
IM clients
For many people, communicating online has become an integral part of daily life. The multitude of options for communicating with others – email, chat, forums, blogs, etc. — all occupy their own specific place on the Internet. Instant messengers (IM), which allow users to talk to others anywhere in the world in real time, are one of the popular alternatives.
In order to use IM, a user needs an Internet connection and a client application installed on their PC. There are lots of IM applications and almost all support the same basic functions, allowing a user to search for other users with similar interests, access personal profiles, choose a status mode, etc. A number of IM clients (or Internet pagers, as they are sometimes called) offer additional features.
The most popular IM client in Russia is undoubtedly ICQ – a playful abbreviation of the phrase “I seek you”. Every ICQ user has a unique number, or UIN (Unified Identification Number) that s/he uses to log on. Each UIN is protected by a password set by the user. Messages are sent via the TCP/IP transport protocol using a format specially created by the developer Mirabilis. As a rule, a single message consists of one TCP packet. Some other clients also make use of modified versions of this protocol to send messages, e.g. QIP (Quiet Internet Pager) and Miranda.
Microsoft’s MSN Messenger (or Windows Live Messenger) is another IM client popular with users in the West. MSN Messenger uses Microsoft Notification Protocol (MSNP, also known as Mobile Status Notification Protocol). The MSNP2 protocol is publically available, although other versions are not publically available. The latest version of MSN Messenger uses version MSNP14.
QQ, an IM application similar to ICQ, is very popular in China.
Figure 1. The Chinese IM client QQ
As well as standard IM functions, Skype also offers voice chat. This client, which is popular around the world, allows users to exchange voice messages for free. To do this, the user needs a headset and a computer with the application and an Internet connection. Skype can also be used to call any telephone number, although this is not a free service.
IM threats
Unfortunately, the virtual world is open to abuse and instant messaging applications are not immune. IM is often the target of the following malicious activities:
- Stealing passwords to IM accounts using brute force attacks or social engineering.
- Spreading malware (this can be done in two ways):
- Messages are sent which contain links; if the user clicks on the link, a malicious program file is downloaded to the user’s PC. Social engineering is used to tempt the user to open the file and by doing so, launch the malicious program.
- Messages are sent which contain links to infected websites.
- Spam.
All IM applications are vulnerable to some type of threat. Take, for instance, the popular Chinese IM client QQ. Trojan-PSW.Win32.QQPass, and a related program, Worm.Win32.QQPass, are both widespread in China and were specially created to steal QQ client passwords. WormWin32.QQPass propagates by copying itself to removable media along with an autorun.inf file (this ensures the worm will be launched on an uninfected computer as long as the Autorun function is enabled).
Skype has also not escaped the attention of virus writers. Worm.Win32.Skipi spreads via Skype by sending a link to its executable file to all Skype contacts on the victim machine. The worm also spreads by copying itself to removable media together with a file called “autorun.inf”. In addition to this, it will prevent antivirus solutions and Windows from being updated by editing the hosts file, and also attempts to terminate processes associated with security applications. And of course, the picture wouldn’t be complete without a Trojan: Trojan-PSW.Win32.Skyper is designed to steal Skype account passwords.
Microsoft’s MSN Messenger is actively used to spread IRC bots. Many of them are capable of propagating via the messaging client when they receive a command from a remote user via a backdoor. For instance, if a cybercriminal has a small botnet s/he wants to extend, s/he sends a command to backdoors on the infected machines. The command instructs the machines to send a message with a link such as http://www.***.com/www.funnypics.com to all MSN Messenger contacts on those machines. After that, everything depends on the person that receives the message. If he decides to look at the “funny pics”, that means another computer will be added to the zombie network – by clicking on the link the user downloads a backdoor to his/her machine.
Malicious users exploit MSN Messenger because it is included in the Windows installation package. This means all Windows users automatically have the MSN client on their machines. The popularity of MSN around the world makes it all the more attractive to cybercriminals wanting to increase the number of infected computers in their botnets.
Figure 2. Part of Backdoor.Win32.SdBot.clg.
