
Overview
A host of events took place in the world of IT threats during the first quarter of 2011. The predictions that we made in our annual Security Bulletin, particularly concerning mobile threats and targeted attacks, began to come true at an alarming rate and the situation continues to hot up. Below, we analyze the most significant incidents that occurred in the first quarter.
Now in a store near you – mobile Trojans!
We start with malware for the Android OS uploaded to the Android Market by cybercriminals. The malicious applications, over fifty of which have been detected, were infected with Trojans and repacked as legitimate programs. The attackers were after mobile phone data, including IMEI and IMSI numbers. The Trojans also included a module that could install additional malicious components on devices without users being aware. This involved gaining full control of the phone by ‘jailbreaking’ it, a process that circumvents protection to provide full access to the file system. In order to gain root privileges, which provide virtually limitless possibilities for manipulating the system, the malware leveraged Android OS vulnerabilities using popular ‘rage against the cage’ exploits, which were distributed in the same package as the Trojans.
It was lucky for users who had Kaspersky Mobile Security 9 installed on their devices that these exploits were used. The Trojans were new and had not been included in antivirus databases, while the exploits bundled with them were successfully detected. Until signatures were created for the Trojans, KMS 9 proactively detected the whole bundle as Exploit.AndroidOS.Lotoor.g and Exploit.AndroidOS.Lotoor.j. Since adding the Trojans to our antivirus databases, we have detected them as Backdoor.AndroidOS.Rooter. It should be noted that they are also called DroidDream in other antivirus vendors’ classifications.
This situation gives rise to two questions:
- Is it difficult for cybercriminals to get an Android Market Developer account?
Sadly, it is very easy. All a user has to do to get an account is pay US $25. Clearly, Google wants to attract as many developers to its operating system as possible. However, $25 is not nearly enough of a barrier to entry and cybercriminals can afford to create dozens of such accounts. This could result in an endless loop, with Google shutting down accounts used to distribute malware and cybercriminals creating new ones without any problems. - Can more stringent controls be enforced over applications offered on the Android Market?
The primary problem is the resources available for this task. Checking all the code in apps available via Android Market, App Store, Samsung Market, plus others, is a difficult task because it is almost impossible to automate. This means that in future we will inevitably face an increase in the amount of malware-infected software in the various app stores.
As mentioned above, the malware detected on Android Market exploited vulnerabilities. Note that vulnerabilities affected devices with Android versions earlier than 2.3 ‘Gingerbread’, which was released on 6 December, 2010. According to Google, three months after its release the number of systems running the new version of the OS was only 2%. It is obvious that users are not in any hurry to upgrade their systems. The main reason for this lack of inertia is that device manufacturers make significant modifications to their operating systems before installing them on mobile devices. After this, upgrading the OS may become impossible or wholly dependent upon the manufacturer’s involvement.
This means that installing patches then becomes manufacturer-dependant and so they share the responsibility for the security of mobile devices. However, they often have no interest in supporting and updating software on existing devices. Since smartphone models become outdated very quickly, updating software on devices that are in effect obsolete results in additional costs with no obvious way to recoup them. All users can hope for is that device manufacturers will take appropriate measures and make it possible to install updates on their devices. Is it possible to seriously discuss security in circumstances such as these?
Importantly, Google can remotely install / remove applications on / from any Android device. This ought to be very helpful when it comes to neutralizing malware on phones which are already infected. However, the incident with Trojans on Android Market has demonstrated several weaknesses in the system.
Firstly, once they got administrator privileges, Trojans made themselves at home on the smartphones and could only be removed by an application that had the same administrator privileges. Google had to release a dedicated program that had such privileges in order to remove these Trojans from infected devices.
Secondly, as cybercriminals further develop mobile malware, they may implement technologies that allow Trojans to disable this remote administration mechanism, a process similar to disabling the Windows Update functionality on PCs.
Thirdly, the current system involves removing Trojans from infected phones, but not the prevention of infections. However, if a Trojan is used by attackers to steal money or important data, its removal will not undo the damage.
Overall, the situation with the Android OS is becoming similar to the current situation with Windows:
- There is a plethora of Android devices with outdated software which includes various unpatched vulnerabilities;
- In the majority of cases, users ignore security alerts displayed when any application is installed or launched for the first time;
- As with Windows, the most infected computers are those on which users have administrator privileges, the greatest risk of infection is faced by those Android systems which have been jailbroken;
- Mobile malware communicates with its owners using a method that is widely employed by Windows malware – via command-and-control centers, which will ultimately lead to the emergence of mobile botnets;
- Application control systems can be bypassed: applications can be installed on Android devices using means other than Android Market.
