
Introduction
Last November we conducted a brief analysis of the threat landscape over the holiday period – from October to December in 2014 and 2015 – to find out if the number of financial cyberattacks during this time differs to that usually seen throughout the year. The retrospective analysis found that the percentage of phishing attacks during this period was higher than the average yearly rate. The dynamics of financial malware attacks also clearly showed that in 2014 and 2015, criminals staged their malicious campaigns to match dates around the Black Friday – Cyber Monday period, and also around Christmas and the New Year.
Based on this data we made the following prognosis: the same holiday period in 2016 will see a spike in cyberattacks. Now that the holidays are over, it is time to find out how accurate that prediction was.
Financial phishing
The numbers
As seen in the table below, unlike in previous years, the difference between the overall yearly results and the results in Q4 is not significant. However, the percentage of financial phishing attacks blocked by Kaspersky Lab products in Q4 2016 was higher than the total average for the year.
| 2013 | Full year | Q4 |
| Financial phishing total | 31.45% | 32.02% |
| E-shop | 6.51% | 7.80% |
| E-banks | 22.20% | 18.76% |
| E-payments | 2.74% | 5.46% |
| 2014 | Full year | Q4 |
| Financial phishing total | 28.73% | 38.49% |
| E-shop | 7.32% | 12.63% |
| E-banks | 16.27% | 17.94% |
| E-payments | 5.14% | 7.92% |
| 2015 | Full year | Q4 |
| Financial phishing total | 34.33% | 43.38% |
| E-shop | 9.08% | 12.29% |
| E-banks | 17.45% | 18.90% |
| E-payments | 7.08% | 12.19% |
| 2016 | Full year | Q4 |
| Financial phishing total | 47.48% | 48.13% |
| E-shop | 10.17% | 10.41% |
| E-banks | 25.76% | 26.35% |
| E-payments | 11.55% | 11.37% |
Moreover, the Q4 2016 results are the highest we’ve seen so far. 48.13% of all phishing attacks registered by Kaspersky Lab products were focused on gleaning users’ financial data, which is 0.65% higher than the average share of financial phishing in 2016, and 4.75% more than in the same period in 2015. However, the holiday period is not the only reason for such a high percentage of financial attacks. Phishing scams are the easiest way for even low level professional criminals to earn money. The preparation and supporting stages for such scams don’t require a lot of specific tools or knowledge, yet they bring a good return. In other words, phishing attacks appear more attractive to criminals due to their ease and affordability, when compared to staging a financial malware attack. This has resulted in the growth in popularity of phishing.
Delivered on time
As evidenced in our original analysis of the threat landscape during the holiday period in 2014 and 2015, criminals were trying to tie their phishing campaigns to certain dates which resulted in a visible increase in the number of attacks during the Black Friday, Cyber Monday and also Christmas periods. The 2016 figures showed no difference but we’ve seen an increase in the number of attacks which utilized well-known brands from the online retail and financial industries.