The underlined sections show the commands used to spread the Trojan
ICQ threats
This section provides an overview of the most common attack methods used to target IM clients, using ICQ as an example.
Password theft
As mentioned above, all ICQ users have a Unified Identification Number, or UIN. At the moment, nine-digit numbers are the most common. However, many users are keen to have a UIN that is identical to their mobile phone number, a numerical palindrome, or in which all the digits are the same. Such UINs are easy to remember and, for some, a matter of prestige. ICQ numbers with five, six or seven digits, which may contain only two different numbers, are seen as being particularly valuable.
‘Attractive’ UINs are traded, often fetching high prices. Many sites even have a number ordering service that promises to “obtain” the number wanted by the customer. Moreover, batches of unremarkable nine-digit numbers are offered to those interested in sending mass mailings. Using multiple numbers to distribute spam makes it possible to evade the anti-spam denylists used by irritated users to ignore specific numbers.
The vendors of such ‘prestigious’ numbers rarely mention how the numbers are obtained. E-commerce sites contain assurances that the UINs are being sold legally. In most cases, however, the vendor has acquired the ICQ numbers by illegal means.
A number of methods are used to steal UINs. The multitude of Internet stores selling attractive UINs often engage in industrial-scale password searches and account theft. Another method is to steal the password to the ICQ user’s primary email and then use it to change the original UIN password without the user’s knowledge. Here’s a more detailed overview of how this works.
ICQ technical support offers a service for users that have forgotten their UIN passwords. The process of restoring a password has been modified several times and has become more sophisticated. It now acts as a fairly reliable safeguard against password theft. Users are required to answer a question that they themselves set. If they have forgotten the answer, then the question can be changed using their primary email – the email address entered in the contact information during registration. The process is reasonably secure, but if a third party has somehow gained access to the primary email, the UIN is there for the taking. After obtaining the password to the primary email it is possible for a malicious user to contact ICQ pretending to be an account holder who has forgotten his or her UIN password. The malicious user can then prevent the original owner from accessing not only his or her ICQ account but also the primary email simply by changing the old password. Theft of this kind is not easy – obtaining passwords to email accounts linked to ICQ numbers requires a very powerful computer or even network.
However, the most popular method for stealing ICQ numbers is by using malicious programs, and Trojan-PSW.Win32.LdPinch in particular. It’s over the last few years that this family of Trojans has come to pose a threat to users. LdPinch not only steals passwords to ICQ and other IM clients such as Miranda but also to email accounts, various FTP programs, online games etc. There are dedicated constructor programs designed to create specific types of malicious Trojans. Such programs make it possible to set parameters defining which user passwords the malware will steal once installed on the victim machine. Once the program has been configured, the malicious user only has to provide an email address where confidential information will be sent. The ease with which these malicious programs can be created means they are prevalent not only in mail traffic but also in IM traffic.
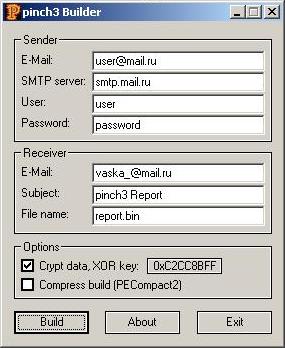
Figure 3. Constructor used to create Trojan-PSW.Win32.LdPinch
Spreading malicious programs
Mail traffic contains a range of malware families which either spread themselves, or are sent via spam. ICQ, however, is generally used to spread three types of malicious program:
- IM worms – these malicious programs use the IM client to self-propagate.
- Trojans designed to steal passwords, including passwords for ICQ numbers (in the vast majority of cases, it is Trojan-PSW.Win32.LdPinch).
- Malicious programs classified by Kaspersky Lab as Hoax.Win32.*.* (malware created to fraudulently obtain money from users).
How exactly is ICQ used to spread malware?
IM worms require little or no user interaction to spread. When run, many IM worms send themselves to the IM contacts on the victim machine. These worms have a range of functions: they can steal passwords, create botnets and, sometimes the payload is purely destructive (e.g. deleting all .mp3 files from the victim machine). Malicious programs such as Email-Worm.Win32.Warezov and Email-Worm.Win32.Zhelatin (Storm Worm) have used ICQ to actively spread.