Since 2007, the number of new antivirus database records for mobile malware has virtually doubled every year.
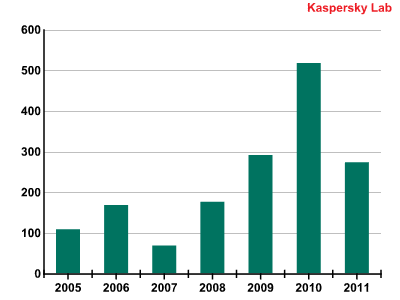
The number of new mobile malware signatures added to antivirus databases
Based on our statistics for the first quarter of this year, it can be safely predicted that the number of malicious programs for mobile devices detected in 2011 will be more than double that of 2010.
The situation with mobile malware is particularly disturbing because large amounts of important data are already stored on mobile devices and smartphones are likely to be widely adopted as mobile wallets in the near future. In addition, since employees are increasingly using their personal mobile devices for work-related purposes, so-called consumerization, data leaks from individual smartphones are turning into a real headache for their employers.
Targeted attacks
The events described in this section began in 2010. Towards the end of last year, a group calling itself Anonymous claimed responsibility for DDoS attacks targeting the Mastercard, Visa and Paypal websites in revenge for these companies refusing to handle funds connected with the Wikileaks project. Many people wondered who was hiding behind the Anonymous name. In early 2011, HBGary, an IT security company, announced that it knew who was behind the attacks. However, HBGary itself was attacked several days later.
The first quarter of 2011 was marked by several attacks on different organizations. In addition to attacking HBGary, hackers hit RSA, BMI and Lush, as well as the Play.com and wiki.php.net sites, etc. As a result of these successful attacks, the cybercriminals gained access to a variety of data, including user identities, which though they cannot be used for immediate gain, are of interest to black hats.
A few years ago it would have been an exceptional achievement for hackers to compromise the servers of a large company, but sadly, such incidents are becoming commonplace. All the signs indicate that some of the professional cybercriminals have struck gold by switching from mass home computer infections to hacking major corporations. This is more risky for the attackers because unlike home users, major corporations can and will retaliate. However, the stakes and thus the potential rewards involved with targeted attacks on corporations are higher and there are fewer competitors in this segment of the black market.
It is alarming that IT security companies are the focus of so many attacks. Such companies usually serve huge numbers of customers and a successful attack may provide cybercriminals with keys to the digital wallets of large numbers of users in different parts of the world.
The task of compromising the servers of IT security companies is very difficult from a technical standpoint. In the case of HBGary, the hackers were able to penetrate the company’s network by attacking the least critical, and therefore least protected, server used by the technical support team. Since the server’s administrator happened to be the company’s CEO, the hackers gained access to a variety of data after obtaining his login and password on the compromised server. The data stolen was very valuable, because HBGary works with large financial organizations and governmental bodies. Run-of-the-mill cybercriminals would have tried to sell the data on the black market immediately. However, the attackers did not follow the conventional path: they made an enormous amount of confidential data publicly available. The attackers’ primary objective was to damage the company’s reputation by making news of the hack public.
In the attack on security provider RSA, the human factor played a significant role. The attackers sent malicious Excel files titled ‘2011 Recruitment Plan.xls’ to the company’s employees in the hope that at least one person would open the received file. They obviously calculated correctly: one of the RCA employees opened the malicious file, which contained zero-day exploits. This gave the attackers control over that employee’s computer and enabled them to penetrate the powerful protection of the corporate network. This story demonstrates yet again that people who work for a company are the weakest link in its IT security chain. The main way of strengthening the link is training – not only of IT staff, but ordinary employees as well. However strong a company’s technical protection might be and however professionally its security policies are configured, it is impossible to create a really well-protected system unless all of its employees understand and follow the basic rules of IT security.
Government resources belonging to Canada, France and South Korea were also attacked by hackers in the first quarter of 2011. While attacks on private companies are usually financially motivated, the reasons for attacking governmental resources are not as clear. In Canada and France, the cybercriminals were after classified documents. In South Korea, the government’s Twitter and YouTube accounts were targeted. In the case of Anonymous and HBGary, the cybercriminals were motivated by reasons other than greed. Attackers were spurred to act as a form of protest against specific decisions taken by organizations and governmental bodies. The Internet has become an integral part of our daily lives and is no longer just a global information environment; it is now an arena for political struggle also.
