
Instant messaging (IM) has its origins in low-level, John-to-Judy communications. John can’t do his assignment. He dashes off a five-word message to Judy who punts him the right answer. The whole operation is done in under fifty keystrokes. Ten words, a few smilies and an answer. Cool. With none of the formalities or obligations of email, IM brought us a communication channel which allows us to squeeze off banalities or shoot out occasional brilliance in an irresponsible but socially acceptable way. You can even ignore each other as you go about your day while still feeling somehow connected. Its core attraction is the fact that it allows the teenager in each of us to communicate without having to say anything deeply significant – or even anything at all. But IM has moved out of the bedroom and into the office. And there the consequences are more serious.
Instant messaging is useful at work for the same reasons it’s fun in the bedroom: informal, friendly and quick, it can facilitate fast answers to questions and strengthen goodwill at the same time. But instant messaging also has several downsides. It can be a major time-waster and distraction. If you use one at work, you’ll know how true that assertion is. But more importantly, it adds vulnerability to the informational environment – and herein lies the focus of this paper.
Vulnerability is increased in several ways. Firstly, there is an array of malicious programs designed to attack IM protocols. Secondly, vulnerabilities in the client program make it a target for hackers. Thirdly, confidential information sent over IM is easy pickings for competent and motivated people who want it. Add to the mix a disgruntled or disloyal company employee with a will and a way to transfer confidential data out via IM, and the reasons why you should start worrying right now become compelling.
Since the organisations participating in this study are Russian, this research has a Russian emphasis. However, since Russia’s IT environment bears comparison to that of any technologically developed country, this study’s findings are equally relevant to an international audience.
- Index of graphs and tables
- Summary
- Methodology
- Respondent profiles
- IM-client usage
- How IM affects IT security
- Security policies
- Protection from IM threats in the real world
- Recommendations for secure IM usage
- Effectiveness of typical methods
- Conclusions
Index of graphs and tables
- Fig. 1 – Number of computer-based workplaces
- Fig. 2 – IM-client usage
- Fig. 3 – Threats arising from IM usage
- Fig. 4 – Sending of confidential information by IM
- Fig. 5 – IM-policy enforcement across the company
- Fig. 6 – Methods of defence from IM threats in use
- Fig. 7 – Recommended methods of defence from IM threats
- Fig. 8 – Protection for confidential correspondence
- Table 1 – Policy effectiveness in companies of various sizes
- Table 2 – Policies and confidential information leaks
- Table 3 – Correlation between protection measures and company size
- Table 4 – Protection measures vis-à-vis degree of threat danger
Summary
- The overwhelming majority (92.4%) of respondents acknowledged the dangers associated with information technologies, but almost one in two (48.6%) did nothing of a practical nature to prevent undesirable events from occurring
- The leak of confidential information (41.4%) was seen as the chief threat arising from IM clients. And not without cause. One in four respondents (27%) admitted to sending classified information via an IM client and another 15.8% were unable to give an unambiguous answer to this section of the survey
- Almost half the companies (43.8%) which had protection measures in place against IM threats used traffic blocking, and almost a third (28.6%) used administrative restrictions. This indicates that those surveyed preferred to block rather than manage this communication channel
- Over half the respondents (57.9%) who used traffic blocking considered it an effective measure whereas three-quarters of companies regarded administrative restrictions (74.7%) and IM-traffic monitoring (78.9%) the most effective means of dealing with threats via IM
- Despite the risks, small businesses (up to 100 workstations) were found to have installed systems to protect against threats via IM 23.8% less often than big companies (over 501 users); the latter protected themselves in this regard a mere 66.8% of the time
Methodology
The survey was conducted between May 1st and June 1st 2007 and is based on the answers of 1101 respondents worldwide who participated via an online questionnaire (see Appendix) on SecurityLab.ru. The questionnaire was directed toward SecurityLab.ru’s highly professional readership which is made up mainly of experienced specialists in the area of information technology and information security.