However, in most cases user action is required to ensure that an attack will be successful. A wide variety of social engineering ploys can be used to make a potential victim click on a link, and open a file if one is downloaded from the link.
Here’s an example of an attack designed to download malware to the victim’s machine. First of all, the malicious user creates several user accounts with seductive profile information (e.g. “pretty girl, 22, looking for a man”). Bots (small programs with primitive intelligence that can support a basic conversation) are then linked to that profile number. The first thing users usually want to see is a photograph of the “pretty girl”; the bot responds to such requests by sending a link. Needless to say, the link doesn’t lead to a photo, but to a malicious program.
A variation on the above is when a link to a malicious program is inserted in the personal details of the “girl”. This type of attack requires more effort than the previous method. For example, at least a few of the main personal information fields have to be filled in and potential victims have to be selected. Then a conversation has to be struck up to ensure that users are tempted to click on the link to “nice photos from the Pacific coast” in the “girl’s” personal details.
Social engineering ploys are also used when spreading malicious programs with the help of ICQ spam. More precisely, it’s not the malware itself that is spread – users are sent links to malicious programs.
Links in spam can also lead to sites (legitimate ones that have been hacked, or ones which have been specially created) which contain Trojan-Downloader programs. These downloaders then install other malicious software on the victim computer. A more detailed description of such attacks is given below.
Browser vulnerabilities (in particular, those in Internet Explorer) are frequently exploited to download malware with the help of malicious code already placed on a website. First of all, a popular legitimate site will be attacked, and code (e.g., iframe or encrypted JavaScript) placed on its pages. This code will in turn download a malicious program to the computers of those who visit the site. Another technique is to create a simple site on cheap or free web hosting – a site which contains similar downloader code. The site will then be advertised using mass mailing via IM mailing. If a user clicks on a link to the site, malicious software will be secretly downloaded to the victim machine. The user may not even suspect that the site s/he visited was attacked or was a fake. Meanwhile, LdPinch or IRCBot will be busily running on the infected computer.
The vulnerabilities used in carrying out such attacks can be present in the instant messaging applications themselves. In many cases the vulnerability can lead to buffer overflow and the execution of arbitrary code on a system, or provide remote access to a computer without the user’s knowledge or consent.
If the malicious code that is run on a system after a buffer overflow is able to self-propagate, then by using the same application vulnerability on other machines the program can penetrate the computers of a significant number of users, causing an epidemic. Exploiting vulnerabilities requires a high degree of technical skill, and this limits, to some extent, the options open to cybercriminals.
ICQ spam has recently been used to spread fake programs that supposedly generate pin codes for cards used to pay for various mobile phone services. Kaspersky Lab detects these programs as not-virus.Hoax.Win32.GSMgen. In actual fact, such software generates unlimited quantities of randomly generated numbers that are supposed to be pin codes for cards used to top up telephone accounts. The results generated by the program are encrypted and in order to decipher them a key has to be obtained from the author, which, of course, comes at price. The sum is usually small – about $10-$15 – which makes the offer even more attractive. The reasoning goes something like this: “I pay $15 once and then I can use my mobile phone for the rest of my life for free!” The fact that the number received in return for payment does not top up an account makes this an everyday case of fraud. (It should be noted that if the program did indeed generate pin codes to pay for mobile services, the price would be significantly higher, and the authors would keep a much lower profile so as not to attract the attention of mobile operators and law enforcement agencies.)
ICQ spam
Unlike email spam, ICQ spam has not been researched in depth. Below are the results of a small study conducted from February 23 to March 23, 2008. The research involved categorizing the subjects of unwanted messages sent to ICQ users and performing a comparative analysis of ICQ spam vs. email spam.
Popular subjects in ICQ spam
The subjects in ICQ spam messages are quite varied and can include advertisements for a new website or game server, requests to vote for somebody in a contest, offers to buy expensive mobile phones at reduced prices or messages that include URLs that lead to malicious programs. A spam link can lead to a website with an exploit that uses vulnerabilities in Internet Explorer or other popular browsers (messages with malicious links were not classified as a separate category for the purposes of this study).