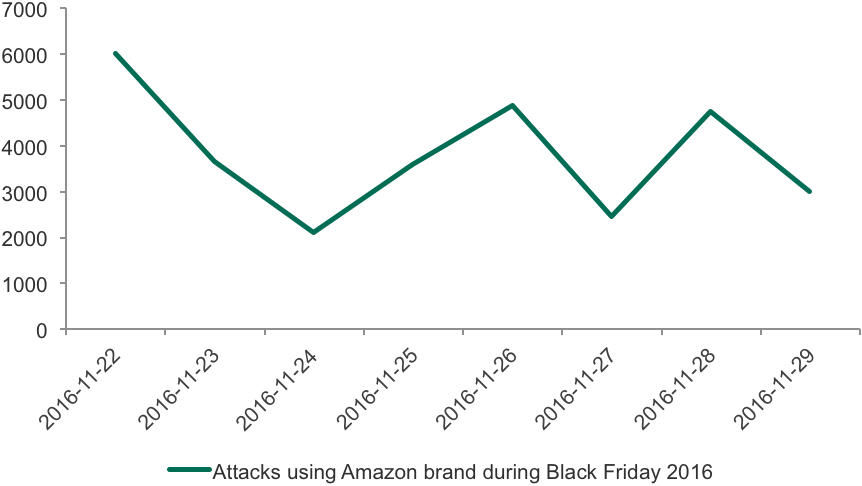
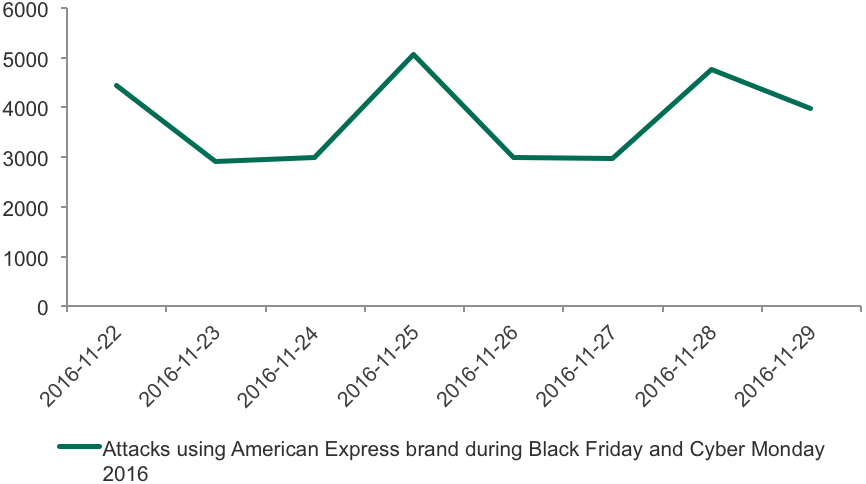
As seen on the graph above, the spikes of detections of Amazon-themed phishing scams matched the dates of Black Friday and Cyber Monday 2016 almost perfectly. The same dynamics are repeated with some other topical brands including payment systems.
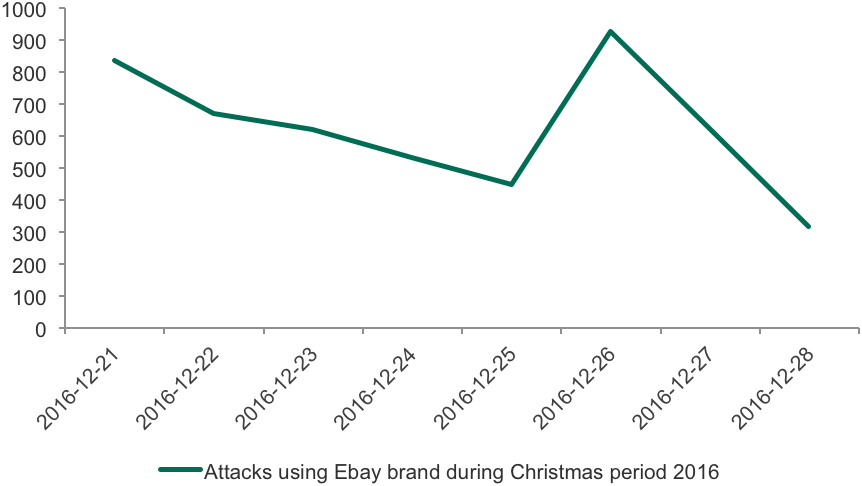
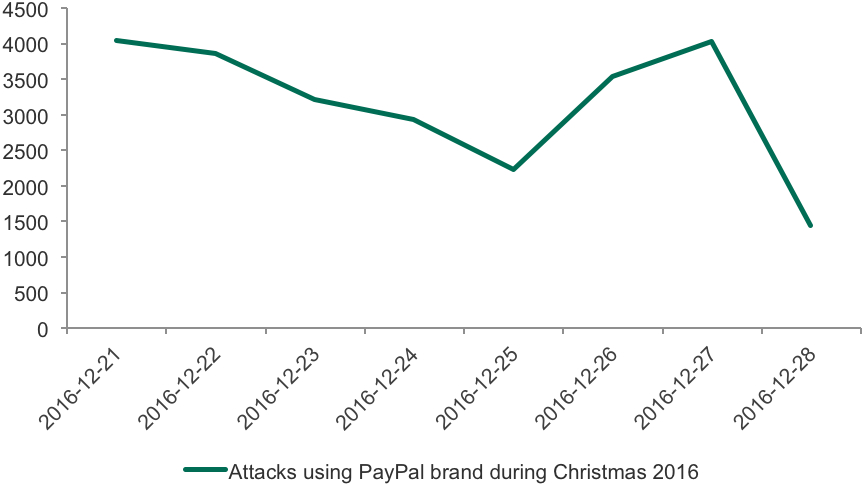
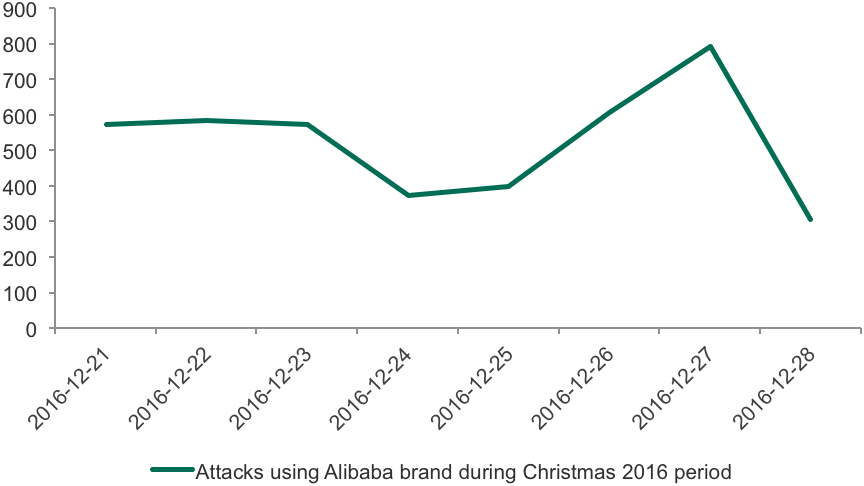
Interestingly, the dynamics during the Christmas period are different. As seen below, the number of attacks started decreasing several days prior to Christmas Eve, and then went up on 25th of December.
Such synchronous behavior could be explained by multiple factors, one of which is that cybercriminals are also celebrating Christmas and that the overall number of web users also decreases on 24th December. But on 25th December, the number of attacks goes back up.
Scams: from Black Friday to Christmas-themed
In our initial report, we examined some examples of so-called topical phishing scams dedicated to a specific topic – the Black Friday sales. While the report was published several weeks before the actual sales started, we already identified some examples of Black Friday-themed phishing scams. Closer to the start of the sales some new examples appeared.
