
All your arm are belong to us
The IoT world has long since grown beyond the now-ubiquitous smartwatches, smartphones, smart coffee machines, cars capable of sending tweets and Facebook posts and other stuff like fridges that send spam. Today’s IoT world now boasts state-of-the-art solutions that quite literally help people. Take, for example, the biomechanical prosthetic arm made by Motorica Inc. This device helps people who have lost their limb to restore movement.
Via dedicated sensors, the biomechanical prosthetic arm reads the muscle contraction parameters and analyzes them to produce movements with the robotic fingers. The arm takes little time to get used to standard movements, after which it becomes a full-fledged assistant.
Like other IoT devices, the prosthetic arm sends statistics to the cloud, such as movement amplitudes, the arm’s positions, etc. And just like other IoT devices, this valuable invention must be checked for vulnerabilities.
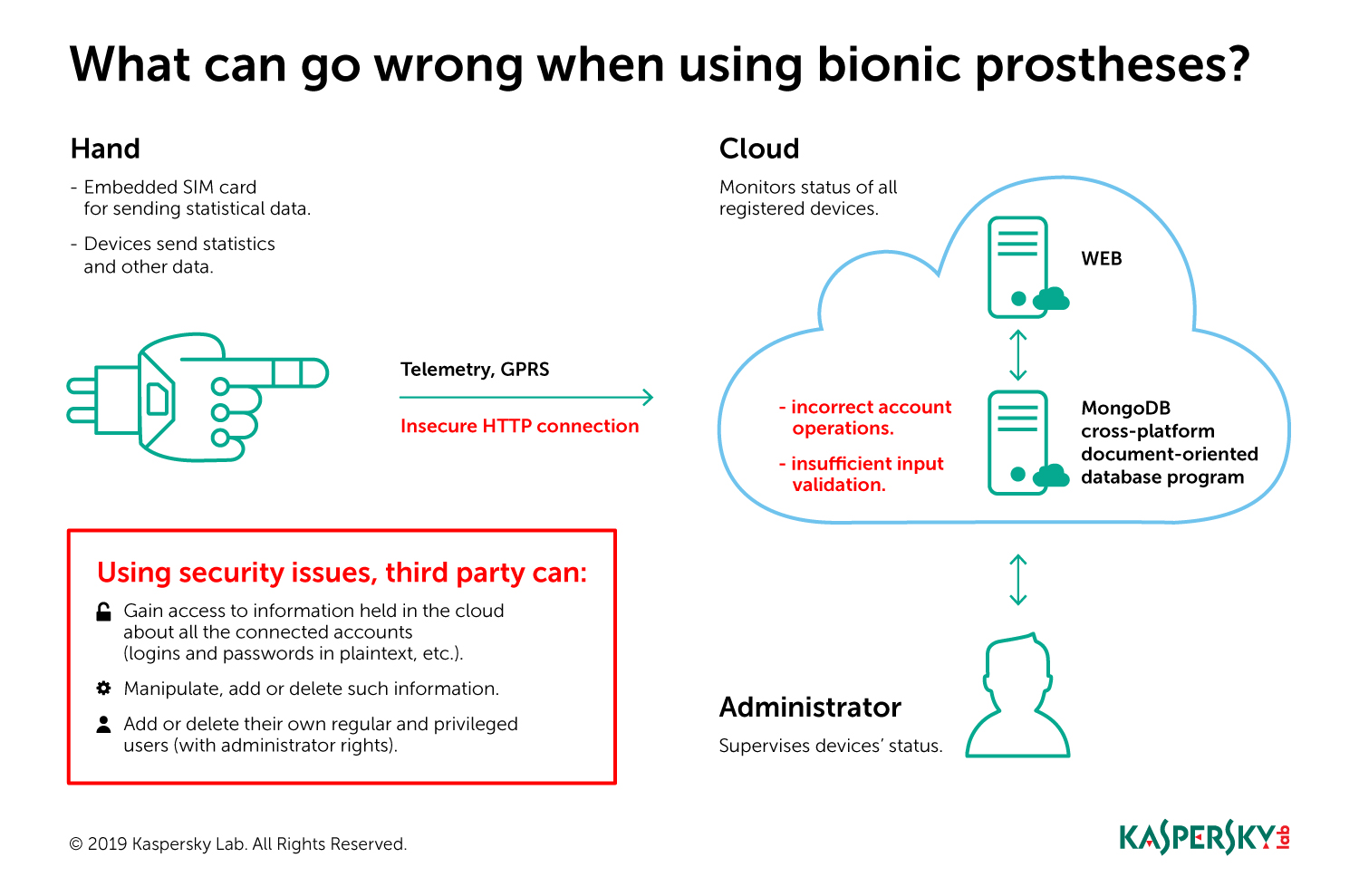
In our research, we focused on those attack vectors that can be implemented without the arm owner’s knowledge. Below is a standard diagram of the arm’s interactions with the outside world.
Each arm is equipped with an embedded SIM card for sending statistical data. The SIM is needed to access the internet and send statistics and other information about the arm’s status. A connection is established to Motorica’s remote cloud, which is an interface for remotely monitoring the status of all registered biomechanical arms. Good thing about the arm’s current architecture – the connection between the arm and the cloud in unidirectional. This means that only the arm is sending data to the cloud, while the cloud sends nothing back. Yet, Motorica Inc says, they plan to implement this feature later.
The basic logic of the arm, such as movement directions, switching motors on or off, etc., are implemented in the C language. The cloud for receiving, processing and storing information is implemented based on the following technologies:
- NodeJS – for backend,
- ReactJS – for frontend,
- MongoDB – database.
Arm-wrestling
At first, we decided to attack the logic of the arm. But soon we discovered that the C code is well-structured and has no vulnerabilities in it. However, the arm that we tested has only the basic functionality. Motorica Inc. wants to add more functions to its biomechanical limbs: smartphone interconnect, contactless payments and other useful features. From our point of view, all these new technologies must be tested for cybersecurity. Especially the ones that could be exploited for MiTM attacks.
Then we started to analyze the protocol used to send the statistics to the cloud and the logic for processing that information on the server. The initial findings showed that the data was sent using the insecure HTTP protocol. A little later we found some incorrect account operations and insufficient input validation that can be used by a remote attacker to:
- gain access to information about all the accounts in the cloud including the logins and passwords (in plaintext) for all the prosthetic arms and administrators,
- add or delete regular and privileged users (with administrator rights),
- launch attacks against administrators via the cloud and then attack Motorica’s internal infrastructure,
- NoSQL-injection,
- cause denial of service for cloud administrator.
In our research we did not go deep into data analysis transferred between muscle sensors and the arm itself or study how the device is interconnected with contactless payment systems or smartphones. These look like very promising research fields for the next years.
What type of attackers might be interested in such attacks – getting prosthetic arm’ data? It’s difficult to say at this moment. However, when biomechanical limbs become more intelligent – attacks could be more beneficial to their perpetrators. Or, when it gets connected to the neuro-implanted brain-chip, the remote attacker will get access to something more valuable than money. Anyway, all IoT devices (and especially biomechanical ones) should be tested for cybersecurity issues at every stage of development.
If you create amazing technologies that are bigger and more important than just classical IoT devices, that help people, or even save lives – you have to check how your technology works, and whether there is a chance to attack your device and damage people. To prevent basic vulnerabilities, please follow the best coding practices, implement SDL, do security source code review, create a security champion in your development team, do external vulnerability researches and penetration testing. All these useful and much needed steps will increase the cybersecurity level of your devices and technologies.

















How to Attack and Defend a Prosthetic Arm