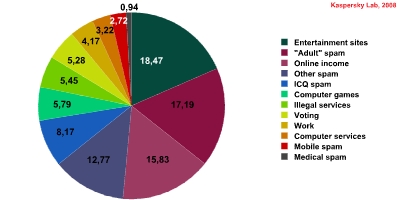
Figure 4. Distribution of ICQ spam by subject
Advertising of Entertainment Sites (18.47%) came top of the rankings. In all probability, this category will continue to lead the ICQ spam statistics. The main reason for its popularity is the effectiveness of this type of spam. Take a typical situation when someone who has been working on a computer for a long period receives an ICQ message about a new website with lots of funny images/stories/videos etc. It is very likely that the tired user will follow the link in the message as a diversion from work.
The Adult Spam category in second place (17.19%) circulates messages similar to those in email spam that advertise dating sites, porn resources, individuals pages which contain erotic material etc.
The Online Income category (15.83%) includes messages that promise money in return for clicking on banners, visiting certain websites and looking at advertising. It also includes network (or multilevel) marketing offers.
The Other Spam category (12.77%) consists of messages on different subjects, each of which account for a relatively low percentage of spam traffic, making it impossible to classify them in individual categories. Some of the message authors in this category have very vivid imaginations. They send a variety of chain letters, toothpaste ads, predictions by archbishops of a fascist dictatorship in Russia, etc. Among the goods advertised, DVDs and car parts are predominant. ICQ phishing messages, which will be discussed later in this article, also fall into this category.
Messages related to ICQ in some way were included in the category in fifth position of our ranking (8.17%). One interesting phenomenon is “ICQ chain letters”, most of which contain the following text (translated from Russian):
service. You can prevent this, send this message to
20 people from your contact list. This is not a
joke (source www.icq.com) If you send it 20
times you will receive an email and your flower
will beCome blue. I.e. you will be among those
who are against. If voting wins, ICQ will
reMain free.”
The only things that change are the date and the number of people to whom the message is supposed to be sent. Interestingly, some messages contain multi-level quoting, indicating that many users really believe someday their “flower will become blue” and ICQ will remain free forever.
Messages in different languages that urge users to upgrade to the new, sixth version of the ICQ client are also sent on a regular basis. At first, it was unclear why these messages were so popular among spammers. There was unconfirmed information that ICQ 6.x includes a vulnerability that leads to errors when processing messages formed in a certain way. On February 28, 2008 this was confirmed: according to http://bugtraq.ru, “…sending a specially formed … message (in the simplest case, “%020000000s”) to a user with ICQ 6.x installed results in an error when generating HTML code to display messages in the embedded Internet Explorer component. This error may lead to the execution of arbitrary code on the remote system.” This vulnerability is not present in the latest build of the ICQ client.
Messages in the Computer Games category (5.79%) can be divided into two large groups. Messages in the first group advertise various browser-based online games, those in the other – game servers, mostly for Lineage II and Counter-Strike.
Offers of Illegal Services (5.45%) are only one third of a percentage point behind computer game ads. These offer users the chance to get the password to a specific mailbox, organize a DoS attack, make counterfeit documents (both Russian and non-Russian), and learn how to hack credit cards or obtain the information necessary to do so – all for a price.
Eighth position (5.28%) went to the category containing messages that ask users to vote for specific participants in a range of Internet contests.
Job and joint business offers came ninth (4.17%) and offers of computer services, including hosting, tenth (3.22%).
The Mobile Spam message group at the end of the rankings (2.72%) also consists of two types of messages. The first type includes messages that advertise websites selling mobile phones. The prices of popular models on such sites are often significantly lower than market prices, raising suspicions as to the origin and legality of such telephones. The second type is messages that advertise sites with a variety of mobile content.
During the period from February 23 to March 23, 2008, no more than 1% of messages in ICQ spam were found to be advertising medications or health related services.
