
More than a year has passed since the release of our last article on HackingTeam, the Italian company that develops a “legal” spyware tool known as Remote Control System, or short, RCS. In the meantime a lot has been happened, so it’s time for an update on all our current research findings on the RCS malware.
Locating the command servers
One of the most important things we’ve uncovered during our long and extensive research is a specific feature than can be used to fingerprint the RCS command servers (C2s). We presented details of this method at the Virus Bulletin 2013 conference.
To summarize, when a special request is sent to a “harmless” HackingTeam RCS C&C server, the RCS C&C responds with the following error message:
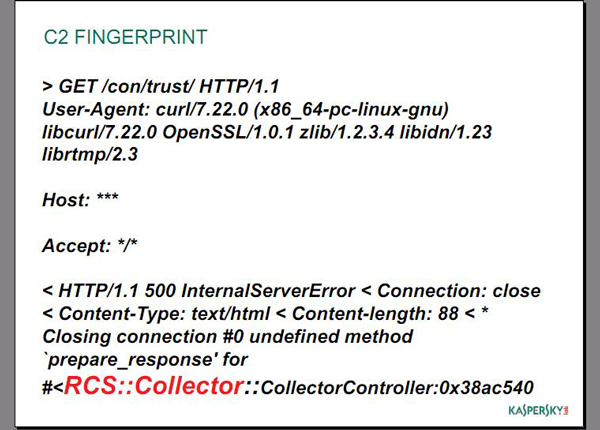
Slide from our VB presentation with HackingTeam’s C2 fingerprint
First of all, the codename ‘RCS’ is there, all right. What we weren’t sure about was the ‘Collector’ referred to in the response. This probably refers to the fact that the server “collects” information from the victims. We used this particular fingerprinting method to scan the entire IPv4 space, which allowed us to find all the IP addresses of the RCS C2s around the world and plot them nicely to a map showing their locations. šWe pinpointed a grand total of 326 C2s.
| Count of C2s | Country name |
| 64 | UNITED STATES |
| 49 | KAZAKHSTAN |
| 35 | ECUADOR |
| 32 | UNITED KINGDOM |
| 24 | CANADA |
| 15 | CHINA |
| 12 | COLOMBIA |
| 7 | POLAND |
| 7 | NEW ZEALAND |
| 6 | PERU |
| 6 | INDONESIA |
| 6 | BRAZIL |
| 6 | BOLIVIA |
| 6 | ARGENTINA |
| 5 | RUSSIAN FEDERATION |
| 5 | INDIA |
| 4 | HONG KONG |
| 4 | AUSTRALIA |
| 3 | SPAIN |
| 2 | SAUDI ARABIA |
| 2 | MALAYSIA |
| 2 | ITALY |
| 2 | GERMANY |
| 2 | FRANCE |
| 2 | EGYPT |
| 1 | UKRAINE |
| 1 | THAILAND |
| 1 | SWEDEN |
| 1 | SINGAPORE |
| 1 | ROMANIA |
| 1 | PARAGUAY |
| 1 | MOROCCO |
| 1 | LITHUANIA |
| 1 | KENYA |
| 1 | JAPAN |
| 1 | IRELAND |
| 1 | HUNGARY |
| 1 | DENMARK |
| 1 | CZECH REPUBLIC |
| 1 | CYPRUS |
| 1 | Other |
| 1 | BELGIUM |
| 1 | AZERBAIJAN |
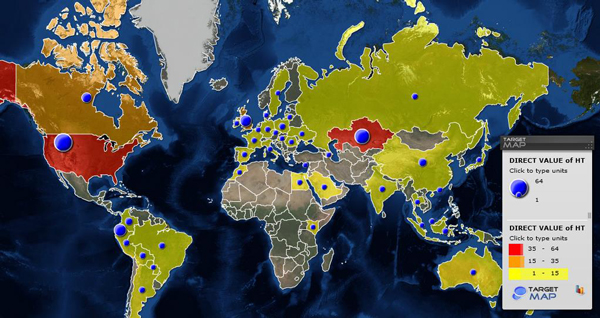
Map showing the countries of the current HackingTeam servers’ locations
The largest amount of identified servers was in the US, Kazakhstan and Ecuador. Unfortunately, we can’t be sure that the servers in a certain country are used by that specific country’s LEAs; however, it would make sense for LEAs to put their C&Cs in their own countries in order to avoid cross-border legal problems and the seizure of servers. Nevertheless, several IPs were identified as “government” related based on their WHOIS information and they provide a good indication of who owns them.
