 26,000. A total of 28 new cryptor families and 9,296 new modifications were detected in Q2.
The following graph shows the rise in the number of newly created cryptor modifications over the last two quarters.
Number of Trojan-Ransom cryptor modifications (Q1 2016 vs Q2 2016)
Some of the more high-profile or unusual Trojans detected in Q2 2016 are listed below:
-
CryptXXX (Trojan-Ransom.Win32.CryptXXX)
This cryptor has been widely distributed via exploit kits since April 2016. Its earlier versions contained gaps in the file encryption algorithm which allowed Kaspersky Lab to release a utility to decrypt them. Unfortunately, the attackers have made adjustments to subsequent versions, making it impossible to decrypt the files affected by later CryptXXX modifications.
-
ZCryptor (Trojan-Ransom.MSIL.Zcryptor)
This malware combines cryptor functionality and a worm distribution method. Trojan ransomware does not usually include tools for self-propagation, and ZCryptor just happens to be an exception to this rule. Like a classic worm, while infecting, it creates copies of its body on removable media and generates the autorun.inf file to implement the automatic launch of its executable file once the media is connected to another system (if, of course, autorun is not disabled).
-
RAA (Trojan-Ransom.JS.RaaCrypt)
Sometimes we come across cryptors that differ from their peers in terms of functionality, and sometimes an unusual implementation will catch the attention of an analyst. In the case of RAA, the choice of programming language was curious: it was written entirely in JavaScript. The whole body of the program was included in a single .js file delivered to the victim as an attachment in a spam message. When run, it displays a fake error message, and in the meantime, encrypts the user’s files.
-
Bart (Trojan-Ransom.Win32.Bart)
This cryptor puts the victim’s files in password-protected ZIP archives; and it creates passwords using the Diffie-Hellman algorithm on an elliptic curve. The design of the ransom note and the payment site is an exact copy of that used by the notorious Locky.
-
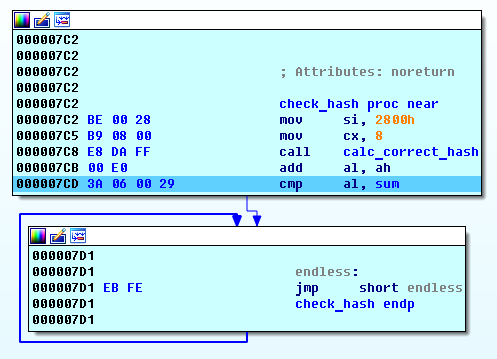
Satana (Trojan-Ransom.Win32.Satan)
This is a combination of MBR blocker and file cryptor, probably inspired by similar functionality in the notorious Petya + Mischa Trojans. Satana, unlike Petya, does not encrypt MFT; in fact, its MBR module is obviously incomplete because the process of checking the password entered by the victim results in nothing more than a continuous cycle. Below is a fragment of the code demonstrating this.
The number of users attacked by ransomware
Number of users attacked by Trojan-Ransom cryptor malware (Q2 2016)
In Q2 2016, 311,590 unique users were attacked by cryptors, which is 16% less than the previous quarter. Approximately 21% of those attacked were in the corporate sector.
It is important to keep in mind that the real number of incidents is several times higher: the statistics reflect only the results of signature-based and heuristic detections, while in most cases Kaspersky Lab products detect encryption Trojans based on behavior recognition models and issue the Generic verdict, which does not distinguish the type of malicious software.
Top 10 countries attacked by cryptors
| Country* | % of users attacked by cryptors** | |
| 1 | Japan | 2.40 |
| 2 | Italy | 1.50 |
| 3 | Djibouti | 1.46 |
| 4 | Luxembourg | 1.36 |
| 5 | Bulgaria | 1.34 |
| 6 | Croatia | 1.25 |
| 7 | Maldives | 1.22 |
| 8 | Korea | 1.21 |
| 9 | Netherlands | 1.15 |
| 10 | Taiwan | 1.04 |
* We excluded those countries where the number of Kaspersky Lab product users is relatively small (less than 10,000).
** Unique users whose computers have been targeted by ransomware as a percentage of all unique users of Kaspersky Lab products in the country.
In Q2, half of the top 10 were European countries – one less than the previous quarter.
Japan, which came ninth in Q1, topped the ranking of countries attacked by cryptors with 2.40%: the most widespread cryptor families in the country were Teslacrypt, Locky and Cryakl.
Newcomers to this ranking were Djibouti (1.46%), Korea (1.21%) and Taiwan (1.04%).