Phishing messages are also occasionally sent to ICQ users. These messages were not categorized as an individual group because they are relatively rare. Cybercriminals use social engineering methods when attempting to obtain passwords to users’ UINs. The success or failure of such attacks largely depends on how well informed a user is. If there are genuine problems, as a rule the official ICQ support service will inform users of the problems, but it will never ask them to send their passwords by email or enter it in a web form on a website.
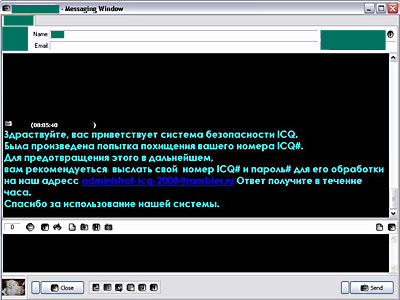
Figure 5. Phishing message sent in an attempt to obtain an ICQ account password
has been made to steal your ICQ number. To prevent this in the future, it is
recommended that you send your ICQ number and password for processing to
our address administrat-icqo2008@rambler.ru. You will receive a reply
within an hour. Thank you for using our system.
Distinguishing characteristics of ICQ spam
Unlike email, ICQ makes it possible to search for people based on the interests described in their user contact information. This makes it possible for cybercriminals to target specific audiences with their spam. It is fairly easy for spammers to get relevant data (in most cases, the ages and interests of users) and use it to gain the attention of spam recipients.
Practically all spam messages come from UINs that are not on the user’s contact list. The number of unwanted messages received by a user in any given period of time depends on the UIN. Users with six-digit UINs receive an average of 15 to 20 unwanted messages every hour, many of which contain links to Trojan-PSW.Win32.LdPinch. Users with nine-digit numbers that have nothing special about them receive an average of 10 to 14 such messages every day, while users with ‘attractive’ numbers get 2 to 2.5 times more spam.
In terms of message subjects, ICQ spam significantly differs from email spam. While about 90% of email spam advertises various goods and services, the proportion of such advertising in ICQ spam is less than 13% (the total share of the Illegal Services, Computer Services, Mobile Spam and Medical Spam categories), with Illegal Services (5.45%) being the largest of all the categories offering services.
On the whole, entertainment-related subjects predominate in ICQ spam. The reason for this is that ICQ is rarely used for business communication, while most of its users are young people. Spammers take the interests of their target audience into account: ICQ spam is dominated by invitations to visit entertainment sites and by ‘adult’ advertisements. Spam in the Computer Games, Voting and Mobile Spam categories also targets young people. On the whole, young people are targeted by about 50% of all spam messages.
The low share of ‘medical’ spam (traditionally a leading category in email spam) is also determined by the target audience. In ICQ spam, the share of this category is below 1%. Apparently, ICQ users do not respond as required to advertising of medical goods and services.
Distinguishing characteristics of ICQ spam:
- Targets a young audience.
- Overall bias towards entertainment.
- Virtually no advertising of consumer goods. Exceptions are offers for mobile phones and pharmaceuticals, as well as a small number of messages which fall into the category of Other Spam.
- Relatively high percentage (8.17%) of messages related to ICQ itself.
- Significant proportion (5.45%) of messages offering illegal services. The most popular offers are email and ICQ hacking, counterfeit documents, credit card hacking.
An attack scenario
The user launches a file downloaded using a link received via ICQ, but the photo promised by the spammer never shows up on the screen. The user waits for a minute or two, and in the meantime the Trojan searches the computer for passwords stored on it. Some of the passwords are encrypted, but they can be easily decrypted by the cybercriminal. Then the Trojan collects all the passwords found and creates an email message containing all the confidential information collected. The message is sent to the cybercriminal’s email address which was created a couple of days prior to the attack. To prevent the Windows firewall from warning the user of the danger, the Trojan disables the firewall by modifying the relevant registry key. The Trojan also takes similar action against other programs that could prevent it from stealing passwords and other important information from the user. Finally, the malicious program creates a .bat file that deletes both the Trojan and itself, thereby destroying any traces of malicious activity.