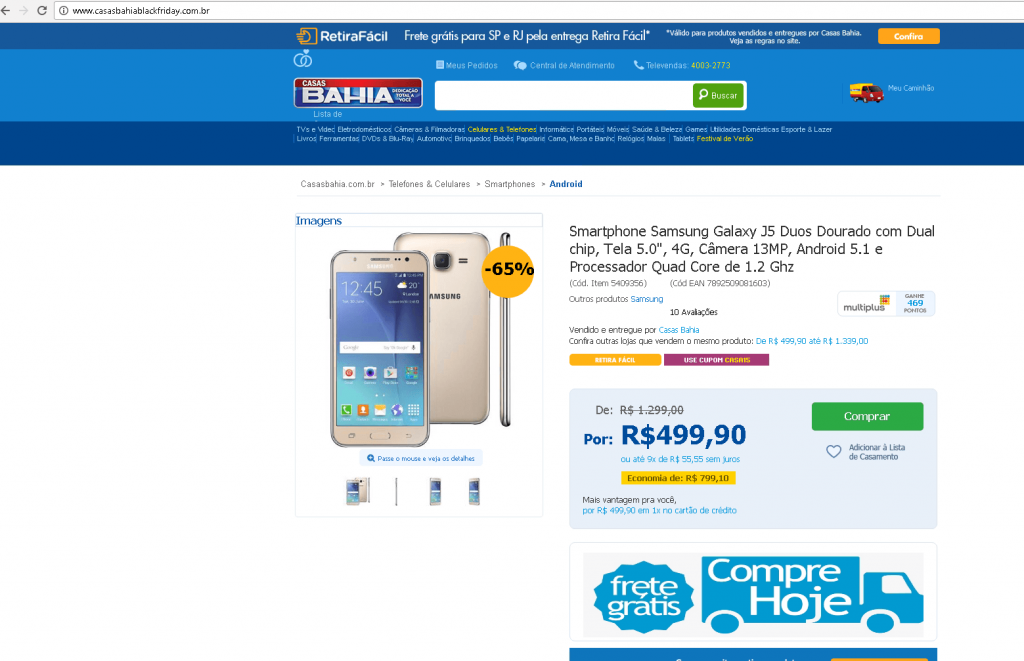
Example of a Black Friday-themed phishing scam offering a smartphone with 65% discount.
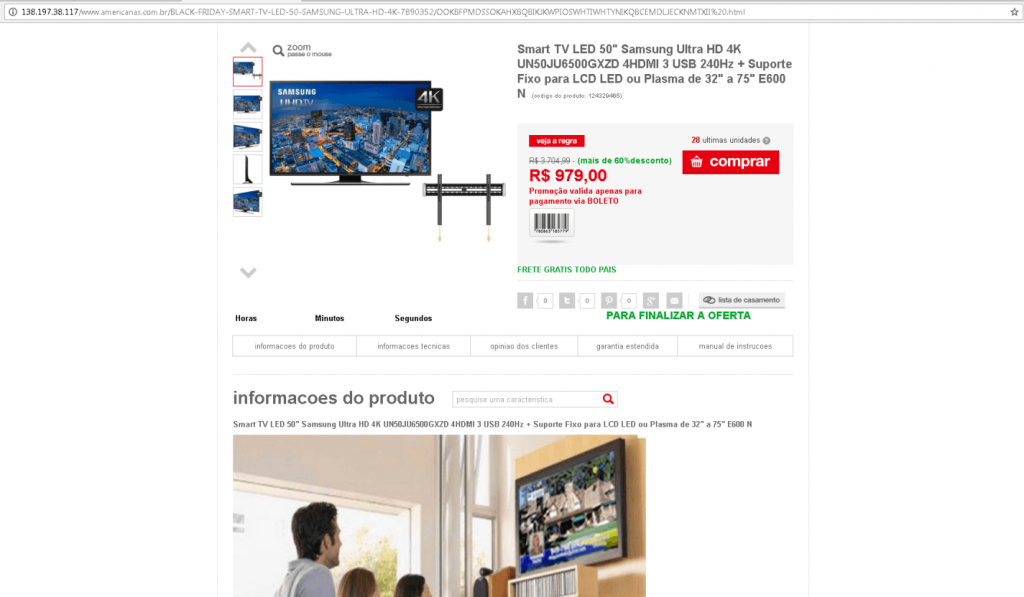
Example of a Black Friday-themed phishing scam offering a TV for an attractive price.
The scams mostly promoted personal electronics, like smartphones and TVs, at extremely low prices, and tried to lure users into providing payment information to criminals. With Christmas approaching, the topics of scams changed accordingly. In December, our researchers started to detect Christmas and New Year-themed phishing schemes.