The first Russian survey concerning IM-client security in the corporate environment was conducted by the InfoWatch Analytical Centre in mid-September, 2005. Despite the fact that the respondent base today is somewhat different, some parallels may still be drawn; in comparing current results with those of two years ago, the InfoWatch Analytical Centre will limit itself to only the broadest tendencies.
Respondent profiles
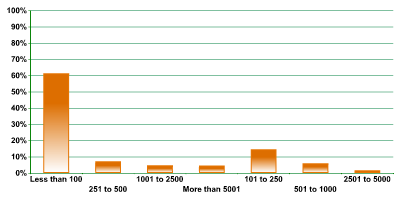
Fig. 1 profiles respondents by the number of computerised workplaces in the organisation. The greatest number of participants worked in small businesses (61.3%) with less than 100 workstations. Medium-sized businesses (101-500 workstations) garnered 21.7%. The remainder (17.0%) represented large enterprises. Survey results relating to company size are segmented along these lines throughout.
Fig. 1 – Number of computer-based workplaces
IM-client usage
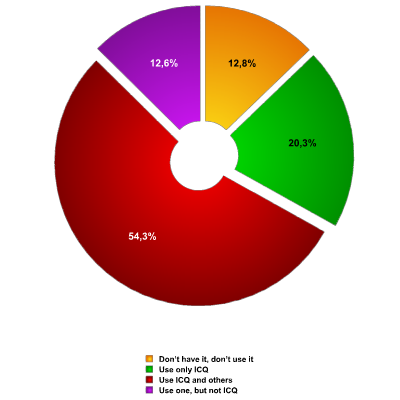
The survey showed (fig. 2) that the vast majority of users (74.3%) used ICQ as their IM client. ICQ is very popular in Russia as a whole, and this number merely reflects the general adoption of ICQ among the population. However, over half (54.3%) of respondents used additional IM clients in tandem. Almost the same as two years ago: 12.8% of those surveyed used no IM client at all.
Fig. 2 – IM-client usage
We see that IM technology has become a core business communication tool. Earlier rumours about its imminent demise due to security issues have not materialised. The benefit to business which IM brings is such that the majority of companies are prepared to bring in IM clients, security issues or no – a fact which is not lost on the cyber criminals – which in some way explains the growing number of malicious programs designed to exploit IM’s vulnerabilities. And that’s without even getting into the realm of insider activity.
How IM affects IT security
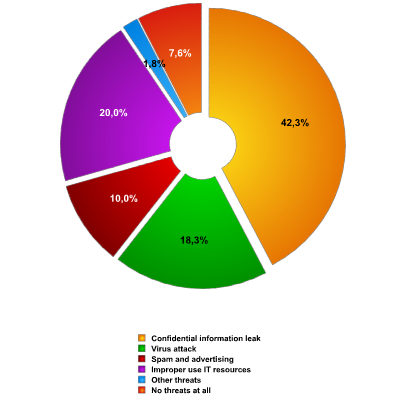
Fig. 3 shows the chief threats connected with IM usage. The leak of confidential information (42.3%) takes pole position with risks arising from virus attacks and improper use of IT resources attracting around a fifth of the votes each. Spam and advertising garnered 10%. Only 7.6% of respondents considered IM usage free from risk.
Fig. 3 – Threats arising from IM usage
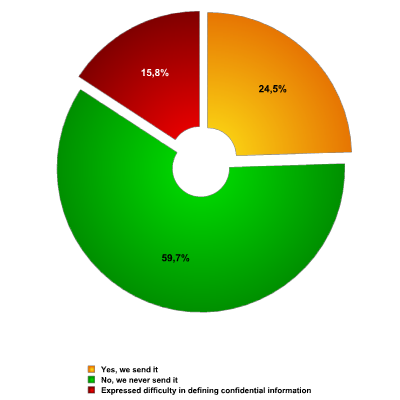
Respondents were also asked about the primary issue arising from IM usage: confidential information leaks (see: fig. 4). We found that only 59.7% were confident that they had never sent confidential information via IM and 24.5% admitted to having sent confidential information occasionally.