By the time a user begins to suspect that something suspicious is going on, the hacker will have processed tens or hundreds (depending on the mailing size) of messages with passwords sent by the Trojan. Incidentally, many users remain unaware that any malicious activity has taken place at all. In any case, the only evidence the user has is a link to a non-existent photo, so the chances of tracing the cybercriminal are very slim.
Users often console themselves by saying they had nothing of importance on their computers anyway. But a hacker or cybercriminal wouldn’t agree: s/he now has an impressive list of passwords to email accounts, FTP clients and online games, as well as the user’s bank account and, yes, the ICQ account itself.
You could ask why the hacker might need one more nine-digit number that nobody knows. This is why: s/he will enter the password in their ICQ client and gain access to the user’s contact list. A message will then be sent to all users on the contact list asking them to lend 50 e-dollars and promising to repay the debt the next day. The rest will depend on the recipients’ generosity and their relationship with the user whose account has been stolen. Usually, it is not too difficult to persuade a hesitant user to oblige. At the same time, the hacker will be chatting to other users on the contact list, trying to persuade them to pay up as well. Even if only one person on every victim’s contact list agrees to pay the virtual money to the hacker, the latter will receive a considerable amount of money comparable to the daily wages of a good programmer or even more – all for an hour of chatting.
What about the FTP account? What will happen if the FTP server to which the cybercriminal gained access using the stolen password stores the web pages belonging to a sufficiently popular website? The cybercriminal will be able to add a simple iframe or encrypted JavaScript code at the end of each web page, which will surreptitiously download and launch a malicious program to all computers used to view the site.
All the actions described above are easy to automate. A cybercriminal can easily find ICQ UINs to send spam to on numerous dating sites and forums. More precisely, this will be done by a special program that does all the routine work, including filtering out duplicate numbers and checking the spam list for inactive numbers. Then the hacker will upload a Trojan to a website registered with a free hosting service and will send a link to the website using the spam list created by the hacker’s software. After this, another program will sort the numerous messages sent by the Trojans launched on victim computers and categorize the passwords received. The list of new ICQ numbers received from the Trojan will be converted to a new spam list. If an infected user’s ICQ number turns out to be attractive (i.e., easy to remember), it can be sold later for a large amount of money. And then the final stage – sending messages with convincing requests to lend a little money. If a reply to the request is received, it’s time for the hacker to get involved and use his or her knowledge of psychology and social engineering techniques. After this, the ‘hijacked’ numbers can be sold wholesale to spammers. The process described above may sound like fiction, but in actual fact, such schemes are quite common.
To summarize, here’s a list of why cybercriminals attack IM clients:
- Selling stolen ICQ numbers (nine-digit numbers are sold wholesale and ‘attractive’ numbers are sold individually for significant amounts of money).
- Creating spam lists for sale to spammers or for mass distribution of malicious programs.
- Using the contact lists of victims as trusted sources to ‘borrow’ money.
- Downloading malicious programs using software vulnerabilities.
- Changing the web pages of legitimate sites (using FTP server passwords) to download malicious software to visitors’ computers.
- Creating botnets or extending existing zombie networks.
- Other malicious activity.
Counteracting attacks on IM systems
What can users do against such sophisticated and relentless attacks? Defend themselves, naturally! Below is advice to help readers protect themselves against threats that spread via IM clients.
First of all, be careful and do not click thoughtlessly on links in received messages. Listed below are several types of messages that users should view with extreme caution:
- Messages received from unknown users with strange nicknames (such as SbawpathzsoipbuO).
- Messages from users on your contact list which ask you to take a look at new photos which have an.exe file extension.
- Messages that allegedly contain sensational news of an affair between two celebrities with “a report from the scene”. The ‘report’ in this case is usually a link to the following file: http://www.******.com/movie.avi.exe. It is highly likely that this link will lead to Trojan-PSW.Win32.LdPinch.
- Messages suggesting that the user download a program which will provide new opportunities e.g., “NEW BUG in ICQ enabling you to create any number that does not exist”. A link in the message will no doubt lead to a program, but that program will steal the user’s UIN rather than create a new account number.