Top 10 most widespread cryptor families
| Name | Verdict* | Percentage of users** | |
| 1 | CTB-Locker | Trojan-Ransom.Win32.Onion/Trojan-Ransom.NSIS.Onion | 14.59 |
| 2 | Teslacrypt | Trojan-Ransom.Win32.Bitman | 8.36 |
| 3 | Locky | Trojan-Ransom.Win32.Locky | 3.34 |
| 4 | Shade | Trojan-Ransom.Win32.Shade | 2.14 |
| 5 | Cryrar/ ACCDFISA | Trojan-Ransom.Win32.Cryrar | 2.02 |
| 6 | Cryptowall | Trojan-Ransom.Win32.Cryptodef | 1.98 |
| 7 | Cryakl | Trojan-Ransom.Win32.Cryakl | 1.93 |
| 8 | Cerber | Trojan-Ransom.Win32. Zerber | 1.53 |
| 9 | Scatter | Trojan-Ransom.BAT.Scatter/Trojan-Downloader.JS.Scatter/Trojan-Dropper.JS.Scatter/Trojan-Ransom.Win32.Scatter | 1.39 |
| 10 | Rakhni | Trojan-Ransom.Win32.Rakhni/Trojan-Downloader.Win32.Rakhni | 1.13 |
* These statistics are based on detection verdicts received from users of Kaspersky Lab products who have consented to provide their statistical data.
** Unique users whose computers have been targeted by a specific Trojan-Ransom family as a percentage of all users of Kaspersky Lab products attacked by Trojan-Ransom malware.
First place in Q2 was occupied by the CTB-Locker (Trojan-Ransom.Win32/NSIS.Onion) family. In second place was the TeslaCrypt family represented by one verdict: Trojan-Ransom.Win32.Bitman. The Trojan-Ransom.JS.Cryptoload verdict, which in the past downloaded malware and was associated with TeslaCrypt, is no longer characteristic of this family only. TeslaCrypt was earlier a major contributor to the statistics, but fortunately ceased to exist in May 2016 – the owners disabled their servers and posted a master key to decrypt files.
In Q2 2016, #crypto #ransomware attacks were blocked on 311,590 computers of unique users #KLreport
Tweet
Cerber and Cryrar are the only changes to this ranking compared to the previous quarter.
The Cerber cryptor spreads via spam and exploit kits. The cryptor’s site on the Tor network is translated into lots of languages. Cerber’s special features include the following:
- It explores the infected system meticulously: checks for the presence of an antivirus, if it is running under a virtual machine (Parallels, VmWare, QEMU, VirtualBox) or Wine, checks for utilities from various researchers and analysts (it does this by searching for certain processes and files on the disk drive), it even has a denylist of system drive serial numbers.
- It checks the keyboard layout and the IP address of the infected system. If it detects that the machine is located in a CIS country, it stops infecting it.
- It attempts to bypass antivirus protection by terminating their processes, interrupting services, deleting files.
- In addition to notifying users about encryption in the form of TXT and HTML files, as is the case with other families, it also runs the VBS script which reproduces the following voice message: “Attention! Attention! Attention! Your documents, photos, databases and other important files have been encrypted!”
The Cryrar cryptor also known as the Anti Cyber Crime Department of Federal Internet Security Agency (ACCDFISA), Anti-Child Porn Spam Protection, etc. first appeared back in 2012. It has the distinctive feature of placing the victim’s files in password-protected self-extracting RAR archives. According to KSN statistics, it shows no signs of conceding its position to newer rivals.
Top 10 countries where online resources are seeded with malware
The following statistics are based on the physical location of the online resources that were used in attacks and blocked by our antivirus components (web pages containing redirects to exploits, sites containing exploits and other malware, botnet command centers, etc.). Any unique host could be the source of one or more web attacks.
In order to determine the geographical source of web-based attacks, domain names are matched against their actual domain IP addresses, and then the geographical location of a specific IP address (GEOIP) is established.
In Q2 2016, Kaspersky Lab solutions blocked 171,895,830 attacks launched from web resources located in 191 countries around the world. 54,539,948 unique URLs were recognized as malicious by web antivirus components.
81% of notifications about blocked web attacks were triggered by attacks coming from web resources located in 10 countries.
Distribution of web attack sources by country, Q2 2016
The US (35.44%) returned to the top of this ranking in the second quarter. Russia (10.28%) moved up one place to second. The previous quarter’s leader, the Netherlands, dropped to fourth place after its share fell by 17.7 percentage points. Germany completed the Top 3 with a share of 8.9%. Bulgaria left the Top 10, while Canada was a newcomer in ninth place with 0.96%.
Countries where users faced the greatest risk of online infection
In order to assess the risk of online infection faced by users in different countries, we calculated the percentage of Kaspersky Lab users in each country who encountered detection verdicts on their machines during the quarter. The resulting data provides an indication of the aggressiveness of the environment in which computers work in different countries.
| Country* | % of unique users attacked** | |
| 1 | Azerbaijan | 32.10 |
| 2 | Russia | 30.80 |
| 3 | China | 29.35 |
| 4 | Slovenia | 27.54 |
| 5 | Ukraine | 27.46 |
| 6 | Kazakhstan | 27.03 |
| 7 | Vietnam | 26.02 |
| 8 | Algeria | 25.63 |
| 9 | Armenia | 25.09 |
| 10 | Belarus | 24.60 |
| 11 | Brazil | 24.05 |
| 12 | France | 22.45 |
| 13 | Moldova | 22.34 |
| 14 | Kyrgyzstan | 22.13 |
| 15 | Bulgaria | 22.06 |
| 16 | Italy | 21.68 |
| 17 | Chile | 21.56 |
| 18 | Qatar | 20.10 |
| 19 | India | 20.00 |
| 20 | Portugal | 19.84 |
These statistics are based on the detection verdicts returned by the web antivirus module, received from users of Kaspersky Lab products who have consented to provide their statistical data.