SCADA – is this just the beginning?
On 21 March, 2011 information regarding 24 vulnerabilities in SCADA systems from different vendors, including Siemens, Iconics, 7-Technologies and DATAC, was published on a seclists.org mailing list.
After the widely publicized Stuxnet story, vulnerabilities in SCADA systems are causing increased concern among security companies. These systems control the operations of industrial facilities, power plants, traffic light systems and other objects that are critical to our day-to-day lives. The possibility of such objects being manipulated by an external force poses a threat to millions of people.
In essence, SCADA software is in no way different from regular programs. Such software is written in the same programming languages, with well-known protocols, including in most cases, network protocols used for communication. SCADA software is also written by people, which undoubtedly is the main source of bugs. This is why errors similar to those found in ordinary programs are often found in SCADA software, and exploits developed for such systems are also an everyday occurrence.
It should be kept in mind that there are numerous SCADA systems globally which were configured when the enterprises they control were launched and have hardly ever been updated since. Updating such systems is not always feasible, because few enterprises can afford to clone their industrial plants for the purposes of testing patches.
It is worth noting that an exploit pack for SCADA systems is already available online, while some of the vulnerabilities published in late March remained unpatched at the time of writing.
Digital distrust?
Today, the entire concept of ‘digital trust’ – the assurance that file sources, web banking, online shopping, email and other telecommunications services are safe to use – revolves around our ability to rely on the integrity of digital signature verification mechanisms and the companies that issue digital certificates.
Our forecast that digital certificates would become a major IT security issue in 2011 is, sadly, beginning to come true. In late March, Microsoft released a bulletin reporting that nine fake certificates had been issued on behalf of Comodo, whose certificates are trusted by default in all versions of Windows and Mac OS X. Fake certificates enable cybercriminals to conduct phishing attacks, spoof website content and carry out MITM (man-in-the-middle) attacks.
According to Comodo, the issuance of fake certificates became possible because the accounts of the company’s two trusted partners were compromised. This incident has highlighted another matter: since the right to issue certificates on behalf of a trusted company can be transferred to third parties, users are forced to have faith not only in the trusted company itself but in its partners as well.
These certificates were not issued for financial organizations, but for websites visited by millions of users and belonging to large corporations, including services such as Google, Gmail, Microsoft Live Mail, Yahoo!, Skype and Mozilla add-ons. This is not typical of old-school hackers who are interested first and foremost in money, and consequently, in financial organizations. Attacks involving fake certificates are not conducted for financial gain, but they can result in the identities of an enormous number of Internet users being stolen. This is in line with the concept of the new breed of cybercriminals that we mentioned in our Security Bulletin.
Curiously, according to Comodo, the hacker attacks on partners were conducted from Iran. That country also hosted a website on which a fake certificate was first used. Later, a person posing as a self-taught Iranian hacker claimed responsibility for compromising the system and even published part of the private key to prove his claims. However, it is clear that the attack had been very carefully planned and professionally carried out – something a self-taught hacker is highly unlikely to be capable of. In addition, attempts to find the hacker who so openly claimed responsibility for the attacks have so far proven fruitless. It is not impossible that the Iranian trail is a false flag operation and was used to divert attention from the real perpetrators.
Rustock routed, but its owners go free
In the middle of March, the Rustock botnet stopped sending spam. This was the direct result of a joint operation by Microsoft and US law enforcement agencies which resulted in the botnet’s command centers being taken down. Following this, the total amount of spam being circulated worldwide fell by 15 percentage points.
Rustock was a botnet controlled via command centers with specific addresses that were hard-coded into its spam bots. When the botnet’s command servers were taken down, its owners lost control of the infected machines. The cybercriminals will not be able to regain control of the computers making up the botnet without reinfecting them, but this does not mean we have seen the back of Rustock.
The bot was created for a single purpose: to send spam. As a result, it has minimal functionality: masking its presence on the computer, receiving commands from the botnet’s owner and sending millions of unsolicited emails. Rustock bots never had self-propagation functionality. The zombie network was created using other botnets. Malware already installed on infected computers, for the most part Trojan-Downloader.Win32.Harnig, was commanded to download and install the Rustock spam bot. The typical Rustock host was a computer with no antivirus solution installed on it and which ran an unpatched installation of Windows XP. There are hundreds of thousands of such computers across the globe. As long as the owners of Rustock walk free, they can create another similar botnet – quite possibly, to include the same machines that made up the zombie network which has been taken down.