Mobile modules
It was a well-known fact for quite some time that HackingTeam products included malware for mobile phones. However, these were rarely seen. In particular, the Android and iOS Trojans have never been identified before and represented one of the remaining blank spots in the story. Earlier this year, we discovered a number of mobile malware modules coming from HackingTeam for the following platforms:
- Android
- iOS
- Windows Mobile
- BlackBerry
All these modules are controlled by the same configuration type, which is a good indication that they are related and belong to the same product family.
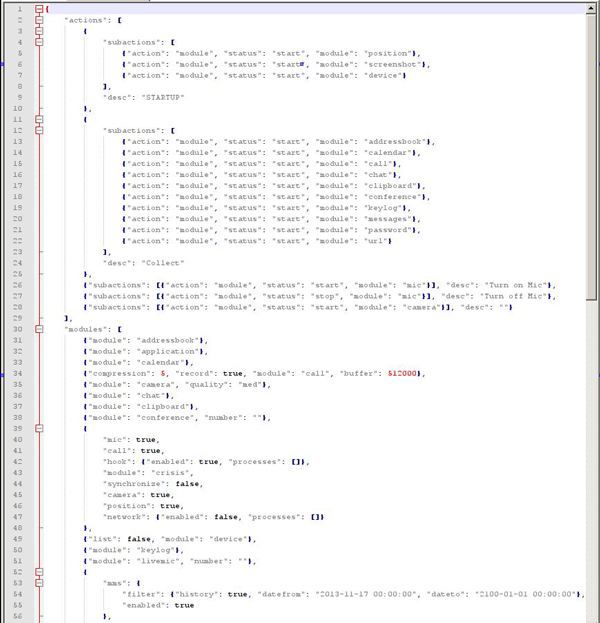
Configuration file from the RCS mobile modules
Certainly, our main interest during the analysis of the mobile modules was in iOS and Android, due to their popularity. The iOS module works only on jailbroken devices. Here is a description of the main functionality of the iOS module:
- Control of Wi-Fi, GPS, GPRS
- Recording voice
- E-mail, SMS, MMS
- Listing files
- Cookies
- Visited URLs
- Cached web pages
- Address book
- Call history
- Notes
- Calendar
- Clipboard
- List of apps
- SIM change
- Live microphone
- Camera shots
- Support chats, WhatsApp, Skype, Viber
- Log keystrokes from all apps and screens via libinjection
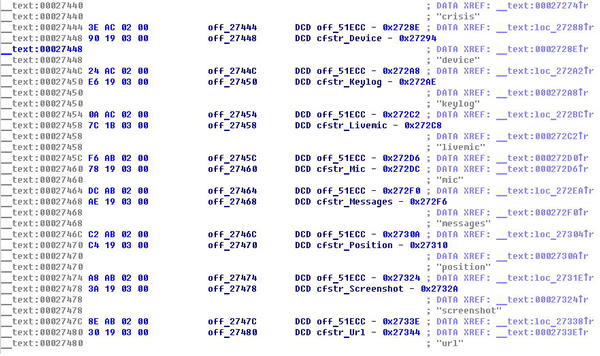
Disassembled code of the iOS module
The Android module is protected by the DexGuard optimizer/obfuscator and is therefore extremely difficult to analyze. However, we discovered (see the trace below) that the sample has all the functionality of the iOS module listed above – plus support for hijacking information from the following applications:
- com.tencent.mm
- com.google.android.gm
- android.calendar
- com.facebook
- jp.naver.line.android
- com.google.android.talk
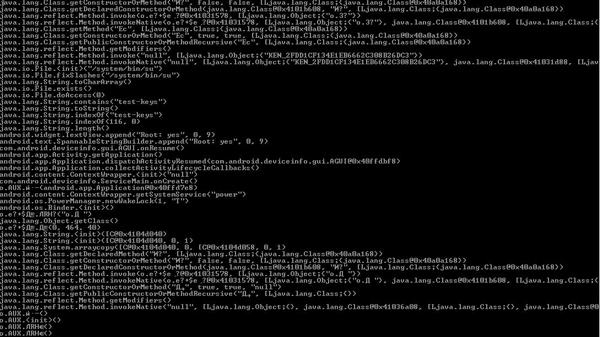
Trace of an RCS Android sample
Mobile infectors
Another aspect of particular interest to us was the way the malware samples are installed on mobile devices. We discovered several modules that infect mobile devices connected to infected Windows or Mac OS X computers.