One suspects that the real number of people who sent out confidential information by this channel is actually higher, but that there was understandable resistance to admitting to such behaviour.
Fig. 4 – Sending of confidential information by IM
Security policies
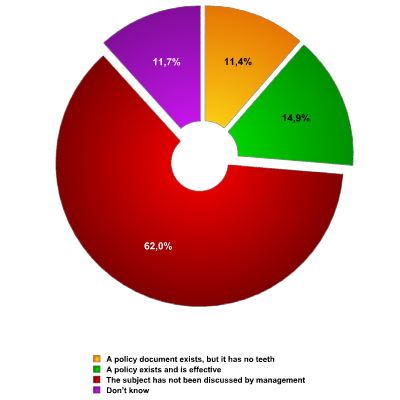
The introduction of a robust information security policy is, perhaps, the simplest means of reducing risk from IM. Despite this, 62.0% of respondents stated that their companies did not have such policies in place with only 14.9% of respondents regarding their companies’ policies as effective. Multiple answers were permitted.
Fig. 5 – IM-policy enforcement across the company
Table 1 shows the correlation between policy implementation and company size. We see that the larger the company, the more likely it is to have an information security policy in place and enforced. However, the damage a confidential information leak could do to a smaller company is potentially greater since it might easily go under after the theft of only a few key documents.
| No policy exists | A policy exists and is effective | A policy document exists, but it has no teeth | Don’t know | |
| Small business | 69.2% | 9.3% | 10.9% | 10.6% |
| Medium-sized business | 61.9% | 18.0% | 11.1% | 9.0% |
| Big business | 39.5% | 28.1% | 13.7% | 18.7% |
Table 1 – Policy effectiveness in companies of various sizes
Table 2 shows the correlation between the sending of confidential information and existence of a corporate security policy relating to IM. The resulting data gives rise to two more conclusions. Firstly, an effective policy approximately halves the risk of a confidential information leak, but does not eradicate it completely. Secondly, an ineffective policy not only does not reduce risk, it actually increases the likelihood of confidential information being sent out. The lesson is clear: if an organisation plans to introduce a directive regarding the use of IM clients, it should see to it that it is effectively enforced.
| A policy exists and is effective | A policy document exists, but it has no teeth | Don’t know | |
| Yes, we send it | 78.1% | 53.1% | 60.3% |
| No, we never send it | 61.9% | 18.0% | 11.1% |
| Expressed difficulty in defining confidential information | 6.9% | 16.5% | 16.1% |
Table 2 – Policies and confidential information leaks
Protection from IM threats in the real world
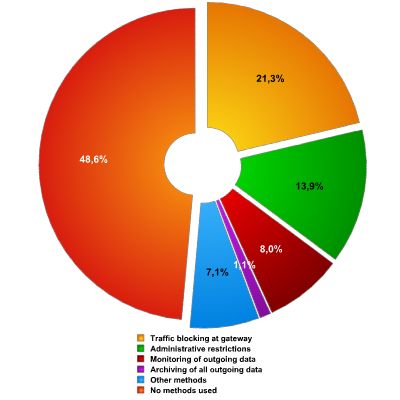
The remaining means of defence against IM threats are seen in fig. 6. These figures show that almost half (48.6%) of companies have no defence whatsoever to IM threats, and among those which do, the primary tactic is traffic blocking. Purely controlling methods (monitoring) are yet to acquire wide acceptance, probably since their implementation would give rise to technical problems and user resistance.
Fig. 6 – Methods of defence from IM threats in use
Predictably, larger companies take various steps to protect themselves from IM threats more often than smaller companies. It is disappointing that the increase is achieved in the main due to purely prohibitive measures such as traffic blocking. The use of controlling measures is observed across the board at around 8-10%.