The cybercriminals did not actively attempt to create a new botnet immediately after the old one was taken down. According to Kaspersky Lab data, no new downloaders installing Rustock on users’ machines were detected over the two week period from16 March to the end of that month.
Victims of GpCode
The end of the quarter was marked by an attack conducted using a new variant of GpCode, an extremely dangerous ransomware Trojan that encrypts data on infected computers and demands money for decrypting it.
New variants of the encrypting Trojan were first detected at the very end of 2010. Unlike earlier variants which deleted the originals of encrypted files, the new variants of GpCode overwrite files with encrypted data. While deleted originals of encrypted files can be restored using specialized software, overwritten files cannot be recovered without the private key. What further complicates the situation is that the new variants of GpCode use strong encryption algorithms – AES with 256-bit keys and RSA with 1024-bit keys. It is not currently possible to decrypt data encrypted with these algorithms within acceptable time limits and using only the openly stored encrypted data, which is all that remains on victim machines.
The cybercriminals have adopted drive-by downloads to infect users’ machines, luring potential victims to infected websites through the use of black SEO techniques. Users could find themselves on a malicious website if their search query was associated with cooking. Note that all the sites used in the attack were hosted on free hosting services, including am.ae, cx.cc, gv.vg, etc. To disguise their intentions, the cybercriminals registered domain names associated with food, such as “delicate-grill.ae.am”, “generalcook.gv.vg”, “warmblueberry.cx.cc” and “full-bread.ae.am”.
The Trojan’s victims are primarily located in Europe and the former Soviet republics. Infections have been recorded in Germany, Russia, Poland, France, the Netherlands, Kazakhstan, Ukraine and in a number of other countries. The cybercriminals demand that victims pay ransoms via Ukash, an e-money system that is present in all of these countries.
The attack targeted home users and was carried out across a period of just a few hours. It is impossible to create signatures and deliver them to users’ machines within such a short period of time without using modern anti-malware technologies. It is worth mentioning that protection in the form of cloud-based UDS (Urgent Detection System) signatures was promptly made available to Kaspersky Lab product users.
The brief distribution period means that the author[s] of GpCode did not set out to infect vast numbers of machines. This is probably due to the fact that a mass infection would cause law enforcement agencies in different countries to turn their full attention to identifying the perpetrator[s], which would clearly be very undesirable for those responsible. This means that further attacks of the encryption Trojan will also target a relatively narrow audience.
Statistics
Below, we will review some statistics recorded by the various anti-malware modules in Kaspersky Lab products that are installed on users’ computers around the globe. All the statistical data used in this report has been obtained with the help of consenting participants of the Kaspersky Security Network (KSN). The global exchange of information regarding malware activities involves millions of Kaspersky Lab’s product users from 213 countries around the world.
Online threats
The statistical data cited in this chapter was recorded by the web antivirus module in Kaspersky Lab products which is designed to protect users against the downloading of malicious code from infected web pages. Infected sites include those specifically created by cybercriminals, websites with content created by users, such as forums, and other legitimate websites that have been compromised.
Detected objects on the Internet
In the first quarter of 2011, the number of blocked attacks stood at 254,932,299 – these attacks were carried out from web resources located in different countries all over the world.
The Top 20 malicious objects detected on the Internet
| Ranking | Name | Percentage of all attacks (%)* |
| 1 | Blocked | 66.16% |
| 2 | Trojan,Script,Iframer | 20.43% |
| 3 | Exploit,Script,Generic | 14.68% |
| 4 | Trojan,Win32,Generic | 9.59% |
| 5 | Trojan,Script,Generic | 8.91% |
| 6 | Trojan-Downloader,Script,Generic | 8.12% |
| 7 | AdWare,Win32,HotBar,dh | 3.40% |
| 8 | AdWare,Win32,FunWeb,gq | 3.26% |
| 9 | Trojan,HTML,Iframe,dl | 2.16% |
| 10 | Exploit,JS,Pdfka,ddt | 1.82% |
| 11 | Exploit,HTML,CVE-2010-1885,ad | 1.73% |
| 12 | Hoax,Win32,ArchSMS,pxm | 1.59% |
| 13 | Trojan,JS,Popupper,aw | 1.57% |
| 14 | Hoax,Win32,ArchSMS,heur | 1.57% |
| 15 | Trojan-Downloader,Win32,Generic | 1.56% |
| 16 | Trojan-Downloader,Java,OpenConnection,cx | 1.55% |
| 17 | Trojan-Downloader,Java,OpenConnection,cg | 1.33% |
| 18 | Exploit,HTML,CVE-2010-1885,aa | 1.33% |
| 19 | Trojan-Downloader,HTML,Agent,sl | 1.24% |
| 20 | Trojan-Downloader,Java,OpenConnection,cf | 1.15% |
These statistics are compiled from the malware detection verdicts returned by the web antivirus modules of users of Kaspersky Lab products who have agreed to submit their statistical data.
