
I recently came across an interesting IRCBot which KAV detects as Backdoor.Win32.IRCBot.lo.
When I took a closer look at it, I found out that it’s quite an advanced bot with a lot of features.
The thing which interested me most was the ability of the bot to spread via IM. There’s support for just about every IM-client.
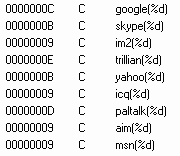
It also started me thinking about the way malware which spreads via IM has evolved over the last year, specifically the shift from IM-Worm+IRCBot to ‘IM-Bot’ – an IRCBot which also includes IM-Worm functionality.
We’ll have an article about this on viruslist in the near future.




















IM-Bot?