* These calculations excluded countries where the number of Kaspersky Lab users is relatively small (fewer than 10,000 users).
** Unique users whose computers have been targeted by web attacks as a percentage of all unique users of Kaspersky Lab products in the country.
In Q2, Azerbaijan moved up from fourth to first place and became the new leader of this ranking with 32.1%. Russia (30.8%) dropped from first to second, while Kazakhstan (27.03%) fell from second to sixth place.
Since the previous quarter, Spain, Lithuania, Croatia and Turkey have all left the TOP 20. The newcomers to this ranking were Bulgaria (22.06%), Chile (21.56%), Qatar (20.10%) and Portugal (19.84%).
The countries with the safest online surfing environments included Canada (15%), Romania (14.6%), Belgium (13.7%), Mexico (13.2%), the US (12.8%), Switzerland (12. 4%), New Zealand (12.1%), Czech Republic (12%), Argentina (9.9%), Japan (9.5%), the Netherlands (8.3), Sweden (8.2%) and Germany (8%).
On average, 19.4% of computers connected to the Internet globally were subjected to at least one web attack during the three months. This is a fall of 1.8 p.p. compared to Q1 2016.
Local threats
Local infection statistics for user computers are a very important indicator: they reflect threats that have penetrated computer systems by infecting files or removable media, or initially got on the computer in an encrypted format (for example, programs integrated in complex installers, encrypted files, etc.).
Data in this section is based on analyzing statistics produced by antivirus scans of files on the hard drive at the moment they were created or accessed, and the results of scanning removable storage media.
In Q2 2016, Kaspersky Lab’s file antivirus detected 249,619,379 unique malicious and potentially unwanted objects.
Countries where users faced the highest risk of local infection
For each of the countries, we calculated the percentage of Kaspersky Lab product users on whose computers the file antivirus was triggered during the quarter. These statistics reflect the level of personal computer infection in different countries.
Top 20 countries with the highest levels of computer infection
| Country* | % of unique users** | |
| 1 | Somalia | 65.80 |
| 2 | Vietnam | 63.33 |
| 3 | Tajikistan | 62.00 |
| 4 | Russia | 61.56 |
| 5 | Kyrgyzstan | 60.80 |
| 6 | Bangladesh | 60.19 |
| 7 | Afghanistan | 60.00 |
| 8 | Armenia | 59,74 |
| 9 | Ukraine | 59.67 |
| 10 | Nepal | 59.66 |
| 11 | Ethiopia | 59.63 |
| 12 | Laos | 58.43 |
| 13 | Kazakhstan | 57.72 |
| 14 | Rwanda | 57.33 |
| 15 | Djibouti | 56.07 |
| 16 | Yemen | 55.98 |
| 17 | Venezuela | 55.76 |
| 18 | Algeria | 55.58 |
| 19 | Cambodia | 55.56 |
| 20 | Iraq | 55.55 |
These statistics are based on the detection verdicts returned by on-access and on-demand antivirus modules, received from users of Kaspersky Lab products who have consented to provide their statistical data. The data include detections of malicious programs located on users’ computers or on removable media connected to the computers, such as flash drives, camera and phone memory cards, or external hard drives.
* These calculations exclude countries where the number of Kaspersky Lab users is relatively small (fewer than 10,000 users).
** The percentage of unique users in the country with computers that blocked local threats as a percentage of all unique users of Kaspersky Lab products.
Somalia remained the leader of this ranking in Q2 2016 with 65.8%. Yemen (55.98%) fell from second to sixteenth place, while Vietnam (63.33%) jumped from eighth to second. Tajikistan (62%) rounded off the TOP 3. Russia moved up one place from fifth to fourth, although the figure for that country declined by 2.62 percentage points to 61.56%.
In Q2 2016, 27,403 #mobile #banking Trojans were detected by @kaspersky mobile security products #KLreport
Tweet
Newcomers to this ranking are Djibouti in fifteenth place (56.07%), Venezuela in seventeenth (55.76%), and Cambodia in nineteenth (55.56%).
The safest countries in terms of local infection risks were Croatia (29%), Singapore (28.4%), Germany (28.1%), Norway (27.6%), the US (27.1%), Switzerland (26.3%), Japan (22.1%), Denmark (21.4%) and Sweden (21.3%).
An average of 43.3% of computers globally faced at least one local threat during Q2 2016, which is 1.2 p.p. less than in the previous quarter.
IT threat evolution in Q2 2016. Statistics



































Harm Kuiper
Thanks, great report! Feel free to contact me if you want more input.