* The share of the total number of web attacks recorded on the computers of individual users.
The bulk of the malicious objects detected online are denylisted links which account for 66.16% of all objects detected. This list contains the URLs of websites with various types of malicious content. All such websites fall into two broad categories. The first category includes sites which actively use social engineering to trick users into installing malicious programs themselves. The second category is made up of sites that surreptitiously download and launch malicious programs on victim computers via drive-by downloads that contain exploits.
In the ranking, 2nd to 6th positions are occupied by different heuristic verdicts. In most cases, the users were attacked by script Trojans and exploits. The fact that Trojan.Script.Iframer is at 2nd place and its analogue, Trojan.HTML.Iframe.dl, is at 9th, indicates that many legitimate websites contain injections of malicious code which are masked as invisible ‘iframe’ tags used during drive-by attacks.
Meanwhile, 7th and 8th places on the list are taken by adware samples HotBar.dh and FunWeb.gq. This adware appears most often in four countries: the US with 28% of all detected HotBar.dh and FunWeb.gq infections, China on14%, India on 6% and finally, the UK with 4%.
Late last year, Trojans from the family Trojan-Downloader.Java.OpenConnection were the most popular with cybercriminals. In Q1 2011, however, they were at the bottom of the ranking. These Trojans exploit a vulnerability in the Java Runtime Environment that enables cybercriminals to bypass the virtual environment and call Java system functions. Any software using the Java Runtime Environment below Version 6 Update 18 is vulnerable. As a large number of functions are used to counteract exploits in interpreted languages, the exploits attack virtual machines rather than programs written in these languages.
It is notable that two positions in the ranking, 12th and 14th places respectively, are taken by programs detected as Hoax.Win32.ArchSMS. They are archives that require users to send an SMS to a paid number in order to unpack them. These malicious programs are mostly detected on the Russian-language sector of the Internet.
Malware hosting countries
Web resources containing malicious programs exist in practically every country of the world. In Q1 2011, 89% of all web resources used for hosting malware were detected in 10 countries around the globe.
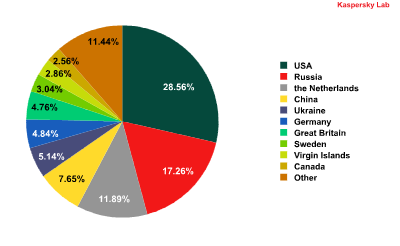
The distribution of countries with malware-hosting web resources in Q1 2011
The United States still tops the list of countries in which malware-spreading web resources were detected. In the US, the bulk of the malicious content is located on compromised legitimate sites. Between January and March 2011, the share of malicious hosting sites in the US increased by 1.7 percentage points.
The most dramatic increases in malicious hosting sites occurred in Russia, up 3.5 percentage points and the UK with 2 percentage points, which puts them in 2nd and 7th positions respectively.
The number of malicious hosting sites in China decreased, continuing the trend that began in 2010. The volume of web attacks originating from this country fell by 3.33 percentage points compared to Q4 2010. The number of servers with malicious content in Germany also decreased as a result of a massive web clean-up effort organized in that country.
Countries where users run the highest risk of web infection
To evaluate the risk of users’ computers being infected via the web in various countries of the world, we analyzed how often web antivirus modules detected a malicious program on users’ machines in each country.