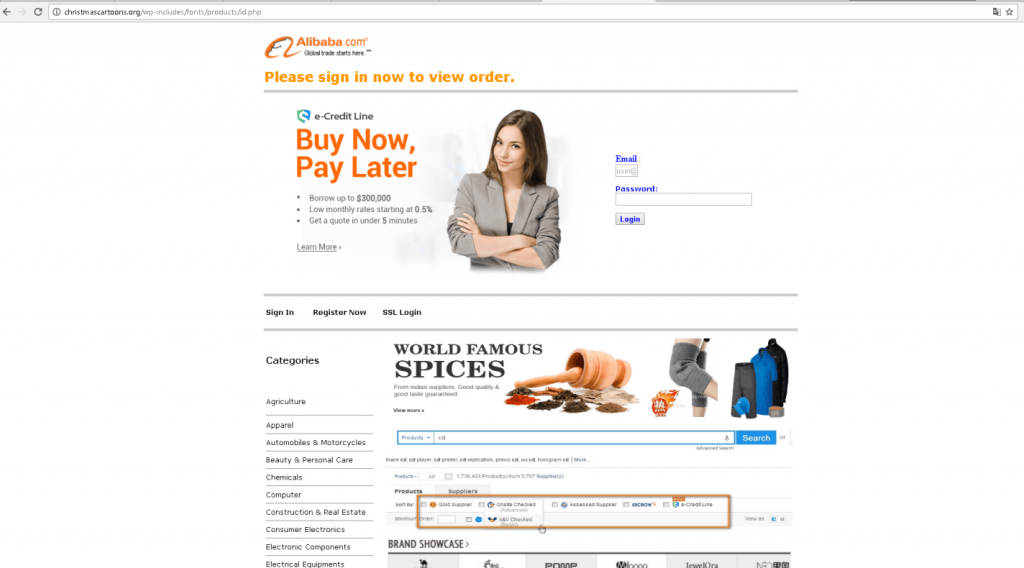
Example of a Christmas-themed phishing scam resembling the Alibaba.com e-shop.
The example on the screen shot above doesn’t look Christmas-themed at first glance. However this fake Alibaba.com website was available on the christmascartoons.org URL and was supposed to attract victims with a tempting offer to get a loan with very low interest, along with the ability to search for goods and buy them from the same page using a credit card.
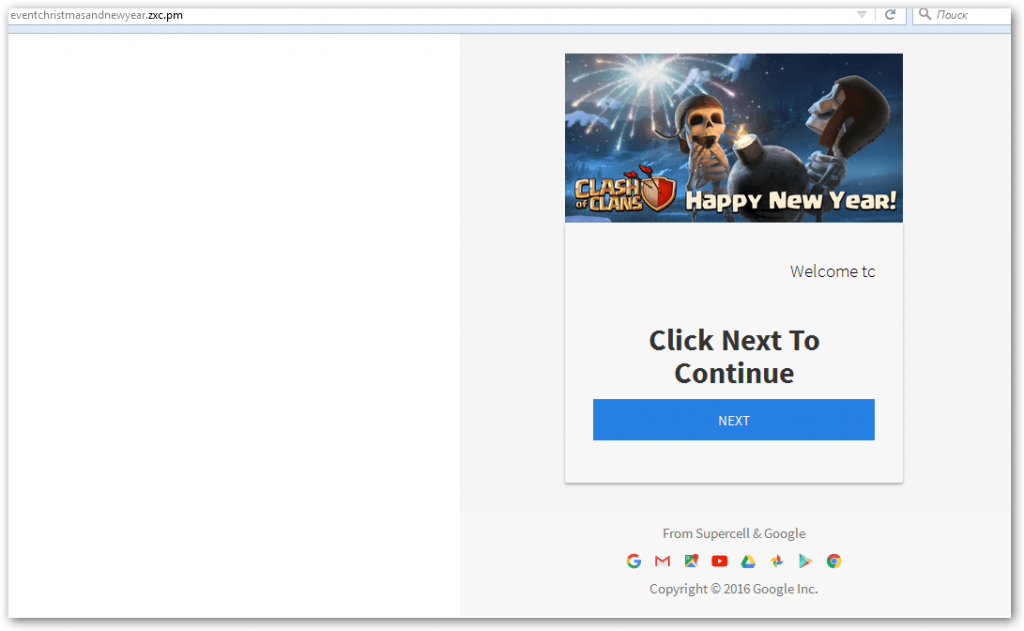
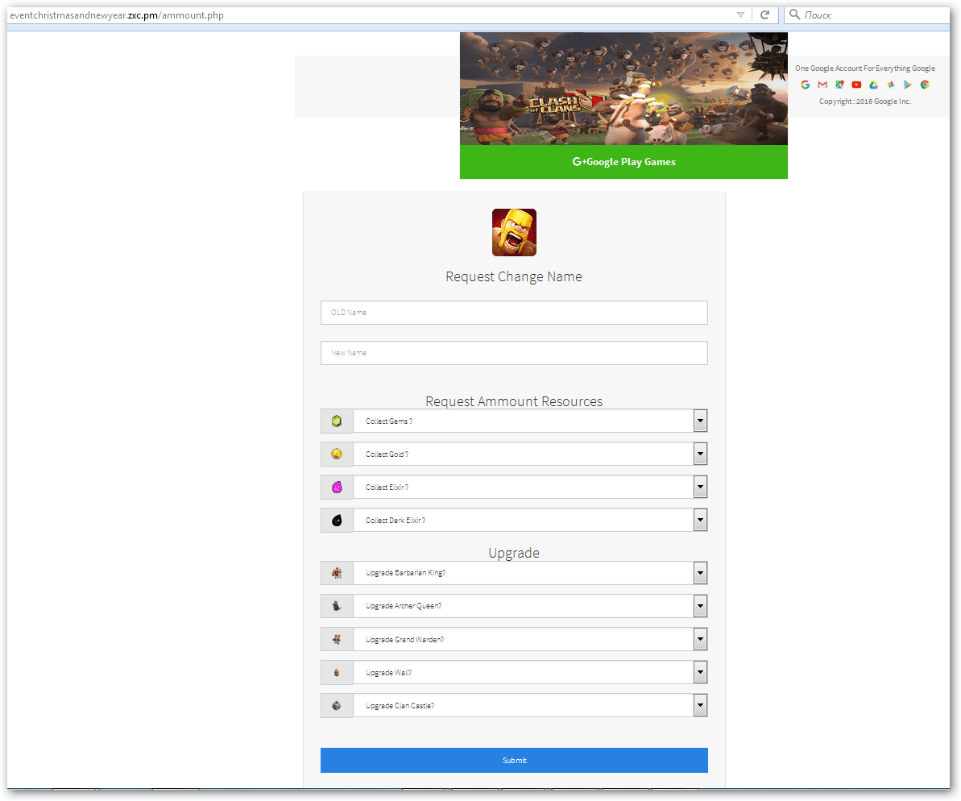