As already mentioned, the iOS module can only be used on jailbroken devices. That is why the iOS infector uses the AFP2 protocol to transfer. The “infector” has a nice GUI that enables installation if there is physical access to the victim’s device or remote admin access to an infected computer.
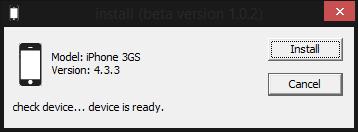
Main window of the iOS infector
| iPhone1,1 | iPhone1,2 | iPhone2,1 |
| iPhone3,1 | iPhone3,2 | iPhone3,3 |
| iPhone4,1 | iPhone5,1 | iPhone5,2 |
| iPad1,1 | iPad2,1 | iPad2,2 |
| iPad2,3 | iPad2,4 | iPad3,1 |
| iPad3,2 | iPad3,3 | iPad3,4 |
| iPad3,5 | iPad3,6 | iPhone |
| iPhone 3G | iPhone 3GS | iPhone 4 |
| iPhone 4 | iPhone 4 (cdma) | iPhone 4s |
| iPhone 5 (gsm) | iPhone 5 | iPad |
| iPad2 (Wi-Fi) | iPad2 (gsm) | iPad2 (cdma) |
| iPad2 (Wi-Fi) | iPad3 (Wi-Fi) | iPad3 (gsm) |
| iPad3 | iPad4 (Wi-Fi) | iPad4 (gsm) |
| iPad4 |
List of Apple devices supported by the iOS infector
After successfully connecting, the iOS infector copies several files to iOS and runs an install.sh file:
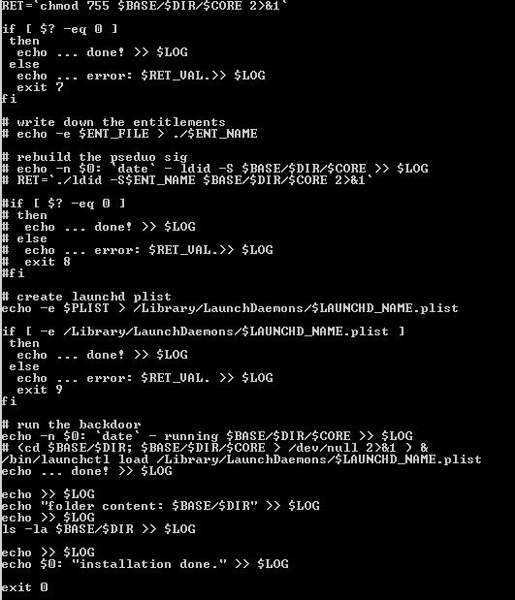
Part of the install.sh file that is run on an infected iOS device
As mentioned above, remote admin access to an infected computer is one of the possible ways for the malware to be installed on a connected mobile device. The fact that only jailbroken iOS devices are supported can be a limiting factor. However, this is not a huge problem since an attacker can also run a jailbreaking tool such as Evasi0n via the same infected computer. In this case the only thing that can protect a user from a remote jailbreak and infection is the mobile device’s passcode. However, if the device is unlocked while connected to the infected computer, it can be infected by the attacker.