The Top 10 countries in which users computers run the highest risk of infection via the web
| Position | Country * | % of individual users ** |
| 1 | Russian Federation | 49.63% |
| 2 | Oman | 49.57% |
| 3 | Iraq | 45.65% |
| 4 | Belarus | 43.84% |
| 5 | Armenia | 42.42% |
| 6 | Azerbaijan | 42.15% |
| 7 | Kazakhstan | 40.43% |
| 8 | Saudi Arabia | 39.99% |
| 9 | Ukraine | 39.99% |
| 10 | Sudan | 38.87% |
*Countries in which the number of users of Kaspersky Lab products is below the threshold of 10 thousand were not included in the calculations
**The number of individual users’ computers that were attacked via the web as a percentage of the total number of users of Kaspersky Lab’s products in the country.
In the first quarter of 2011, KSN users in Russia and Oman faced the highest risk of infection. In these two countries, nearly every second users’ machine (49%) became the target of a web attack during the three month period. The nature of the threats in these two countries is, however, entirely different. In Oman, computers are primarily infected to further expand existing zombie networks; in Russia, fraudulent programs proliferate alongside botnets.
All of the countries can be assigned to one of the following groups:
- High-risk countries. Includes 7 locations with risk indicators of between 41- 60%. These are: Russia, Oman, Iraq, Belarus, Armenia, Azerbaijan and Kazakhstan.
- Average risk countries. Includes those locations with risk indicators of between 21- 40%. This group contains 87 countries in total.
- Safe-surfing countries. Includes those locations with risk indicators of between 13-20%. During Q1 2011, this group contained 33 countries. The lowest percentage of users’ computers attacked while surfing the net were located in Japan, Germany, Serbia, the Czech Republic and Luxembourg.
Local threats
All statistics quoted in this chapter were recorded by the on-access scanner inside Kaspersky Lab’s products.
Malicious objects detected on users’ computers
During Q1 2011, Kaspersky Lab’s solutions successfully blocked 412,790,509 attempted local infections of users’ computers connected to the Kaspersky Security Network.
In total, there were 487695 incidences of malicious and potentially unwanted programs reported. This number includes, among others, objects that had arrived to the victim computers via local networks or removable storage media rather than through the web, email or network ports.
The Top 20 malicious objects detected on users’ computers
| Position | Name | % of individual users* |
| 1 | DangerousObject.Multi.Generic | 29.59% |
| 2 | Trojan.Win32.Generic | 24.70% |
| 3 | Net-Worm.Win32.Kido.ir | 14.72% |
| 4 | Virus.Win32.Sality.aa | 6.43% |
| 5 | Virus.Win32.Sality.bh | 4.70% |
| 6 | Net-Worm.Win32.Kido.ih | 4.68% |
| 7 | Hoax.Win32.Screensaver.b | 4.48% |
| 8 | HackTool.Win32.Kiser.zv | 4.43% |
| 9 | Hoax.Win32.ArchSMS.heur | 4.08% |
| 10 | Worm.Win32.Generic | 3.36% |
| 11 | Trojan.JS.Agent.bhr | 3.32% |
| 12 | AdWare.Win32.HotBar.dh | 3.28% |
| 13 | Packed.Win32.Katusha.o | 2.99% |
| 14 | Hoax.Win32.ArchSMS.pxm | 2.91% |
| 15 | Trojan.Script.Iframer | 2.80% |
| 16 | Worm.Win32.FlyStudio.cu | 2.74% |
| 17 | HackTool.Win32.Kiser.il | 2.50% |
| 18 | Trojan-Downloader.Win32.Geral.cnh | 2.11% |
| 19 | Trojan-Downloader.Win32.VB.eql | 2.04% |
| 20 | Trojan.Win32.Starter.yy | 1.95% |
These statistics are compiled from the malware detection verdicts given by the antivirus modules of users of Kaspersky Lab products who have agreed to submit their statistical data.
* The number of individual users on whose computers the antivirus module detected these objects as a percentage of all individual users of Kaspersky Lab products on whose computers a malicious program was detected
First place in the ranking is occupied by various malicious programs detected with the help of cloud-based technologies. These technologies work when a malicious program first enters circulation and the antivirus databases do not have signatures or heuristic tools to detect it; at this time, information about this malware may exist in the cloud. In such cases, the malicious program is named according to the format: DangerousObject.Multi.Generic.
Variants of Net-Worm.Win32.Kido and Virus.Win32.Sality occupy 3rd to 6th places in the ranking – both are well known and have been around for quite a while. These malicious programs use effective methods of dissemination which remain active for a long time after they have been released in the wild. Judging by the current situation, these malicious programs will remain at the top of the most widespread malware list for a long time to come.