In another example targeting mobile users, criminals tried to exploit the popularity of the Clash of Clans mobile game.
The scam promises that the developers of the game are giving away some valuable in-game virtual items for free, as a New Year present to fans.
Users can choose from range of items, however in order to receive these gifts, they need to fill in a registration form which requests their Gmail account details.
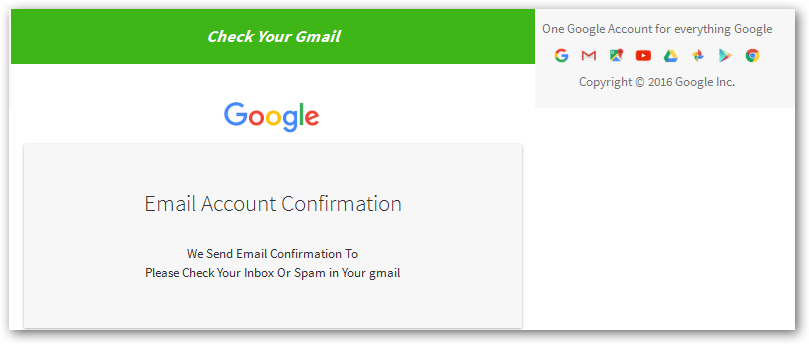
Needless to say, in exchange for this information, the victim receives nothing but a loss of control over their email account and the confirmation email.
