
The recent online hysteria over the BitCoin virtual money system has attracted the attention not only of those who dream of making money out of thin air but also of cybercriminals who, as usual, want to steal anything they can get their hands on.
A few days ago our colleagues at F-Secure wrote that they had detected a primitive Trojan that steals e-wallets from the computers of BitCoin users.
However, some cybercriminals seem to think that it’s more profitable to steal computer resources rather than e-wallets.
Today our analysts detected a new threat spreading in the Russian sector of the Internet – Trojan.NSIS.Miner.a. This Trojan has two components – the legitimate bcm.exe file BitCoin Miner (not-a-virus:RiskTool.Win32.BitCoinMiner.a), and a malicious module that installs bcm without the user’s knowledge and adds it to the autorun registry. The infected computer then starts to generate bit-coins for the Trojan’s author.
Of course, the Trojan’s code clearly indicates the server address where the cybercriminal’s account is located.
We decided to see how successful our nameless ‘miner’ was, and ended up getting a bit of a surprise.
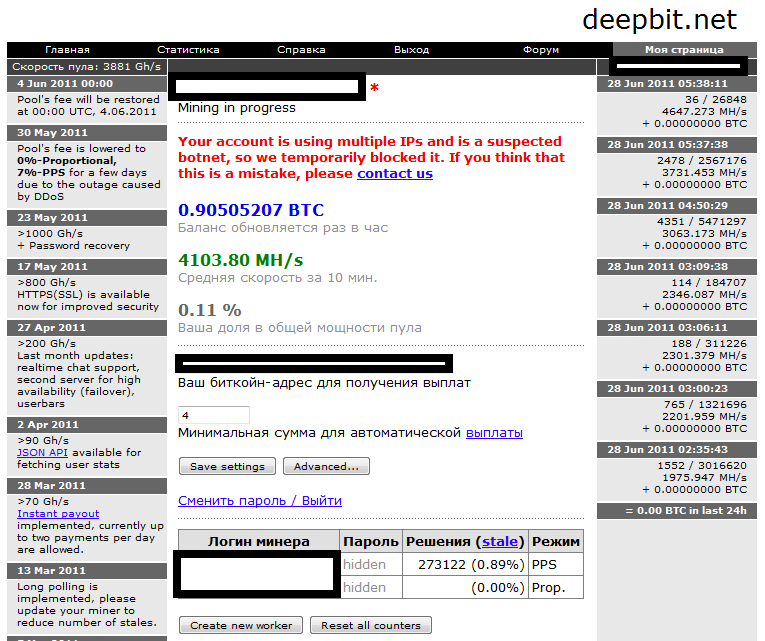
Your account is using multiple IPs and is a suspected botnet, so we temporarily blocked it. If you think that this is a mistake, please contact us
Before the account owner had time to start out on his road to riches, the automated system suspected something was up and the account was temporarily blocked 🙂
Judging by the statistics, the black hat failed to find his very own Klondike and managed to ‘pan’ slightly less than a single coin.
We informed the owners of the site about this Trojan and hopefully the account will be blocked for good.






















Gold rush