Another interesting mobile infector is the one for BlackBerry devices, which uses the JavaLoader application to load malware samples on BB 4.5 and 5.0. In its disassembled code, we found a path to the PDB debug file, which appears to have been mistakenly forgotten by the authors. The original project was located in the ‘C:\HT\RCSBlackBerry\Workspace\RCS_BB_Infection_Agent\’ when this malware was created.
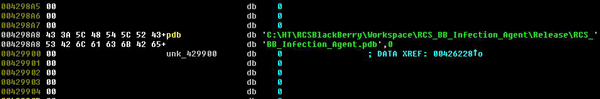
Part of the code of a Blackberry infector with a path to the PDB file
Summary
In this latest installment of our ongoing research, we uncovered a huge infrastructure that is used to control the RCS malware implants. Our latest research has indentified mobile modules that work on all well-known mobile platforms, including as Android and iOS. These modules are installed using infectors – special executables for either Windows or Macs that run on already infected computers. They translate into complete control over the environment in and near a victim’s computer. Secretly activating the microphone and taking regular camera shots provides constant surveillance of the target – which is much more powerful than traditional cloak and dagger operations.
The new data we are publishing on HackingTeam’s RCS is extremely important because it shows the level of sophistication and scale of these surveillance tools. We like to think that if we’re able to protect our customers from such advanced threats, then we’ll sure have no trouble with lesser, more common threats like those posed by cybercriminals.
Appendix:
MD5s of mobile infectors:
- 14b03ada92dd81d6ce57f43889810087 – BlackBerry infector
- 35c4f9f242aae60edbd1fe150bc952d5 – iOS infector
MD5s of Android samples:
- ff8e7f09232198d6529d9194c86c0791
- 36ab980a954b02a26d3af4378f6c04b4
- a2a659d66e83ffe66b6d728a52130b72
- 9f06db99d2e5b27b01113f78b745ff28
- a43ea939e883cc33fc766dd0bcac9f6a
- a465ead1fd61afe72238306c7ed048fe
MD5s of Windows samples:
- bf8aba6f7640f470a8f75e9adc5b940d
- b04ab81b9b796042c46966705cd2d201
- 1be71818a228e88918dac0a8140dbd34
- c7268b341fd68cf334fc92269f07503a
List of active C2s on 19.06.2014:
- 50.63.180.***
- 146.185.30.***
- 204.188.221.***
- 91.109.17.***
- 106.186.17.***
- 119.59.123.***
- 95.141.46.***
- 192.71.245.***
- 106.187.99.***
- 93.95.219.***
- 106.187.96.***
- 124.217.245.***
- 23.92.30.***
- 82.146.58.***
- 93.95.219.***
- 209.59.205.***
RCS modules (using Kaspersky Lab’s classification names):
- Backdoor.OSX.Morcut
- Rootkit.OSX.Morcut
- Trojan.OSX.Morcut
- Backdoor.Win32.Korablin
- Backdoor.Win64.Korablin
- Rootkit.Win32.Korablin
- Rootkit.Win64.Korablin
- Trojan.Multi.Korablin
- Trojan-Dropper.Win32.Korablin
- Backdoor.AndroidOS.Criag
- Trojan-Spy.AndroidOS.Mekir
- Trojan.Win32.BBInfector
- Trojan.Win32.IOSinfector
- Trojan.OSX.IOSinfector
- Trojan-Spy.IphoneOS.Mekir
- Trojan-Spy.WinCE.Mekir
- Trojan-Spy.BlackberryOS.Mekir
HackingTeam 2.0: The Story Goes Mobile





















William anderson
I do government reverse engineering. I am interested in getting blackberry samples. Please contact me