But the latter is only sent so criminals could be sure that the credentials provided by the victim are legitimate.
In general, we can’t say that the holiday period in 2016 has seen an unusually high increase of phishing attacks, however, our major hypothesis, stated in previous reports – that criminals would exploit Black Friday and Christmas topics and dates – has been confirmed.
And of course, financial phishing wasn’t the only type of cyberthreat that behaved unusually in the last three months of 2016. The financial malware landscape also showed some interesting changes.
Financial malware attacks
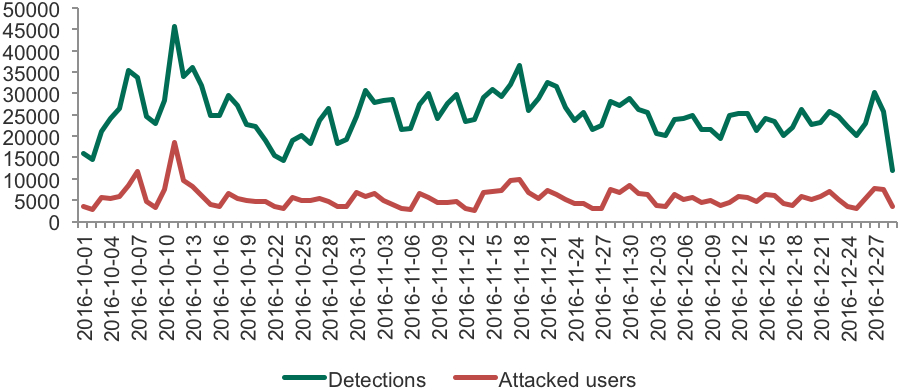
In total, during Q4 2016 Kaspersky Lab registered attacks with financial malware against 319,692 users worldwide. That is 22.49% more than during the same period in 2015, when 261,000 users were attacked, and 2.7% more than in 2014. It is hard to say if such an increase has been provoked by criminal interest in the holiday season; however, data on the dynamics of attacks shows that just like phishing scammers, financial malware operators tried to connect their activity to particular dates.
Dynamics of attacks with financial malware during Q4 2016 (holiday period)
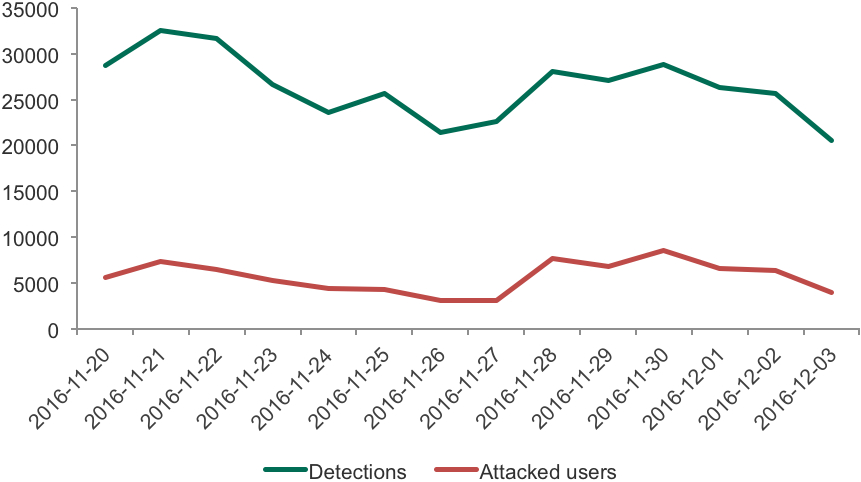
25th November 2016 (Black Friday) saw a modest, but visible spike in attacks, with another on 28th November (Cyber Monday). In all, November became the second hottest month of the period in terms of number of attacked users: with more than 120 000. The hottest was October, with more than 130 000 attacked users.