Two fraudware programs mentioned above and detected by Kaspersky Lab’s products as Hoax.Win32.ArchSMS have taken 9th and 14th positions on this list – they also entered the Top 20 web-threats (see the section ‘Detected objects on the Internet’ above).
Countries in which users’ computers ran the highest risk of local infection
We have calculated the percentage of KSN users in different countries on whose computers attempted local infections were blocked. The resulting numbers show the average share of infected computers in a specific country.
The Top10 countries in which infected computers are located
| Position | Country * | % of individual users’ computers infected ** |
| 1 | Sudan | 69.86% |
| 2 | Bangladesh | 64.33% |
| 3 | Iraq | 62.15% |
| 4 | Rwanda | 57.28% |
| 5 | Nepal | 55.85% |
| 6 | Tanzania | 55.11% |
| 7 | Afghanistan | 54.78% |
| 8 | Angola | 53.63% |
| 9 | Uganda | 53.48% |
| 10 | Oman | 53.16% |
*Countries in which the number of users of Kaspersky Lab products is below the threshold of 10 thousand were not included in the calculations
**The number of individual users on whose computers local threats were blocked as a percentage of all Kaspersky Lab product users in the country
The Top 10 list of countries where users’ computers are exposed to the highest risk of local infections consists entirely of Asian and African countries. In these regions, the level of IT penetration has been growing exponentially. Unfortunately, users’ levels of security awareness have not advanced similarly, which leads to high numbers of infections – over 50% of all computers were infected. In Sudan, which is at the top of the list, malware was detected on two out of every three computers connected to KSN. Incidentally, that country also occupies 10th place on the list of countries with the most computers infected via the Internet.
As for local infections, all countries can be grouped according to their infection rates.
- The group at maximum risk of local infection consists of Sudan, Bangladesh and Iraq, each with over 60% of computers having been infected locally.
- The group with a high risk of local infection, between 41- 60%, consists of 48 countries including India, Indonesia, the Philippines, Thailand, Russia, Ukraine and Kazakhstan.
- The group with a medium risk of infection, between 21- 40%, consists of 55 countries including China, Brazil, Ecuador, Argentina, Turkey, Spain, Portugal and Poland.
- The group with the lowest risk of infection includes 24 countries.
The safest countries in terms of the risk of local infection are:
| Position | Country | % of individual users with locally infected computers |
| 1 | Japan | 6.3% |
| 2 | Germany | 9.2% |
| 3 | Switzerland | 9.6% |
| 4 | Luxembourg | 10.2% |
| 5 | Denmark | 11.1% |
Interestingly, the 2nd and 3rd groups mostly include developing countries, while the 4th group essentially consists of developed countries such as Austria, the UK, Germany, the US, France and Japan.
Vulnerabilities
In Q1 2011, there were 28,752,203 vulnerable applications and files detected on users’ computers.
The Top 10 vulnerabilities detected on users’ computers are shown in the table below.
| № | Secunia ID – vulnerability’s unique ID |
Name of vulnerability and link to description |
Benefits to cybercriminal of exploiting vulnerability |
Percentage of users on whose computers the vulnerability was detected |
Date published |
Rating |
| 1 | SA 41340 | Adobe Reader / Acrobat SING “uniqueName” Buffer Overflow Vulnerability | Gain access to a system and execute arbitrary code with local user privileges | 40.78% | 08.09. 2010 |
Extremely Critical |
| 2 | SA 41917 | Adobe Flash Player Multiple Vulnerabilities | “Gain access to a system and execute arbitrary code with local user privileges Exposure of sensitive information Bypass security systems” |
31.32% | 28.10. 2010 |
Extremely Critical |
| 3 | SA 43267 | Adobe Flash Player Multiple Vulnerabilities | Gain access to a system and execute arbitrary code with local user privileges | 24.23% | 09.02. 2011 |
“Highly Critical
” |
| 4 | SA 43262 | Sun Java JDK / JRE / SDK Multiple Vulnerabilities | “Gain access to a system and execute arbitrary code with local user privileges
DoS attacks |
23.71% | 09.02. 2011 |
“Highly Critical
” |
| 5 | SA 41791 | Sun Java JDK / JRE / SDK Multiple Vulnerabilities | “Gain access to the system and execute arbitrary code with the local user privileges
DoS attacks |
21.62% | 13.10. 2010 |
“Highly Critical
” |
| 6 | SA 39259 | Apple QuickTime Multiple Vulnerabilities | “Gain access to a system and execute arbitrary code with local user privileges
Exposure of sensitive information |
12.16% | 11.11. 2010 |
“Highly Critical
” |
| 7 | SA 42475 | Winamp MIDI Timestamp Parsing Buffer Overflow Vulnerability | Gain access to a system and execute arbitrary code with local user privileges | 9.40% | 07.12. 2010 |