There are tools which facilitate effective control such as traffic monitoring and archiving. By warehousing all outgoing data in a backup facility, organisations can significantly reduce the risk of leaks since users know that all outgoing information is being stored. And if a leak occurs, the archive can be queried to find out who did what and when. Moreover, a whole slew of governmental and industry regulations make the archiving of electronic company correspondence mandatory.
| Administrative restrictions | Traffic blocking | Monitoring | Archiving | Other | No measures | |
| Small business | 13.0% | 16.5% | 8.1% | 0.6% | 5.8% | 56.0% |
| Medium-sized business | 14.7% | 29.4% | 7.2% | 1.9% | 6.2% | 40.6% |
| Big business | 14.9% | 30.2% | 9.9% | 2.2% | 10.6% | 32.2% |
Table 3 – Correlation between protection measures and company size
Table 4 shows the correlation between measures taken and the most dangerous threats. We found that administrative restrictions and traffic blocking were the most widely used means of preventing IM threats; monitoring was the most rational method when the core risk the company faced was that of confidential information leak; and almost half the users who accepted the threat presented by IM programs took no preventative measures whatsoever
| Administrative restrictions | Traffic blocking | Monitoring | Archiving | Other | No measures | |
| Confidential information leak | 14.2% | 25.4% | 12.0% | 1.6% | 6.6% | 40.2% |
| Virus attack | 14.3% | 18.2% | 4.9% | 0.4% | 5.9% | 56.3% |
| Improper use of IT resources | 16.4% | 29.1% | 5.3% | 1.1% | 4.3% | 43.8% |
Table 4 – Protection measures vis-à-vis degree of threat danger
Recommendations for secure IM usage
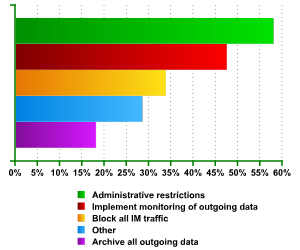
The survey also asked for input on desirable means of threat prevention. It revealed that the means which respondents had in place were not those which, ideally, they would have liked to see. Since respondents were invited to choose more than one option, the total figures here exceed 100%.
Fig. 7 – Recommended methods of defence from IM threats
Unlike “actual” methods, the “recommended” methods incline toward the implementation of user controls such as administrative restrictions and monitoring. This can be explained by the unpopularity of directly prohibitive methods and by the fact that IM usage has clear business-related benefits.
Effectiveness of typical methods
The survey compared the effectiveness of the methods already in place with regard to those considered desirable. Only 57.9% of respondents who used traffic blocking recommended it, while among those who used administrative restrictions and monitoring 74.7% and 78.9% respectively recommended their practices. On this backdrop, traffic blocking came a poor third in terms of customer satisfaction.
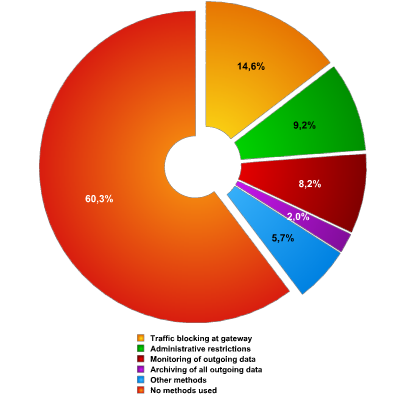
Fig. 8 indicates the level of protection among those who admitted to sending confidential information by IM. The survey showed that 60.3% of companies in which these respondents worked had no IM protection in place whatsoever. This is a situation which will, doubtless, be exploited for elicit gain in due course by criminal elements.
Fig. 8 – Protection of confidential correspondence
Conclusions
This survey confirms our view of two years ago that IM technologies are becoming a core business tool. A groundswell of companies is beginning to realise the risks that use of such technologies present and take precautionary measures. However, many companies are choosing to ignore the issue entirely, leaving themselves wide open to insider activity.
With the continued use of IM technologies in the business environment taken as a given, the number of tools designed to protect companies from the attendant risks can be expected to rise. The number of companies which ignore the issue will decrease over time, while demand from the companies themselves and supply from solutions vendors will increase on the back of escalating threats and actual high-profile cases of confidential information loss via the IM channel due to insider activity.


















Instant Messenger: making business friendlier but less secure