Dynamics of attacks with financial malware during Black Friday and Cyber Monday 2016
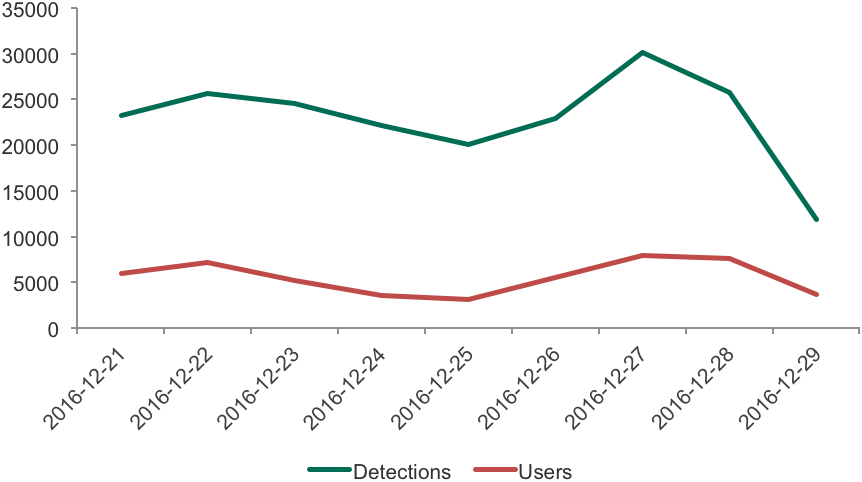
The activity of attackers during the Christmas period showed a different pattern. A major increase happened before (on December 22nd) and after (from 25 – 27th December). This may be explained by the fact that most e-commerce activities happen around these dates: people buy gifts and goods for Christmas and the New Year, travel for vacations and spend money on entertainment.
Dynamics of attacks with financial malware during the Christmas 2016 period
It is also important to note that the dynamics of attacks during the holidays are very similar to what we have already seen in 2015 and 2014. Criminals are eager to get users’ money and the holiday period is a key time for them.
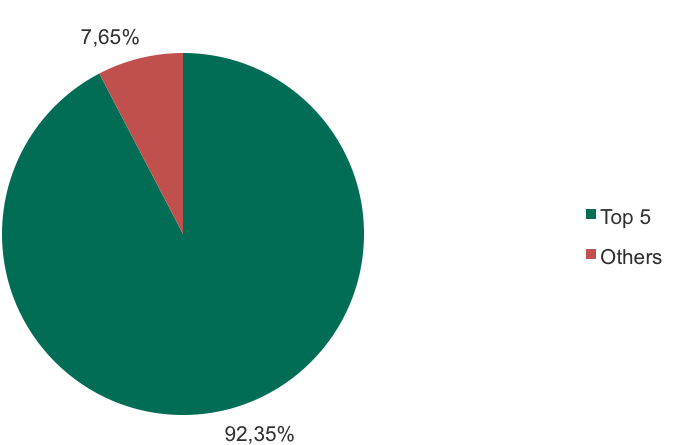
To reach their goals they use one of 30 families of banking trojans of which five are the most widespread: Zbot, Nymaim, Shiotob, Gozi and Neurevt. These five are responsible for attacks against 92.35% of users in the period.
The share of users attacked with Top 5 banking trojans
Conclusion
It looks like the trends we spotted as part of our analysis of the threat landscape during the holiday period in 2014 and 2015 have repeated in 2016, but on a larger scale, with more users being attacked. It is too early to draw conclusions on how successful fraud campaigns during the 2016 holiday season were, because usually criminals who were able to steal credentials to payment cards don’t cash them in immediately. They wait for several months in order to make fraudulent transactions less suspicious to the anti-fraud systems of financial organizations, but it would be safe to say that there were multiple attempts to exploit the high sales season.
Although the holiday season is over, it is still imperative to keep in mind several simple rules to stay safe when carrying out financial operations online. Steps to follow can be found in our initial report about holiday threats.




















Holiday 2016 financial cyberthreats overview