Such messages should simply be ignored.
If a message comes from a user you know, find out whether they really sent it. And of course, do not download a file with an .exe extension and launch it. Even if the file extension is not specified in the link, you could be redirected to another page that contains malicious software.
As always, users should observe the elementary rules of ‘computer hygiene’: an antivirus product with up-to-date databases and a firewall which blocks unauthorized network connections should be installed on the computer. It is a good idea for the antivirus product to include proactive protection that detects malicious programs based on their behavior and/or a heuristic analyzer.
Users are often unaware of the fact that a malicious program has been run on their computer. Friends or contacts may provide clues to the fact that the PC has been infected. One example would be a friend asking “Why did you ask me to lend you 50 WebMoney units yesterday when we chatted on ICQ?” when the real owner of the ICQ account did no such thing. Another, even more obvious, indication of an infection is a fruitless attempt to use the login or password for a service: unsuccessful authorization attempts mean that the password has been changed. By whom? Either by the official service provider or by a cybercriminal. In the first case the user will either get a new password or notice that the password has been changed sent via email or some other means. If a cybercriminal is to blame, this will not happen.
What should be done if a Trojan has delivered its malicious payload and then deleted itself from the computer? First of all, make sure the computer really is clean by scanning it with an antivirus program. Then change any passwords the Trojan may have stolen, if possible. To do this, try to remember which programs require passwords and try to enter these passwords. If your attempt is successful, change the password immediately. It also makes sense to send the relevant alert to all users on your contact list and ask them not to respond to requests sent from your IM account asking to borrow money, and not to attempt to view photos by following links sent in an IM message.
Installing the latest version of ICQ downloaded from the official ICQ website can help to prevent execution of arbitrary code on the system that is made possible by an ICQ 6.x vulnerability related to processing HTML code.
You can take the following steps to protect yourself from ICQ spam.
Since spammers can check a user’s ICQ status using a website, it makes sense to block this feature in your ICQ client. Spam mailings usually target users who actively chat on ICQ or at least are always online. Therefore, it’s best to remain in invisible mode whenever possible. However, some programs can tell other users whether you are actually offline or just invisible. In this situation, you can use an anti-spam bot – a simple module supported by some IM clients (such as QIP). The screenshot below shows the configuration of a simple anti-spam bot.
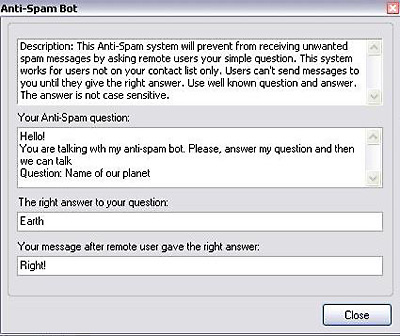
Figure 6. Configuration of a simple anti-spam bot
How does an anti-spam bot work? If a user who is not in your contact list wants to chat to you, they will have to answer a question before they can start chatting. They will not be able to send you any messages until the question is answered. It is a good idea to use questions that everyone knows the answers to, such as “how much is 2+2*2?” or “what is the name of our planet?” If the user writes “6” or “Earth” respectively and sends the message, they will then be allowed to send you further messages. This protection is relatively successful at blocking a range of bots that send spam, although some of these bots may be intelligent enough to answer the most popular questions, e.g., the default questions used in protection modules.
Conclusion
Instant messaging programs are very attractive to malicious users of all kinds, and because of this the problem of malware distribution via IM clients is serious. New versions of IM clients contain as yet unknown vulnerabilities, which can be identified first by hackers and only afterwards by program developers. Such situations can easily lead to mass epidemics. Some users are also extremely tired of getting unwanted messages (IM spam).
Currently, there are no methods or solutions designed specifically to protect IM clients. However, observing the simple rules of ‘computer hygiene’, and using a well-configured anti-spam bot combined with a healthy dose of common sense can help users enjoy worry-free chat via the Internet.






















“Instant” threats