“Highly Critical
” |
| 8 | SA 31744 | Microsoft Office OneNote URI Handling Vulnerability | Gain access to a system and execute arbitrary code with local user privileges | 9.05% | 09.01. 2007 |
“Highly Critical
” |
| 9 | SA 42112 | Adobe Shockwave Player Multiple Vulnerabilities | Gain access to a system and execute arbitrary code with local user privileges | 8.78% | 03.11. 2010 |
“Highly Critical
” |
| 10 | SA 39272 | Adobe Reader / Acrobat Multiple Vulnerabilities | “Gain access to a system and execute arbitrary code with local user privileges XSS” |
8.18% | 14.04. 2010 |
“Highly Critical” |
In 2010, most of the list was populated by vulnerabilities in Microsoft products. In Q1 2011, however, there was only a single Microsoft product vulnerability and that was in 8th place. Vulnerabilities in Adobe products occupied five positions in the list, including 1st and 2nd places, while 4th and 5th positions were taken up by vulnerabilities in the Java Virtual Machine. Vulnerabilities were also present in popular media players such as Apple QuickTime in 6th place and Winamp in 7th.
All of the vulnerabilities that appeared in the Top 10 enable cybercriminals to take control of computers at the system level, which makes the other benefits seem relatively insignificant.
Conclusion
Most prevalent in Q1 2011 was the increasing number of attacks launched against various organizations. In addition to conventional DDoS attacks that block access to corporate servers for indeterminate periods of time, there were also many that focused on gaining unauthorized access to such servers in order to steal information. Attacks of this type fall into two broad groups.
Attacks within the first group are carried out with the aim of stealing data from corporate servers and selling it to third parties. It is important to note that as a result of an attack, the cybercriminals often gain access to personal data belonging to the clients of a targeted organization. This data can be used later for, among other things, carrying out targeted attacks against the companies where the owners of the stolen data work.
Attacks that fall within the second group are perpetrated as a form of protest. Such attacks are not carried out for financial gain and ultimately pursue a single goal – that of tarnishing the reputation of the targeted organization and destroying its public image.
The statistics collected from computers belonging to KSN subscribers show that users’ computers in the developing countries are at the highest risk of both local and web-borne infection. With local infections, the groups within the maximum and high risk brackets consist exclusively of developing countries. In the countries that fall into the maximum risk bracket, local threats are blocked on over 60% of all computers that have Kaspersky Lab’s security products installed on them, while the corresponding figure for the high risk bracket is 40-60%. IT penetration is increasing rapidly in these countries, and levels of IT security awareness may not always advance at the same pace. However, the most advanced Trojans such as TDSS, Sinowal and Zbot, etc, primarily target users in developed countries, including the US, Germany, the UK, Italy, France and Spain. It is the digital wallets of users living in these countries that the cybercriminals are really after.
According to data provided by the market research and analysis company IDC, smartphone sales have already surpassed PC sales. The growing popularity of the Android OS in the mobile market may soon lead to a situation similar to that which exists in the PC domain. Given the possible future domination of the Android OS, cybercriminals may concentrate their efforts on writing malware for this platform rather than diluting their efforts across a number of different platforms. Such tactics will assist the cybercriminals in infecting the largest possible number of users’ mobile devices.
The protection of mobile devices is currently complicated by the fact that personal smartphones are often used to store and send confidential information belonging to the companies that users work for. At the same time, company employees tend to underestimate the importance of protecting data stored on such devices.
The growing popularity of social networks, blogs, torrents, YouTube and Twitter increasingly alters the digital landscape. These services facilitate the swift and simple exchange of data between users located in every corner of the world. Data published in users’ blogs often gains as much credibility as official media outlets do. The popularity of such resources has already caught the cybercriminals’ attention. In future, the number of attacks carried out on and via these services is only likely to increase.


















IT Threat Evolution for Q1-2011